FINANCIAL SERVICES AND BANKING
Secure financial data from the attacks other tools miss

SECURING FINANCIAL DATA
How do attackers target financial services?
Identity-driven attacks like credential theft, business email compromise (BEC), and ransomware now bypass traditional defenses by blending into normal financial activity. By exploiting blind spots across Microsoft 365, hybrid infrastructure, and legacy systems, these threats often go undetected, causing damage before SIEMs or EDRs can respond.
Security operations teams are left overwhelmed with noise and struggling to meet compliance requirements.
CLOSING CRITICAL GAPS
Outsmart modern attackers targeting your finance data
Vectra AI, a leading NDR solution, gives financial security teams AI-driven behavioral detections to close visibility gaps, reduce complexity, catch unknown threats, and maintain compliance — across network, identity, and cloud.
Close visibility gaps
Traditional tools miss activity that uses valid credentials — the primary method of modern financial intrusions. Vectra AI:
Monitors cloud, SaaS, and on-prem systems without relying on agents.
Detects privilege escalation, lateral movement, reconnaissance, and C2 behaviors that mimic legitimate financial workflows.
Correlates identity, cloud, and network behaviors into clear attack narratives so analysts can respond faster.
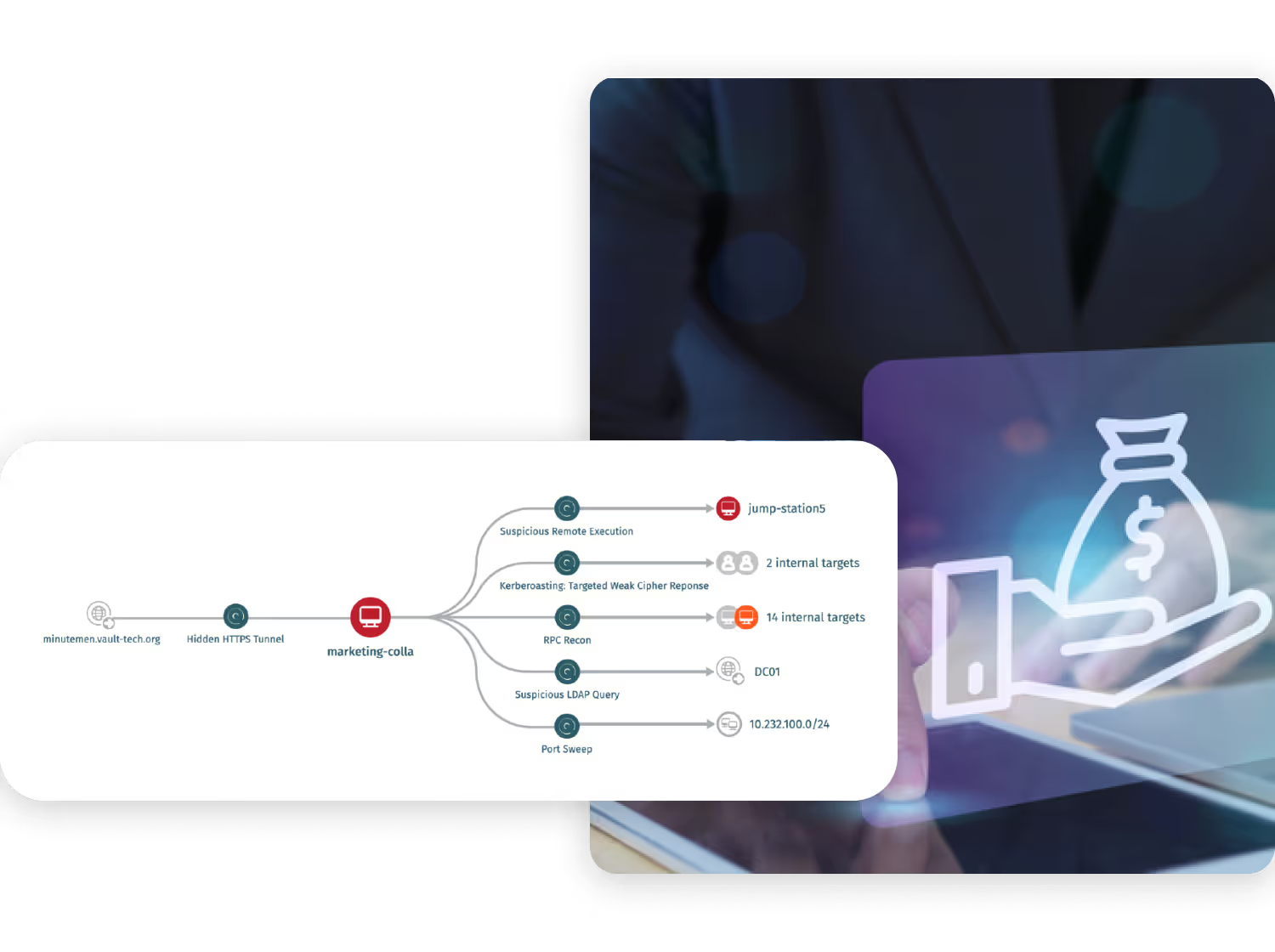

See how DZ Bank replaced legacy detection with behavior-based analytics to uncover encrypted, credential-driven APT activity missed by other tools.
