Regardless of the industry or your specific role, it’s probably safe to say at this point that you’re experiencing some level of pull (maybe push) towards embracing AI. Maybe colleagues or friends are sharing their experiences with various AI tools? Perhaps you’re being encouraged by leaders to experiment and see if AI can give you some time back from day-to-day tasks? Or maybe your child miraculously no longer has homework because they’ve hired an AI agent? Whether you’re already a power user or waiting until the DJ plays the right song before stepping on to the dance floor, one thing is certain — AI is the future, and it’s already here.
If AI is the future, we may as well use it to our advantage
Since there are different types of AI, for this discussion let’s cover how agentic AI will enable better threat detection, investigation, and response (TDIR) now and in the future — specifically by utilizing an NDR. A good place to start is with a recent piece of research by Gartner, Emerging Tech: Agentic AI Integration Will Separate TDIR Platform Winners and Losers. This piece does a nice job of explaining not just how agentic AI will impact TDIR, but it provides some food for thought for product leaders in terms of how they need to think about enabling analysts and practitioners to easily collaborate with AI.
Gartner raises a good point here because if usability (or collaboration with AI) isn’t something we discuss when talking about AI — it probably should be. We hear a lot about what we can do with it, the tasks it can replace, how powerful the capabilities are getting, etc., but at the end of the day, if it’s not built to easily fit into people’s lives and workflow — does it really matter how great it is? It’s the same reason a growing number of elementary through college students are using ChatGPT and other LLMs (large language models). It couldn’t be easier to ask a question and receive a robust response (or term paper) in seconds.
The flip side of that, is that students are now evolving and learning with AI and becoming the ultimate “AI tinkerers” — a term Vectra AI VP of Product Marketing, Mark Wojtasiak wrote about following his experience at Gartner’s Security Risk and Management conference. Mark is discussing it in terms of advice for security practitioners who have an opportunity right now to experiment with AI to see what outcomes they can drive — basically, it’s critical for security folks to start “tinkering” with AI. To take that a step further, even if you’re just getting started, it may also be worth considering how you can align outcome-driven metrics with your AI-powered TDIR approach, which will make reporting on outcomes easier down the road. Sound advice considering there’s certainly no shortage of tools to test drive and especially since we know attackers are already using AI to move faster towards their motives. On that note, below are some easy ways security practitioners can start incorporating agentic AI into their workflow to help power faster and more effective TDIR outcomes across modern networks.
5 ways to use leverage agentic AI for better TDIR
“40% of data breaches involved data stored across multiple environments.” - IBM 2024 Cost of a Data Breach Report
For cybersecurity pros, AI can make sure you see every move modern attackers make, help connect the dots in real-time, so you have the full context needed to stop them before a breach occurs.
1. Use AI agents to automatically triage alerts
Instead of manually combing through thousands of alerts, agentic AI can continuously review events, triage them across hybrid networks, and filter out benign detections — giving analysts a head start. For example, AI can flag behaviors that match attacker activity across network, identity, and cloud — and present only the most relevant incidents for human review. This means less noise to deal with and a greatly improved threat signal.
2. Stitch together identity, network, and cloud activity
Attackers don’t stay in one place. One of the biggest opportunities with agentic AI is its ability to continuously stitch together activity across multiple domains (network, identity, and cloud for example). When AI can track an identity compromise or lateral movement across your modern network, you get context that’s impossible to see with other tools as these things are happening beyond the endpoint and already inside your environment. This is where network detection and response (NDR) shines — especially when enriched with identity and cloud signals.
Good read: Choosing the Right NDR: Gartner’s 5 Questions Every Security Buyer Should be Asking
3. Prioritize incidents based on real risk
Not every alert needs attention. Agentic AI can evaluate threats based on behavior, context, and business impact — not just IOCs or signatures. For example, it can differentiate between routine admin behavior and stealthy command-and-control communication by analyzing historical patterns and intent. That means you’re not just alerted about something unusual — you're alerted when something is dangerous. AI prioritization helps teams focus their limited time on indicators of attack (IoAs) that actually matter.
4. Get a running start on investigations
Time is everything when responding to an attack. AI agents can kick off initial investigations the moment suspicious activity is detected — gathering logs, mapping out assets involved, highlighting recent changes, and even generating a timeline of events. This means by the time an analyst gets involved, they’re not starting from scratch. With agentic AI, your team moves from “what happened?” to “what do we do next?” much faster.
