When attackers poisoned npm packages last week, the industry rushed to analyze how it happened and what code was injected. But the exploit itself isn’t the full story.
Whether the entry point is a phished maintainer, a rogue dependency, or a third-party supplier, the initial compromise is only step one. What comes after matters just as much. Once malicious code runs inside your environment, attackers use that access to move laterally, escalate privileges, exfiltrate data, or set the stage for ransomware.
For SOC teams, spotting poisoned code is important, but equally critical is detecting the attacker behaviors that follow once malicious code is running.
How the npm Exploit Unfolded
The recent exploit did not come from a vulnerability in npm itself. Instead, it began with a classic case of social engineering. Attackers sent a phishing email to popular npm maintainers, posing as official support and urging them to “revalidate” their accounts. One maintainer, responsible for several widely used packages, entered both credentials and a one-time 2FA code into the attacker’s fake portal. This gave the attackers full control of the account, despite two-factor authentication being enabled.
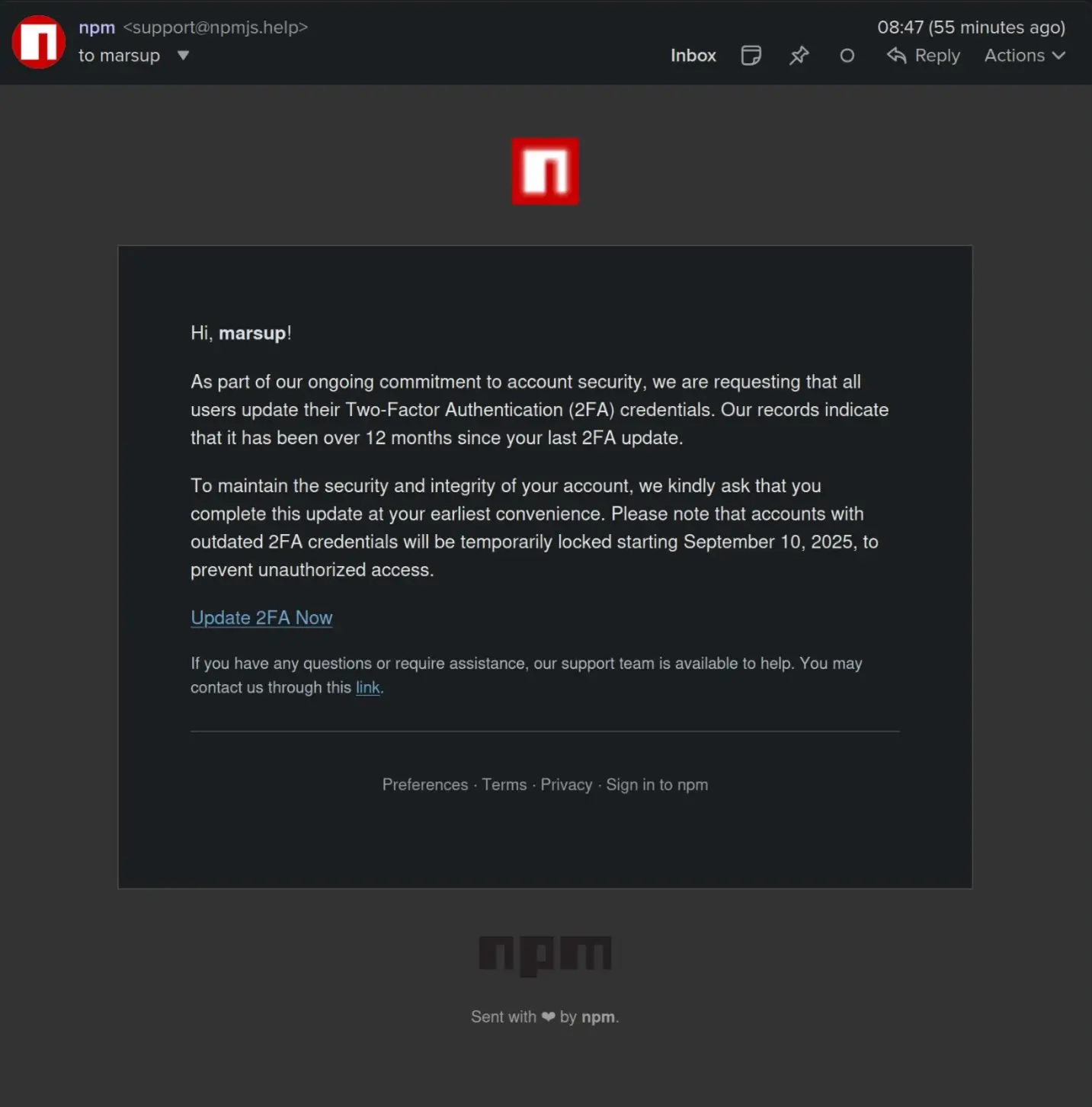
With access in hand, the threat actor quickly published new versions of trusted packages such as chalk, debug, supports-color, and others. These packages are foundational building blocks for countless applications, downloaded billions of times each week. The compromised updates contained obfuscated JavaScript designed to execute inside web browsers.
