The modern-day organization is a cumulation of multiple technologies, systems, and machines which can be called a modern network. There are many complexities with a modern network so to better visualize and understand it, think of a modern network as a walled, medieval city.
The wall represents a firewall, protecting the traditional perimeter of the city. The gates, guard towers, and moat along the city walls are like endpoints. Inside, people like farmers, merchants, and scholars represent users, each with their own identifying factor. Embassies and merchants who are from this city but work in other cities are your remote workers. Buildings like farms or banks stand for different systems, servers, or machines. The general store holds tools they use, like Microsoft Word, Excel, and even a smart helper called Copilot. Some buildings float in the clouds—those are cloud servers. Finally, the roads and paths that connect it all represent the modern network.
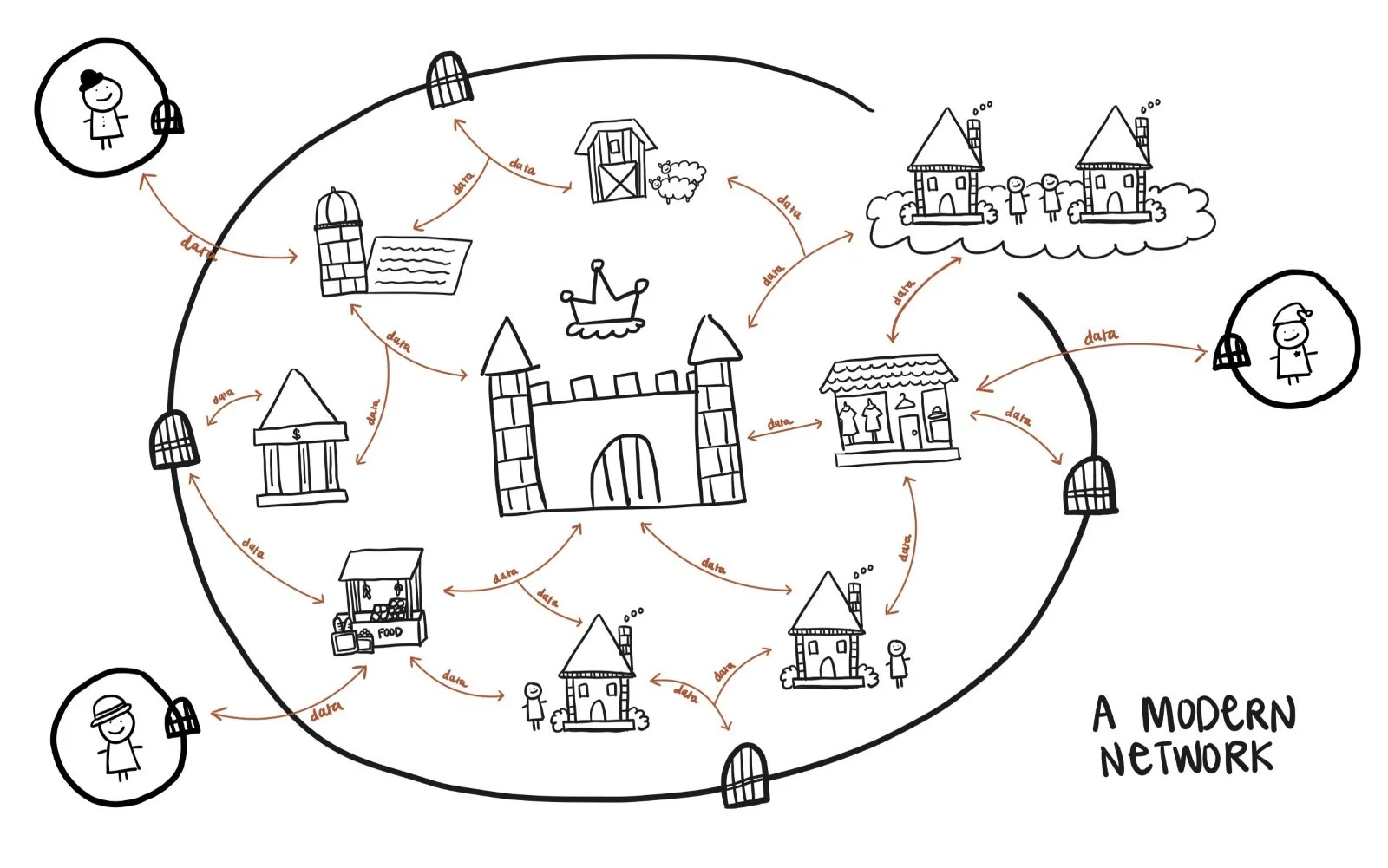
This walled city is incredibly rich in the commodity that runs the world – data. And the ripest, highest quality data is housed in the castle or in other words, the crown jewels.
An attacker would be interested in infiltrating this city to harvest the commodity, wreak havoc, and potentially hold the crown jewel at a ransom. And even though the city is protected by walls, guards, and gates, there are still many methods an attacker can use to invade.
