SECURING PATIENT CARE
The hidden risks in modern healthcare
Every medical device, patient record, and cloud workload is a target for modern attacks. But traditional tools can’t keep up on their own.
Unknown threats
evade detection
evade detection
Advanced attacks don’t use signatures. They hide in normal traffic, live off the land, and spread quietly across your network.
Vectra AI uses AI-driven behavioral detections to expose lateral movement, C2 communications, and privilege escalation that evade other tools.
Add AI-driven detection
CLOSING CRITICAL GAPS
Outsmart modern attackers targeting your healthcare data
The Vectra AI Platform, a leading NDR solution, gives healthcare security teams AI-driven behavioral detections to close visibility gaps, reduce complexity, catch unknown threats, and maintain compliance — across network, identity, and cloud.
Close visibility gaps
Your systems hold highly sensitive data — and attackers know it. But complex networks and IoT devices make it hard to see what's really happening. The Vectra AI Platform:
Monitors data centers, cloud workloads, and unmanaged medical IoT devices without adding agents or complexity.
Uses behavioral models to expose privilege escalation, lateral movement, and command-and-control activity that traditional tools miss.
Prioritizes and stitches related signals into clear narratives, giving healthcare SOC teams a fast, logical starting point for investigations.
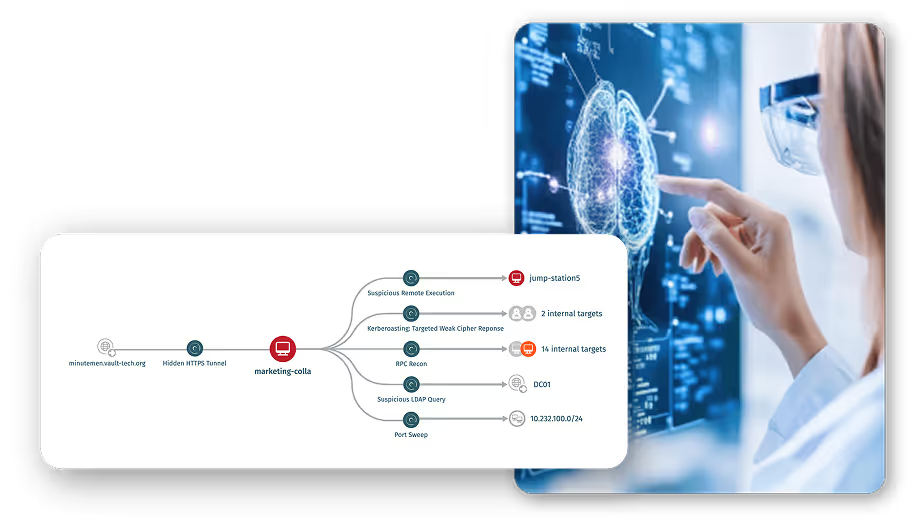

See how Bolton NHS correlates AI-driven detections with data from multiple tools to expose the truth about cyberattacks.
Read More

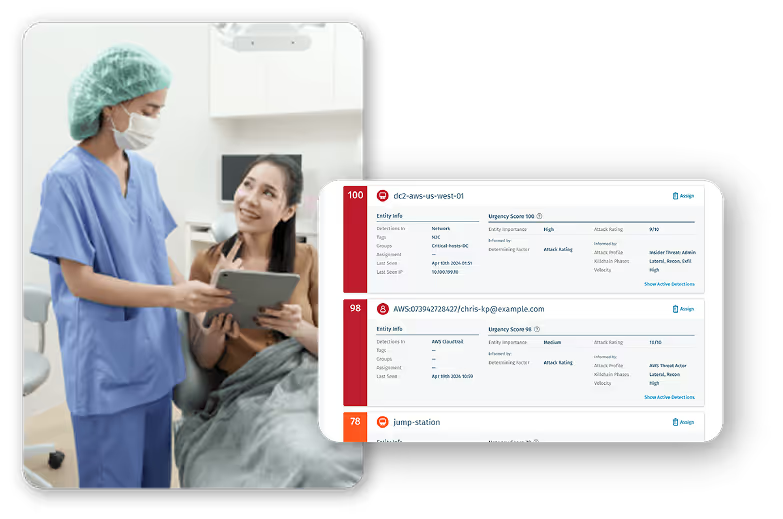
See how an Australian Private Health Fund reduced critical alerts by 80% while increasing visibility across cloud workloads, Teams, SharePoint, and Exchange.
Read More
Quiet the alert noise
Ambiguous alerts make it impossible to monitor abnormal activity. With the Vectra AI Platform:
AI-driven models correlate and compress multiple detections into actionable alerts, reducing noise and helping analysts focus only on true attacker behaviors.
Real-time detection and deeper context let SOC teams understand anomalies faster, cutting wasted time and improving MTTR.
Continuous monitoring across cloud, SaaS, and on-premises environments eliminates false positives and reduces critical alerts by 80% or more.

Reduce SIEM complexity
As your attack surface expands, so does the amount of data to index, enrich and analyze. By integrating the Vectra AI Platform with your SIEM, you can:
Pre-correlate and compress high-volume alerts before they hit your SIEM, cutting data ingestion costs and log noise.
Deliver high-fidelity detections enriched with context, so analysts can investigate faster without sifting through raw logs.
Streamline SOC workflows to prioritize attacker behaviors, not background noise.


