Vectra AI Platform
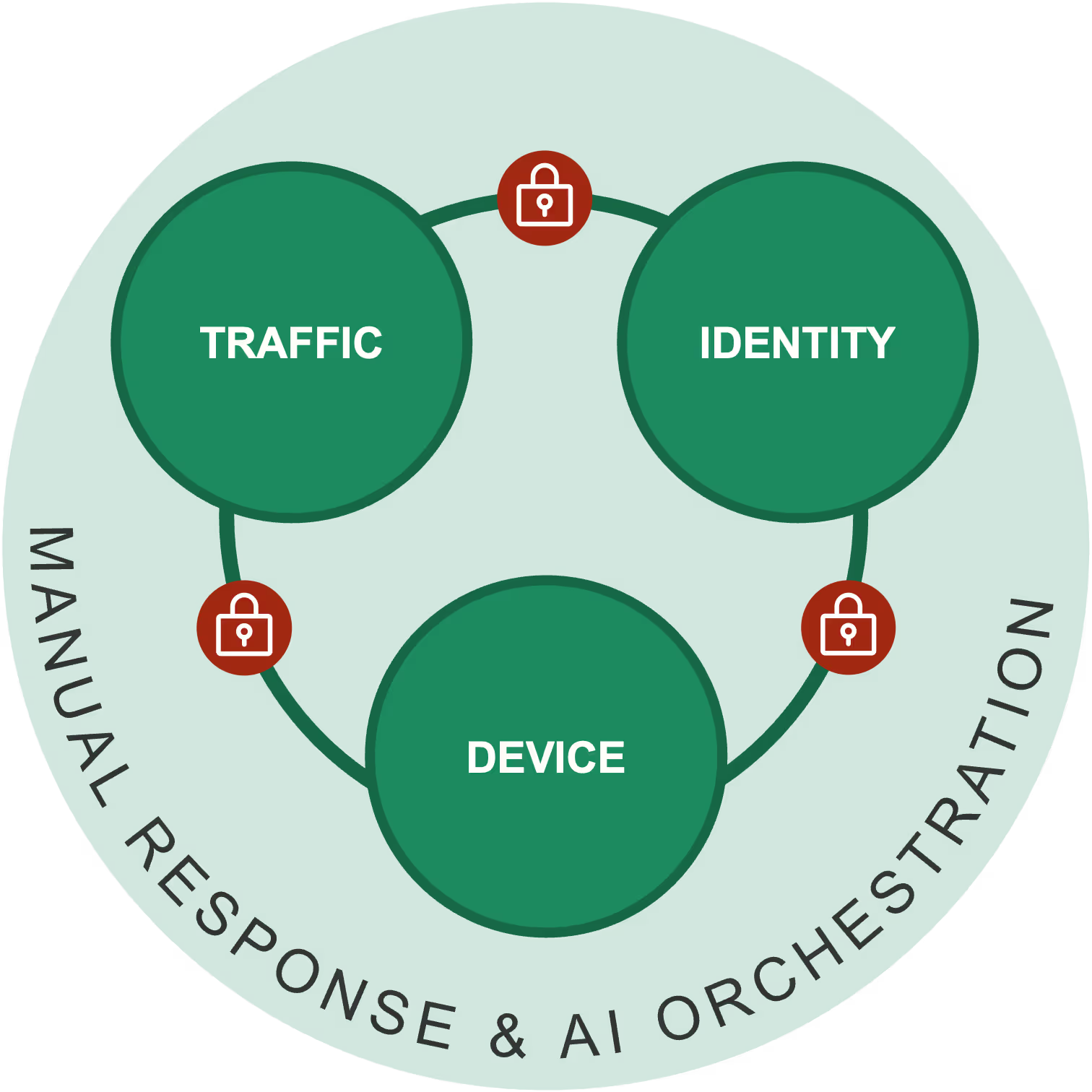
360 Response: Enforced control across identity, devices, and network traffic
Decisive containment during active attacks. Lockdown compromised identities, isolate devices, and block attacker traffic using high-fidelity detections.

Demo video
See 360 Response in action
Identity Lockdown
Watch Identity Lockdown automatically shutting down compromised identities.
- Compromised identity detected
- Active sessions revoked
- Password reset enforced
- Attacker access removed
Device Lockdown
See Device Lockdown isolating compromised endpoints before they move.
- Compromised device identified
- Host isolation triggered
- Lateral movement blocked
- Endpoint removed from play
Traffic Lockdown
View Traffic Lockdown cut off attacker communication at the firewall.
- Risky host added to blocklist
- Firewall enforcement applied
- Command-and-control blocked
- Exfiltration paths cut off
WHY VECTRA AI
360 Response:unified containment for hybrid attacks
Most tools try to stop attackers by disrupting a single connection, with actions like TCP resets. It sounds effective. It isn't enough.
360 Response converts Vectra AI’s attack signal intelligence into precise, enforced actions wherever attackers operate in your hybrid environment:
Identity Lockdown
Account containment across AD and Entra ID
- Disable or restrict compromised accounts
- Invalidate active sessions and force reauthentication
- Support password reset workflows to remove stolen credential advantage
Result
Attackers lose their identity foothold in across on-prem and cloud environments.
