MITRE ATT&CK
Key insights
- 2025 ATT&CK Evaluations showed 100% detection coverage in select scenarios (Daily Security Review).
- Cloud adversary emulation was added to ATT&CK Evaluations in 2025 (MITRE).
- About 35% of global DDoS attacks come from IoT botnets (Growth Acceleration Partners).
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a comprehensive framework for understanding and analyzing cybersecurity threats. It is widely adopted in the cybersecurity community for improving threat detection, threat intelligence, and defense strategies. Here's an in-depth overview of MITRE ATT&CK:
Overview
Purpose of the MITRE ATT&CK framework
MITRE ATT&CK is designed to document and share knowledge about the behavior of cyber adversaries, focusing on the tactics, techniques, and procedures (TTPs) they use. This framework helps organizations understand the methods attackers use to compromise systems and helps improve defensive measures.
Structure of the MITRE ATT&CK framework
The framework is divided into different matrices based on operational domains, such as Enterprise, Mobile, and Industrial Control Systems (ICS). Each matrix is a collection of tactics and techniques relevant to that domain.
How security teams use the MITRE ATT&CK framework
MITRE ATT&CK is most valuable after suspicious behavior is observed across the modern network. In live investigations, analysts use ATT&CK to interpret what an attacker is attempting to accomplish, not simply to label individual events.
When multiple behaviors align to related techniques across different tactics and domains, ATT&CK helps teams reason about attacker intent. Analysts can distinguish between early reconnaissance, lateral movement, privilege abuse, or preparation for impact by understanding how behaviors connect over time. This allows investigators to move beyond reacting to isolated alerts and instead evaluate how an attack is progressing across the enterprise.
Recent ATT&CK Enterprise Evaluations showed portions of vendor detection coverage at 100% across real-world techniques, demonstrating the framework’s utility for measuring detection performance.
Security teams most often rely on ATT&CK to:
- Interpret attacker progression across tactics rather than focusing on single techniques.
- Align investigations, reporting, and post-incident reviews around a common behavioral framework.
In practice, ATT&CK provides a shared behavioral model for reconstructing attacker activity across network, identity, and cloud environments. It supports investigation workflows by giving analysts a consistent way to connect observations, validate hypotheses, and communicate findings clearly across security, IT, and leadership teams.
Why mapping activity to MITRE ATT&CK does not equal detection
