Cybersecurity AI for the modern network
We research modern attacks to no end, extracting the right data and leveraging the right models to expose every move attackers make.
Vectra AI is named a Leader in the 2025 Gartner MQ for Network Detection and Response (NDR).
A cybersecurity AI approach aligned to how modern attackers operate
AI alone isn’t enough. Our approach meticulously aligns the right algorithm with each threat detection challenge. It starts with a deep understanding of modern attack behaviors and AI techniques, so we can deliver reliable results even as models become increasingly complex.
AI RESEARCH
Cybersecurity AI driven by research and data
Behind the Vectra AI Platform is a team of security researchers, data scientists, and engineers who constantly study modern attacker methods and translate them into problems AI can solve. It’s how we equip you with the right model for every domain.
Our team of dedicated researchers continually uncover new and unknown attack vulnerabilities. They study and break down the latest methods, motivations, and behaviors attackers use to expose gaps, exploit vulnerabilities, bypass controls, steal credentials, and move laterally.
We get even more granular by determining the right data, math and AI/ML models to pinpoint attacker behavior by domain. Our security researchers map attacker methods in use across each specific domain, then collaborate with data scientists to determine the countermeasures needed to accurately detect those methods.

No single algorithm works for every problem. That’s why our researchers and engineers build highly specialized models for every problem — so you can trust the Vectra AI Platform to detect real attacker activity. We apply the right algorithm to solve each specific security use case including:
- Neural Networks
- DBSCAN
- Generative AI
- Logistic Regression
- K-Means
- Decision Trees and Random Forests
- LightGBM
- Boosted Trees
- XGBoost
- Multi-Dimensional Anomalies
- Support Vector Machines
- Heuristics
- And more…
AI Detections
Vectra AI detections surface real attacker behaviors
Different isn’t always bad
Thinking like an attacker means identifying what's malicious — not just what’s unusual.
Vectra AI detects what’s actually urgent
So your security team sees what matters.

Other solutions flag suspicious activity.
They miss actual attacks while generating thousands of alerts:
User logging into Azure AD while on vacation
Admin accessing new cloud workload for the first time
Beacon from a mobile app to a rare IP in AWS
Vectra AI detects real attacker behaviors.
We reduce hundreds of thousands of alerts to the few that matter:
Attacker using psexec from admin account
Phished Azure AD login spoofing normal user activity
High-privilege account used from new system
Over 100 AI-driven attacker behavior detections across network, identity and cloud
AI Agents
Vectra AI agents show you what's real and urgent
Our AI agents autonomously triage, stitch, and prioritize detections across network, identity, and cloud. This advanced approach is built on years of security research, data science, and innovation in agentic AI. It’s how we emulate analyst-level decision making for threat detection, investigation, and response.
150,000
events detected

Traditional Security Tools
1,000 alerts
Other cybersecurity AI stops here having only focused on detecting anomalies. It flags anything different.

