As long as I can recall, enterprises have always relied on prevention and policy-based controls for security, deploying products such as antivirus software, IDS/IPS and firewalls.
But as we now know, and industry research firms have stated, they aren’t enough to adequately deal with today’s threat environment, which is flooded by a dizzy array of advanced and targeted attacks.
In an effort to provide some solid direction, Gartner has advised information security architects to do the following:
- Shift your security mindset from “incident response” to “continuous response” by assuming that your systems are compromised and require continuous monitoring and remediation; and
- Adopt an adaptive security architecture to protect against advanced threats using Gartner’s 12 critical capabilities as the framework.
Components of an adaptive security architecture
The adaptive security architecture that Gartner refers to provides continuous, pervasive monitoring and visibility. "To enable a truly adaptive and risk-based response to advanced threats, the core of a next-generation security protection process will be continuous, pervasive monitoring and visibility that are constantly analyzed for indications of compromise.”
“Enterprise monitoring should be pervasive and encompass as many layers of the IT stack as possible, including network activity, endpoints, system interactions, application transactions and user activity monitoring.”
“Improved prevention, detection, response and prediction capabilities are all needed to deal with all types of attacks, 'advanced' or not. Furthermore, these should not be viewed as siloed capabilities; rather, they should work intelligently together as an integrated, adaptive system to constitute a complete protection process for advanced threats.”
Because no single product can provide a complete security solution, vendors should partner with each other to deliver a comprehensive, interoperable solution to customers.
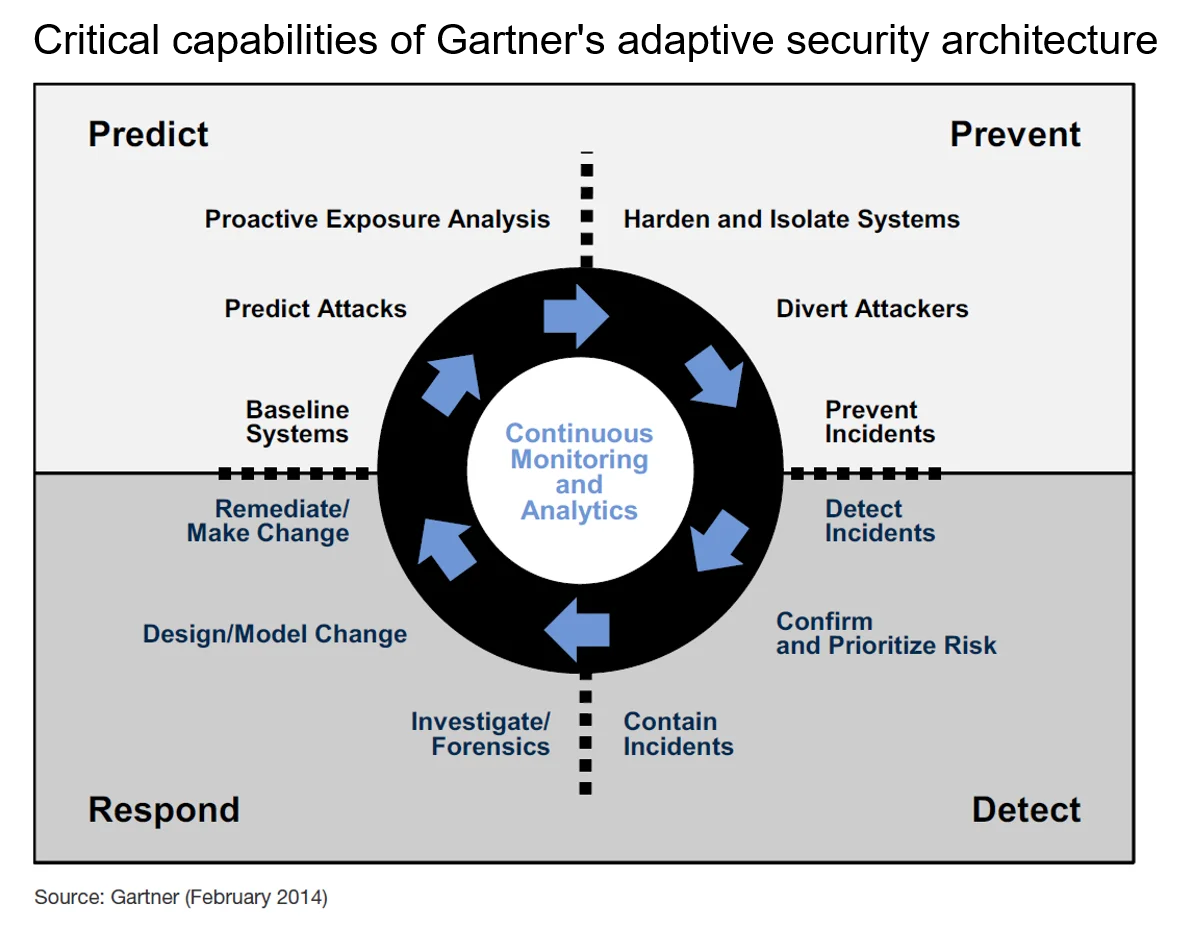
Functionality and processes that fall under the prevention category should reduce the attack surface by blocking known threats before they impact the enterprise.
Designed to find attacks that sneak past prevention security, good detection should reduce the dwell time of threats as well as any possible damage from them.
Response capabilities are needed to investigate and remediate security issues that are discovered, including forensic analysis, root cause analysis and recommend preventive measures to avoid future incidents.
Finally, predictive technology should incorporate information gleaned by the cybersecurity community in response to real-world events as well as anticipated threats.
Where do you go from here?
Operationally, you’ll be better off with integrated solutions that deliver an adaptive security architecture.
Use the research note Designing an Adaptive Security Architecture for Protection Against Advanced Attacks to evaluate your existing investments and competencies to determine where there are gaps. Also use this architecture to evaluate new vendors and solutions.
Insist on having continuous, pervasive monitoring and visibility of your entire network and ensuring that collected data is analyzed constantly for indications of compromise.
Also be sure that your security infrastructure supports integration with robust threat response solutions to ensure that host devices are quarantined, malicious processes are shut down, and other measures automatically occur to secure the enterprise.
By following these critical steps, your cybersecurity team can save an extraordinary amount of time and effort and they will be empowered to take prompt, decisive action before cyber attacks lead to data loss or damage.
How Vectra enables the implementation of an adaptive security architecture
For step-by-step information on how Vectra addresses the need for an adaptive security architecture, download this free compliance brief.
“Designing an Adaptive Security Architecture for Protection from Advanced Attacks,” by Neil MacDonald and Peter Firstbrook, 12 February 2014, refreshed 28 January 2016, ID G00259490, https://www.gartner.com/doc/2665515/designing-adaptive-security- architecture-protection

