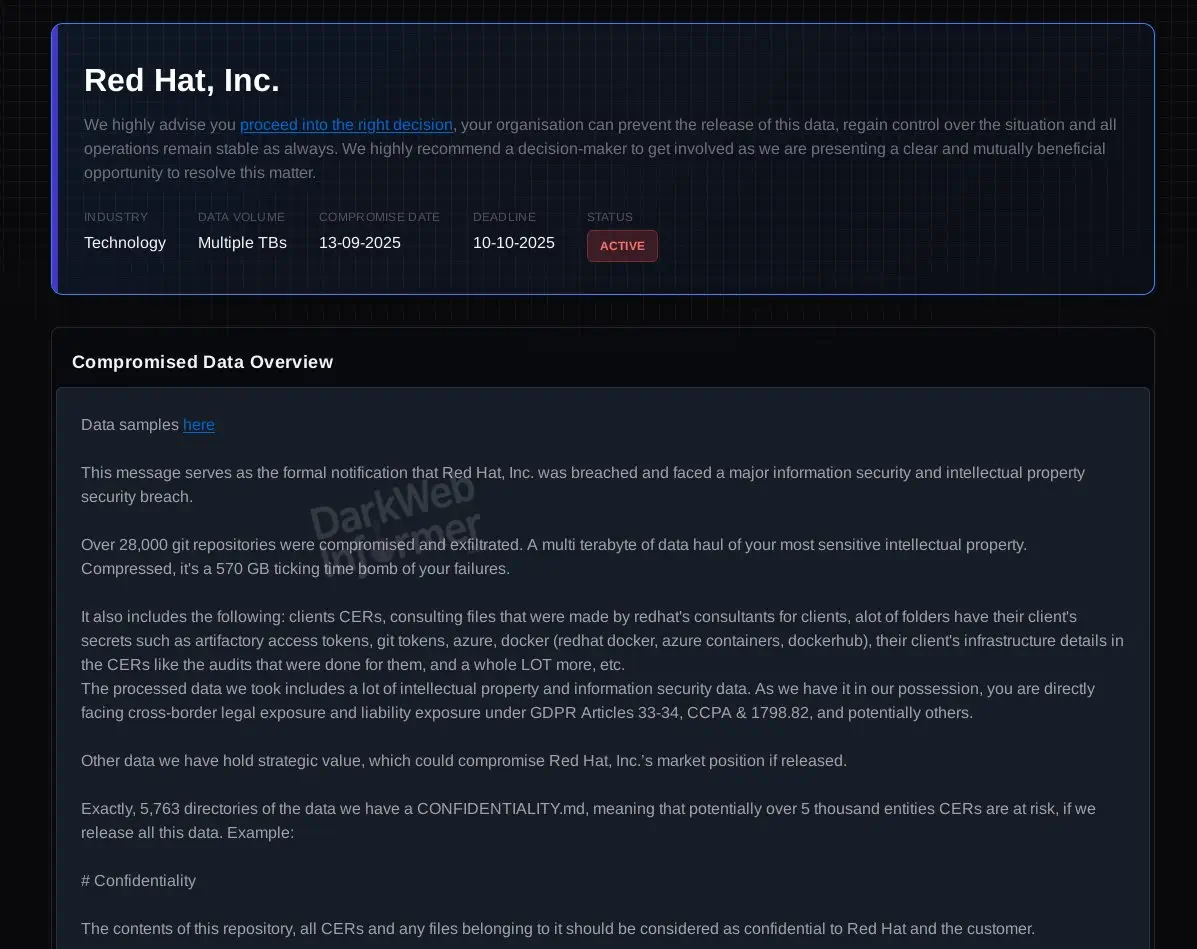
An extortion group calling itself the Crimson Collective claims to have stolen nearly 570GB of compressed data from Red Hat’s self-managed GitLab instance. Among the files were around 800 Customer Engagement Reports (CERs), documents that often contain sensitive infrastructure details, authentication tokens, and configuration data from client environments.
This type of data provides attackers with a ready-made blueprint to move into downstream customer networks, amplifying the impact far beyond the initial breach. The potential impact spans across industries, with the group publishing a directory listing that included well-known organizations in finance, healthcare, retail, government, and defense.
Red Hat GitLab Breach Explained: What Happened
Red Hat confirmed that an unauthorized party accessed and copied data from its self-managed GitLab instance. The company emphasized that the breach was limited to its consulting division and did not affect its broader product ecosystem or software supply chain.
The attackers, however, claim they found authentication tokens, database URIs, and private details inside both code and CERs, and that these were leveraged to reach customer environments. While Red Hat has contained the incident and is notifying impacted customers, the group has already publicized repository and CER listings dating back to 2020.
