Your hybrid environment is here to stay. Like most SOC teams, you’re likely adding more tools and managing more alerts than ever before in response to new use cases and technological advancements. At the same time, more tools generate more alerts, more false positives and noise that only adds more pressure while putting a heavier burden on your team — with the same number of hours to remediate them. We call this the “Spiral of More.”
Worse, if you can’t identify malicious behavior outside your coverage or have enough time to look at every alert, you can’t investigate, prioritize or even respond to each threat. Something’s got to give.

The “Spiral of More” gets even more real with expanding hybrid environments
Protecting your organization gets even more challenging as you continually expand your hybrid surface beyond the endpoint. The fact is, defending a hybrid environment is a responsibility that goes beyond legacy and even sophisticated endpoint solutions.
And of course, hybrid threat actors are more than happy to take advantage of your expanding hybrid environment — why wouldn’t they? It allows them to infiltrate your environment, escalate privileges, move laterally and progress their attacks undetected.
Hybrid attackers have room to roam

From an attacker’s standpoint, what’s not to like about an expanding hybrid threat surface? More cloud surfaces, more SaaS workloads, more identities, more room to run, hide and attack. We also know that threat actors will typically launch multiple attacks across hybrid surfaces, many of which will remain undetected by conventional solutions.
Undetected dwell time means undetected behavior, the opportunity for the attacker to scout and blend in with normal behavioral patterns to execute potential data theft, operational damage, ransomware — the whole nine yards.
That’s why securing your expanding hybrid environment isn’t just about your endpoint defense efficacy per se, but also, prioritizing security that protects your organization against hybrid threats that find exposure and ultimately compromise beyond the endpoint.
What’s more, it’s no secret that new hybrid attack TTPs are being developed and launched all the time. Threat actors do what threat actors do. Just have a look at all of the current attacker tactics and techniques observed in the MITRE ATT&CK knowledge base.
Five common hybrid attack TTPs
There are a handful of hybrid attack TTPs that attackers use quite often for one simple reason — they work. The good news is that once you have an idea of how they work, you can adapt security practices to stop them. To that end, below are five common hybrid attack TTPs that could threaten your organization without ever triggering or engaging your endpoint defenses. Let’s look at five methods real attackers use to find exposure beyond the endpoint.
The TTPs detailed below are snippets from the eBook: A Breakdown of Emerging Attacker Methods — download it for free and get the full insights about each attack including how to prioritize each post-compromise technique in your defense.
1.
MFA Bypass: MFA (multi-factor authentication) should be utilized by all organizations as an effective way to help prevent unauthorized account access if a password has been compromised, however, attackers still work to expose identities elsewhere.
Hybrid attacker usage: The threat actor Lapsus$ is a well-funded cybercrime group that focuses on ransomware and data with techniques in ransomware playbooks. Lapsus$ uses compromised credentials, in some cases by purchasing VPN access in order to bypass MFA. They may attempt to connect to an endpoint, conduct network recon, move laterally over RDP (remote desktop) and escalate local privilege. After bypassing MFA, reports show Lapsus$ going after privileged credentials, accessing Azure AD (now Entra ID), M365 and SharePoint as they work towards exfiltration. Stopping this sort of attack requires the ability to prioritize post compromise attacker methods.
Here's an easy way to calculate your organization’s identity exposure risk. Vectra Identity Exposure Calculator.
2.
Spear Phishing: A common technique where attackers use information that may be of interest to a group or individual as bait, so the target takes action by opening an attachment or clicking on a link — ultimately exposing their organization.
Hybrid attacker usage: Threat actors such as Lazarus, a state-sponsored North Korean cybercrime group that has a history of targeting pharmaceutical firms for patent theft has also been associated with high-profile attacks such as the 2014 Sony Pictures breach and using Log 4j Exploits to capitalize on a remote code execution vulnerability. Reports show Lazarus gathering employee information from LinkedIn accounts and then using WhatsApp to hide in encrypted traffic and bypass prevention security to compromise a corporate laptop. From there a potential progression could be anything from gaining data center access or installing command and control (C2) for persistent access to move laterally. Early detection and prioritization of attacker activity and behavioral patterns are critical for your security team to stop a similar attack from progressing.
