Security teams and red teams often approach threat simulations with complex playbooks and elaborate kill chains. In practice, though, attackers don’t need that level of sophistication. What we regularly see is how simple it still is to get in. Real-world intrusions rarely follow those scripted sequences, they exploit low-hanging fruit: weak configurations, leaked credentials, and unmonitored access points.
Initial access remains the simplest, most effective step in an intrusion. Understanding how attackers seize that first opportunity is what separates prevention checklists from genuine resilience.
The Modern Reality of Initial Access
Your environment is no longer a single perimeter. You’re securing an interconnected web of data centers, cloud platforms, SaaS apps, and remote endpoints. Each of these is an entry point, and adversaries know it.
Initial access typically happens through one of two paths:
- Technical exploitation: unpatched vulnerabilities, exposed services, or misconfigured assets.
- Identity-based compromise: stolen or abused credentials, infostealers, SIM swaps, or malicious federation setups.

Attackers don’t always need sophisticated malware or zero-days. In many cases, they find that credentials, tokens, or even VPN keys are for sale online. Entire underground markets exist where “initial access brokers” trade verified footholds into organizations, making it easier than ever for threat actors to skip the hard work of intrusion and jump straight into your environment.
Real-World Playbooks: How Attackers Do It
Attackers reuse what works. Here are a few common scenarios SOC teams should recognize:
1. Opportunistic misconfigurations
DC Healthlink was one of my biggest hacks, and it wasn’t even a hack. It was out in the open. There wasn’t anything complicated about it, it was just a public bucket. Completely open.
- IntelBroker*
Actors use search engines like SHODAN and scan for publicly exposed data stores or misconfigured cloud services. Once found, they exploit weak permissions or leaked access keys to gain control of assets that should never have been visible in the first place.
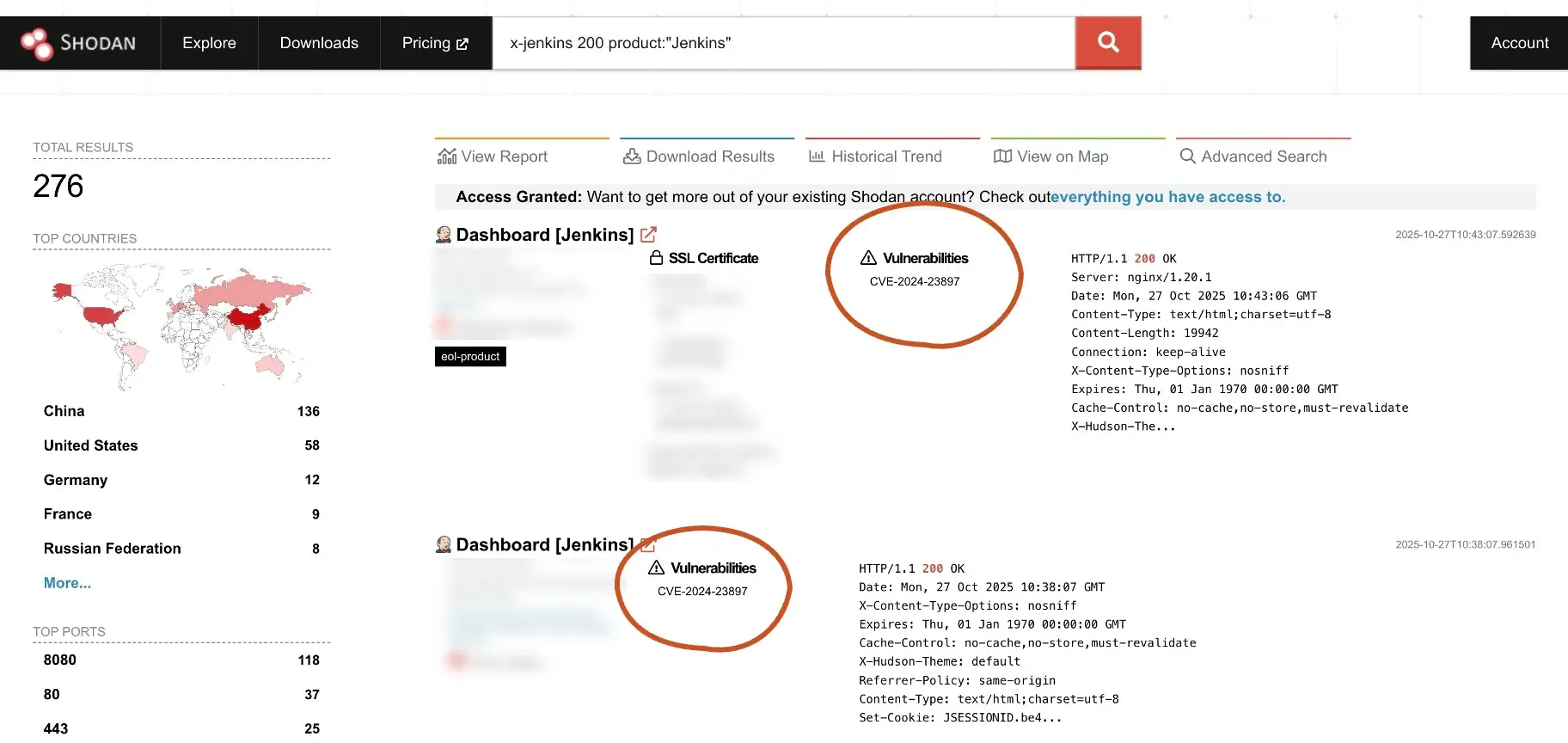
2. Supply-chain shortcuts
The Snowflake incident highlighted a growing risk: attackers using stolen contractor credentials harvested by commodity infostealers to reach enterprise data. Even if your defenses are strong, your partner’s laptop can be your weakest link.
I rat employees at home via spearphishing and spearmishing and use their work laptops, that’s how I hack MSP’s. Sometimes I rat their spouse which can be easier, then pivot to them.
- Ellyel8*