Vectra AI
AI Triage
50,000 events
AI Triage separates normal network activity from behavior that’s likely to be malicious. It automatically investigates and resolves benign activities.
AI Stitching
1,000 events
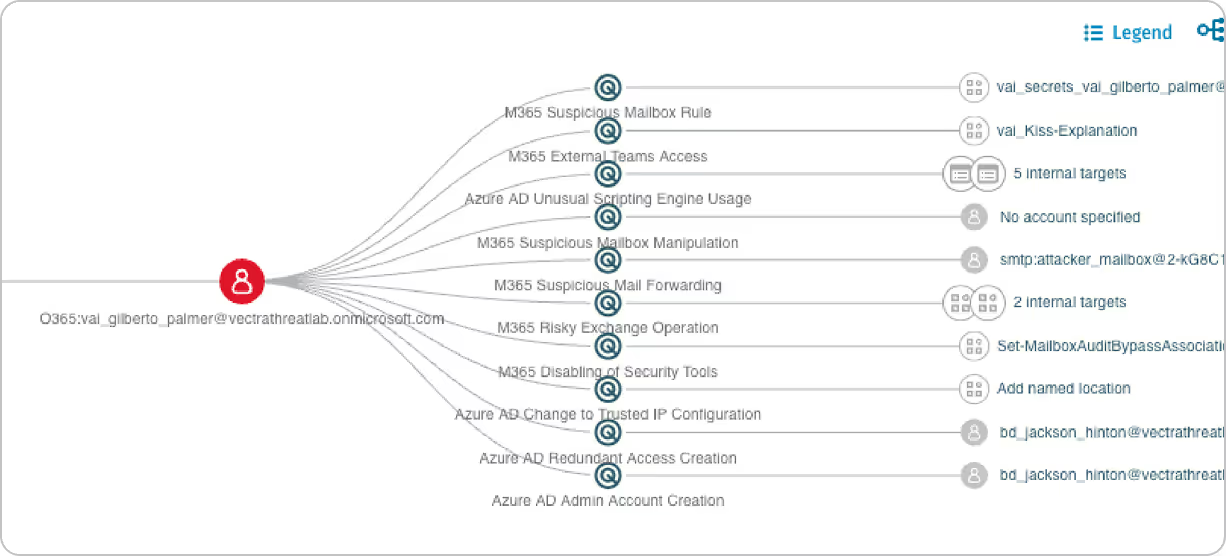
AI Stitching correlates behaviors across network, identity, and cloud to identify the original compromised account or device — creating a complete attack profile across domains.
AI Prioritization
5 alerts
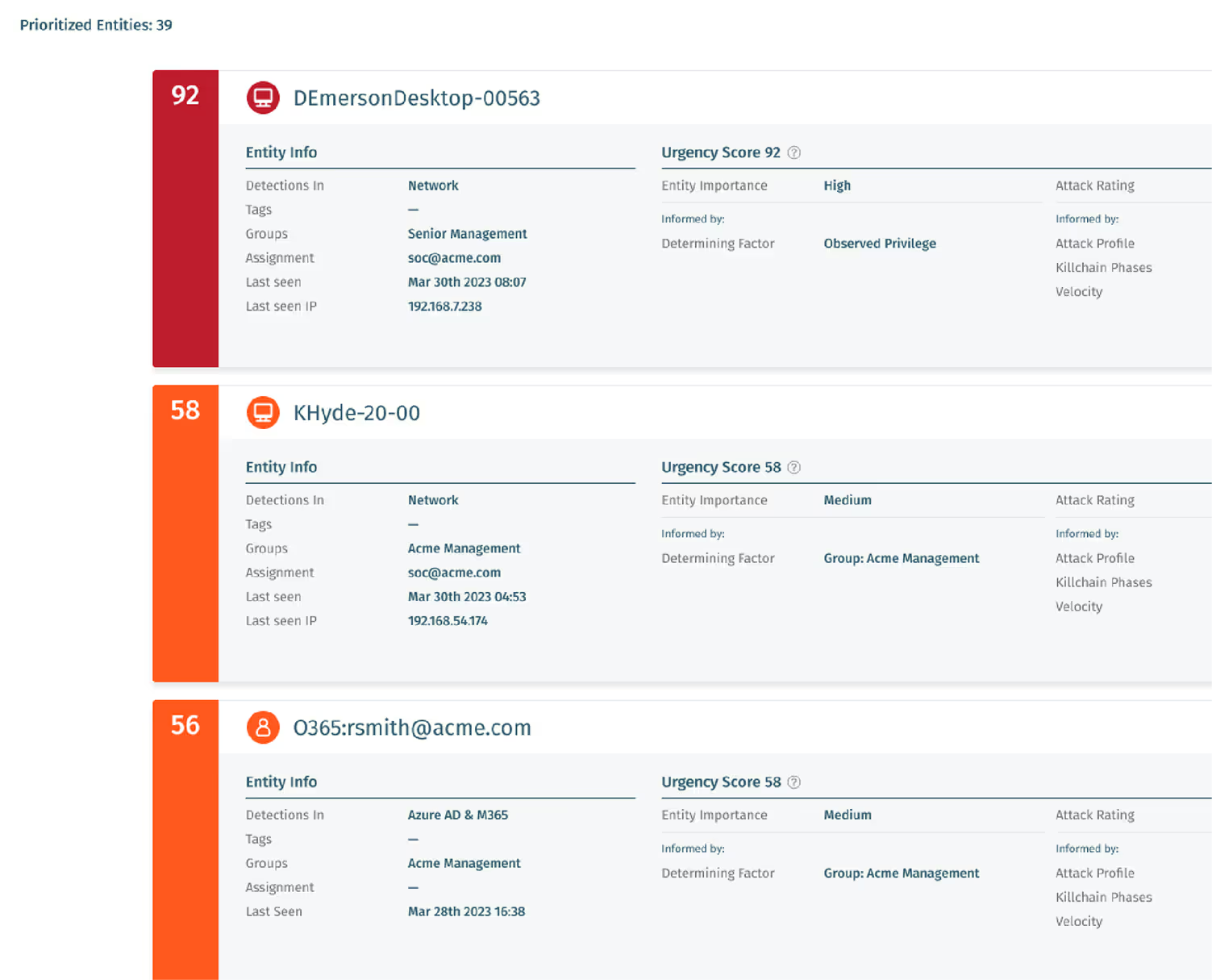
AI Prioritization delivers entity-centric urgency scoring based on attack profile, velocity, and techniques. This tells analysts which events are urgent and real to accelerate response.
AI Analyst
AI Analyst accelerates incident response for MDR customers by automating escalation workflows and investigative reporting.
Our AI agents autonomously triage, stitch, and prioritize detections across network, identity, and cloud. This advanced approach is built on years of security research, data science, and innovation in agentic AI. It’s how we emulate analyst-level decision making for threat detection, investigation, and response.
AI agents handle the busy work, putting you in control to stop attacks early
While AI agents triage, stitch, and prioritize real threats, your team stays in control — armed with deep visibility, instant context, and direct response actions through AI-enabled threat hunting and response.
AI-enabled threat hunting
See the full story behind every threat.
Answer critical security questions with 25+ enriched metadata types and 250+ contextual fields spanning network, identity, and cloud — augmented with host, account privilege, and threat context.
Use guided zero-query investigations to identify threats at speed.
Gain in-depth insights with Advanced Investigations providing easy access to AI-enriched metadata.
Reduce risk through expert-led threat hunts using pre-built searches and weekly guided hunts.