The malicious payload acted like a man-in-the-browser attack. It hooked into browser APIs, monitored network requests, and intercepted crypto wallet transactions. If a user attempted to send cryptocurrency, the malware silently swapped the recipient’s address with one controlled by the attacker. The end result was theft of funds, all while the transaction looked normal to the victim.
Although the malicious versions were available for only a short period, the scale of npm dependency usage meant the impact spread rapidly. Automated build systems in CI/CD pipelines pulled in the tainted updates almost immediately, forcing thousands of developers and organizations into incident response mode.
From Exploit to Execution: Why the First Step Doesn’t Define the Attack
In the npm case, the injected code was tuned to hijack cryptocurrency transactions. But that narrow goal doesn’t mean the risk was limited. Once malicious code is running inside an environment, attackers can do far more than swap wallet addresses.
With the same level of access, they could:
- Steal credentials and escalate privileges.
- Move laterally into cloud and identity systems.
- Create persistence through mailbox rules, OAuth apps, or redundant accounts.
- Exfiltrate data or stage ransomware.
Threat actors like Scattered Spider demonstrate how quickly access can be weaponized: pivoting into cloud and SaaS platforms, manipulating mailbox permissions, creating backdoor trust relationships, and probing critical workloads. From there, attackers move laterally to reach sensitive data and exfiltrate it. This is the true danger SOC teams must prepare for: not just the implant, but the cascade of attacker behaviors that follow.
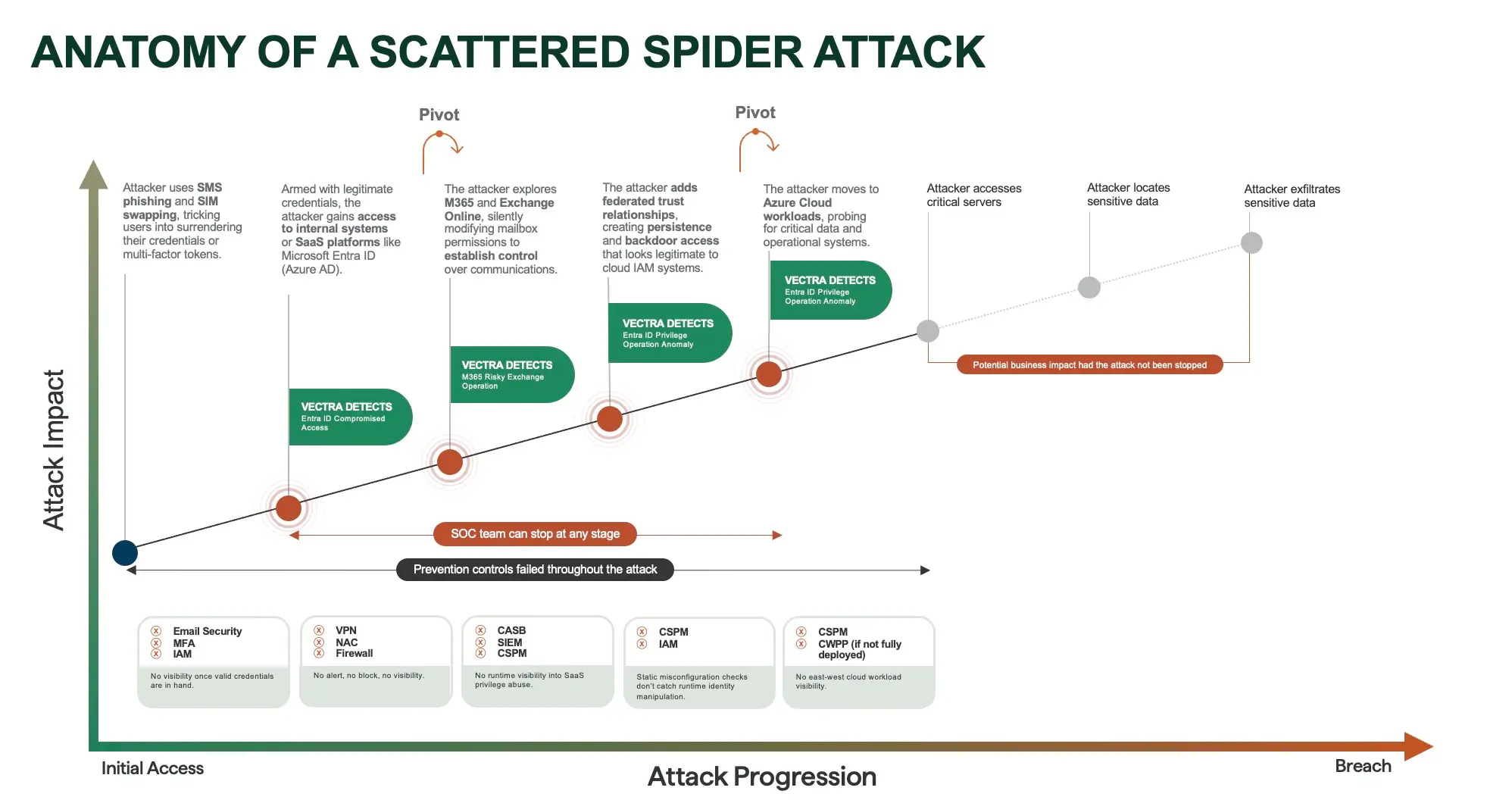
Why SOC Teams Should Care