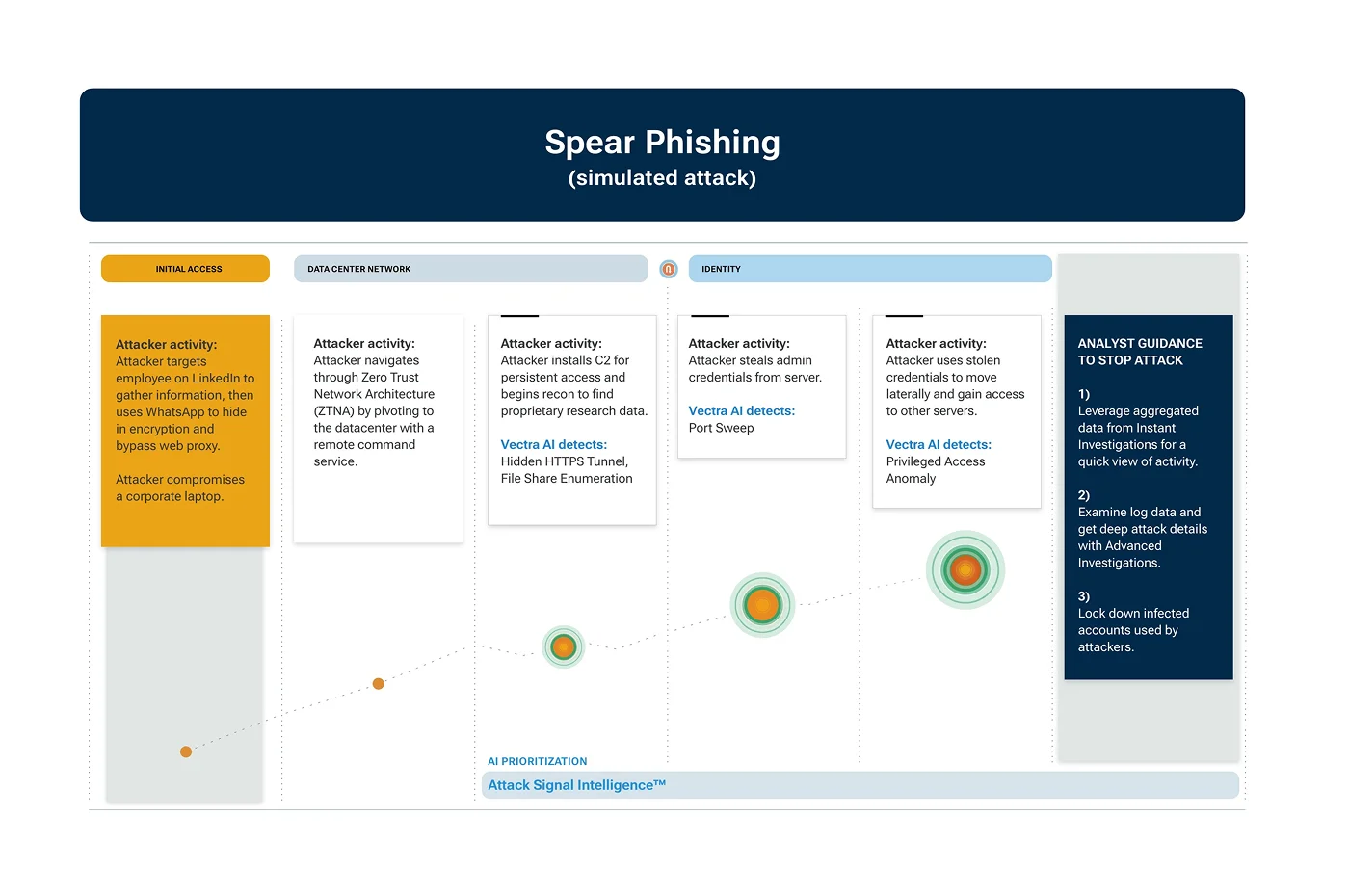
3.
