VECTRA AI PLATFORM
Observability and exposure management for modern multi-cloud enterprises
Continuously observe behavior across hybrid and multi-cloud environments to understand where exposure exists and stop attacks before impact.
View technical documentation
WHAT’S THE PROBLEM?
Why observability and exposure management fail in hybrid and multi-cloud environments
When observability is fragmented, threat exposure grows. Attackers move across domains faster than security teams can respond.
Where traditional tools break down:
Cloud-native tools offer shallow, platform-specific visibility
The result: An inability to prevent attacks upfront and delayed detection and weak response when intruders gain a foothold.
WHAT’S THE SOLUTION?
Unified observability and exposure management across hybrid and multi-cloud networks
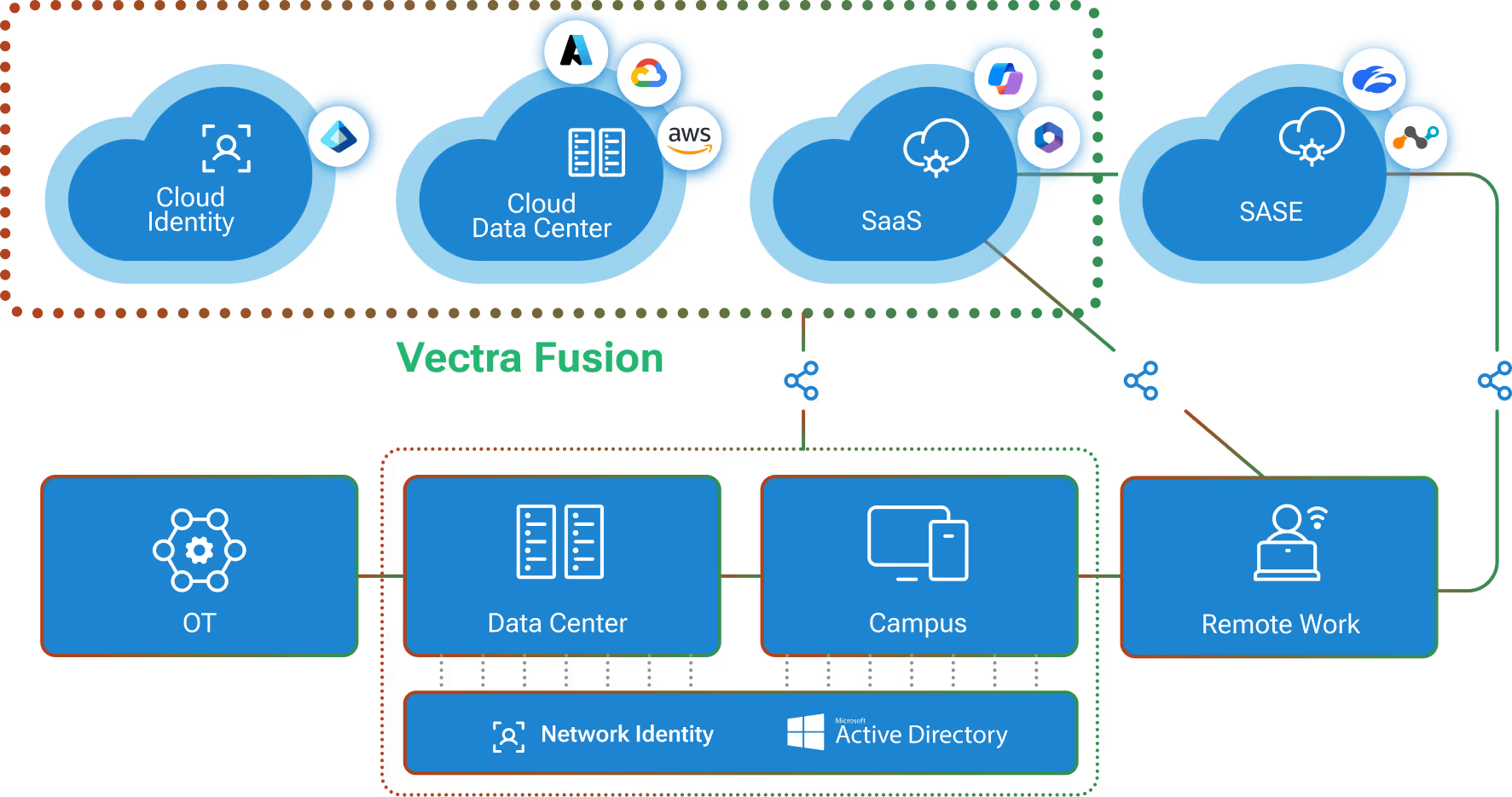
Vectra AI Fusion delivers continuous, observability that surfaces real exposure and reveals attacks in progress across hybrid and multi-cloud environments.
Reduce exposure
Get a real-time view of where attackers can strike. Vectra Fusion exposes misconfigurations, trust violations, and risky lateral movement paths so you can close gaps and eliminate blind spots.
See attacks earlier
Identify attack exposure and intent the moment it begins. Vectra Fusion reveals early-stage actions that siloed tools often miss.
Respond with precision
Quickly get the context you need to execute the right response in minutes, not hours or days.
Only Vectra Fusion delivers true resilience across the cyber kill chain — preventing threats before they start and responding quickly when they do, all in one solution.
HOW DOES IT WORK?
How observability turns into continuous threat exposure management
By observing activity across on-premises and multi-cloud networks, Vectra AI turns exposure into something security teams can see, prioritize, and act on continuously.
Coverage
Vectra Fusion gives you broad visibility across every cloud environment. By ingesting VPC and VNet cloud flow logs as well as DNS data (instead of full packets), Vectra Fusion transforms the cloud data plane into a single source of truth, revealing exposure points and early signs of attacker movement.
Clarity
Vectra Fusion deepens visibility with 300+ network detection models and rich contextual data from cloud and third-party sources. By detecting malicious activity across north–south and east–west traffic (even when flows are encrypted) analysts get clear, high-fidelity signals that accelerate triage and investigation.
Control
Vectra Fusion enables fast response and remediation. With integrations to SIEM, SOAR, and cloud-native enforcement platforms, Vectra Fusion automates containment responses. Customizable dashboards give teams the insights and actions needed for ongoing reporting.
Trusted by leading Security Operations professionals