AI-enabled response
Accelerate and automate containment with targeted, integrated controls.
Isolate compromised hosts through EDR.
Disable attacker-controlled accounts in Active Directory and Entra ID.
Revoke attacker access with MFA re-prompt.
Block command-and-control traffic instantly at the firewall to cut off adversary communication.
No more digging to find out:

Which high important assets have active detections?

Which compromised entities need to be investigated?

How did the attack start? Were there attempts elsewhere?
Quickly detect, investigate, and respond to potential attacks
Detect
See threats ranked by urgency score in a single, unified view — powered by Attack Signal Intelligence™.
Detect with Vectra AI
Investigate
Deep diving into detections has never been easier with instant and advanced investigations.
Investigate with Vectra AI
Respond
Stop attacks in minutes with native, integrated, and managed response capabilities.
Respond with Vectra AI
Hunt
Deep diving into detections has never been easier with instant and advanced investigations.
Hunt with Vectra AI
Discover
Monitor all your network and cloud threat surfaces in one dynamic dashboard.
Discover with Vectra AI
See what matters. Not just what’s different
Our advanced AI connects the dots of various threat behaviors as attackers move across modern networks. It surfaces truly malicious activity — not just noise.
60%
less time assessing and prioritizing alerts.
35
AI patents
150+
AI models
12
MITRE references