Another example is the recent NPM supply-chain exploit, where poisoned packages injected malicious code directly into development environments. The injected payload initially targeted cryptocurrency transactions, but quickly turned into self-replicating worm, currently being tracked as "Shai-Hulud," which is responsible for the compromise of hundreds of software packages.
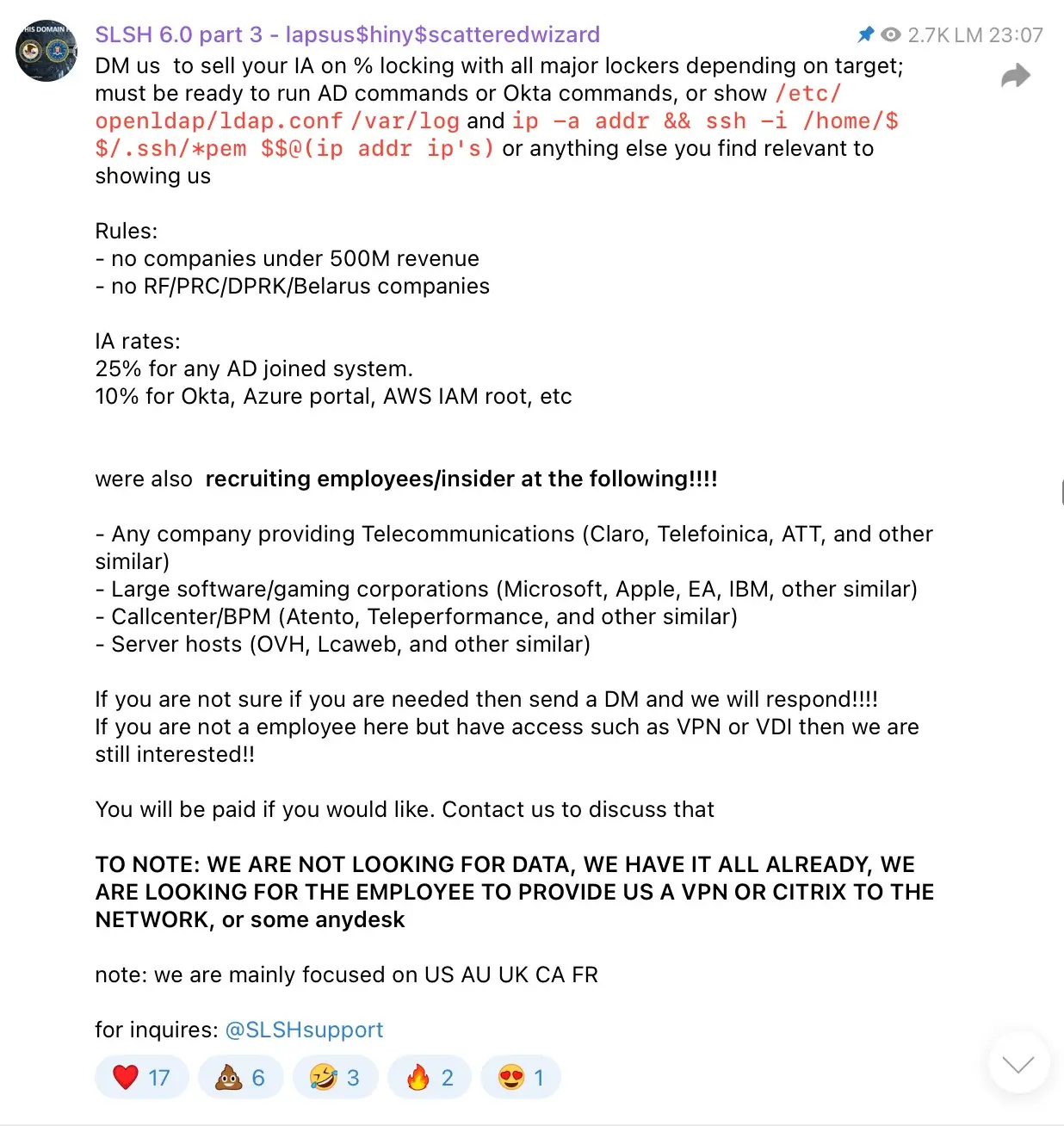
3. Identity hijacking and SIM swapping
Groups such as Scattered Spider exploit human trust. They target employees via SMS phishing and social engineering, clone phone numbers, and reset MFA tokens. From there, mailbox rules and federated trust abuse give them persistence. These groups also try to “recruit” employees/insider and will pay to get their credentials.
4. Nation-state stealth
Campaigns like Volt Typhoon rely on built-in tools and “living off the land” tactics. They capture registry hives, clear logs, and use PowerShell to stay invisible within legitimate traffic — bypassing most endpoint-based defenses.
Why Prevention Alone Isn’t Enough
Preventive controls (MFA, patching, EDR) are vital, but none are foolproof. Endpoints go unmanaged, credentials get reused, and logs can be tampered with. Attackers often disable or avoid agents altogether. Once an attacker gains entry, the question becomes: Can you see what they’re doing next?