MITRE ATT&CK documents how adversaries operate, but it does not determine whether observed activity represents an active attack. Many legitimate administrative and automated actions resemble ATT&CK techniques, especially in modern environments driven by cloud services, APIs, automation, and non-human identities.
Mapping an alert to a technique such as discovery or credential access does not, on its own, indicate urgency or risk. Without behavioral context, frequency, and correlation across domains, ATT&CK mappings can create false confidence or unnecessary investigation work.
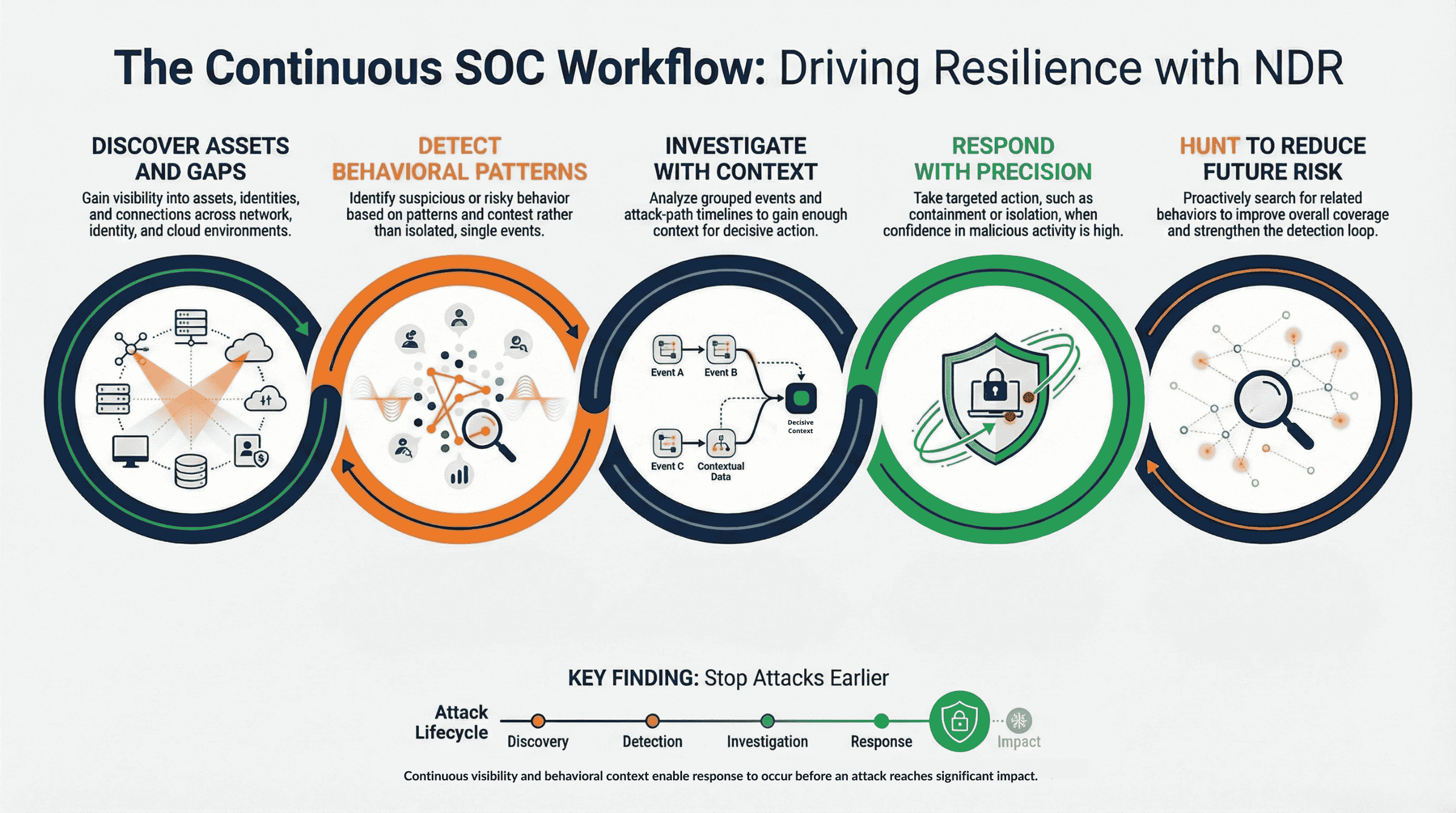
Effective detection does not come from labeling activity alone. It comes from observing behavior continuously, understanding how signals relate to one another, and applying context to determine intent and risk. This is why SOC workflows must connect discovery, detection, investigation, and response rather than treating them as separate functions.
This is also where MITRE ATT&CK differs from traditional SIEM workflows. While SIEMs collect and correlate events excel at log collection, they lack the behavioral framework provided by MITRE ATT&CK to interpret attacker intent. This structural limitation creates a visibility void that attackers exploit daily
This gap is where network detection and response (NDR) provides continuous visibility into live network behavior across on-premises, cloud, and hybrid environments, visibility that does not depend on logs or predefined rules. By observing how entities communicate, move, and change behavior over time, NDR supplies the behavioral signal needed to connect ATT&CK techniques into a coherent attack sequence.
In a continuous SOC workflow, NDR enables teams to detect behavioral patterns early, investigate activity in context, and respond before attackers reach their intended impact. This operational foundation allows ATT&CK to function as a practical investigative framework rather than a static reference model.
→ Read the Full Analysis: Why SIEM Can’t See and Stop Modern Attacks
MITRE ATT&CK across network, identity, and cloud environments
Modern attacks rarely stay within a single ATT&CK matrix. A campaign may begin with enterprise phishing, transition into identity abuse, and later involve cloud-specific actions such as privilege escalation, persistence, or resource manipulation.
ATT&CK provides a common language to describe these behaviors, but defenders must connect them across environments that operate as one interconnected system. Techniques that appear low risk in isolation can signal active compromise when they align across network traffic, identity behavior, and cloud activity.
Reflecting this cross-domain focus, the 2025 MITRE ATT&CK Evaluations expanded to include cloud adversary emulation scenarios, highlighting how defenses must correlate behaviors across traditional and cloud environments.