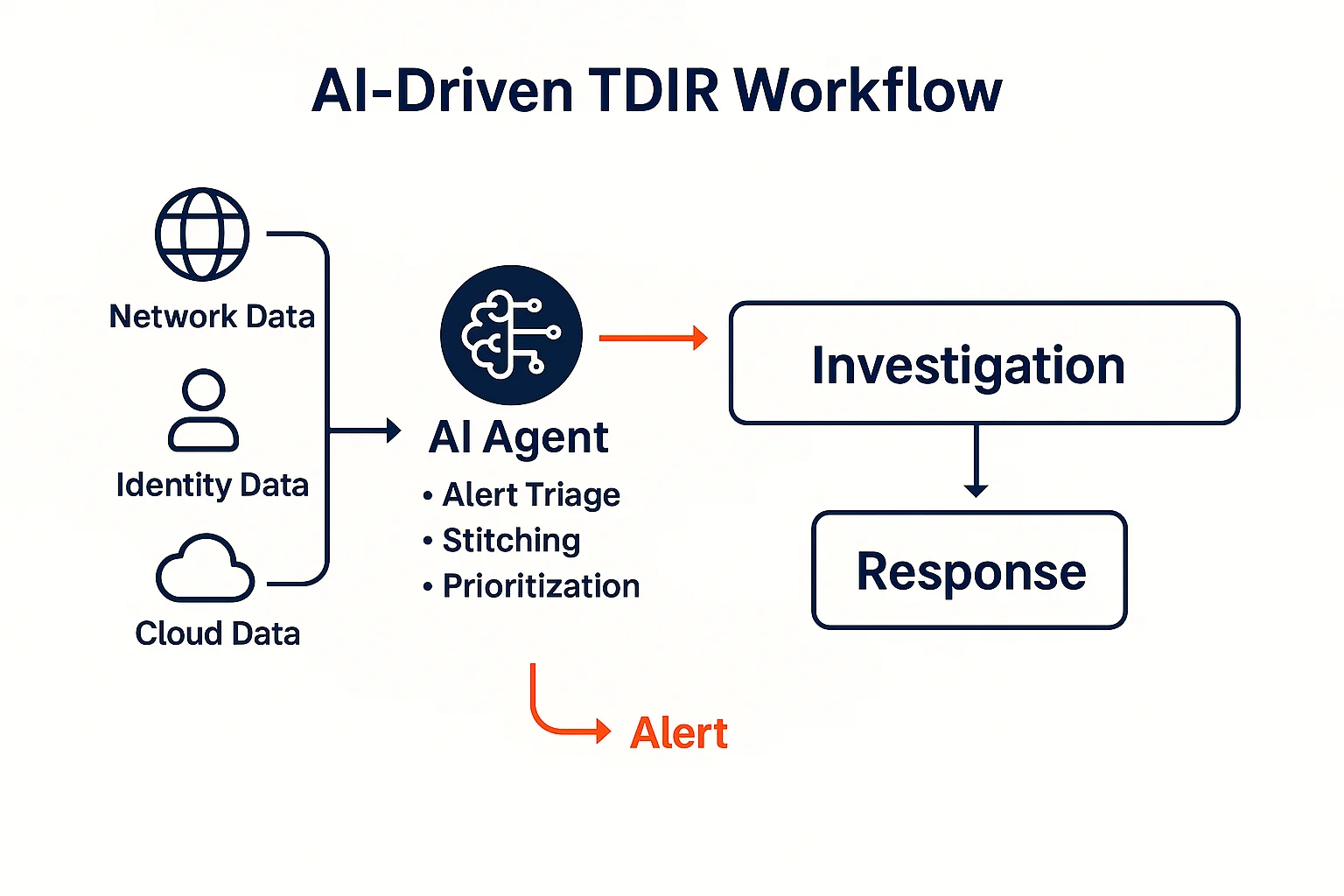
5. Use NDR as a low-lift, high-impact entry point
If you’re looking for a smart place to begin with agentic AI, NDR is it. Why? You’ll be able to see everything across all surfaces — from initial access to lateral movement, command-and-control, and data exfiltration. NDR platforms equipped with agentic AI can continuously observe and learn from traffic patterns, trigger autonomous investigations when attacker behavior is detected, and provide analysts with a fully formed picture of the threat. Unlike log-based systems that rely on clean, structured data, NDR thrives in noisy, dynamic environments — making it a powerful foundation for AI-driven TDIR.
Download the 2025 Gartner® Magic Quadrant for Network Detection and Response (NDR).
Regardless of your role in the SOC or maybe you’re a one person show — experimenting with AI doesn’t require a full-blown transformation. Start small. Tinker. You could take a product demo, or explore capabilities on your own (Vectra AI has dozens of product briefings on our Hunt Club Podcast to see how things work for free). Try one or two of these approaches and see what kind of time, clarity, or insight it gives you.