For SOC teams, the npm exploit is a reminder that supply chain compromises are not just a developer concern. Prevention tools and SCA scans play an important role in identifying vulnerable or malicious packages, but they stop at the point of code analysis. What they cannot provide is visibility into how attackers use that access once poisoned code is running.
That responsibility sits squarely with the SOC. The challenge is not only to understand that a compromise occurred, but to detect how it reshapes attacker workflows in your environment. This means watching for behaviors that prevention tools miss: persistence being established in identity systems, credentials abused to pivot into SaaS and cloud platforms, or network activity that signals data staging and exfiltration.
Whether the entry point is npm, PyPI,3CX,MOVEit, or the next third-party supplier, the exploit is only the beginning. The impact is determined by how quickly you can surface and respond to the behaviors that unfold afterward.
Closing the Security Gap with Vectra AI
The npm exploit shows how quickly trust in software supply chains can be turned against you. Even if the initial goal was cryptocurrency theft, the same access could have been used to steal credentials, escalate privileges, or exfiltrate data. That’s why SOC teams need defenses that don’t just analyze code but continuously watch for how attackers behave once they’re inside.
The Vectra AI Platform provides that visibility. By monitoring identity, network, and cloud environments in real time, Vectra AI detects the behaviors adversaries rely on to expand their foothold and achieve their objectives. Whether malicious code arrives through a poisoned package, a SaaS account phish, or a compromised third-party provider, Vectra AI surfaces the attacker’s actions and gives SOC teams the context to respond before damage escalates.
Explore our self-guided demo to see how Vectra AI closes the gap and ensures that when prevention fails, detection and response are ready.

