In December 2025, CISA, the FBI, NSA, and multiple international partners published a joint advisory warning that pro-Russia hacktivist groups are conducting opportunistic cyber attacks against critical infrastructure organizations worldwide. The report focuses on attacks against operational technology and industrial control systems, including water, energy, and food production environments.
What makes this advisory particularly important is not the sophistication of the attackers. The report is explicit that these groups rely on basic, widely available techniques and often lack deep technical or engineering expertise. Yet despite this, they are still achieving operational disruption, forcing manual intervention, and in some cases causing physical impact.
In short: this report highlights that the real problem is not sophisticated exploits, but exposed systems, weak authentication, and poor visibility into how legitimate access is misused.
How the Attacks Unfolded
According to the report, pro-Russia hacktivist groups follow a repeatable and low-cost attack pattern that can be executed at internet scale.
The attacks follow a consistent sequence:
- Scan the internet for exposed OT-related devices, especially HMI or SCADA systems accessible over VNC
- Identify weak, default, or missing authentication
- Gain remote access using legitimate remote services
- Interact directly with HMI or SCADA interfaces
- Modify settings, change credentials, disable alarms, or force loss of view
- Capture screenshots or videos to post online and claim success
This activity does not rely on malware delivery or software exploitation. Authentication succeeds. Remote services function as designed. Interfaces respond normally.
Once access is established, attackers perform hands-on actions intended to disrupt operations or remove operator visibility. These actions include changing credentials to lock out operators, altering parameters and setpoints, suppressing alarms, or forcing systems into states that require on-site manual intervention. Throughout the intrusion, attackers often record screens or capture screenshots to publicize their access and exaggerate impact on social platforms.
While the advisory notes that attackers frequently overstate the severity of their actions, victim organizations still report real operational consequences, including downtime, labor costs, and recovery efforts.
The Advisory Exposes a Detection Gap
The report does more than document attack techniques. It exposes a fundamental detection challenge.
These intrusions rely on legitimate access mechanisms such as VNC, valid credentials, and interactive system interfaces. There is no exploit chain and no obvious policy violation until the impact is already visible.
From the perspective of many traditional security tools, this activity looks normal. Authentication succeeds. Network traffic follows allowed paths. Systems behave as expected.