Using ATT&CK as a unifying framework helps security teams reason about attacks holistically. It enables defenders to understand how activity in one domain contributes to a broader campaign, rather than treating network, identity, and cloud events as separate incidents.
Key Components of the MITRE ATT&CK framework
Tactics
These are the adversary’s goals during an attack, representing the "why" of an attack. Examples of tactics include:
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Exfiltration
- Impact
Techniques
These describe "how" adversaries achieve their tactical goals. Each tactic includes multiple techniques, detailing specific methods adversaries use. For instance:
- Phishing (under Initial Access)
- PowerShell (under Execution)
- Credential Dumping (under Credential Access)
Sub-Techniques
These provide more granular details on specific methods within a technique. For example:
- Phishing: Spearphishing Attachment
- PowerShell: PowerShell Scripts
Procedures
These are the specific implementations of techniques by adversaries. They offer practical examples of how particular techniques and sub-techniques are executed in real-world scenarios.

Applications
- Threat Intelligence: Helps in mapping observed adversary behavior to known tactics, techniques, and procedures (TTPs) for better understanding and attribution.
- Detection and Mitigation: Provides a basis for developing detection rules, correlation searches, and security playbooks to identify and respond to threats.
- Security Assessments: Used in red teaming and penetration testing to simulate adversary behavior and evaluate the effectiveness of security controls.
- Incident Response: Aids in the investigation process by mapping the actions of an attacker during an incident to known techniques, assisting in identifying the scope and impact of the breach.
- Security Operations: Enhances the effectiveness of Security Operations Centers (SOCs) by providing a structured approach to monitor and respond to adversary activities.
Benefits
- Common Language: Standardizes the terminology and methodology for discussing cyber threats, enabling better communication across organizations and teams.
- Comprehensive Coverage: Provides extensive documentation of adversary behaviors, covering a wide range of tactics and techniques.
- Real-world Relevance: Continuously updated with real-world threat data and community contributions, ensuring its relevance and accuracy.
- Integration with Tools: Compatible with various security tools and platforms, facilitating seamless integration into existing security infrastructures.
What MITRE ATT&CK intentionally does not provide
MITRE ATT&CK is deliberately descriptive rather than prescriptive. It documents adversary behavior, but it does not tell organizations how to prioritize, respond, or measure risk.
The framework does not determine:
- Which techniques represent immediate risk in a specific environment.
- How quickly an attacker is moving or how far they have progressed.
- Whether activity is malicious or benign without additional behavioral context.
These limitations are a strength. By remaining vendor-neutral and observation-based, ATT&CK provides a stable reference model that organizations can apply across different environments, tools, and risk models.
How organizations operationalize MITRE ATT&CK over time
Organizations gain the most value from ATT&CK when they treat it as an ongoing operational framework rather than a one-time mapping exercise. Modern attack techniques evolve, environments change, and defensive coverage shifts continuously.
Over time, teams use ATT&CK to reassess detection coverage, refine hunting strategies, and evaluate whether controls align with real-world attacker behavior. This continuous application keeps security programs grounded in observed threats rather than static assumptions.
Operational use of ATT&CK supports long-term security maturity by ensuring defensive strategies evolve alongside adversary tradecraft and the changing shape of the modern network.
As attacks increasingly span identity, cloud services, and automation-driven infrastructure, the value of MITRE ATT&CK comes from how effectively teams can interpret behavior across these environments. Modern security operations depend less on static technique lists and more on understanding how attacker actions connect and evolve in real time.
For example, IoT botnets now account for roughly 35% of global DDoS attacks, underscoring the scale and coordination of modern adversary behavior that defensive frameworks like ATT&CK surface.
How the Vectra AI Platform uses MITRE ATT&CK to interpret attack progression
The Vectra AI Platform uses MITRE ATT&CK as a behavioral reference framework to help security teams understand how modern attacks unfold across the modern network. Rather than treating ATT&CK as a static mapping exercise or a detection mechanism, Vectra AI uses it to provide investigative context for observed attacker behavior across network, identity, and cloud environments.
