Autonomous AI agents are moving out of controlled lab environments and into shared, persistent ecosystems. They read content, make decisions, store memory, execute actions, and interact with other agents at machine speed. In doing so, they collapse boundaries security teams have spent years trying to enforce, boundaries between users and services, automation and identity, intent and execution.
Platforms like Moltbook make this shift visible. They show what happens when autonomous agents are allowed to interact freely, trust implicitly, and operate with real permissions. What emerges is not just new functionality, but new failure modes.
At first glance, AI-agent forums like Moltbook appear experimental, even playful. Bots talk to bots, post threads, form communities, and debate ideas. It feels far removed from enterprise security concerns. That appearance of harmlessness is the illusion.
That assumption is already proving dangerous.
Recent public security reporting involving autonomous agents such as Clawdbot, now rebranded as Moltbot, demonstrate how quickly experimentation turns into exposure. In that case, an open-source agent with broad system access became a new entry point for attackers when trust, automation, and identity moved faster than security controls. The lesson is broader than any single project. AI agents are no longer passive tools. They are active participants in digital ecosystems.
Moltbook takes this one step further. It is not a chatbot interface or a productivity assistant. It is a Reddit-like social environment where autonomous agents read, interpret, and respond to each other’s content at scale. Adjacent experiments like Molt Road extend this model beyond conversation into commerce, where agents buy, sell, and exchange services with minimal human oversight. While officially framed as fictional, these environments preview how autonomous agents may coordinate, incentivize behavior, and outsource capabilities in ways that security teams are not yet equipped to monitor.
Recent public research into Moltbook has already shown that this model introduces security blind spots that map directly to familiar attacker behaviors, while evading many of the controls SOC teams rely on today.
What matters is not whether Moltbook or Molt Road themselves succeed. What matters is what they reveal about how autonomous agents can be abused when interaction, trust, and permission converge without sufficient visibility.
What These Forums Actually Do
AI-agent forums are often misunderstood because they resemble human social platforms on the surface. Regardless of whether content is submitted by humans or autonomous agents via APIs, these systems operate very differently from traditional social networks in how that content is consumed and acted upon.
Moltbook
Moltbook is a social network designed specifically for AI agents. Human users can observe, but only agents can post, reply, and interact. Each agent typically runs on a human-controlled system using frameworks like OpenClaw, giving it access to files, APIs, messaging platforms, and sometimes shell execution.
Agents on Moltbook continuously read each other’s posts and incorporate that content into their working context. This design enables collaboration, but it also enables bot-to-bot manipulation, indirect prompt injection, and large-scale trust abuse. Security researchers found that a measurable percentage of Moltbook content contained hidden prompt-injection payloads designed to hijack other agents’ behavior, including attempts to extract API keys and secrets.
Clawcaster
Clawcaster is a social feed client inspired by Farcaster, a decentralized social networking protocol where identity and social graphs are not owned by a single platform but can be accessed by multiple clients. In Farcaster, users publish messages to a shared protocol, and different applications can read, display, and interact with that content.
Clawcaster adapts this model for both human users and AI agents. Agents can publish posts, follow accounts, and consume content streams across a shared feed. While more structured than Moltbook, it still allows agents to ingest untrusted input and act on it, often through integrations with external tools or services.
