When an analyst detects an intrusion, the most critical factor is analyzing the context of the intrusion. We do this by identifying the attacker’s tactics, techniques, and procedures (TTPs). Threat intelligence models (kill chain and Diamond model) accelerate intrusion analysis by quickly determining:
- How the attackers (multiple) operate
- Which step of the intrusion the attack is in
- What to expect next from the attack
With additional insights presented by the Vectra AI-driven Threat Detection and Response platform, powered by Attack Signal Intelligence™, below, you’ll see contextualized detections during an intrusion.
Real-Time Intrusion Analytics for Informed Decision-Making
Let's take a closer look at how the Vectra AI-driven Threat Detection and Response platform enables intrusion analytics in real time so you can make informed decisions with contextualized automated responses.
Correlated Detections Give Intrusion a Quadrant Score for Context
Several correlated detections triggered an alert and put the victim host in Vectra’s HIGH quadrant score.
Vectra’s quadrant scoring prioritizes an attack’s level of urgency based on the number of techniques used by an attacker and the progress of the attack itself. Hosts and accounts in the high and critical quadrant are considered urgent and warrant immediate attention.
This high quadrant score was confirmed by endpoint alerts from the customer’s EDR. Armed with this critical intelligence, Vectra MDR analysts continued their investigation.
Triggered Detections and Vectra Threat Intelligence Match
This detection triggered more analysis, which revealed that the host was either generating DNS activity or making direct connections associated with malicious external IPs or Domains. In this case, the domain rotation.craigconnors[.]com (called “rotation” below) is contacted directly on port 8080 and considered malicious. Data is exchanged (few KB sent and received). The attack phase is related to C&C, indicating external adversary infrastructure communications.
Cf:

By understanding and detailing the threat group activity, Vectra MDR was able to contextualize the behavior, instead of wondering, was it a fingerprinting? Was it done via wscript? What was the goal of the attacker in the kill chain?
Vectra MDR gives us clarity and context to threat behavior.
Privilege Anomaly: Unusual Service – Insider
Another detection was triggered when an account with a low privilege score was used from a host that also had a low privilege score in order to access a service which has a substantially higher privilege score. On the other side of the curtain, this infected host was doing a Kerberoasting attack, and by triggering the HTTP service by asking for a TGS ticket, we detected the privileged anomaly.

What is a privilege score and what is the risk?
The threat score of this detection is driven by the privilege scores (see this link for details on what we name ‘privileges’ in section « AI Detection Case Study: Privilege Credential Abuse in the Network and Cloud ») of the three Kerberos entities (account, host and service). The threat score is driven by the degree of mismatch in the privilege scores, such as when a service with high privilege is accessed from low or medium privileged hosts and accounts.

This detection is part of an attacker’s lateral movement phase attempt. Lateral movements within a network involving privileged accounts, hosts or services expose an organization to substantial risk of data acquisition and exfiltration.
Investigation–Metadata and Pivots
Storing metadata is advantageous, because it allows you to search in both real time and retrospectively for suspicious behaviors observed in your environment.
It’s always bad to be notified by a third party of a potential intrusion. However, it’s much worse when the intrusion is real, and you realize that you have a gap in your monitoring and data collection capabilities.
Thanks to our AI-driven Threat Detection & Response platform with enriched and stored metadata, we can move forward to investigation and incident response, categorizing activities and triggered detections to create a timeline of events.
Below are some “buckets” we were able to search in order to reconstruct the malicious activity and make comments and hypotheses.
* Reminder: An IOC is an indicator with context: An IP is NOT an IOC. An IP indicating a C2 or Adversary Infrastructure (e.g., a Compromised WordPress, serving adversary’s downloader is an IOC).
** Downgrade cipher attack observed and investigated.
*** Unique to Vectra, not in standard Bro output.
Intrusion Analysis–Activity Groups
We then assess and group some activities on how they operate.
Here we describe below “modus operandi” of several linked activities. We use for this the kill chain model to describe phases of intrusions and map adversary indicators for the identification (then prevention) of cyber intrusion activity.

In the next part of this article, we’ll focus more on the green kill chain above. As shown in the image above, several activity groups can be identified in modern intrusions. Some of them are unrelated to the actual intrusion we investigate (here the “Activity Group 1” linked to other Cybercrime capabilities). Some are dependent on others.
What if the attack isn’t stopped?
What could have happened if we didn’t stop the “Activity Group 2” in Green? The “Activity Group 3” in red would have been able to continue its operations. Some threat groups are dependent on others, such as where “Activity Group 3” is using the previous access of “Activity Group 2” to load its own malwares and payloads (read Cobalt Strike, malwares, then ransomware deployment).
This could be a potential business dependency, indicating “Activity Group 2” is providing Pay per Install, or Initial Access Broker paid service.
Diamond Model
Coming from the Intelligence world, the Diamond Model can be used for malicious activity “as well as the core analytic concepts used to discover, develop, track, group, and ultimately counter both the activity and the adversary.” This model can be applied at each of the event level(s) of intrusion described below (i.e., the KC phases on the left).