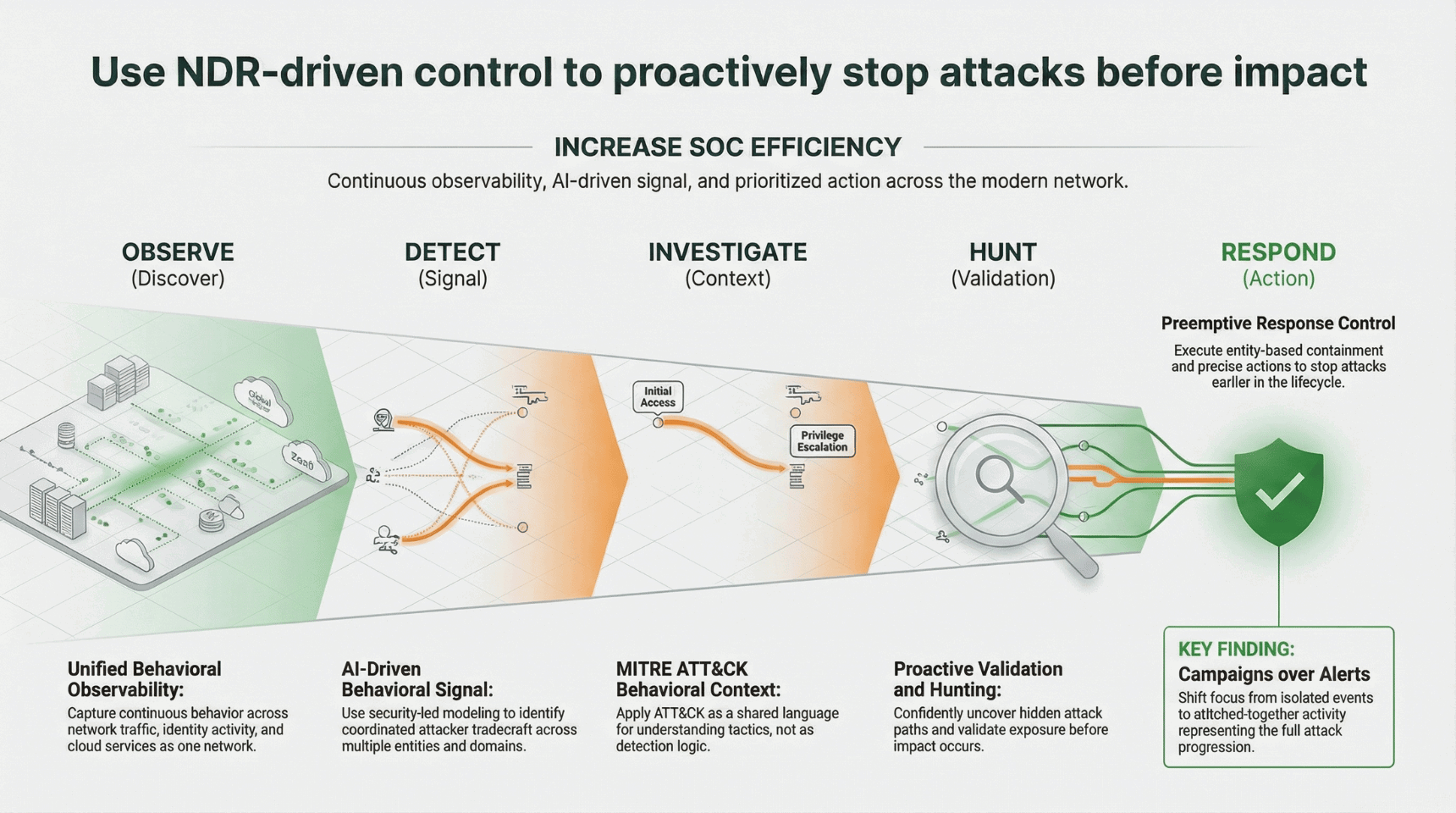
Vectra AI continuously observes behavior across Entra ID, Microsoft 365, Azure cloud, and on-premises networks, then aligns relevant behaviors to ATT&CK tactics and techniques. This gives analysts a clear, familiar way to understand what attackers are doing, how activity is progressing, and where it fits within known adversary tradecraft, without requiring manual correlation across siloed tools.
Key aspects of how Vectra AI applies MITRE ATT&CK include:
- ATT&CK-aligned behavioral context that helps analysts interpret observed activity across network, identity, and cloud as part of a broader attack sequence, not isolated events.
- Cross-domain correlation that connects behaviors spanning multiple ATT&CK tactics and environments, enabling teams to see how attacks form, move, and escalate across one unified attack surface.