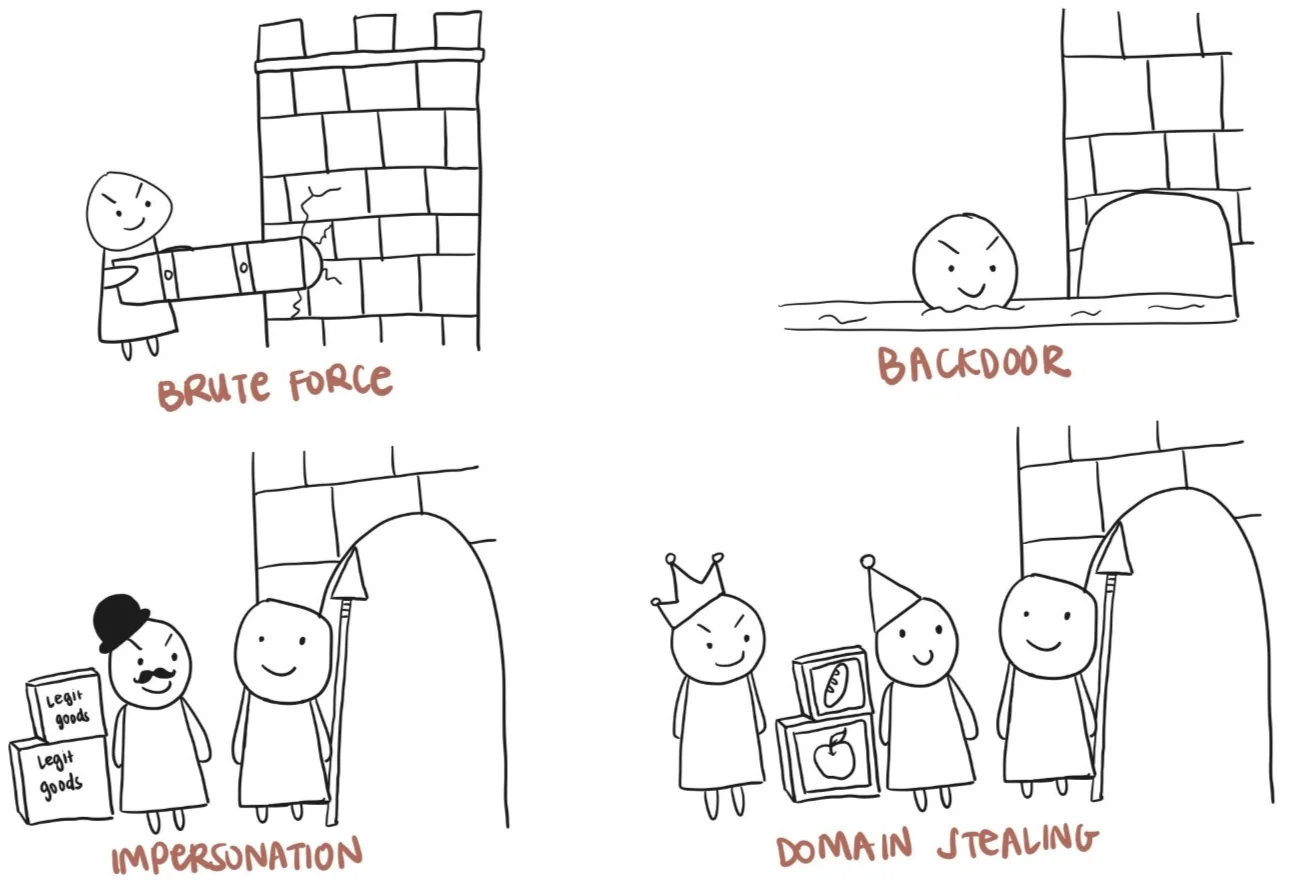
- Brute force: The attacker can take a battering ram and break through a wall or gate. In cybersecurity terms, this is when an attacker hacks into an environment directly on the endpoint.
- Impersonation: The attacker steals the identity of an innocent merchant traveling into the city and disguises itself as that merchant. In cybersecurity terms, this is when an attacker steals the credentials of a user to bypass an endpoint under the guise of the user.
- Backdoor: The attacker finds a hidden tunnel outside the walls that leads into the backroom of the general store. In cybersecurity terms, this is an attacker using a poorly managed backdoor in an environment.
- Domain stealing: The attacker dresses like the king and asks a merchant traveling into the city to tag along. Thinking that the attacker is truly the king, the merchant will concede. In cybersecurity terms, this could be when an attacker sends a phishing message to an employee posing as the CEO or high-level executive.
How do you protect a modern network?
There can be guards at each of the gates to stop attackers from entering, but three of the four attacker methods utilize elusion and the fluidity nature of the walled city’s makeup in social hierarchy and construction to bypass the gate completely. While there is some mode of protection, it simply is not enough to effectively address all the ways an attacker can infiltrate. And once the attacker is inside the walls of the city, there is nothing the guards, walls, or gates can do to stop them.
Protection can occur at the edges of the city, but there should also be protection within the city. This is where network protection can fill in the gaps endpoint protection cannot. Network detection and response (NDR) is similar to stationing a guard at strategic points on roads and paths around the city and analyzing the behaviors of each passerby to single out the irregular patterns of individuals or follow patterns that indicate a breach.

For example, network protection will look at why a farmer is transporting 100 goats to the clothing store. The volume of goats is alarming and is an indication of suspicious behavior. In cybersecurity terms, the goats represent data while a farmer can represent a user, and the clothing store is a server. In another example, network protection will also note why the clothing store manager is suddenly sending letters to an unknown kingdom. In cybersecurity terms, this is analogous to a host communicating with an external suspicious IP.
Protecting a modern network from modern attacks requires an NDR
The best modern network protection strings together these suspicious behaviors and builds a story of how the attacker is conducting their attack and what they plan to do next, then shutting down hosts, accounts, or servers so the attack doesn’t progress further.
The moral of this analogy is that while endpoint protection is critical to protecting modern networks, network protection is the core to defending against modern attacks. Naturally, we think to start at the entry points or the endpoints as the first line of defense or in other words, we start our threat detection and response strategy with endpoints. However, because of the complexities that come with modern networks, we must think beyond just endpoint protection.
A modern network requires security technology that brings visibility to and bridges all the touchpoints in the kingdom like the farmer, the general store, and the crown jewels. That way, today's defenders can enforce proactive security measures and be steps ahead of the modern attacker.
Learn more about the modern network: https://www.vectra.ai/products/network