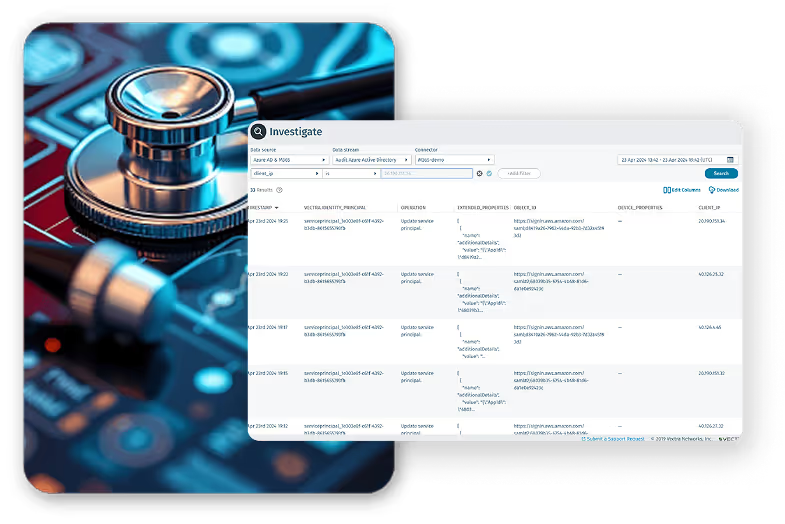
Discover how Pennine NHS moved away from log-based SIEM reliance with Vectra AI’s behavioral detection for one-click investigations.
Read More

According to IDC, SOC teams using the Vectra AI Platform are 40% more efficient and spend 50% less time investigating alerts. Download the report to learn why.
Download the Research Report
Increase analyst efficiency
Lean healthcare SOC teams can’t afford to waste time chasing false positives or tuning endless rules. Analysts need clarity to focus on protecting patient care. The Vectra AI Platform:
AI-driven models correlate and compress multiple detections into actionable alerts, reducing noise and helping analysts focus only on true attacker behaviors.
Allows analysts to prioritize high-value investigations by surfacing true attacker behaviors.
Provides automated threat detections capable of reducing the need for FTEs by 44%.
MODERN ATTACKS ON HEALTHCARE
Who’s targeting your patient data?
Attack groups like these relentlessly probe healthcare networks for gaps they can use to evade detection, steal data, and disrupt patient care.
Is your current technology security stack prepared to stop these attackers?
CUSTOMERS
Trusted by 2,000+ security teams to see and stop attacks






FAQs
How the Vectra AI helps you protect patient care
How does Vectra AI help protect patient data in hybrid healthcare networks?
Vectra AI applies AI-driven behavioral detections across all environments, from on-premises data centers to cloud apps to connected medical devices, giving SOC teams unified visibility and early warning of attacks that threaten patient data protection and EHR systems.
What makes Vectra AI a better IDS replacement for healthcare than traditional tools?
Legacy IDS/IPS systems generate noise and miss stealthy credentialed attackers. Vectra AI replaces this with high-fidelity detections tailored to hybrid healthcare network security, cutting false positives and surfacing lateral movement, command-and-control, and privilege abuse that legacy IDS can’t catch.
The Vectra AI Platform, recognized as a leading NDR solution, delivers unified coverage across network, identity, and cloud — making it ideally suited to detect and stop the advanced threats facing modern healthcare environments.
How does Vectra AI improve medical device cybersecurity?
Most medical and IoT devices can’t run endpoint agents. Vectra AI Platform provides agentless monitoring that protects patient devices and clinical OT systems, detecting suspicious behaviors like unauthorized access or abnormal communication before they impact care delivery.
Can Vectra AI help with ransomware healthcare protection?
Yes. Vectra AI detects ransomware behaviors such as privilege escalation, lateral movement, and abnormal encryption patterns in real time. By exposing these early in the kill chain, SOC teams can stop ransomware before it disrupts operations or compromises healthcare data security.
Explore how our network detection and response platform supports early ransomware detection across hybrid healthcare environments.
How does Vectra AI support compliance-driven healthcare security programs?
Meeting regulatory requirements for healthcare security (HIPAA, GDPR, and regional mandates) requires clear visibility and strong incident response. Vectra AI helps organizations prove patient data protection, reduce breach risks, and simplify audits, supporting cybersecurity compliance with NDR built for actionable detections and forensic context.
How does Vectra AI protect electronic health records (EHR) and PHI?
Attackers frequently target EHR and PHI databases. Vectra AI monitors identity systems, cloud workloads, and internal traffic to detect account takeovers and unauthorized queries that indicate an attacker moving toward sensitive healthcare data.
Can Vectra AI detect attacks on healthcare networks that use living off the land tactics?
Yes. Unlike signature-based IDS/IPS hospital network protection, Vectra AI analyzes behavior to spot attackers hiding in normal tools and protocols. This is critical for hybrid medical network security, where attackers often blend into routine clinical and IT activity.
How does Vectra AI integrate with penetration testing or red-team exercises in healthcare?
Vectra AI augments infrastructure penetration testing by detecting the same stealth tactics red teams use. Healthcare SOCs use these insights to validate defenses, prioritize risk, and harden hybrid healthcare network security against real-world adversaries.
Resources
How to secure patient care in a hybrid world
Get started today
Get an up-close look at how leading healthcare organizations protect patient care with Vectra AI.