Read More

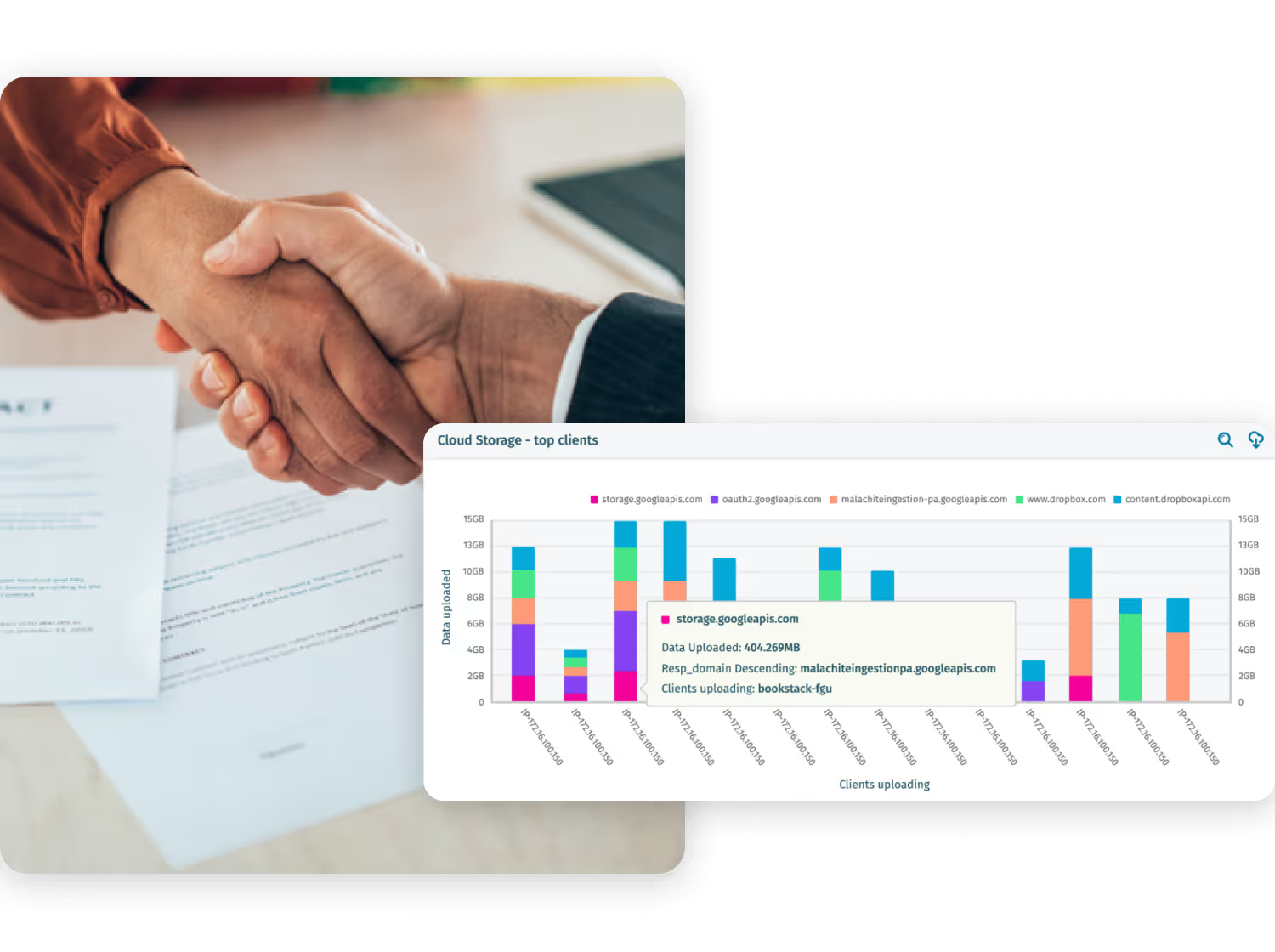

See how Verifone reduced 438,000 alerts to just six credible incidents — freeing analysts to focus on real threats and preventing ransomware escalation.