Device Lockdown
Host and endpoint containment using your existing EDR
- Isolate compromised hosts from the network
- Stop lateral movement and data staging on the device
- Triggered manually or automatically from high-confidence detections
Result
The endpoint the attacker depends on is removed from play.
Traffic Lockdown
Network containment enforced by your firewalls
- Add risky host IPs to a Vectra managed IP blocklist
- Let firewalls subscribe to that list as an external threat feed
- Block all traffic from those sources according to your policies
Result
Command-and-control, exfiltration, and internal pivoting are cut off at the network layer.
All three layers work together, driven by the same AI signal, from the same analyst experience.
approach
What is the 360 Response workflow?
Detect
- Vectra AI analyzes behavior across identity, cloud, SaaS, and network, and scores entities with urgency and importance
Decide
- High confidence threats reach 360 Response. Policies define when actions are manual, and when they are automatic
Lockdown
- Identity Lockdown removes attacker access to identities
- Device Lockdown isolates compromised endpoints
- Traffic Lockdown blocks communication at the firewall
Contain
- Attack paths are cut at multiple layers in minutes, not hours
Release and improve
- Lockdowns expire on a set schedule or are lifted by analysts, and the data feeds directly into reporting and resilience metrics
OUTCOMES
How does 360 Response put defenders back in control?
With 360 Response, defenders move from hoping disruption is enough to knowing containment is enforced.
You get
- Real control across identity, host, and network
- Containment you can explain and prove to your leadership
- Automation that targets only high confidence threats
- Response that scales without adding additional manual work
Your leadership sees
- Fewer incidents that progress
- Faster containment times
- Stronger evidence of resilience and control across hybrid environments
360 Response turns every high-fidelity detection into a decisive action that stops attackers and shows that your team is in command of the environment.
FAQ
Top FAQs: 360 Response
What is 360 Response in the Vectra AI Platform?
360 Response is Vectra AI’s unified containment capability that enables security teams to stop active attacks across identity, host, and network layers. It is a core component of the Vectra AI Platform’s continuous control approach, transforming high-confidence AI detections into enforced response actions. 360 Response uses existing identity providers, endpoint detection and response tools, and firewalls to contain threats without introducing new agents or manual workflows. By coordinating containment across multiple layers, 360 Response helps organizations regain control during active compromise and reduce the risk of escalation in complex hybrid environments.
How does 360 Response support continuous control during an active attack?
360 Response supports continuous control by enabling fast, coordinated containment while a hybrid attack is in progress. It applies response actions across the most abused layers of the hybrid environment, including identity, endpoints, and network traffic. When high-confidence threats are detected, 360 Response can trigger identity, device, and traffic lockdowns either manually or automatically. This coordinated response cuts off attacker access, lateral movement, and communication paths at the same time, helping security teams act decisively and maintain control as attacks unfold rather than reacting after damage has occurred.
How does Identity Lockdown help stop identity-based attacks?
Identity Lockdown helps stop identity-based attacks by disabling or restricting compromised user accounts in Active Directory and Entra ID. When triggered, it can revoke active sessions and support password reset workflows to invalidate stolen credentials. This prevents attackers from reusing valid identities to access cloud services, SaaS applications, or on-premises resources. Identity abuse is one of the most common escalation techniques in modern attacks, and Identity Lockdown removes that advantage quickly. By enforcing identity containment early through identity threat detection and containment, security teams reduce the likelihood of privilege escalation and cross-environment pivoting.
How does Device Lockdown isolate compromised devices without adding operational overhead?
Device Lockdown isolates compromised devices using native integrations with endpoint detection and response tools already deployed in the environment. When a device is locked down, it is removed from the network, preventing lateral movement and stopping attacker activity from that device. 360 Response does not require an additional endpoint agent, which helps teams avoid added complexity or deployment friction. Device Lockdown can be initiated manually by analysts or automatically for high-confidence threats, enabling fast containment while remaining consistent with existing security integrations with leading EDR platforms.
How does Traffic Lockdown enforce network-level containment?
Traffic Lockdown enforces network-level containment by blocking attacker communication through firewall-based controls. When a threat enters lockdown, its IP address is added to a Vectra-managed blocklist that firewalls consume as an external threat feed. Firewall policies then deny traffic from those IPs, preventing command-and-control, data exfiltration, and internal pivoting. Unlike connection resets, this approach enforces persistent, policy-driven blocking that attackers cannot bypass. Traffic Lockdown extends the value of Network Detection and Response (NDR) capabilities by turning detection into enforced action.
How does 360 Response fit into Vectra AI’s continuous control framework?
360 Response is one of five foundational components of Vectra AI’s continuous control framework, alongside proactive threat exposure management, value reporting, analyst experience, and managed services. Together, these capabilities help organizations reduce exposure before compromise, contain threats during active attacks, and prove resilience after incidents are resolved. 360 Response focuses on the response phase by delivering enforced containment across identity, host, and network layers. When combined with Vectra AI’s detection, investigation, and reporting capabilities, it enables security teams to demonstrate measurable improvements in control, resilience, and operational maturity.
Resources
You might also be interested in....
NEXT STEPS
Gain the control, clarity, and coverage you need to stop hybrid attacks
360 Response delivers true control across identity, host, and network so attackers lose every path they rely on. Paired with the Vectra AI Platform’s extensive attack surface coverage, high-fidelity signal and unified investigation experience, your team gets control to enforce containment across your entire hybrid environment.