The Remote Desktop Protocol (RDP) is a method for connecting to and controlling computers over the Internet. RDP became a default feature of Windows operating systems in 1996 and has since become a popular tool in the professional world.
Benefits of using RDP in the Workplace
RDP's versatility allows professionals in banking, manufacturing, healthcare, and more to access essential databases, monitor facilities remotely, and check records on the go. For instance, bankers can manage financial databases during client dinners, factory technicians can oversee operations globally, and nurses can access patient records via tablets, showcasing RDP's wide-ranging applications.
The Dark Side of RDP: Security Risks
However, the convenience of RDP comes with significant security concerns. The ability to remotely access computers makes RDP an attractive target for cyberattackers. According to our Attacker Behavior Industry Report, an alarming 90% of organizations showed signs of suspicious RDP activities in the first half of 2019, indicating the prevalence of RDP abuse.
Industry-Wide Impact of RDP Misuse
Manufacturing, finance/insurance, and retail industries are the most affected by RDP misuse, together accounting for nearly half of all suspicious RDP activities detected. This widespread issue underscores RDP's role as a consistent attack vector for cybercriminals.
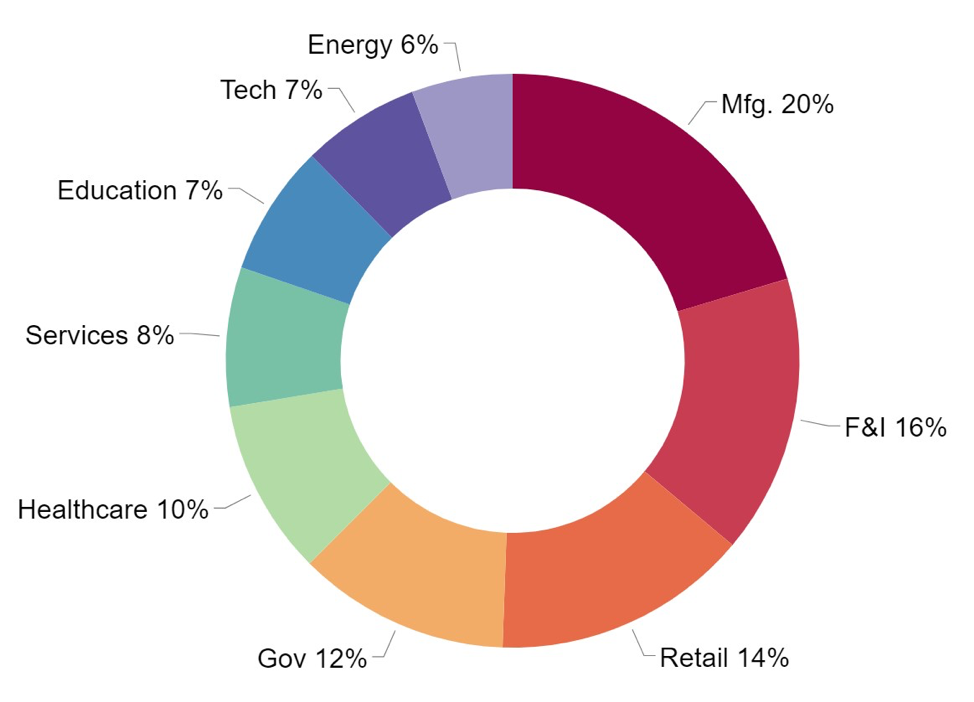
Overall, all industries detected a substantial amount of RDP abuse. From month-to-month, the raw number of RDP abuse detections per industry changed only a small amount. More specifically, the average coefficient of variation for RDP abuse detections per industry was only 18.5%. This suggests that RDP is consistently used as an attack vector.
Cyberattacks and RDP Vulnerabilities
Cyberattackers often leverage RDP as a stepping-stone when launching their full attacks. For example, the FBI reported that attackers gained entry through RDP when carrying out the CryptON, CrySiS, and SamSam ransomware attacks. RDP can also be used to move laterally through a victim's network and to carry out reconnaissance efforts. Major governmental organizations such as the NCSC UK, FBI, and DHS have recommended that organizations reduce employee access to RDP. However, RDP remains so beneficial that reduced use is unlikely in the near future.
To illustrate this point, consider how the manufacturing industry benefits from RDP.
RDP's Value in Manufacturing
Manufacturers can improve data centralization via RDP. Instead of installing industrial control systems (ICS) on each employee’s computer, organizations can use just one central RDP server with ICS applications installed. This strengthens their security posture because cyberattackers who gain access to a technician's laptop still cannot access the ICS without proper RDP credentials.
Furthermore, RDP saves manufacturers money. Industrial manufacturing systems require close monitoring and frequent modifications. In the past, manufacturing technicians had no choice but to travel between an organization's different production plants in order to monitor all of them, a costly and time-consuming task. RDP changes that. According to Machine Design, studies show that, "60% to 70% of machine problems simply require a software upgrade or changes to a few parameters, and these can often be done remotely.”
Technicians are now empowered to monitor systems at multiple manufacturing plants at once. The cost savings on this are substantial. HMS Networks, a supplier of industrial communication and industrial IoT solutions, estimates that each trip a technician makes onsite for a machine fix costs $2,200.
The Future of RDP: Balancing Benefits and Security
Despite its advantages in data management and cost reduction, RDP remains a significant security risk. Ongoing real-time monitoring of RDP usage is crucial for detecting and mitigating misuse. For a comprehensive analysis of RDP's security implications, our Spotlight Report on RDP offers an in-depth look at malicious RDP usage, emphasizing the importance of vigilance in its application.