The advisory ultimately underscores that reducing exposure, while necessary, is not sufficient on its own. Security teams also need the ability to detect when access that appears legitimate is being used in ways that are not. That detection gap is why these attacks continue to succeed.
What Vectra Detects Across This Attack
The below attack anatomy illustrates why these intrusions are so effective. At every stage, the attacker operates inside what looks like normal behavior.Prevention controls do not fail because they are misconfigured. They fail because there is nothing overtly malicious to block.
This is where the Vectra AI Platform becomes relevant.
Vectra AI focuses on behavioral detection across your entire hybrid environment (including Identity, Cloud, Network, IOT/OT), allowing security teams to see when access that appears legitimate starts behaving like an attack.
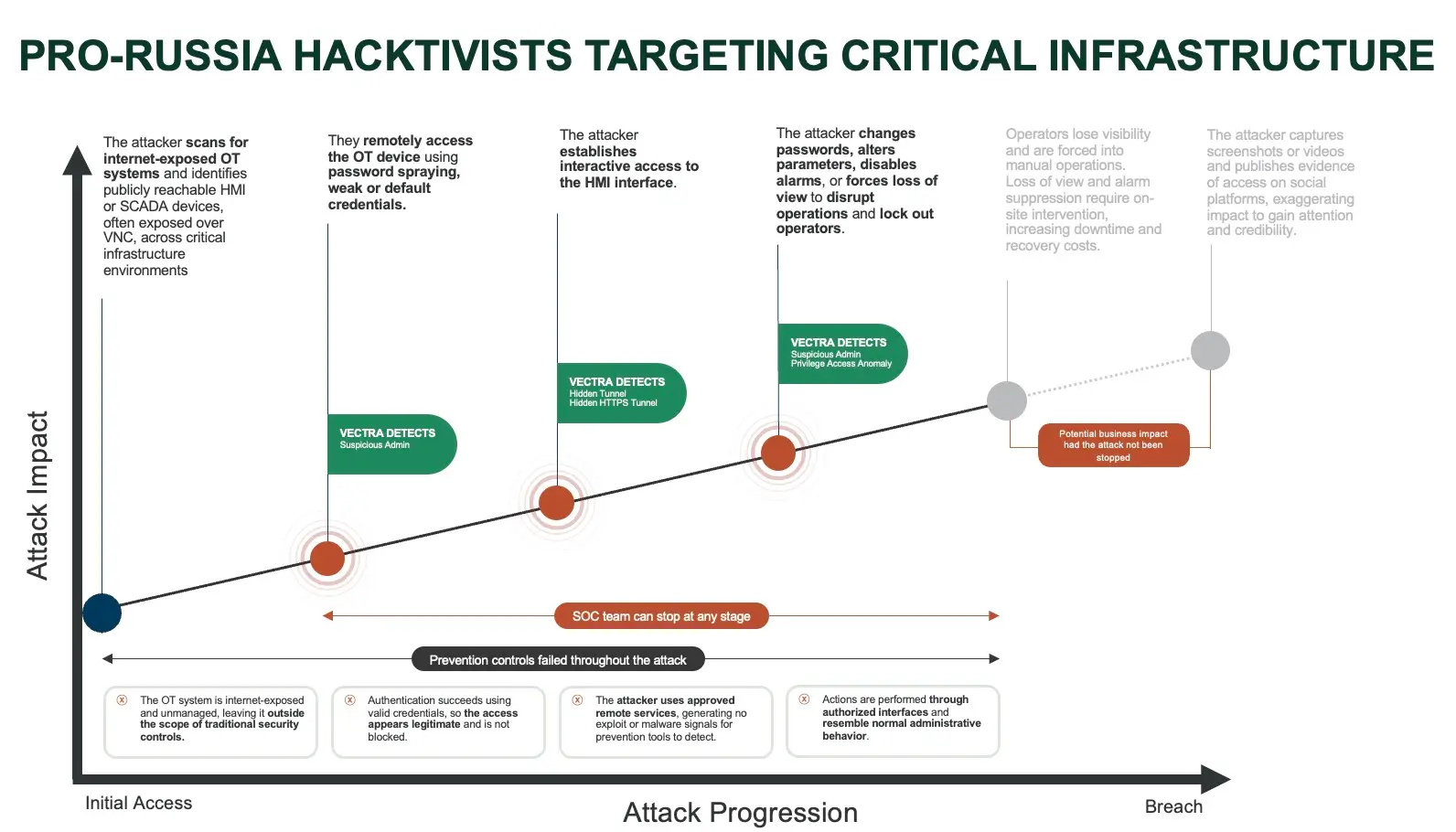
Early Access: Detecting Risky Administrative Behavior
When the attacker gains access to an exposed OT device using password spraying or default credentials, authentication succeeds. From a prevention standpoint, this looks like a valid login.
Vectra AI detects this stage by identifying suspicious administrative behavior, surfacing when an identity begins accessing systems or services in ways that deviate from its established patterns, even when credentials are technically valid.
This provides SOC teams with visibility before operational impact occurs.
Foothold and Interactive Access: Seeing What Other Tools Miss
Once interactive access to the HMI interface is established, the attacker operates entirely through approved remote services. There is no exploit and no malware to detect.
Vectra AI identifies abnormal remote interaction patterns, including unusual use of remote services and encrypted tunnels that do not align with normal operational behavior.
This is especially important in OT environments, where many systems are unmanaged and cannot run endpoint agents.
Operational Manipulation: Identifying Malicious Use of Legitimate Access
When the attacker changes passwords, alters parameters, disables alarms, or forces loss of view, every action is executed through authorized interfaces. Individually, these actions can resemble routine administration.
Vectra AI correlates privilege access anomalies and disruptive behavior patterns, ultimately identifying when an identity suddenly performs high-impact actions that are inconsistent with its normal role, timing, or sequence of behavior.
Rather than relying on single events, Vectra AI surfaces intent by connecting behavior across the attack progression.
Turning Visibility Into Action
The advisory makes it clear that low-skill attackers are succeeding because organizations lack visibility into how legitimate access is abused across hybrid environments.
Vectra AI’s value in this scenario is detecting misuse early enough for SOC teams to intervene, contain the activity, and prevent disruption from escalating.
If you want to understand how these attacks would appear in your own environment, and how early detection changes the outcome, get in touch to schedule a free security assessment.