Read More
Reduce alert fatigue and SIEM complexity
Financial SOC teams are overloaded by noisy EDR and SIEM alerts — especially when attackers intentionally operate inside sanctioned systems like M365. Vectra AI combines and correlates alerts so only real attacker behaviors rise to the top. Vectra AI:
Cuts through the noise, surfacing high-fidelity signals from thousands of raw events.
Provides deep context and real-time detection to accelerate investigations and MTTR, cutting triage workloads by over 90%.
Prioritizes attacker behaviors before SIEM ingestion, reducing data sync volume and cost.

Strengthen identity security to stop modern BEC
Today’s BEC and account takeover attacks abuse legitimate authentication paths inside Microsoft 365, Azure AD, and financial SaaS tools—often bypassing endpoint agents and native cloud controls before they can respond. Vectra AI:
Identifies policy misconfigurations and privilege gaps across Teams, SharePoint, Exchange, and Azure AD.
Detects suspicious user access, privilege misuse, and anomalous cloud activity indicative of BEC or account takeover.
Delivers unified behavioral visibility that stops identity compromise before it impacts customer data or financial operations.
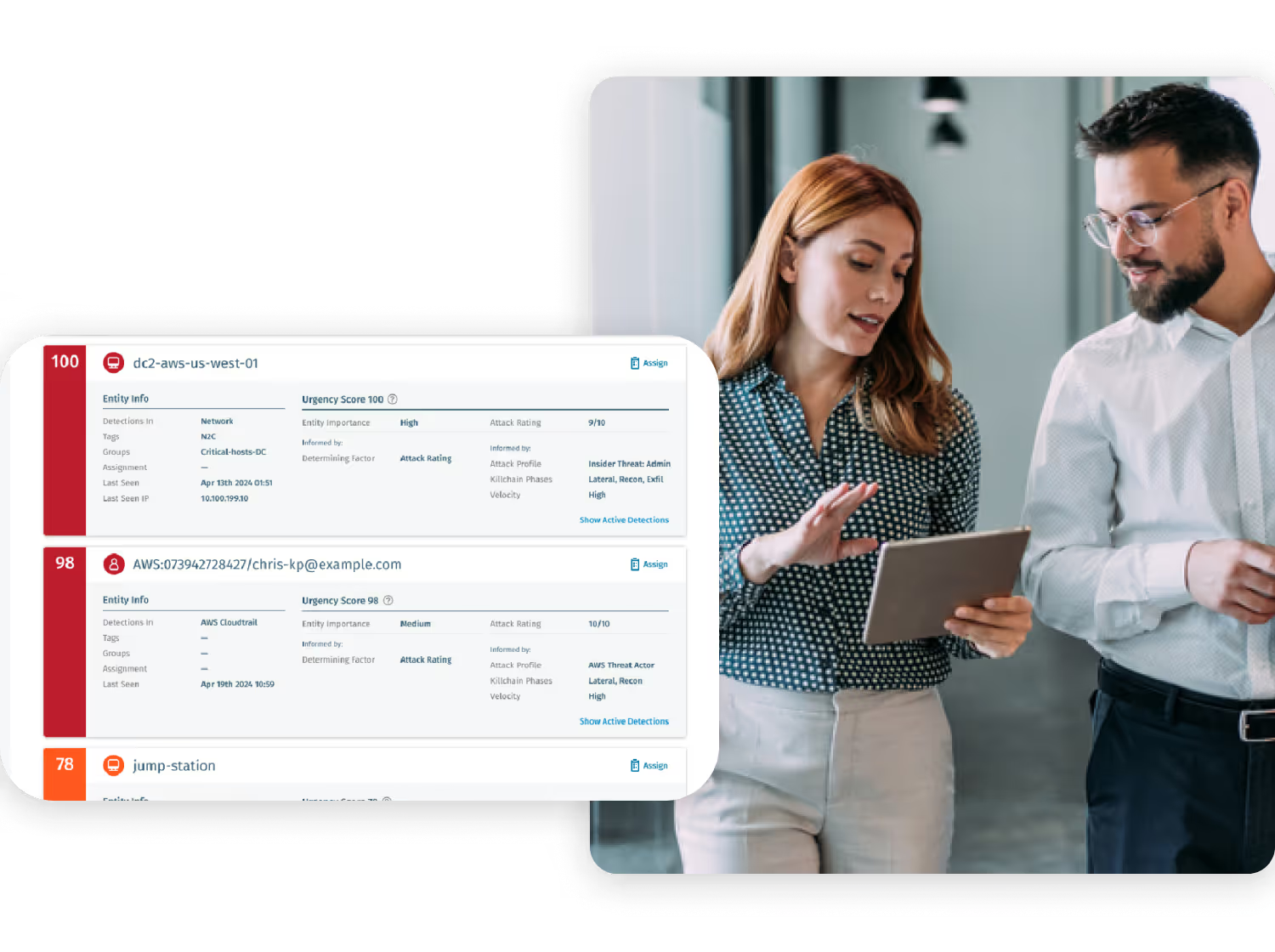
A global financial firm using E5 and Sentinel detected 0 out of 9 red-team identity attacks — then uncovered all threats within a week of deploying Vectra AI.
