With an increasing number of organizations adopting the cloud, cybercriminals are quickly following suit. IBM’s Cost of a Data Breach Report found 45% of all data breaches in 2022 were cloud based with the average cost of a breach coming in at $5 million.
It’s no longer a question of if, but when your organization will have to tackle a cyber adversary. With attacks being inevitable, choosing the right security tools is pivotal to optimize key SecOps metrics such as the time to detect, investigate and respond. We argue an advanced CDR (cloud detection and response) solution is the answer.
Sophisticated cloud compromises – the new normal
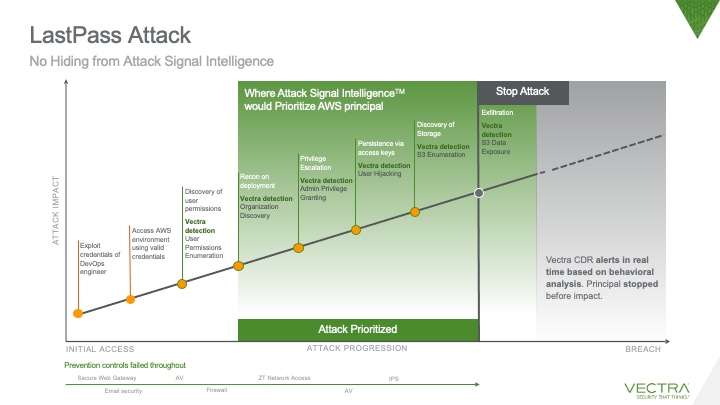
Many cloud vulnerabilities and attacks made headlines this past year but none more so than the attack on LastPass. The password management company suffered a series of attacks on their hybrid deployment, leading to the theft of sensitive customer data from their cloud storage resources.
What was initially reported as partial access to a single developer account was soon uncovered to be a full-blown stolen credential led exfiltration of encrypted customer password vault snapshots from LastPass’ cloud storage resources. The snapshots can potentially be brute forced by the attacker to crack password data. When the breach was first reported, it was indicated critical customer information including master passwords, data and personal information were totally secure. Unfortunately, this turned out to be false.
In security, trust is everything. Compromises of this magnitude lead to negative press, reprimand from the security community and often irreparable reputation damage.
Stolen Credentials – the preferred threat vector of choice for sophisticated cloud adversaries
When it comes to security, the right people and the right processes are important – but the right technology can make all the difference. In the LastPass attack, the cloud was exploited using valid, stolen credentials. This isn’t surprising. Today, most sophisticated attacks in the cloud stem from attackers using phishing campaigns to steal credentials and masquerade as legitimate users. Unfortunately, these vectors often bypass popular preventative security tooling an organization may have in place.
Post compromise, all actions taken from a compromised account can appear completely legitimate. This is exactly what happened at LastPass. Their communique alludes to this:
“Specifically, the threat actor was able to leverage valid credentials stolen from a senior DevOps engineer to access a shared cloud-storage environment, which initially made it difficult for investigators to differentiate between threat actor activity and ongoing legitimate activity.”
Remediating these sophisticated threats that stem from stolen credentials is challenging. In fact, the report from IBM security found attacks originating from stolen credentials have the longest mean time to identify (243 days) and the longest mean time to contain (84 days) of any initial vector in a data breach. Considering kill-chains in the cloud are shallow compared to on-prem networks, a savvy adversary with valid credentials doesn’t require much time to set up channels for persistence and move swiftly from initial access to stages of impact.
To protect cloud environments, it is imperative that SOC teams focus on identifying security incidents involving these adversarial tactics; perfectly suited to the capabilities of a CDR tool.
Based on a detailed analysis of the information shared in the LastPass communique, Vectra CDR would have surfaced numerous malicious behaviors throughout the kill chain and attributed them back to the compromised developer’s account. The investigations workflow would have provided an overview of all actions taken during the attack window, enabling the proverbial SOC team to shut down the attacker before stages of impact.
The importance of choosing the right security tools cannot be overstated
For businesses today, adopting the cloud is not an option, but a necessity. The benefits to cloud are many but the cost of migration is complexity. This adoption is fueling breakneck growth in capabilities offered by cloud providers. Case in point, AWS has added about 40 new services per year for the past 6 years!
This growth and adoption of cloud services has resulted in a larger and constantly changing attack surface. Organizations navigating this dynamic landscape must protect themselves not just against novel attacks, but also from already prevalent threats such as data exposure.
To maintain security hygiene, SOC teams rely on security tools. However, today there are hundreds of vendors providing discrete tooling options which can overwhelm SOC teams. With so much technical jargon being proliferated, it can be difficult to understand capabilities provided by various cloud security vendors. Furthermore, operationalizing these tools can be tedious and often results in the creation of unintended blind spots in the organization’s security posture.
Why Vectra CDR solution is imperative for stopping advanced cloud attacks
While preventative tools do a great job at providing visibility into cloud resources, misconfigurations, and non-compliant settings, they fall short when it comes to detecting novel attack vectors. These are precisely the threat vectors that should raise concern. In fact, in 2022, phishing and stolen credentials made up roughly 35% of all data breaches; significantly higher than those attributed to cloud misconfigurations (~15%). Relying on preventative and posture tools alone is bound to leave blind spots in a deployment and render it vulnerable to savvy attackers.
Powered by Vectra Attack Signal IntelligenceTM, Vectra CDR monitors all actions in a cloud environment and surfaces suspicious behaviors in real time. It leverages AI to go past event-based or simple baseline anomalies and instead focuses on behaviors — the TTPs at the heart of all attacks. The resulting signal clarity allows Vectra to promptly unearth sophisticated multi-step attacks so that SecOps teams can rapidly prioritize, investigate and respond to the most urgent threats. Be it an existing user behaving suspiciously or an external entity with compromised credentials acting within your AWS environment, Attack Signal Intelligence can tell apart suspicious actions from legitimate activity.
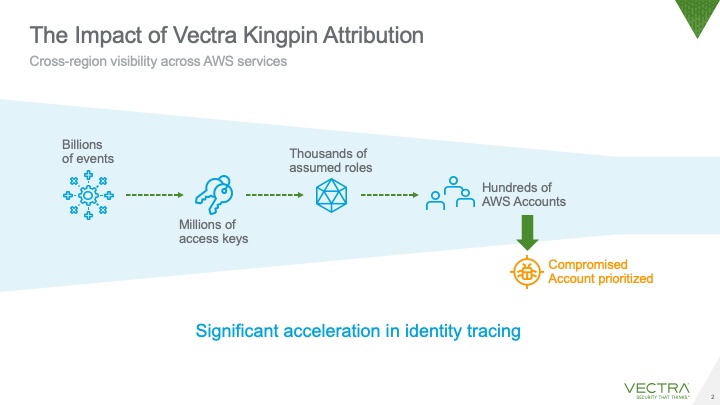
Additionally, a core tenet of Vectra CDR is AI-driven attribution. All observed behaviors are tied back to actionable principals even if they acted through chains of temporary credentials (roles). Vectra CDR also provides features to investigate these principals (including the power to query raw logs) and set up response workflows enabling the SOC to swiftly isolate suspicious principals and stop adversaries.
When it comes to dynamic cloud environments, it is imperative to adopt the right detective tools to provide comprehensive coverage within the boundaries of your cloud deployment. Regardless of where you are in your cloud journey, a CDR solution takes minutes to set up and empowers SecOps to swiftly hunt for advanced threats. In a world where breaches are the new normal, it should be a non-negotiable part of your SOC team’s arsenal.
See how it works, today! Reach out for a free demo of Vectra CDR.

