For years, some tools have claimed that sending a TCP Reset (RST) is enough to stop an attacker. It sounds simple: if something suspicious happens, break the connection. But modern attackers don’t behave in ways a reset can control. TCP RST is unreliable, easily bypassed, and can even disrupt critical business services. 
Why TCP resets fall short
A TCP reset is like slamming a door in an attacker’s face. But modern attackers? They just open another door—instantly.
How? They can:
- Ignore RST packets completely using a one-line firewall rule.
- Use encrypted tunnels, VPNs, and proxies where resets can’t be injected.
- Reconnect immediately from a new port or IP.
- Leverage tools, like Cobalt Strike, Sliver, Metasploit, and Havoc, that are built to resist or bypass resets.
Even when resets do work, they risk collateral damage like corrupting applications or disrupting environments using critical protocols such as BGP. The bottom line: TCP resets don’t stop attackers. They just momentarily inconvenience them.
By the time a reset is sent, the attacker may have already used the stolen credentials, moved laterally through your environment, established persistence, and accessed sensitive, business-critical data.
Resetting a single connection is like shutting one door while the intruder is already inside the building, opening new ones as they go. You’re not stopping the attack; you’re playing whack-a-mole. Modern defenders need a way to lock every door at once and keep them locked.
Learn more about the limitations of TCP reset here: https://support.vectra.ai/vectra/article/KB-VS-2644
The modern solution: Vectra AI’s 360 Response
Vectra AI’s 360 Response replaces fragile packet resets with real, enforced containment across the layers attackers actually abuse, which are identity, device, and traffic. This gives defenders the ability to shut down attacker actions everywhere they try to move.
360 Response locks every possible door through:
- Host Lockdown: Isolates compromised devices via EDR to stop lateral spread.
- Account Lockdown: Disables or restricts compromised user accounts in AD or Entra ID.
- Traffic Lockdown: Applies true firewall blocks that attackers cannot ignore, bypass, or reconnect around.
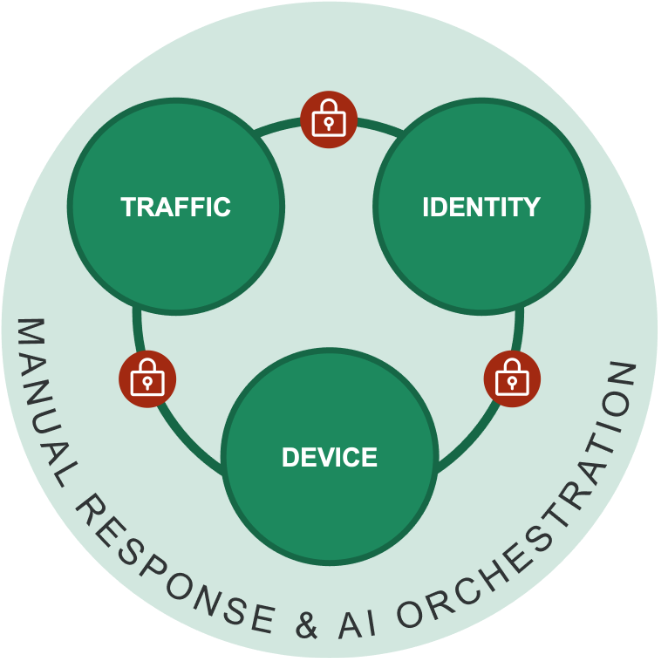
Instead of hoping a reset works, Vectra AI uses the customer’s authoritative enforcement tools to stop attackers decisively. Vectra’s AI detects the threat. 360 Response locks every door. The attacker loses control—and the defender regains it.
360 Response: from disruption to true control
TCP resets were never meant to stop cyberattacks, and today’s adversaries walk right through them. They can be ignored, bypassed, or nullified, and sometimes cause more harm than good. Vectra AI’s 360 Response delivers what resets never could: real, persistent containment that shuts down every path an attacker tries to take.