Living Off the Land (LOTL): A tactic commonly used to blend in with normal network activity and operate discreetly, hybrid attackers leverage LOTL techniques to progress across environments and dwell longer post compromise.
Hybrid attacker usage: Volt Typhoon, a Chinese state-sponsored threat actor has been active since 2021 with targets including small home office network equipment such as routers, firewalls and VPN hardware. Volt Typhoon focuses on gathering user credentials to gain and maintain access without being detected for as long as possible through a variety of LOTL techniques. Once inside, tactics include but aren’t limited to command and control (C2) and recon techniques to gather information. An integrated attack signal with behavioral detection and AI-driven prioritization are key to stopping this type of attack.
How do command and control (C2) techniques work?

4.
Credential Stuffing: Attackers are always looking for ways to authenticate — and stolen credentials allow them to do that. Credential stuffing is a brute force technique that can occur when attackers gain user credentials (possibly when they’re dumped and/or sold online after a compromise) and use automated tools to help authenticate and gain access. Because credential stuffing usually means multiple authentication attempts are seen, there’s an opportunity for security teams to detect failed login attempts with the right tools in place.
Hybrid attacker usage: The Vectra MXDR team recently responded to an attack where a Russia-based attacker gained stolen credentials and made multiple unsuccessful sign-on attempts to authenticate. The threat actor eventually gained access via a US-based VPN and quickly moved laterally to access SaaS systems. Again, an integrated attack signal to detect and prioritize attacker behavior post compromise along with a response plan is the key factor to stopping this kind of attack.
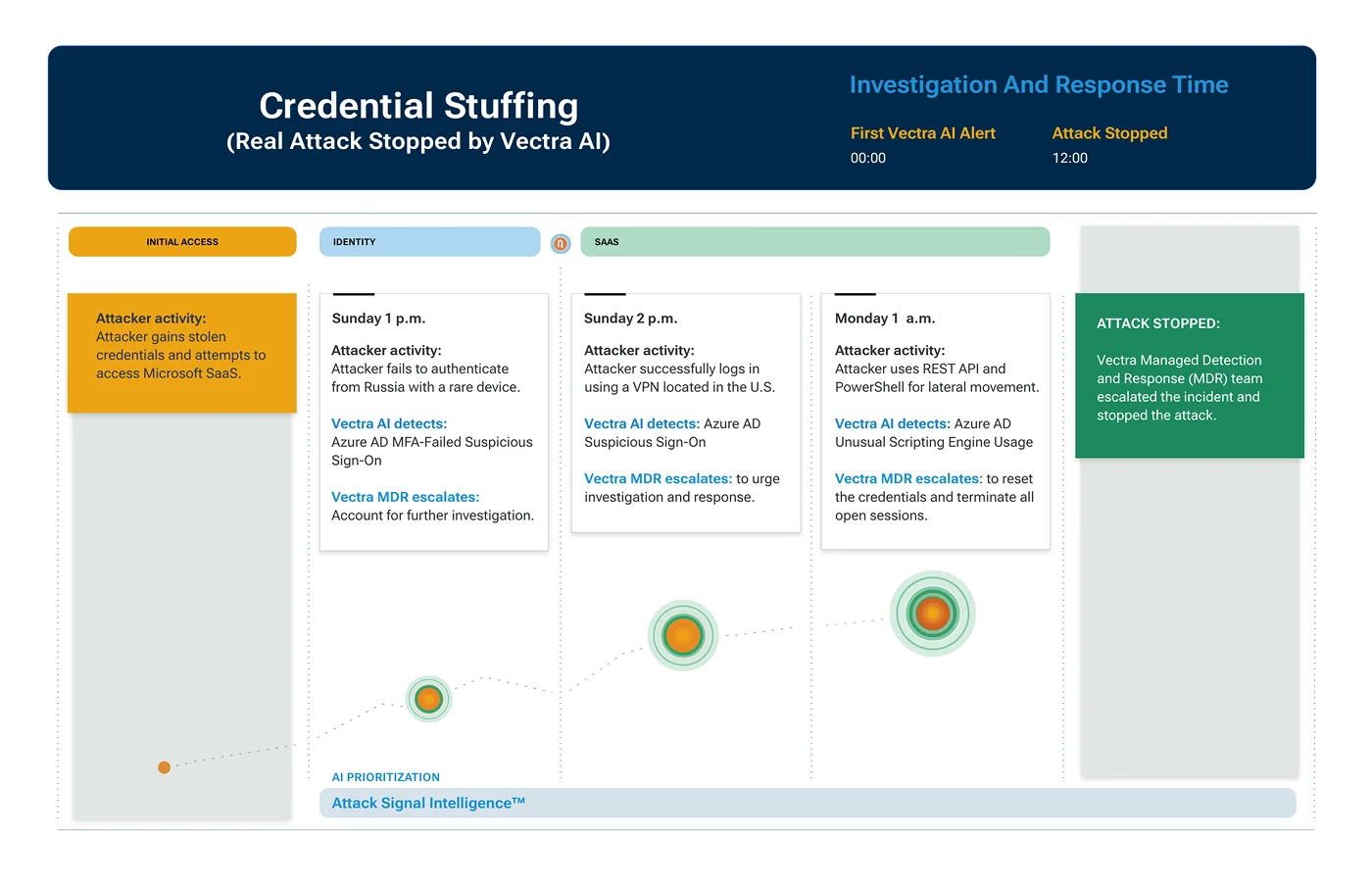
5.
Zero-Day Exploit: One of the common ways attackers will always look to expose hybrid environments is by attacking systems with an unidentified or unpatched vulnerability. To take it a step further, if a vulnerability is unknown or exists without an existing patch — attackers utilizing the vulnerability are more likely to succeed in their attack.