Read More
MODERN ATTACKS ON FINANCE
Who’s targeting your financial data?
Attack groups like these relentlessly probe financial networks for gaps they can use to evade detection, steal sensitive data, and disrupt critical banking operations.
Is your current technology security stack prepared to stop these attackers?
CUSTOMERS
Trusted by 2,000+ security teams to see and stop attacks






FAQs
How Vectra AI helps you protect financial data
How does Vectra AI help financial institutions detect threats that bypass traditional SIEM and EDR tools?
Vectra AI uses AI-driven behavior detection to identify post-breach activity that traditional tools miss — like lateral movement, privilege abuse, and command-and-control traffic — across hybrid cloud and legacy environments. This gives SOC teams earlier visibility into attacks that evade rule-based SIEMs and agent-based EDRs.
What role does Vectra AI play in preventing credential theft and identity-based attacks in banking environments?
Vectra AI continuously monitors identity behaviors across Microsoft 365, Azure AD, and internal infrastructure to detect misuse of valid credentials, suspicious access patterns, and privilege escalation. This helps financial institutions quickly uncover and contain identity-driven threats before they escalate.
How can Vectra AI improve threat detection and response times for SOC teams in financial services?
By correlating signals across cloud, network, and identity domains, Vectra AI prioritizes real threats and slashes alert noise. Financial SOCs reduce dwell time, streamline investigations, and move from reactive to proactive response — often cutting triage workloads by over 90%.
Why is Vectra AI effective in securing hybrid and legacy infrastructure used by banks and financial institutions?
Vectra AI provides agentless visibility across legacy systems and hybrid cloud environments, detecting threats in places that SIEMs and EDRs can’t reach. This is essential for financial organizations that rely on mainframes, COBOL applications, and aging infrastructure alongside modern platforms.
How does Vectra AI enhance visibility across Microsoft 365 and Azure AD environments for financial organizations?
Vectra AI integrates directly with Microsoft 365 and Azure AD to monitor identity activity, detect misconfigurations, and surface anomalous access behaviors. Financial firms use this deep visibility to uncover hidden threats, enforce Zero Trust policies, and reduce risk in SaaS environments.
What makes Vectra AI uniquely positioned to reduce alert fatigue and improve analyst efficiency in financial SOCs?
Unlike traditional tools that overwhelm teams with low-fidelity alerts, Vectra AI delivers attack signal clarity — distilling millions of data points into a handful of high-confidence detections. This empowers analysts to focus on what matters and accelerates time to containment.
How does Vectra AI support compliance efforts for regulations like PCI DSS, FFIEC, and GLBA in the finance sector?
Vectra AI helps financial institutions meet regulatory requirements by providing continuous monitoring, detailed forensic context, and audit-ready reports. With rich visibility into user behavior and threat activity, security teams can demonstrate control effectiveness and simplify compliance validation.
How does Vectra AI help financial firms protect against ransomware and business email compromise (BEC)?
Vectra AI detects early indicators of ransomware and BEC — such as credential abuse, lateral movement, and anomalous email behavior — before data encryption or financial fraud occurs. Financial SOCs use these insights to disrupt attack chains early and protect sensitive assets and operations.
Resources
How to secure patient care in a hybrid world
Get started today
Get an up-close look at how leading financial institutions protect their data with Vectra AI.

