Who is the Crimson Collective (and How They Tie to Scattered LAPSUS$ Hunters)
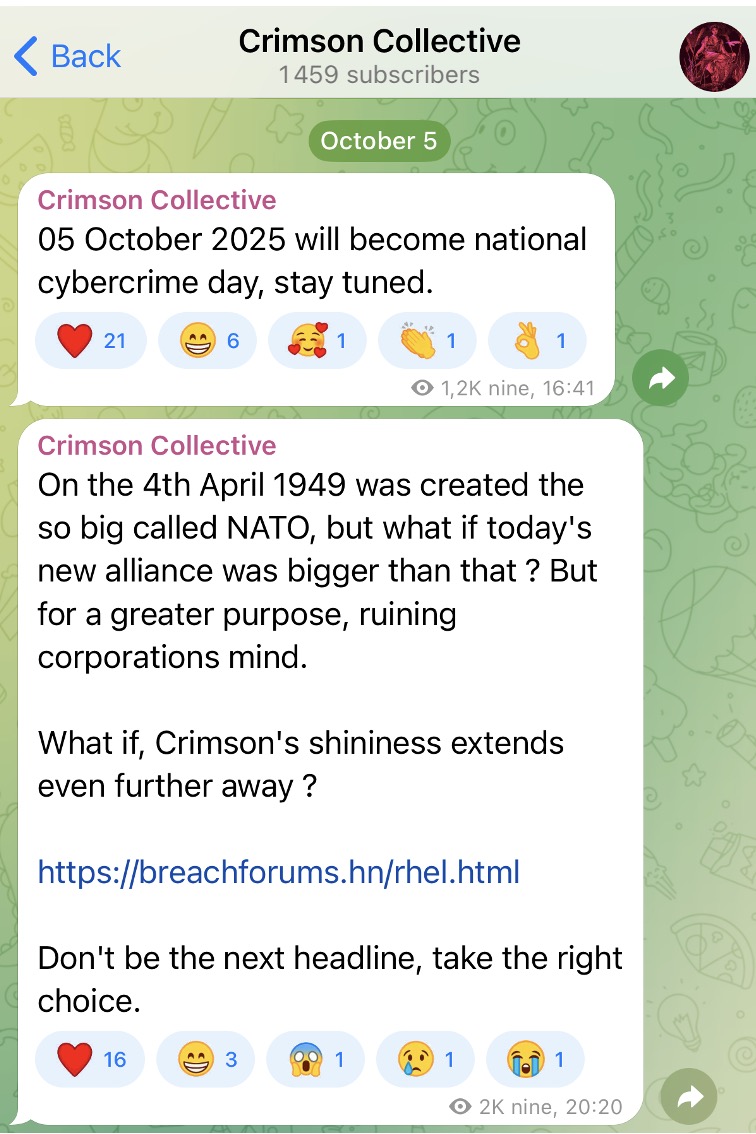
The Crimson Collective is a newly emerged cyber extortion group that first surfaced in late September 2025. Their tactics combine publicity stunts with serious breaches, using a Telegram channel to broadcast stolen data and pressure victims. Before targeting Red Hat, the group defaced a Nintendo web page to draw attention to their presence. Shortly after, they claimed responsibility for breaching Claro Colombia, alleging the theft of millions of customer records.
Unlike nation-state actors, Crimson Collective openly states that they are driven by financial gain.
Update 05/10/25: The Crimson Collective now appears to be cooperating with Scattered LAPSUS$ Hunters. Leaked materials show that some of Crimson’s stolen Red Hat data was actually surfaced on the Scattered LAPSUS$ Hunters website, and public messaging suggests cooperation between the two entities. Though Scattered LAPSUS$ Hunters announced through a farewell letter that it would “go dark” earlier last month, security researcher remained skeptical.
The Crimson Collective may not be an entirely new entity (maybe the new name of The Com?).
Why the Crimson Collective Targeted Red Hat
Consulting repositories often contain customer-specific configurations, deployment details, and privileged access tokens. For attackers, this is not just data theft: it is an entry point into multiple organizations at once.
Examples of what repositories and consulting documents may expose:
- Hardcoded secrets and authentication tokens
- Infrastructure-as-code revealing network topology
- Service accounts with privileged permissions
- Project specifications detailing customer environments
This makes consulting artifacts a high-value target. One successful breach can ripple outward, impacting hundreds of organizations that trusted the consulting provider.
How the Red Hat Consulting Breach Impacts Customers
For customers named in these CERs, the risks are very real. Stolen authentication tokens or exposed configuration details can open the door for attackers to:
- Compromise identities and unauthorized system access
- Move lateralt across critical infrastructure
- Steal data, disrupt services, or launch extortion campaigns
The challenge is visibility (and even the Crimson Collective agrees on that!). Traditional tools are built to block known threats at the perimeter. But with stolen credentials, attackers look like insiders. By the time their activity is flagged, the damage may already be done.
If you are a Vectra AI customer, here’s what to watch for in your environment:
- Unusual use of authentication tokens or service accounts, especially outside of expected hours or geographies.
- Signs of reconnaissance activity against your Active Directory, cloud environment, or internal network.
- Abnormal lateral movement patterns, particularly from accounts tied to consulting projects or administrative access.
- Indicators of data staging or exfiltration, such as large transfers or compression events from atypical hosts.
Vectra AI customers benefit from real-time AI-driven detections that make these behaviors visible, even when attackers appear legitimate.
How Vectra AI Sees What Other Tools Miss
Most security tools stop known threats or block malicious files. That approach fails when attackers are armed with valid credentials or stolen consulting artifacts. In those cases, they walk in with trusted access and traditional defenses struggle to distinguish attacker from employee.
The Vectra AI Platform takes a different approach. It detects behaviors attackers cannot hide, such as reconnaissance, credential misuse, lateral movement, privilege escalation, and exfiltration. By continuously analyzing identity and network traffic, Vectra AI surfaces the subtle but consistent signals of compromise that other tools overlook.
For security teams, this delivers:
- Fewer blind spots: Complete visibility across identity, cloud, SaaS, and on-premises networks, without the need for agents.
- Faster clarity: AI-driven detection that cuts through false positives and alert fatigue.
- Actionable intelligence: Clear context on what is happening, where, and how to respond.
With Vectra AI, attackers may steal documents and tokens, but they cannot operate undetected in your environment.
See how Vectra AI completes your existing technology stack by exploring our self-guided demo, or get in touch with us right away if you believe your organization may be at risk.