“We achieved complete visibility and better security detections across all of our environments — including on-premises and multi-cloud. Vectra Fusion ingests and enriches flow data at massive scale without hardware, complicated network taps, or costly deep packet inspection and decryption.”

Shannon Ryan
Senior Director, Core Security Services & Architecture, FICO
SETUP & DEPLOYMENT
Agentless, frictionless multi-cloud observability for continuous threat exposure management.
Vectra Fusion deploys through simple cloud-native integrations — no sensors, taps, or packet mirroring.
Automated cloud configuration, flow log enablement, and context enrichment
One deployment per cloud provider covers all accounts, regions, and VPCs
API integration with existing CI/CD processes
View technical documentation

faqs
Vectra Fusion: Frequently Asked Questions
What is Vectra Fusion and how does it improve multi-cloud visibility?
Vectra Fusion is a cloud-native observability and detection capability within the Vectra AI Platform. It ingests and normalizes cloud flow logs and DNS data from every cloud, enriches them with contextual metadata, and correlates activity across accounts, regions, and providers. This replaces siloed cloud views with a unified, real-time picture of exposures, attacker movement, and policy violations across your entire multi-cloud environment.
Why are existing cloud and network monitoring tools insufficient for threat detection?
Existing tools fall short for a variety of reasons:
- Platform-native flow tools only show visibility within their cloud and offer detections with little context.
- Cloud-native tools focus on application or identity behavior (not network traffic) so they can’t detect lateral movement.
- Traditional network monitoring tools rely on agents or packet capture, which don't scale.
As a result, teams can’t see attacker movement, correlate behavior across clouds, or identify malicious behavior.
Why is broad coverage across cloud flow logs, data planes, and on-premises networks important?
Attackers don’t limit themselves to one environment. They move between cloud accounts, workloads, SaaS apps, and on-premises systems depending on where protections are weakest. Visibility into cloud flow logs, cloud data-plane activity, and traditional network traffic ensures SOC teams can see exposures, policy violations, and attacker movement across the full hybrid environment — not just isolated parts of it.
Why is pre-compromise visibility critical in hybrid and multi-cloud environments?
Pre-compromise visibility means identifying exposures, misconfigurations, trust violations, and lateral movement paths before attackers exploit them. Vectra Fusion provides this through unified flow log analysis and contextual enrichment across all cloud environments.
What are cloud flow logs and why are they important for security?
VPC and VNet flow logs record communication between a source and a destination into, out of, or between cloud networks. Cloud flow logs show what applications, data, and devices are active and what’s happening to them in a cloud network. They’re considered the source of truth for understanding network activity, and are the most effective way to detect anomalous and malicious activity.
How are flow logs used for security purposes?
Common use cases for cloud flow logs in security include network monitoring, usage monitoring and optimization, compliance, and network forensics and security analysis.
How does Vectra Fusion detect lateral movement across clouds?
Attackers often move laterally between accounts, regions, or even cloud providers. Fusion offers a single, consolidated view that breaks down silos, correlates activity across all clouds in real time, and surfaces patterns and behaviors that would be invisible in individual cloud-native tools. This allows teams to see cross-cloud movement, trust-zone violations, and data exfiltration attempts as they happen.
What use cases does Vectra Fusion support for SOC teams?
Vectra Fusion supports a wide range of SOC and cloud operations use cases. Here are the most common ones:
- Improving visibility and coverage across clouds with a unified view
- Detecting threats in real time across east-west and north-south cloud traffic
- Investigating incidents and accelerating response and remediation
- Validating and documenting compliance
- Protecting IP reputation
- Enforcing Zero Trust segmentation
Which cloud and on-prem environments does Vectra Fusion support?
Fusion supports AWS, Azure, Google Cloud Platform, Oracle Cloud, IBM Cloud, SaaS environments, and on-premises networks.
Does Fusion require sensors, packet mirroring, or agents?
No. Fusion uses cloud-native flow logs, DNS, and telemetry for coverage.
Resources
Learn more about Vectra Fusion
Observe network activity. Understand exposure. Act before impact.
See how Vectra Fusion helps security teams turn continuous observability into measurable exposure reduction and faster attack containment.