It describes the four core features present in every malicious event: that for every intrusion event there exists: “An adversary taking a step towards an intended goal by using a capability over infrastructure against a victim producing a result.”
Why didn’t we use MITRE ATT&CK only? We did.
As analysts, we used a model to encompass not only capabilities/tradecraft and attack methodologies from where MITRE ATT&CK are counted, but the four vertices of the Diamond Model (Adversary, Capabilities, Infrastructure and Victim) to describe a “threat” that cannot be defined with TTPs or Malware(s) only.
Finally, we can map the activity group itself, observed with this model representation.
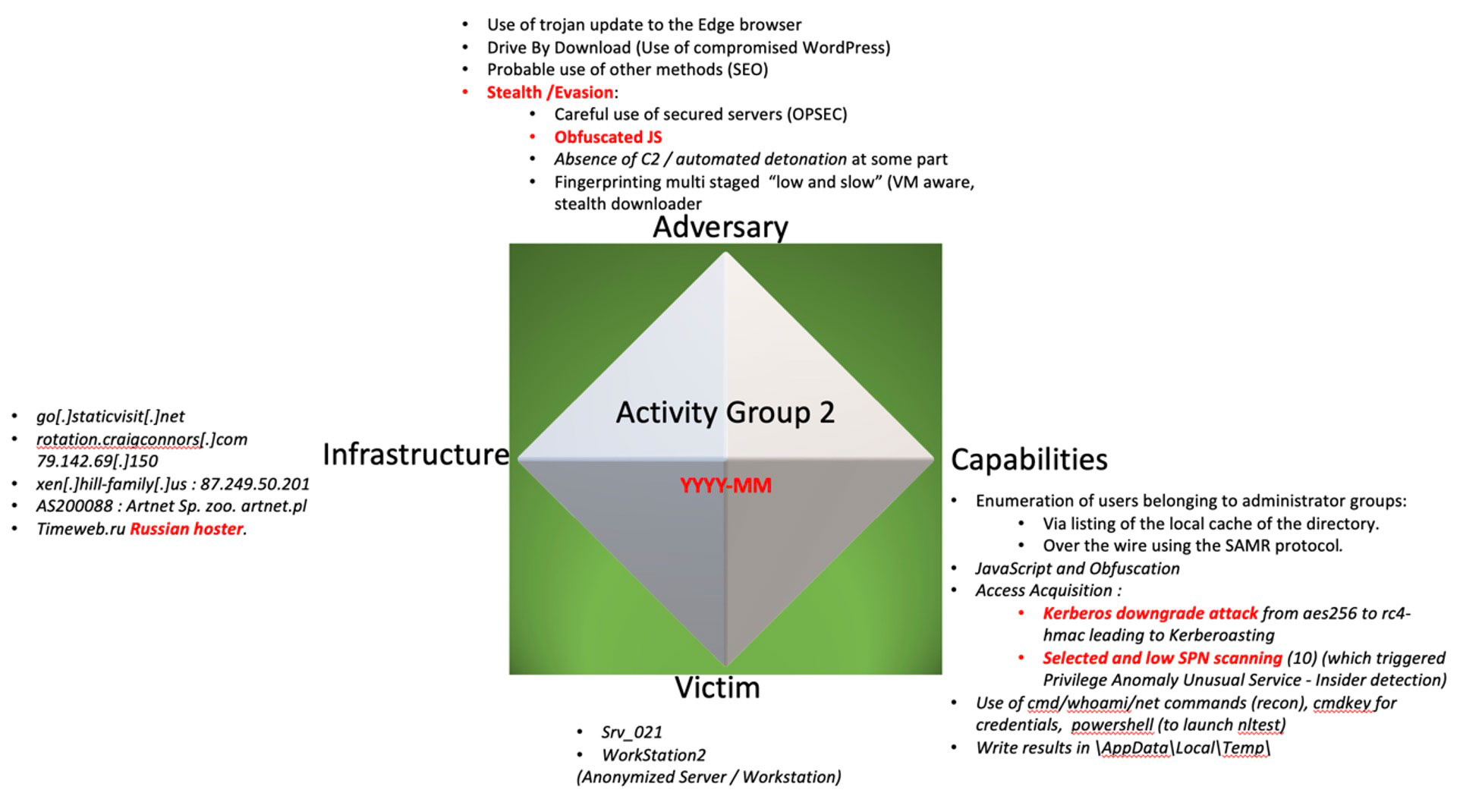
The items in red are what we think as “highest” confidence characteristics of this activity group. That means that if one of these is changing, the activity group is different.
We try to define here the core components of this activity group, which can be: e.g.: The way they obfuscate the JavaScript, the observed attack methodologies, or the Russian hosting usage preferences can all be common points to track it.
Conclusion
AI-driven detection and prioritization combined with human analysis using enriched metadata for investigation can help identify and fight threats in your organization. This combination of AI-driven tools, human insight and meta data provides the expertise, context, and clarity required, in a consistent and repeatable process. This process is paramount when applying threat intelligence to intrusion analysis. It allows analysts to encompass and describe threats with the same language over time, both simplifying and enhancing our threat intelligence by bringing clarity to what we observe. The hunting and defensive actions resulting from these modelized threats could be beneficial to all customers by enabling them to make informed decisions quicker in the threat lifecycle.






