Growth, success and notoriety are generally viewed as healthy problems to have for a business, but as the great Biggie Smalls tried to warn us over two decades ago—sometimes “Mo money” means “Mo problems.” Now, I am not so sure Biggie was referring to “Mo problems” in terms of cyberattacks, but it’s no secret that attackers have an attraction to large targets—so why is it always a shock when we see massive breaches reaping havoc on organizations that thought they were doing everything they could to cover all their bases?
Well, that’s the frustrating part because organizations continue to increase their cybersecurity spending—in fact, the recent Gartner 2021 CIO Agenda Survey cites cybersecurity as the top priority for new spending. There’s no one thing we’re doing wrong to bring on an attack or a breach, but with the attack surface continuing to expand, there is a need to update our thinking in how we approach defending these new surfaces.
Cloud adoption and digital transformation has certainly expanded the attack surface, but where would we be this last year without many of the cloud applications that help keep everyone connected and productive? Another area of the attack surface that has been overlooked is the supply chain, which we’ve all learned can be a vulnerable area after witnessing the SolarWinds supply chain attack earlier this year.
So, what is a supply chain attack?
Supply chain attacks refer to when an attacker gains access to your system through an outside partner such as a supplier or a service provider. One way to think about it, is that as you adopt new services or partners to help your business or organization grow—your supply chain expands, and so does your attack surface.
As far as targets go, any company that produces software or hardware for other businesses or organizations could be a potential target for a supply chain attack. The reality is that there’s a large opportunity for attackers if they’re able to compromise popular software due to the access it would provide to all of the businesses that leverage it. Understanding that cybercriminals view the supply chain as a potentially massive pay day is important, but it’s equally important to recognize that focusing on just trying to stop or prevent a supply chain attack could also lead you into trouble.
There’s a mindset that these types of evasive supply chain attacks can be stopped, but if that was the case then how did the SolarWinds hackers go undetected for nine months? We’re talking about major tech companies that were impacted by this attack—it’s not like they didn’t have security teams and tools in place. To get a better understanding, we took a look at a recent supply chain attack to see how the criminals utilized access to a widely deployed vendor’s product to gain access to many organizations’ local area networks. You can find the full details in our most recent Spotlight Report—Vision and Visibility: Top 10 Threat Detections for Microsoft Azure AD and Office 365, but for now let’s get into some of the quick takeaways.
One of the things that stands out about supply chain attacks, is that with some of the most recent events like SolarWinds—the attackers have shown significant effort and skill in evading preventative controls that involve network sandboxes, endpoint and multi-factor authentication (MFA). The tactics supply chain attackers use to bypass preventative controls include:
- Making extensive checks to ensure that it was not in a sandbox or other malware analysis environment.
- Use of code signing and legitimate processes to evade common endpoint controls.
- Novel in-memory dropper to evade file-based analysis in distributing the command and control (C2) beacon.
- MFA bypass using stolen security assertion markup language (SAML) session signing keys.
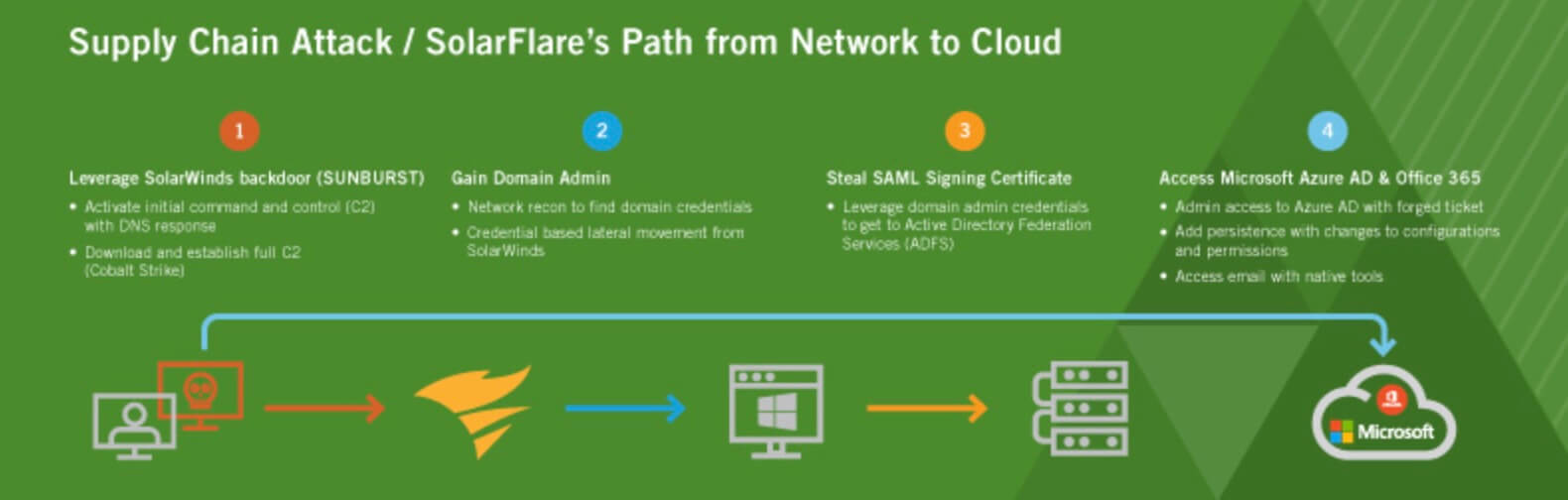
The full report goes into much more detail and even shows how hackers can progress an attack through the environment from the initial backdoor all the way to the cloud. It also notes the level of skill and focus required to cleanly bypass endpoint controls is a tribute to recent advances in endpoint detection and response (EDR). This is an important reminder that a determined and sophisticated adversary will always be able to bypass prevention and endpoint controls.
So, what do we do—just assume we’re going to get breached? Well, yeah that’s actually part of it, along with having the right tools and support in place when you do so the attack can be contained. One of the things we did when collecting data for the Spotlight Report mentioned above was to show how the reported actions of a supply chain attack would map back to Vectra’s defined threat detections. For example, if a hacker forged SAML tokens to gain access to Azure AD and Office 365, bypassing MFA and other security posture validations—this action would trigger a Vectra detection, alerting the security team about the issue.
This is just one example, but make sure you get all the details about how actions taken by attackers could map back to a devastating supply chain attack.
Get your copy of the report today! And, to hear a detailed assessment from Vectra’s Technical Director, Tim Wade, and our CMO, Jennifer Geisler, don't miss our webinar on Tuesday, June 8 at 8:00 am PT | 11:00 am ET | 4:00 pm BST | 5:00 pm CET.