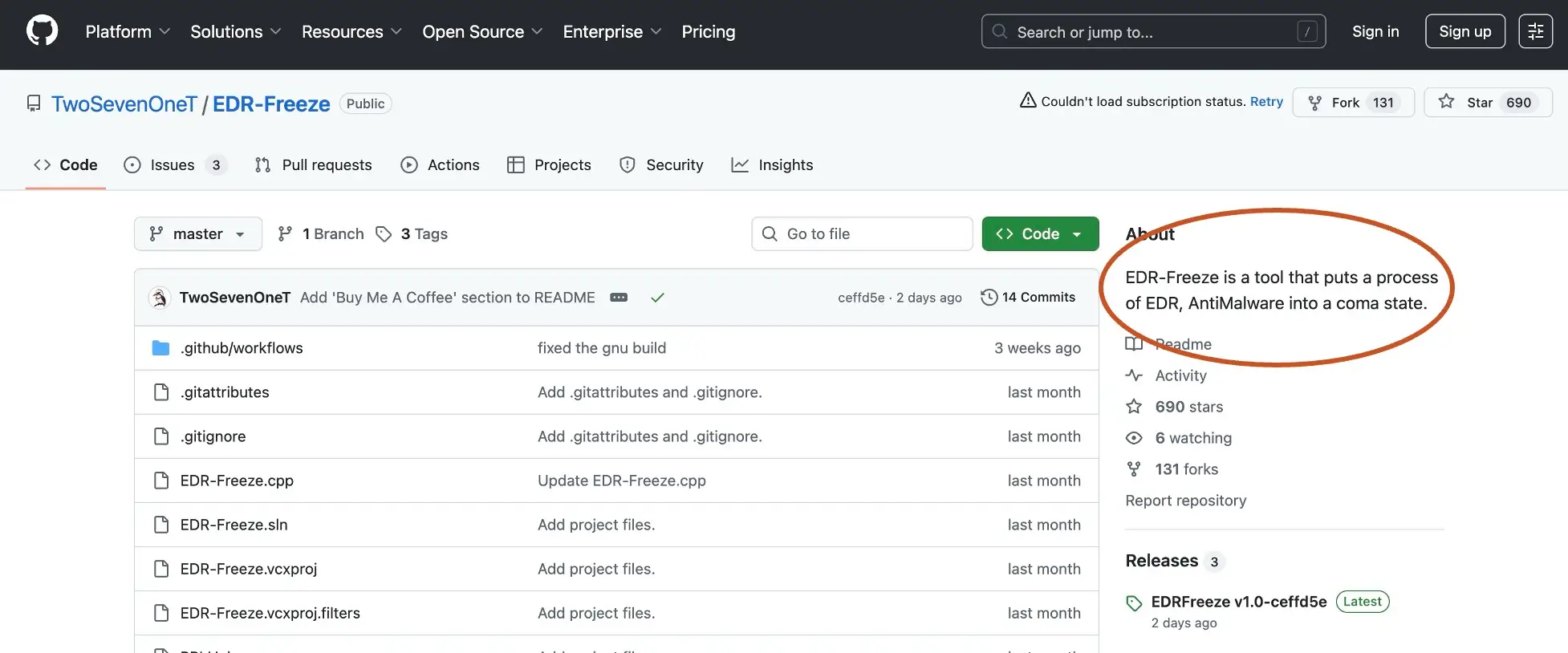
SOC teams need visibility that doesn’t rely solely on endpoints or log integrity. That’s where network and identity telemetry come in.
What Effective Detection Looks Like
Detection should center on behavior, not signatures. You can’t always stop an intrusion, but you can identify the attacker’s actions before real damage occurs.
Here are core principles:
- Agentless visibility: Deploy sensors that observe traffic even where EDR isn’t present — remote devices, unmanaged assets, or legacy systems.
- Identity context: Correlate authentication events with network flows. A legitimate login from a new geography or device shouldn’t go unexamined.
- Behavioral analytics: Track actions such as mailbox rule creation, privilege escalation, or federated trust changes.
- Evidence preservation: Assume logs may be wiped; use passive packet capture and network telemetry that attackers can’t alter.
- AI triage and prioritization: Automate detection of lateral movement patterns and high-risk behavior chains.
How the Vectra AI Platform Strengthens Detection
The Vectra AI Platform delivers agentless detection across network and identity layers, providing visibility attackers can’t evade. It continuously analyzes hybrid traffic — from on-prem to cloud and SaaS — and correlates it with identity behaviors to detect threats like credential abuse, tunneling, and privilege escalation.
Its AI-driven analysis cuts through alert noise, surfacing the behaviors that truly matter so your SOC can respond faster and with confidence. Instead of relying on logs the attacker may have deleted, you gain persistent insight into what’s actually happening in your environment.
Your Next Steps
You can’t control every credential or partner laptop, but you can control your ability to see attacker behavior.
To see how agentless detection reveals these early-stage intrusions, watch the first Attack Lab session on Initial Access and sign up for the next episodes on Persistence and Lateral Movement. Or take a self-guided demo of the Vectra AI Platform and explore how it detects attacker behavior across your hybrid environment.
---
*Quote from Vinny Troia’s book “Grey Area: Dark Web Data Collection and the Future of OSINT”

