Network Detection and Response (NDR)
Key insights
- The global market for NDR solutions is projected to grow significantly, driven by the increasing complexity of cyber threats and the expanding attack surface of modern IT environments. (Source: MarketsandMarkets)
- Organizations utilizing NDR have reported up to a 70% reduction in time to detect and respond to cyber threats, highlighting its effectiveness in improving security operations. (Source: ESG Research)
How does NDR Network Detection and Response work?
Highly performant NDR solutions use advanced machine learning and artificial intelligence tools to model adversary tactics, techniques and procedures that are mapped in the MITRE ATT&CK framework to detect attacker behaviors with high precision. They surface security-relevant context, extract high-fidelity data, correlate events across time, users, and applications to drastically reduce time and effort spent in investigations. They also stream security detections and threat correlations to security information event management (SIEM) solutions for comprehensive security assessments.
NDR solutions move beyond merely detecting threats, responding to threats in real-time by native controls or by supporting a wide-range of integrations with other cybersecurity tools or solutions like security orchestration, automation, and response (SOAR).
Why does my organization need Network Detection and Response?
Network Detection and response (NDR) is a cybersecurity solution that continuously monitors an organization’s network to detect cyber threats & anomalous behavior using non-signature-based tools or techniques and responds to these threats via native capabilities or by integrating with other cybersecurity tools/solutions.
Gartner SOC visibility triad
NDR plays a pivotal role in securing your digital infrastructure.
Threat history is generally available in three places: network, endpoint and logs.

- Network Detection and Response (NDR) provides an aerial view of the interactions between all devices on the network.
- Security teams then configure Security Information and Event Management (SIEM) system to collect event log information from other systems and correlate between data sources.
- Endpoint Detection and Response (EDR) provides a detailed ground-level view of the processes running on a host and interactions between them.
Security teams that deploy these tools are empowered to answer a broad range of questions when responding to an incident or hunting for threats.For example, they can answer: What did this asset or account do before the alert? What did it do after the alert? Can we find out when things started to turn bad?
NDR is most critical because it provides perspective where the others cannot
For example, exploits that operate at the BIOS level of a device can subvert EDR or malicious activity may simply not be reflected in logs.
But their activity will be visible by network tools as soon as they interact with any other system through the network.
Or advanced and sophisticated attackers use hidden encrypted HTTPS tunnels, that blend in with regular traffic, to launch a command and control (C2) session and use the same session to exfiltrate sensitive business and customer data and evade perimeter security controls but NDR solutions are extremely adept at detecting these behaviors.
Effective AI-driven network detection and response platforms collect and store the right metadata and enrich it with AI-derived security insights.
Effective use of AI can then drive the detection of attackers in real-time and perform conclusive incident investigations.
What are the benefits of NDR solutions?
Continuous visibility across the network
Network Detection and Response cybersecurity solutions provide continuous visibility across all users, devices and technologies connected to the network, from data center to the cloud, from campus users to work from home users, from IaaS to SaaS, and from printers to IoT devices.
Behavioral analytics and AI for advanced threats detection
Leading NDR solutions use behavioral analytics and ML/AI to directly model attacker behaviors and detect advanced and persistent attacks with surgical precision. They avoid the deluge of low-fidelity and uninteresting alerts since they don’t detect anomalies, but rather, detect active attacks. They provide detection coverage for several phases of an attack lifecycle, including persistence, privilege escalation, defense evasion, credential access, discovery, lateral movement, data collection, C2 and exfiltration.
As organizations move to hybrid and multi-cloud environments, network visibility becomes fragmented. Cloud native NDR platforms restore that visibility by analyzing behaviors across all workloads, whether in the data center or cloud. Modern NDR solutions detect hidden threats like lateral movement and encrypted command-and-control without relying on signatures or agents.
Improvement of security operations center (SOC) operational efficiency
Leading AI-driven NDR solutions are automatic and dramatically improve security detections and security operations center (SOC) operational efficiency despite organizations and teams being plagued by a chronic shortage of cybersecurity expertise & personnel by offering full attack reconstructions in natural language that provide analysts, all the information they need to act on alerts quickly and completely.
Ability to automatically respond and shut down attacks in real-time
In addition to detecting sophisticated attacks that operate discreetly and employ evasive techniques, NDR solutions offer the ability to automatically respond to serious attack via native controls and shut down an attack in real-time. Additionally they integrate with several cybersecurity products like EDR or cybersecurity solutions like SOAR.
The Evolution of Network Detection and Response

IDS were the first generation of NDR solutions. They used rule-based and signature-based detection to identify known threats. IDS were effective at detecting common attacks, but they were also prone to false positives and could be easily evaded by attackers.