40%
more SOC efficiency.
>90%
Coverage of relevant MITRE and ATT&CK techniques
85%+
alert fidelity
FAQs
Cybersecurity AI for the modern network:
Frequently asked questions
How does Vectra AI use machine learning for cybersecurity?
Vectra AI applies ML to cybersecurity in a domain-specific, behavior-centric way. Unlike traditional anomaly detection systems that flag anything unusual, Vectra's ML threat detection models are purpose-built to identify attacker behaviors across network, cloud, and identity.
Machine learning is deeply integrated into Vectra AI’s detection engineering process, which aligns each model with real-world attacker techniques. These models are trained on high-fidelity behavioral data and tested against diverse attack scenarios. This ensures a high signal-to-noise ratio that minimizes false positives while surfacing truly malicious activity.
With more than 170 AI models and 36 AI patents, Vectra AI detects lateral movement, account compromise, and command-and-control communications using comprehensive strategies including attacker behavior modeling AI and behavioral analytics.
How does real-time AI-based threat detection reduce cybersecurity alert fatigue?
Our AI reduces SOC alert fatigue by replacing generic anomaly alerts with prioritized, correlated threat signals. Vectra AI’s system uses a triad of AI-powered tools — AI detection, AI agents (triage, stitching, and prioritization) — to whittle down hundreds of thousands of alerts to just a few high-fidelity signals.
- AI triage automatically investigates and resolves benign modern network activities.
- AI stitching correlates threat behaviors across domains (network, identity, cloud) to form cohesive attack narratives.
- AI prioritization AI ranks entities based on attack context and entity importance.
This approach drastically reduces analyst workload, improves mean time to detection (MTTD), and enables proactive incident response.
What role does AI/ML play in modern cybersecurity?
In modern cybersecurity, AI and ML are indispensable for keeping up with the speed, volume, and sophistication of modern attacks. Vectra AI advances this paradigm by delivering:
- AI-powered attack signal correlation to unify threat signals across hybrid cloud environments.
- AI in MITRE ATT&CK mapping to provide over 90% coverage of relevant TTPs.
- Zero-day threat prevention by detecting the intent behind actions, not just known signatures.
By modeling attacker behavior rather than chasing static indicators, Vectra’s ML-driven approach supports use cases like insider threat detection AI, lateral movement detection with AI, and behavioral fingerprinting — all crucial for operating in dynamic hybrid environments.
What is the role of Vectra AI Detections in identifying advanced threats?
Vectra’s AI Detections are specifically engineered to focus on real threats — not just anomalies. They’re trained to detect behaviors consistent with attacker goals such as credential theft, lateral movement, privilege escalation, and data exfiltration.
- Domain-specific threat detection models ensure the detection logic is tailored for network, cloud, identity, and SaaS systems.
- Threat detection explainability is built-in, with context and prioritization to show why each alert matters.
- Detections are mapped to MITRE ATT&CK, helping security teams understand where in the kill chain the attacker resides.
How does Vectra AI integrate with existing SIEM platforms and SOC workflows?
The Vectra AI Platform is engineered specifically to support SIEM integration for AI threat detection, connecting with major SIEM platforms through robust APIs and pre-built connectors. Rather than flooding your existing systems with thousands of generic alerts, our platform transforms your SOC workflow automation by delivering investigation-ready incidents with complete attack narratives and behavioral context.
Our security platform deployment options adapt to any environment — whether you're running on-premises infrastructure, cloud-native architectures, or hybrid setups. The automated incident response workflow capabilities integrate directly into your existing processes, dramatically reducing analyst triage time while accelerating threat response across your entire security stack.
How does Vectra AI ingest and correlate cloud service logs to detect threats?
Vectra AI ingests telemetry from key cloud and identity platforms like AWS, Azure AD, Azure and Microsoft 365, and uses purpose-built AI models to transform this raw data into meaningful threat signals. These logs — whether authentication events, access tokens, or API calls — are continuously processed by AI engines that understand attacker behavior in cloud-native environments.
- Domain-specific AI models are trained on behavioral baselines within each cloud platform. This allows them to detect actions that deviate from normal user, role, or system behavior — such as suspicious logins, privilege escalations, or unusual access patterns.
- Our AI automatically correlates detections from cloud, identity, and network, forming a unified narrative of an attack as it unfolds across systems. This enables security teams to see the full scope of compromise (such as from an anomalous Azure AD login to a lateral movement in AWS).
- Once ingested, signals are enriched with context such as user privilege level, device identity, and organizational role. Our AI then applies prioritization logic based on risk factors, so only the most urgent threats rise to the top.
This approach ensures comprehensive coverage of multi-cloud environments, reduces alert volume, and allows defenders to see and stop malicious activity that spans across different cloud services and user identities.
Can Vectra AI scale with enterprise environments?
Yes. The Vectra AI Platform provides comprehensive threat detection for the modern network. Our enterprise threat detection scalability processes millions of entities daily while maintaining precision.
Our multi-cloud visibility with AI correlates threat signals across your entire digital ecosystem, providing unified threat detection regardless of infrastructure complexity. In fact, this increased data volume actually enhances our AI's effectiveness — more entities mean richer behavioral baselines and more accurate detection. Our automated SOC alert triage processes massive data volumes while delivering the critical high-fidelity alerts that matter, typically reducing alert volume by more than 90% while improving detection accuracy.
Resources







