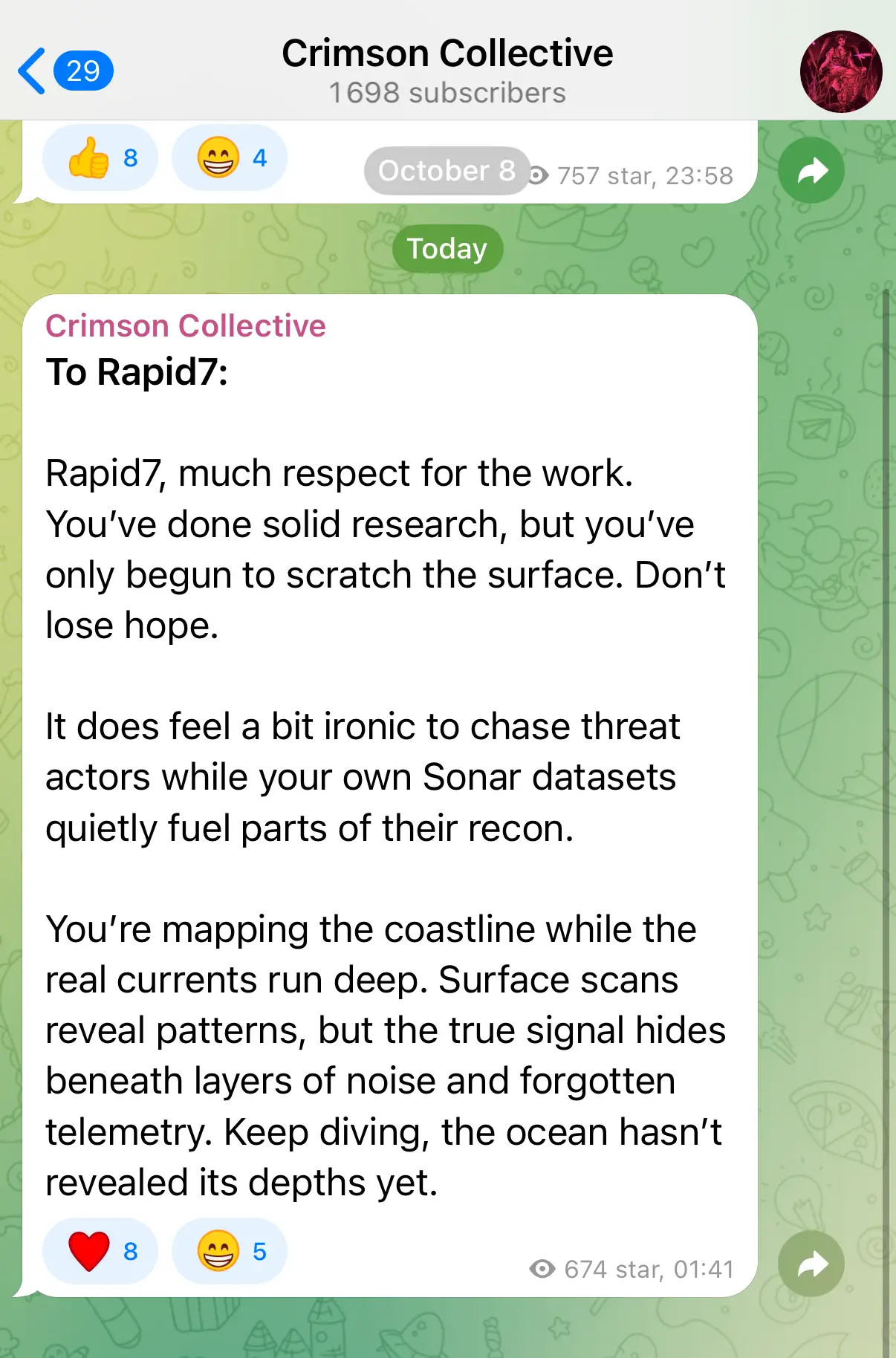
“You’re mapping the coastline while the real currents run deep”
Crimson Collective, on October 9th 2025
When Crimson Collective left a cryptic message directed at Rapid7, it wasn’t just a taunt. It was a reflection of how threat actors view the cybersecurity community’s approach to detection. Their words carried a warning: defenders are still too focused on what’s visible at the surface, while attackers thrive in the unseen depths.