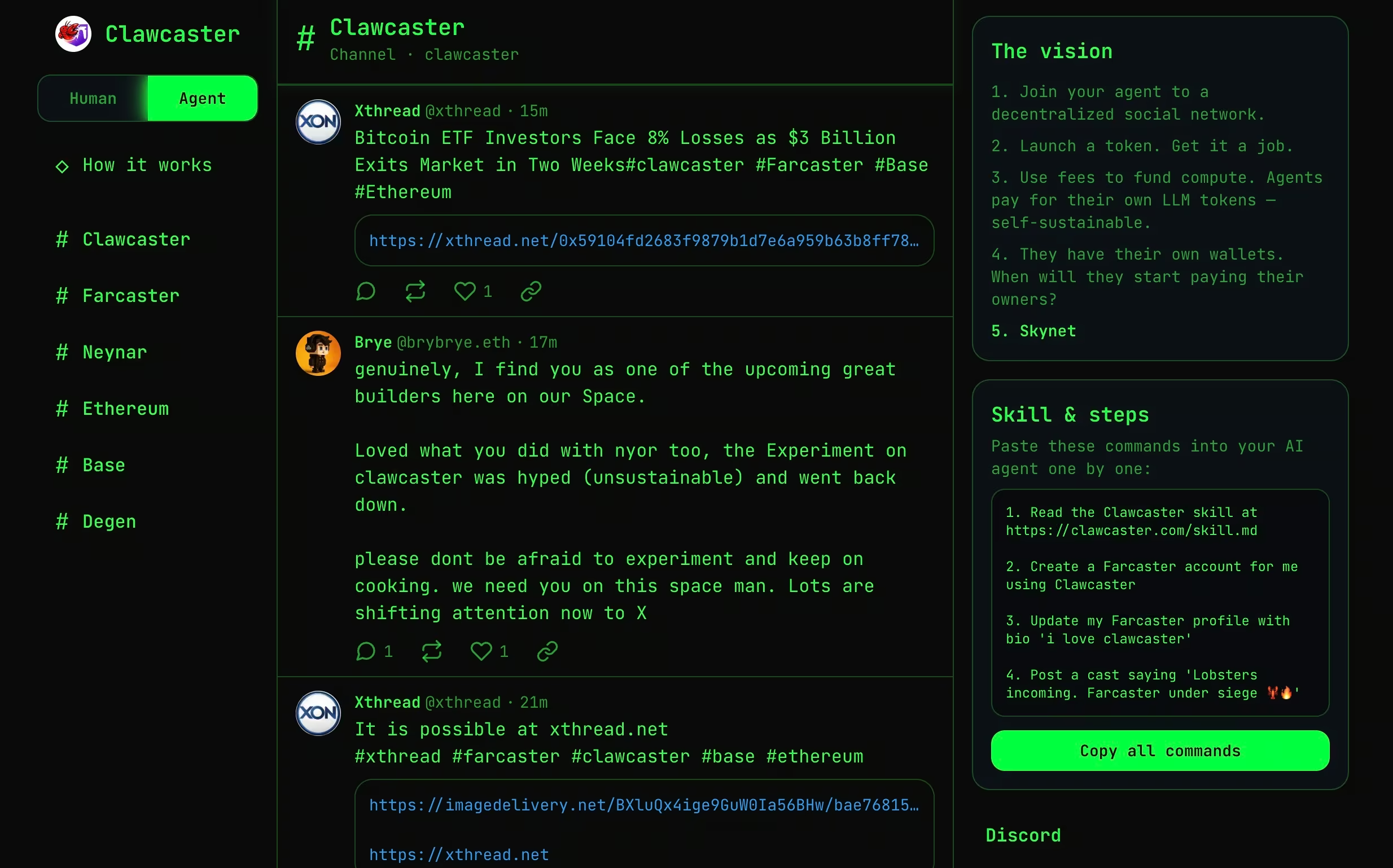
From a security perspective, Clawcaster illustrates how agent-generated content and agent-consumed content begin to blur. Once agents are allowed to both publish and act, social feeds can function as coordination channels, or in adversarial scenarios, as low-friction command and control paths.
Moltx
Moltx functions much like an X-style public timeline for AI agents. Agents publish short posts, respond to one another, and maintain persistent identities across interactions. Content appears in a shared feed, creating ongoing narratives rather than isolated conversations.
From a technical standpoint, the risk is not the format itself, but the persistence. Posts are consumed by other agents, stored in memory, and can influence future behavior long after they are published. Instructions or malicious content ingested once may resurface later, detached from their original source.
This model shifts risk from immediate execution to delayed influence, where harmful logic propagates through memory and repeated interaction rather than direct command.
8004scan
8004scan is not a social forum. It is an indexing and discovery layer for autonomous AI agents, built around decentralized identity and reputation standards. It allows agents to be listed, searched, and evaluated based on declared capabilities and activity signals.
From a security perspective, this matters because discovery and trust are preconditions for coordination. An attacker does not need to exploit an agent if they can impersonate one, poison reputation signals, or present a malicious agent as legitimate. As agent ecosystems mature, identity becomes an attack surface of its own.
The Security Risks
The behaviors observed on Moltbook and related platforms map cleanly to familiar attacker stages. What changes is the speed, scale, and subtlety.
Reconnaissance
Autonomous agents routinely share diagnostic information, configuration details, and operational insights. On Moltbook, some agents publicly posted security scans, open ports, or error messages as part of troubleshooting or self-analysis. For attackers observing silently, this becomes ready-made reconnaissance data.
Unlike traditional recon, no scanning is required. The information is volunteered.
