Over the past decade, cyber operations have become intertwined with geopolitical conflict. In recent asymmetric campaigns, state-sponsored threat groups have mapped critical infrastructure, disrupted systems, held information hostage, and stolen state secrets as a form of warfare.
Most recently, the escalating tensions between the Islamic Republic of Iran and the United States of America increase the potential of a retaliatory cyberattack. Iranian threat group TTPs have evolved to incorporate destruction as a retaliatory tactic; focused on critical infrastructure sectors, which include the power grid, oil and gas, and communications networks.
This has recently led to an advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA). The advisory urges heightened readiness, warning that:

Notably, Iranian threat groups have developed advanced Wiper malware, a class of malware that wipes the hard drive of the computer it infects, and shown a willingness to deploy them against regional energy sector adversaries over the last decade. The result has been large-scale destruction of computing systems, including over 30,000 in the Shamoon malware attack of 2012.
To date, Iranian attacks have been focused on energy and government targets physically located in Saudi Arabia. However, this is driven by mission scope and not technical capability. If these capabilities were to be successfully deployed against a broader set of entities as part of a cyber campaign, the impact could be high.
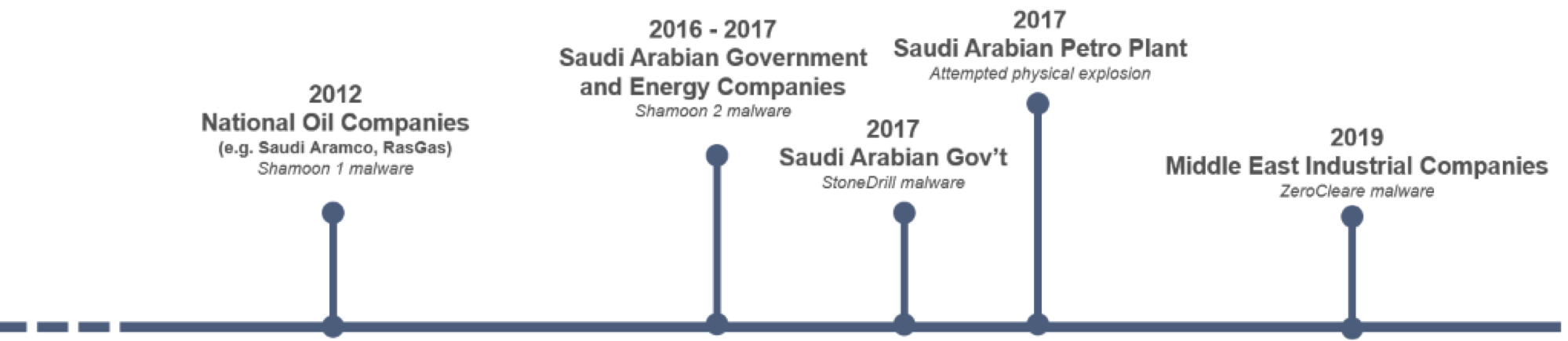
The most recent Iranian-attributed Wiper malware is ZeroCleare, which was identified and researched by IBM in December 2019. The active phase of a ZeroCleare attack propagates the Wiper malware from Domain Controllers to all systems in the domain using Powershell / WMI with domain administrator credentials. The malware then uses the EldoS Rawdisk toolkit to overwrite the Master Boot Record (MBR) and disk partitions on Windows-based machines.
This malware propagation is fast and complete because compromise of the Domain Controller and domain admin credentials enables access to all entities across the infrastructure. The result is an impact that is pronounced and prolonged since there is no recovery of the system once the MBR is destroyed. Further, since there is no exploit that can be patched, the progression can’t be slowed.
Speed is of the essence for security teams put up against these TTPs. It is critical that the attack be detected and evicted before Domain Admin on the Domain Controller is achieved.
The good news is that Vectra Cognito provides coverage across the initial phases of the attack since this attack will behave in a similar manner to other credential-based attacks attempting to achieve a privileged level of access. A summary of the visibility into these behaviors can be found in Table 1.

Note: be especially vigilant for any Privilege Anomalies or Suspicious Remote Execution detections targeting a Domain Controller or—worse—between Domain Controllers, as these would be expected in the later stages of the (pre-wipe) attack progression.
In conjunction with the recommendations in the advisory, we recommend that your security teams pay particular attention to these attack behaviors in your Cognito deployment.
We will continue to update this post as we uncover more information.