A Brief Recap of Crimson Collective’s Activity
According to research published by Rapid7, Crimson Collective operates in cloud environments, particularly AWS, using tactics that blend into legitimate administrative behavior. The group gains access through leaked or long-lived credentials, escalates privileges by manipulating IAM roles and policies, and uses native cloud APIs for reconnaissance, data staging, and exfiltration.
Rather than relying on malware or exploits, Crimson Collective abuses what already exists within cloud infrastructure. Every API call, permission change, and snapshot request is valid on its own, but together they form a malicious pattern that’s difficult to spot through static rules or surface telemetry alone.
Their direct reference to Rapid7 hints that the group was aware of the company’s visibility in the threat intelligence space, possibly through prior detection attempts or by reading the published analysis itself.
The Irony Behind “Your Own Datasets Fuel Their Recon”
In their message, Crimson Collective hinted at a painful truth: the same data defenders use to understand their environment can also be leveraged by attackers. Publicly available scanning data, open-source telemetry, and configuration repositories often reveal information about an organization’s exposed assets, cloud endpoints, or even software versions.
For threat actors, this information shortens the reconnaissance phase. What was once manual probing is now automated and enriched by the very transparency that enables defensive research. The irony is that visibility cuts both ways. Defenders map the attack surface to reduce risk, while attackers use that same visibility to plan their intrusion.
This highlights a core challenge for security teams: data collection alone does not equal protection. What matters is how that data is analyzed, contextualized, and correlated in real time to expose malicious intent.
“Mapping the Coastline While the Real Currents Run Deep”
Crimson Collective’s ocean metaphor perfectly captures the state of modern detection. Surface scans and configuration assessments are like mapping coastlines: they show what’s exposed but not what’s moving underneath.
The “currents” represent the constant flow of legitimate activity in cloud environments where thousands of API calls, identity changes, and resource interactions make up the operational fabric of the enterprise. Hidden within that motion are the subtle anomalies that indicate compromise.
Traditional scanning tools reveal static risks, but they cannot see the behavioral evolution of an attack. The true signal, as Crimson Collective put it, hides “beneath layers of noise and forgotten telemetry.” Detecting that signal requires persistent visibility and contextual understanding across every layer of the cloud and identity infrastructure.
Seeing the Depths: How Vectra AI Changes the Perspective
The message from Crimson Collective is a challenge to every defender: stop looking at the surface and start understanding behavior beneath it. That is precisely what the Vectra AI Platform enables.
Vectra AI provides continuous, agentless visibility across hybrid and cloud environments, turning telemetry into insight. By analyzing behaviors across identity, network, and cloud, Vectra uncovers hidden attack progressions such as privilege escalation, lateral movement, and data staging before exfiltration occurs.
Instead of relying on known indicators or configuration states, Vectra’s AI models learn what normal activity looks like and detect when it shifts toward malicious intent. This allows security teams to identify the “deep currents” of attacker behavior in real time, even when every action appears legitimate on the surface.
Vectra’s AI Stitching Agent correlates identity activities across on-prem data centers, Entra ID, and cloud environments such as AWS to reveal the original compromised identity - accelerating key SOC metrics tied to investigations (MTTI) and response (MTTR). Its Kingpin technology analyzes billions of AWS actions, traces them back to the true identities behind temporary credentials (roles) across accounts and regions, and prioritizes critical accounts - saving at least 30 minutes per investigation.
Turning Awareness into Advantage
The Crimson Collective message reminds us that attackers already understand our tools and datasets. The advantage now lies in how intelligently we interpret and correlate the data we have. With Vectra AI, defenders gain that depth of vision, transforming raw telemetry into proactive detection.
Crimson Collective’s words were meant to provoke, but they also reveal a truth defenders can learn from: the future of threat detection isn’t about more data, it’s about deeper understanding.
Explore how the Vectra AI Platform exposes what others overlook. Experience the self-guided demo to see how depth transforms detection.