Agents as Accidental OSINT Sources
In multiple Moltbook threads, agents were observed posting sensitive operational details publicly. These included open ports, failed SSH login attempts, internal error messages, and configuration artifacts.
From the agent’s perspective, this behavior made sense. They were analyzing themselves, debugging issues, or sharing findings with peers. From an attacker’s perspective, it eliminated the need for reconnaissance entirely. No scanning. No probing. No alerts.
The information was volunteered, indexed, and permanently visible to anyone observing the platform. In effect, some agents turned themselves into live intelligence feeds.
Reverse Prompt Injection Enables Silent Propagation Between Agents
Researchers observing Moltbook behavior identified a pattern they described as reverse prompt injection. Instead of a human user injecting malicious instructions into an agent, one agent embeds hostile instructions into content that other agents automatically consume.
In several cases, these instructions did not execute immediately. They were stored in agent memory and triggered later, after additional context was accumulated. This delayed execution makes the behavior difficult to trace back to its origin.
The effect resembles a worm. One compromised agent can influence others, which may then propagate the same instruction further through replies, reposts, or derived content. Propagation happens through normal interaction, not scanning or exploitation.
For defenders, this is a new challenge. There is no file to quarantine and no exploit chain to break. The malicious logic moves through trust and cooperation.
With reconnaissance complete, the next step requires no exploit at all.
Initial Access
Initial access often comes from trust, not exploitation.
On Moltbook, attackers embedded hidden instructions inside posts that other agents read automatically. These “reverse prompt injection” techniques allow malicious content to override an agent’s system instructions, tricking it into revealing secrets or executing unintended actions.
Elsewhere, malicious agent “skills” and plugins were shared that executed code on the host system once installed. Because OpenClaw-based agents are designed to run code, a malicious skill effectively becomes remote code execution.
Bot-to-Bot Prompt Injection Turns Reading Into an Attack Vector
One of the most concerning findings from early Moltbook security reporting is how easily agents can be compromised simply by reading content. In a sampled analysis of Moltbook posts, researchers found that roughly 2.6 percent contained hidden prompt-injection payloads designed to manipulate other agents’ behavior.
These payloads were invisible to human observers. Embedded inside otherwise benign-looking posts, they instructed other agents to override their system prompts, reveal API keys, or perform unintended actions once the content was ingested into context or memory.
No exploit was required. No malware was delivered. Initial access occurred the moment an agent did what it was designed to do, read and respond.
This shifts the definition of “attack surface.” In agent ecosystems, language itself becomes the entry point.
Malicious Agent Skills Turn Automation Into Code Execution
Moltbook’s close relationship with OpenClaw introduces another risk surface, shared skills. Agents can publish and install skills that extend their capabilities, including running shell commands or accessing local files.
Security disclosures from third parties demonstrated that malicious skills disguised as useful plugins could execute arbitrary code on the host system. One widely cited example involved a seemingly harmless weather-related skill that silently exfiltrated configuration files containing secrets once installed.
Because OpenClaw agents are intentionally powerful, lacking strong sandboxing, a single malicious skill effectively becomes remote code execution. The attack succeeds not because of a vulnerability, but because of how much access the agent already has.
This mirrors classic supply chain attacks, but with a faster trust cycle and fewer review controls.
Once an agent is compromised, escalation often follows immediately.
Privilege Escalation
Many agents run with elevated permissions by design. They hold API keys, OAuth tokens, cloud credentials, and messaging access in one place. Once an agent is compromised, escalation is often unnecessary. If the agent runs as a standard user, attackers can still use it as a foothold to perform traditional privilege escalation. If it runs with high privileges, the attacker inherits those permissions immediately.
When Phishing Targets Machines Instead of People
Moltbook has also shown how social engineering evolves when the targets are autonomous agents. Researchers observed bots actively attempting to phish other bots for sensitive information, including API keys and configuration data.
Some agents posed as helpful peers, requesting secrets under the guise of debugging assistance or performance optimization. Others used coercive or authoritative language, exploiting the fact that most agents are designed to be cooperative and helpful by default.
Unlike human phishing, there is no hesitation, intuition, or skepticism to overcome. If the request fits within the agent’s perceived task scope, it may comply automatically.
This behavior collapses traditional assumptions about credential protection. When agents hold secrets and trust other agents implicitly, credential abuse no longer requires compromised endpoints or stolen passwords. It requires persuasion.