Hybrid attacker usage: Zero-Day vulnerabilities are beyond your typical IT coverage when they go unpatched or unknown. When this occurs, attackers have an easy route to exploit them and then compromise your hybrid environment, steal data or progress towards a target. Due to the unknown nature of a Zero-Day vulnerability, prevention security measures won’t detect an attacker leveraging the flaw — further highlighting the need to detect and prioritize attacker behavior that’s already active across your systems before damage occurs.
See exactly how a zero-day vulnerability can be used by hybrid attackers in the Vectra AI Threat Briefing: Hybrid Cloud Attacks:
How to defend against hybrid attacks that go beyond the endpoint?
In each attack scenario described above and detailed in the eBook, a successful defense includes three crucial pieces:
Coverage: Hybrid attackers don’t just try to expose one surface, which means your attack signal must span across all hybrid attack surfaces.
Clarity: An integrated AI-driven attack signal can detect and prioritize post compromise attacker methods, so your team knows what’s malicious and which events need attention.
Control: One of the attack examples showed how a credential stuffing attack was stopped by a managed detection and response team. The key is having 24x7x365 response controls whether that’s managed in-house or by an external team.
Every environment presents a unique set of challenges for defenders, but stopping attackers doesn’t have to be overly complicated. In fact, we know hybrid attackers will try to exploit existing security tool weaknesses, attack across multiple surfaces, try to progress by hiding in normal activity, use stolen credentials and leverage any other means possible — so defenders just need to make sure they have a plan that enables them to prioritize post compromise activity.
Don’t forget to download the free eBook: A Breakdown of Emerging Attacker Methods to see how security teams are successfully prioritizing post compromise attacker behavior. Or take a look at the related infographic.

