Integration decreases cost and increases effectiveness. For this reason, Vectra is adaptive by design. Everything we do considers how to help our customers be more efficient and faster at fighting attacks. Sometimes it involves determining where to deliver sophisticated threat intelligence beyond the Vectra. Working with Splunk is a great example of this integration.
According to Gartner, “The goal is not to replace traditional security event information management (SIEM) systems, but rather to provide high-assurance, domain specific, risk-prioritized actionable insight into threats, helping enterprises to focus their security operations response processes on the threats and events that represent the most risk to them."
The Vectra App for Splunk provides an extraordinary range of threat intelligence to the Splunk machine-data repository, including detections of unknown malware and attack tools, threats that hide in common apps and encrypted traffic, and in-progress threats in every phase of the attack kill chain.
Vectra also precorrelates threat events to specific physical hosts to enable faster threat investigations and incident response. Splunk captures, indexes and correlates Vectra threat detection data in real-time, making it available in a searchable repository where you can generate graphs, reports, alerts, dashboards and visualizations.
The Vectra App for Splunk brings all Vectra detections directly into the Splunk ES dashboards, allowing them to be easily integrated into existing security operational workflows.
Additionally, it allows security teams to easily correlate Vectra host and detection information with intelligence from other systems, such as URL filtering solutions and firewalls. A link back into the Vectra user interface allows for a seamless transition to drive prioritization and workflow.
Hosts ranked by risk
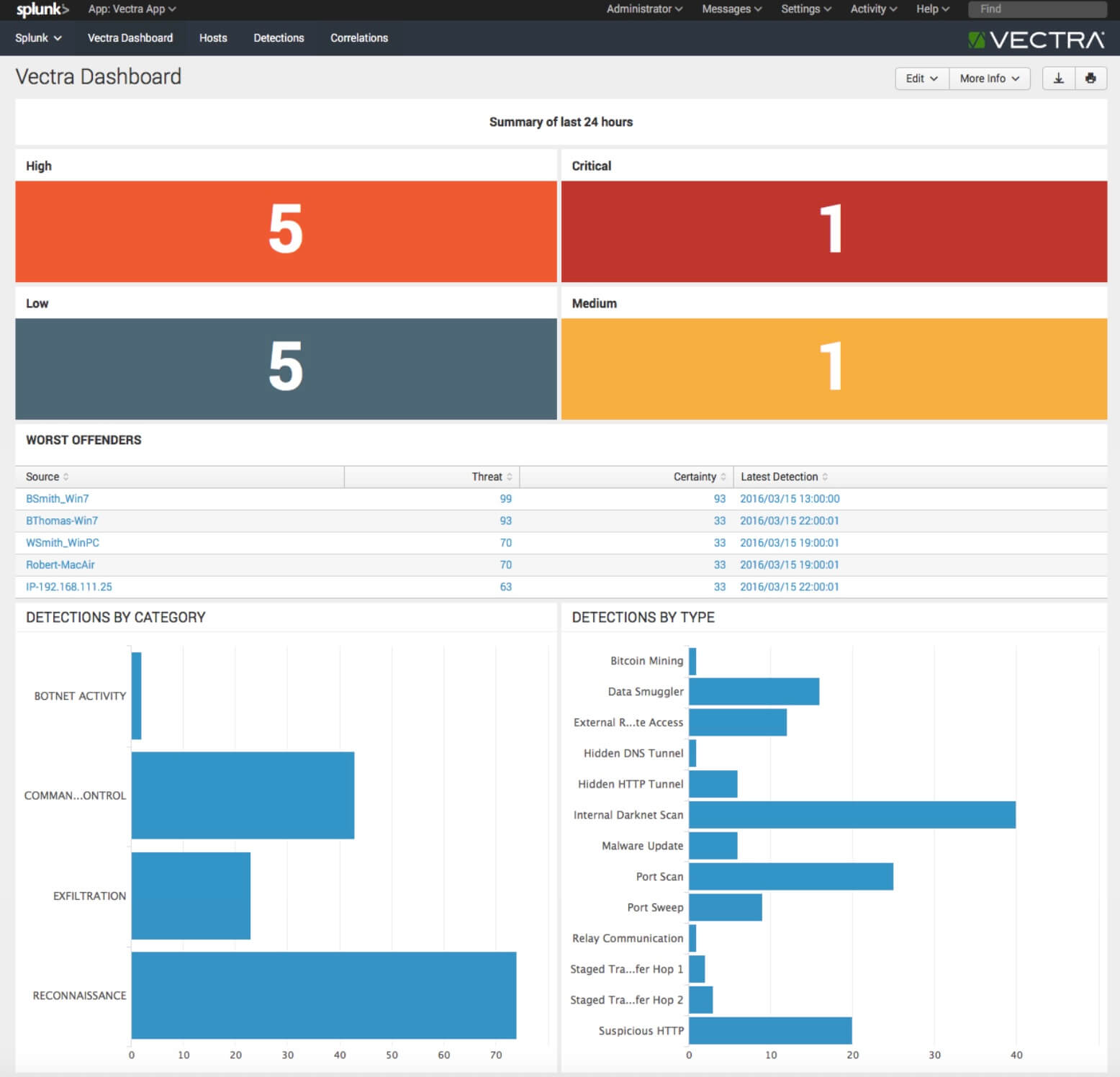
The Vectra solution automatically associates all malicious behaviors to the physical network host—even if the IP address changes—and scores the host in terms of its overall risk.
The Vectra App for Splunk provides an interactive dashboard to quickly show the number of hosts classified as critical, high, medium, and low risk. These scores remove the need for analyst to manually investigate events, and vastly improve the time to respond.
Furthermore, drill-downs into each category in the Vectra App for Splunk redirect you to the host’s page and filter on that particular severity to help speed the investigation.
Visibility into threats across the kill chain
The Vectra App provides critical insight into specific threats as well as the progression of threats across the cyberattack kill-chain.
This visibility allows security teams to quickly distinguish opportunistic botnet behavior from the more serious targeted threats, and take action before data is stolen or damaged. Correlation rules pull additional context from other systems that integrate with the Splunk platform.
Correlation to other solutions
Vectra’s unique approach to detection allows security teams to detect threats that may have been missed by other solutions. The Vectra App for Splunk makes it easy to connect and correlate Vectra findings with other solutions.
The Vectra correlations page enables faster and deeper investigation into events by allowing security teams to correlate source and destination IP addresses from Vectra events with other events in Splunk.

