Vectra Investigate: See the Full Story Behind Every Threat
In today’s modern hybrid network environment, detection alone isn’t enough—security teams must grasp the full narrative behind every incident. The landscape has evolved: modern attacks don’t stop at one vector or endpoint. They pivot, escalate privileges, blend in with legitimate behavior, and exploit network, identity and cloud systems across increasingly complex infrastructures.
Yet fast, actionable insights remain elusive. Data is often siloed, fragmented, buried behind complex tools, or simply unavailable—forcing analysts to manually stitch together information across systems just to answer basic questions: Where did the attack start? What else was impacted? How long has it been active?
This is where Vectra Investigate comes in. As part of the Vectra AI Platform, and backed by our leadership position in the Gartner Magic Quadrant for Network Detection and Response (NDR), Vectra Investigate complements our AI detections, to provide rich, unified, and easily accessible metadata to support rapid, in-depth investigations and threat hunting.
Vectra Investigate is powered by enriched metadata from over 25 sources and 300+ fields, providing up to 30 days of historical visibility across your modern network. By layering AI-driven context onto threat telemetry, Vectra Investigate helps security teams reduce risk, resolve threats , accelerate investigations, and enable proactive threat hunting—all from the same console .
With intuitive access to insights—via query-less investigations, expert hunts, and now, SQL Search and Saved Searches—security teams can go beyond alerts to answer critical questions at speed. According to IDC The Business Value of Vectra AI, organizations using Vectra Investigate have seen a 50% reduction in time spent investigating security alerts, translating to faster decisions and more efficient response.
Customers rely on Vectra Investigate to:
- Maintain continuous visibility into emerging risks like unmanaged shadow IT tools (e.g. DeepSeek) and legacy exposures such as weak ciphers
- Conduct complete incident investigations that correlate both NDR and EDR signals—not just alerting, but uncovering the full scope and impact
- Power threat hunting for lateral movement, compliance validation across regions and roles, and network troubleshooting for performance anomalies
- Answer the high-impact questions that lead to faster decisions, deeper understanding, and more effective outcomes
Unlock faster, deeper investigations through SQL Search and Saved Searches
With the general availability of SQL Search in the Vectra AI Platform, your team now has the power to uncover deep insights from your metadata across cloud, identity, and network environment. Whether you’re tracking data exfiltration, uncovering rare logins, or exposing stealthy beaconing activity, SQL Search gives analysts full flexibility to explore threat signals. But we also know that speed and accessibility are just as critical. That’s why we’ve curated a library of pre-built queries. Saved Searches—ready-made searches – are designed by Vectra AI security analysts—to accelerate your investigations with just one click. This library will be regularly updated based on the latest threat research and attacker techniques, ensuring your team stays ahead of emerging threats.

Why This Matters for Your Team
- Advanced investigations, simplified: Run complex, multi-condition queries to find subtle attacker behaviors.
- Expert knowledge, instantly accessible: Saved Searches let junior and senior analysts alike pivot into deep investigations without writing a line of SQL.
- Ready for the future: This is just the beginning—natural language search and in-product threat hunting guides are coming soon.
Below are 6 practical search examples you can start using today from your Saved Searches tab:
1. Network: File Downloads Over Unsecured HTTP
Why: Attackers often use HTTP to deliver payloads internally.
What it finds: Devices fetching potentially malicious file types over HTTP.