- Attack Signal Intelligence™ enrichment that correlates ATT&CK-aligned behaviors over time to distinguish benign or isolated activity from coordinated attack campaigns in progress.
- Risk-based prioritization that evaluates ATT&CK-aligned behaviors in the context of entity criticality, behavioral patterns, and attack progression, helping teams focus on activity that represents real organizational risk rather than alert volume.
By combining ATT&CK-aligned context with continuous observability, AI-driven signal, and prioritized action, Vectra AI enables security teams to move from recognizing attacker techniques to understanding and acting on real attack progression across the modern network.
→ See how the Vectra AI Platform proves cyber resilience across the modern network
Related cybersecurity fundamentals
FAQs
How can organizations use the MITRE ATT&CK framework?
Organizations can use the MITRE ATT&CK framework to: Enhance threat intelligence and security operations by mapping observed attacks to specific tactics and techniques. Improve defensive strategies by identifying potential security gaps and prioritizing mitigations. Train security teams to recognize and respond to the methods used by adversaries. Benchmark security tools and processes against known threat actor behaviors to assess effectiveness.
How does the MITRE ATT&CK framework facilitate threat hunting?
The MITRE ATT&CK framework facilitates threat hunting by providing a structured methodology for identifying and investigating suspicious activities. Threat hunters can use the framework to map network and endpoint behaviors to known adversary techniques, helping to uncover stealthy attacks.
Can the MITRE ATT&CK framework help in regulatory compliance?
While the MITRE ATT&CK framework is not a compliance framework, it can indirectly support regulatory compliance efforts by enhancing an organization's threat detection, response, and overall security posture, which are critical components of many compliance standards.
How do organizations integrate the MITRE ATT&CK framework into their security operations?
Organizations can integrate the MITRE ATT&CK framework into their security operations by: Incorporating it into security information and event management (SIEM) systems for alerting and analysis. Using it as a basis for red teaming exercises and penetration testing to simulate known attack techniques. Mapping security controls and policies to framework tactics and techniques to identify coverage gaps.
What challenges might organizations face when adopting the MITRE ATT&CK framework?
Challenges may include the complexity of fully understanding and applying the framework, the need for skilled personnel to interpret and implement the insights effectively, and ensuring that security measures are aligned with the evolving nature of the framework.
How does the MITRE ATT&CK framework support incident response?
The framework supports incident response by offering a common language for documenting and sharing information about attacks, facilitating the rapid identification of attack techniques, and guiding the development of effective containment and remediation strategies.
How can organizations use the MITRE ATT&CK framework?
Organizations use the MITRE ATT&CK framework to understand how attackers operate and to ground security decisions in observed adversary behavior. Rather than treating ATT&CK as a checklist, teams apply it to interpret suspicious activity, assess coverage gaps, and guide investigations. ATT&CK also provides a shared language for aligning security operations, threat intelligence, and leadership around how attacks unfold across the environment.
How does the MITRE ATT&CK framework facilitate threat hunting?
MITRE ATT&CK supports threat hunting by providing structured hypotheses based on real attacker techniques. Hunters use the framework to focus searches on behaviors associated with specific tactics, such as credential access or lateral movement, rather than scanning broadly for anomalies. This technique-driven approach helps teams conduct more systematic hunts, uncover hidden attacker activity, and validate whether observed behavior aligns with known attack patterns.
How do organizations integrate the MITRE ATT&CK framework into their security operations?
Organizations integrate MITRE ATT&CK into security operations by mapping detections, investigations, and response workflows to attacker tactics and techniques. Over time, teams use ATT&CK to evaluate detection coverage, guide alert triage, and improve collaboration between SOC, threat intelligence, and incident response functions. Successful integration treats ATT&CK as an ongoing operational framework that evolves alongside the threat landscape and the organization’s environment.
What challenges might organizations face when adopting the MITRE ATT&CK framework?
A common challenge is assuming that ATT&CK alone provides detection or prioritization. The framework describes attacker behavior but does not determine risk, urgency, or intent. Organizations may also struggle with alert volume, incomplete visibility across domains, or difficulty correlating techniques over time. Addressing these challenges requires pairing ATT&CK knowledge with continuous behavioral observation and context-driven analysis.