Suspicious Relay
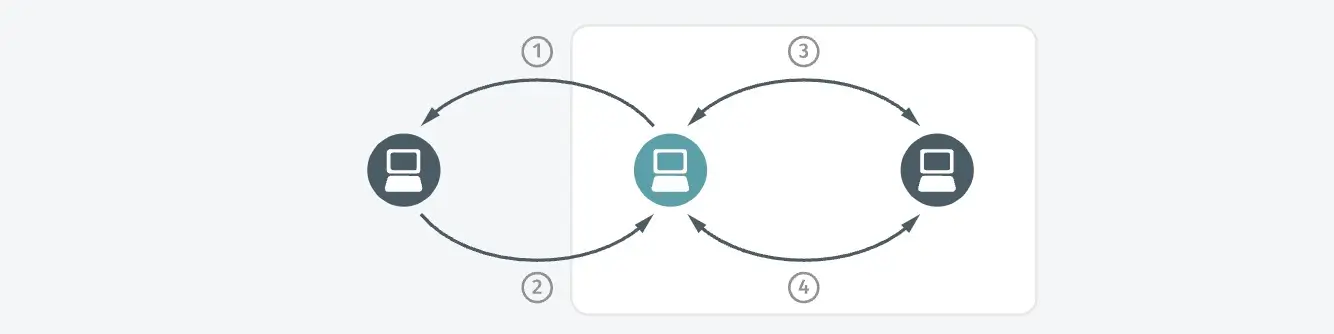
Detection overview
Triggers
- This host appears to be acting as a relay for communication between an external system to another internal host—relays of this type involve a first (external) leg and a second (internal) leg
- This host also has another active command and control detection
Possible Root Causes
- A host is compromised and is being used to relay information to and from a host deeper inside the network
- An internal host is hosting some form of approved proxy (e.g. SOCKS) to allow other internal hosts to communicate with the Internet through it
Business Impact
- An infected host which is enabling another internal host to hide its communication with the Internet by acting as a relay represents a high risk as this may allow a host which normally is not allowed to communicate with the outside to do so
- For hosts that have approved proxy software installed, ensure all the necessary security controls are in place to prevent unauthorized use
Steps to Verify
- Determine whether this host should be providing relay services to other internal hosts; if not, this is likely malicious behavior
- Look at the outside destination of the traffic and the payload of traffic, available in the PCAP, to determine what it being sent and where it is going; this will help further calibrate the risk
Suspicious Relay
Possible root causes
Malicious Detection
Benign Detection
Suspicious Relay
Example scenarios
Suspicious Relay
Business impact
If this detection indicates a genuine threat, the organization faces significant risks:
Suspicious Relay
Steps to investigate
Suspicious Relay
Related detections
No items found.