Which is more astonishing—that even with widespread multi-factor authentication (MFA) adoption, over the last year 71% of enterprises still experienced SaaS account takeovers or that, despite that, close to 90% have accelerated their cloud and digital transformation? Perhaps neither is especially astonishing if you’ve noticed the transformative effects of the last (pandemic) year and have been keen to both the risks and opportunities present. For a view into the past, present and future of that journey, we surveyed more than 1,000 Security decision makers in mid to large enterprises using Microsoft Office 365.
At first everything looks good
Right out the gate it was obvious that there was a sense of optimism on a number of topics, and to some degree there should be. Cloud adoption and transformation gives organizations an opportunity to hit the reset button on many faulty and failing assumptions codified into legacy security architecture, and to modernize in pursuit of a Zero-Trust Architecture. Moving past prevention as a primary (and failing!) security strategy towards one centered on resilience has been the goal of advanced security practitioners for most of the last decade—so seeing that sentiment increase is a net positive!

Optimism gives way to reality
Yet, despite that optimism, over 80% of respondents acknowledged that their own organization’s cybersecurity risks had increased over the last year, and close to 60% specifically felt the gaps between their defensive capabilities and their adversaries’ offensive capabilities were widening—threatening to have them fall further behind what has already felt like a losing arms race.
What explains the gap between that rosy sentiment and the assessment of actual challenges ahead when organizations consider their risks and capabilities? I’d posit that, at a minimum, even as defenders acknowledge opportunities and evolution, they recognize that cloud and digital transformation involves transitional gaps, organizational noise, and opportunities for adversaries to benefit from the speed and scale of the cloud during the transition.
Transformation involves transition
First, technology transitions at enterprise scale often requires maintaining a forward-looking architecture and availability to legacy systems. Unfortunately, this increases the attack surface available to an adversary. For example, running Azure AD in a hybrid mode doesn’t just involve protecting against both legacy Active Directory and Azure AD attacks, but also a third class of attacks inherited from having to support both at the same time and the need to keep the two directories synchronized. From an adversary’s perspective it’s better than just the best of both worlds!
When it comes to transitional periods like this, enterprise defenders need to be prepared to rip the band-aid off and support IT in the task of accelerating the migration to the desired future state while understanding the posture implications and how to prioritize risk and remediation. Drawing out the transition doesn’t just strain the organization’s technical resources; it creates fundamentally new gaps for adversaries to exploit.
Transformation can be noisy
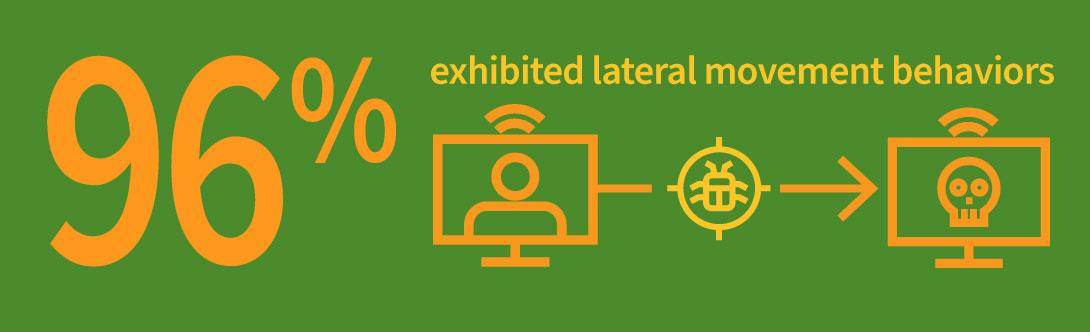
Second, cloud transformation involves baselining into “the new normal”—but finding that behavioral baseline is messy, noisy, and prone to uncertainty and unfamiliarity for defenders. Meanwhile, noise and uncertainty are conditions that adversaries excel at exploiting, and it’s available in spades on this transformative journey. Our Spotlight Report on Office 365 found 96% of customers exhibited suspicious lateral movement behaviors in Office 365 accounts. This volume of alerts would be impossible to analyze without the application of artificial intelligence or machine learning to sort signal from noise.
Fortunately, 60% of respondents specifically are applying a mix of subject matter experts and technology to tackle this problem over the next year. This is a good sign, and prudent defenders will identify tasks in which they excel (e.g., contextualizing behaviors) and which are best suited for machines (e.g., sifting through large sets of noisy data).
Public cloud presents a great opportunity [for attackers]
Thirdly, the cloud doesn’t just enable business to operate at speeds and scales previously unattainable, it provides those benefits to adversaries as well. Unless security investments are made into response capabilities, the gap in security capabilities will grow. This insight becomes obvious when considering that in the cloud attackers perform their discovery via well-defined APIs which conveniently list things like access and permissions across regions and workloads, and are capable of being chained together to quickly execute at speed and at scale. This means defenders must move quickly to stand a chance.
Likely this is why over 50% of respondents planned investments in automation and orchestration over the next year; however, response is only half of the story. Without a high-fidelity signal to cue the response, authorized users may themselves be victims of both adversaries and overzealous defensive automation. This is another example of where organizations would be wise to invest in actionable (AI/ML enhanced) detections of attacker behaviors as a conduit into downstream orchestration.
The future is bright
Still, despite these challenges, the future is bright for organizations willing to go on this journey. As a transformational force, the cloud is powerful. It is fundamentally reshaping business even as it enables security modernization like never before. Perhaps if this transformation hadn’t been occurring with the backdrop of the very tangible benefits AI/ML based capabilities deliver into an organization’s security portfolio, I wouldn’t share the sentiment with some of our more optimistic survey participants. But from our vantage point, it’s hard not to look at the road ahead and think challenge accepted.