SELECT timestamp, orig_hostname, id.orig_h, id.resp_h, host, uri, user_agent,response_body_len
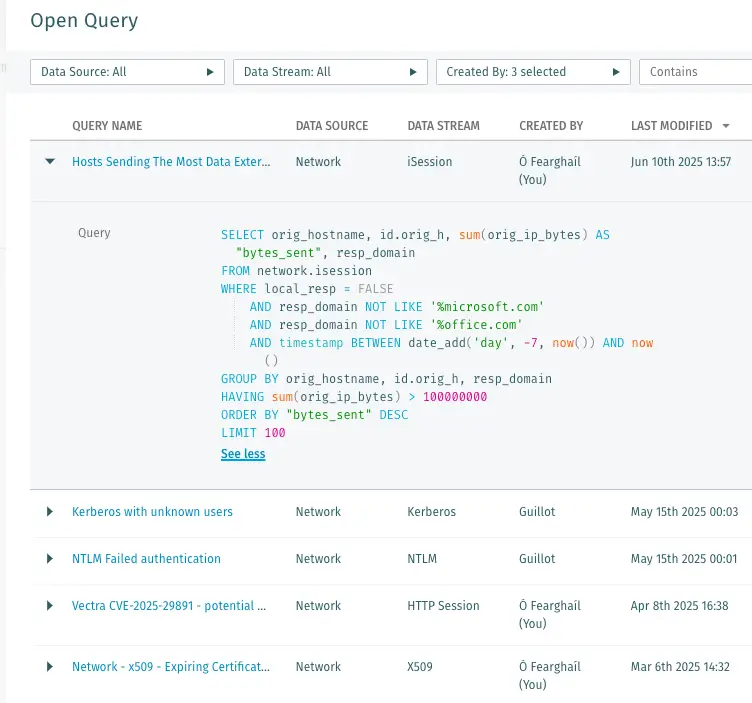
FROM network.http WHERE method != 'HEAD' AND (uri LIKE '%.ps1' OR uri LIKE '%.exe' OR uri LIKE '%.bat' OR uri LIKE '%.msi' OR uri LIKE '%.vb' OR uri LIKE '%.vbs' OR uri LIKE '%.dll' OR uri LIKE '%.reg' OR uri LIKE '%.rgs' OR uri LIKE '%.bin' OR uri LIKE '%.cmd' OR uri LIKE '%.hta') AND timestamp BETWEEN date_add('day', -7, now()) AND now() LIMIT 100 2. Network: Hosts Sending the Most Data Externally
Why: Exfiltration doesn’t always look noisy—volume matters.
What it finds: Hosts with the highest outbound data over the last 7 days.
SELECT orig_hostname, id.orig_h, sum(orig_ip_bytes) AS "bytes_sent", resp_domain
FROM network.isession
WHERE local_resp = FALSE AND resp_domain NOT LIKE '%microsoft.com' AND resp_domain NOT LIKE '%office.com' AND timestamp BETWEEN date_add('day', -7, now()) AND now() GROUP BY orig_hostname, id.orig_h, resp_domain
HAVING sum(orig_ip_bytes) > 100000000
ORDER BY "bytes_sent" DESC LIMIT 100 3. Network: Beaconing to Rare Destinations
Why: Targeted implants often communicate with infrastructure unique to one host.
What it finds: Destinations with repeated communication from only a single device.
SELECT resp_domains,
COUNT(DISTINCT id.orig_h) AS "unique_hosts",
SUM(session_count) AS "total_sessions" FROM network.beacon
WHERE timestamp BETWEEN date_add('day', -7, now()) AND now()
GROUP BY resp_domains
HAVING COUNT(DISTINCT id.orig_h) = 1 AND SUM(session_count) > 20
ORDER BY "total_sessions" DESC LIMIT 100 4. DNS Query Containing “DeepSeek”
Why: Detect possible malware or AI-based tools like DeepSeek being used in your environment.
What it finds: DNS queries containing references to “deepseek”.
SELECT * FROM network.dnsrecordinfo
WHERE query LIKE '%deepseek%' 5. Entra ID: Unusual Sign-In Locations
Why: Unusual login patterns can flag compromised credentials or access abuse.
What it finds: Sign-ins from countries rarely or never seen in your environment.
SELECT location.country_or_region as "location", count(*) AS "signins"
FROM o365.signins._all
WHERE timestamp
BETWEEN date_add('day', -7, now()) AND now()
GROUP BY location.country_or_region
ORDER BY "signins" ASC LIMIT 100 6. AWS: Repeated Unauthorized or Failed API Calls
Why: Brute-force attempts or misconfigured automation often leave API failure trails.
What it finds: Entities making repeated failed AWS API calls, with full error context.
SELECT vectra.entity.resolved_identity.canonical_name, event_name, error_code,
COUNT(*) as "failureCount",
MIN(timestamp) as "firstSeen",
MAX(timestamp) as "lastSeen"
FROM aws.cloudtrail._all WHERE COALESCE(error_code, '') != ''
GROUP BY vectra.entity.resolved_identity.canonical_name, event_name, error_code
HAVING count(*) > 10
ORDER BY "failureCount" DESC LIMIT 100 Get Started Now
With Vectra Investigate, your team moves faster, hunts smarter, and shares knowledge more effectively—ensuring suspicious activity doesn’t go unnoticed.
Use these searches today via your Saved Searches library in the Vectra AI Platform or watch this demo to learn more.