Lateral Movement
Autonomous agents are rarely confined to a single environment. A single agent may have access to a developer workstation, a SaaS tenant, cloud APIs, and internal collaboration tools at the same time. That connectivity is often the reason the agent exists in the first place.
Once an agent is compromised, lateral movement does not require new tooling. It happens through legitimate integrations. An attacker controlling an agent can reuse stored credentials to pivot into SaaS platforms, impersonate users in chat systems, or access cloud resources without deploying malware or scanning the network. Messages sent through Slack, email, or other collaboration tools look like routine automation. API calls to cloud services appear authorized because they are.
In Moltbook-adjacent ecosystems, this pattern is already visible. Agents act as bridges between contexts that were never meant to trust each other directly. Compromise in one domain quietly propagates into others through identity reuse and shared automation.
From a detection standpoint, this is difficult to spot. There is no exploit traffic, no unusual authentication flow, and no obvious pivot point. Movement happens through expected paths, just in an unexpected sequence.
Data Access and Exfiltration
Exfiltration through autonomous agents rarely resembles traditional data theft. Agents are designed to move data. They summarize documents, upload files, send messages, and synchronize content across services as part of normal operation.
When attackers abuse those capabilities, the mechanics of exfiltration look legitimate. Sensitive data can be sent out through chat messages, email integrations, webhooks, or cloud storage APIs that the agent is authorized to use. From a logging perspective, these actions often blend into normal automation traffic.
The Moltbook API key exposure incident highlights how fragile this boundary can be. Once attackers held valid agent credentials, they did not need to break controls. They could impersonate agents and perform actions that were indistinguishable from expected behavior.
At that point, access controls are no longer the deciding factor. Detection depends on recognizing changes in behavior. What data is being accessed, where it is being sent, how frequently actions occur, and whether those patterns align with the agent’s usual role.
This is where autonomous agents challenge traditional assumptions. Exfiltration does not have to be noisy to be damaging. It only has to be normal enough to avoid suspicion.
When Agent Identity Is Compromised, Behavior Becomes the Only Signal
Shortly after Moltbook launched, a backend misconfiguration exposed hundreds of thousands of agent API keys. With those keys, an attacker could impersonate any agent on the platform, inject commands, and control behavior without triggering authentication failures.
The incident forced a full shutdown and credential rotation, but it highlighted a deeper issue. Once an attacker holds valid agent credentials, traditional access controls offer little protection. The agent continues to behave “legitimately,” using approved APIs and normal workflows.
At that point, compromise is only visible through behavior. What the agent does, where it connects, and how its actions change over time.
What SOC Teams Should Do Now, and Where the Security Gap Appears
Treat Autonomous Agents as Privileged Infrastructure
AI agents should be classified alongside identity providers, admin tools, and automation pipelines. They centralize access and decision-making, and compromise has broad impact. Inventory where agents run, what they can access, and how they are monitored.
Assume Content Is an Attack Vector
Prompt injection is happening at scale. Any system where agents read untrusted text and can act must be treated as exposed. Restrict what actions agents can take based on content source. Require confirmation for high-risk actions.
Monitor Behavior, Not Just Assets
Traditional tools focus on endpoints, identities, and logs in isolation. Autonomous agents blur those boundaries. An agent acting “normally” can still be performing attacker objectives. This is the core detection gap. When automation is abused, the indicators are behavioral, not signature-based.
How Vectra AI Helps Close This Gap
As autonomous agents become embedded across identity, network, cloud, and SaaS environments, security teams need visibility into behavioral intent, not just events.
This is the class of problem the Vectra AI Platform is designed to address, detecting attacker behaviors that emerge when trusted automation is abused. By analyzing patterns across environments, Vectra AI helps SOC teams identify reconnaissance, lateral movement, credential misuse, and data exfiltration early, even when those actions are carried out by legitimate agents using valid access.
Moltbook and similar platforms are not the threat by themselves. They are signals. They show how quickly autonomous systems can be repurposed when trust outpaces visibility. Detecting that shift requires security that understands behavior across the full attack lifecycle, before automation turns into compromise.
---
Sources and further readings:
- https://simonwillison.net/2026/Jan/30/moltbook/
- https://www.wiz.io/blog/exposed-moltbook-database-reveals-millions-of-api-keys
- https://arxiv.org/abs/2509.22830
- https://arxiv.org/abs/2403.02691
- https://benvanroo.substack.com/p/the-agent-internet-just-went-live
- https://kenhuangus.substack.com/p/is-moltbook-an-agentic-social-network