Next-generation intrusion detection systems (NGIDS) were developed to address the limitations of IDS. NGIDS used a combination of signature-based detection, anomaly-based detection, and behavioral analysis to identify both known and unknown threats. NGIDS were more effective at detecting sophisticated attacks than IDS, but they were still complex and difficult to manage.
NDR solutions take the capabilities of NGIDS to the next level. They use AI and machine learning to analyze network traffic and identify patterns and anomalies that may indicate an attack. NDR solutions can detect a wide range of threats, including known and unknown malware, intrusions, and data leakage. NDR solutions are also easier to manage than NIDS and NGIDS.
The evolution of NDR is driven by the increasing sophistication of cyberattacks. As attackers develop new techniques, NDR solutions must evolve to keep up. AI and Machine Learning play a critical role in the modern NDR solution, enabling it to detect and respond to threats that would be difficult or impossible to detect using traditional methods.
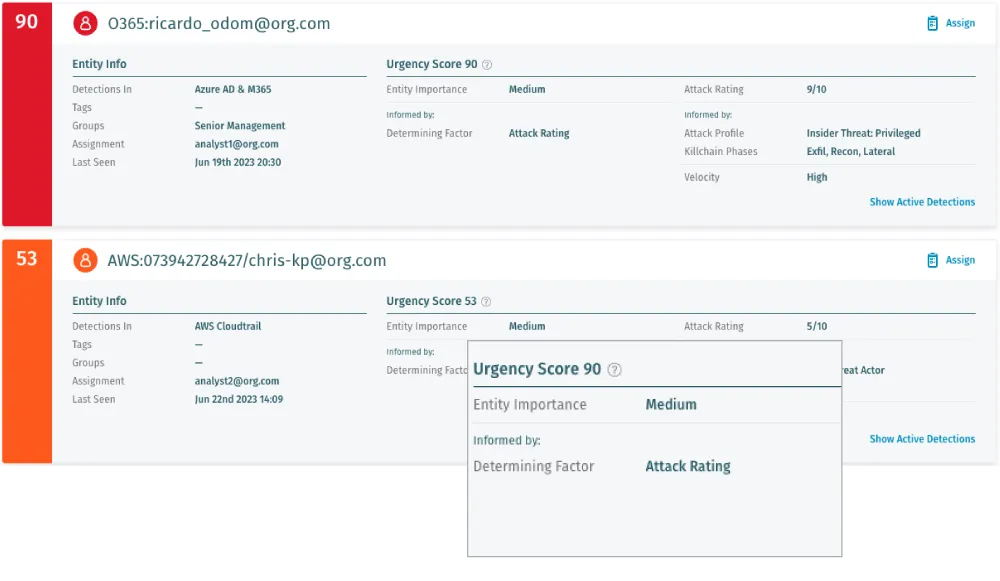
Visualizing attacks with the Vectra AI attack graph
Modern NDR solutions must go beyond basic alerting to support fast, confident decisions during investigations. The Vectra AI attack graph presents a unified view of attacker behavior across the modern network, mapping each phase of an intrusion, from initial access to lateral movement and privilege abuse.
Earlier this year, during a product walkthrough with our team, we showcased how Vectra AI’ NDR Platform helps analysts cut through the alert noise and track the full trajectory of a network-based attack.
Key highlights from the demo:
- See how the attack graph isolates patient zero, visualizes attacker east west movement, and highlights affected hosts and entities.
- Understand the impact of suspicious behaviors like remote execution, LDAP queries, and C2 communication.
- Learn how the interface prioritizes what matters, minimizing cognitive overload for faster triage and investigation.
Every click, every request, every login attempt, Vectra AI monitors them all for signs of deception. See Vectra AI in action
What are Managed NDR solutions?
Managed Network Detection and Response (NDR) is a service that leverage the expertise of a specialized cybersecurity team or service provider to continuously monitor their network traffic, analyze patterns, and identify potential security threats.
The key components of Managed NDR may include:
- Continuous Monitoring: The service provider monitors network traffic in real-time, looking for abnormal patterns or behaviors that may indicate a security threat.
- Threat Detection: Utilizing advanced analytics and threat intelligence, Managed NDR identifies and categorizes potential security threats, including malware, phishing attempts, and other malicious activities.
- Incident Response: In the event of a detected threat, the service provider initiates an incident response process to contain, mitigate, and remediate the security incident.
- Forensic Analysis: Managed NDR often includes detailed forensic analysis to understand the scope and impact of a security incident, helping organizations strengthen their security posture.
- Reporting and Recommendations: Regular reporting on security incidents, vulnerabilities, and recommendations for improving security are provided to the organization to enhance their overall cybersecurity strategy.
By outsourcing the responsibilities of network detection and response, organizations can benefit from the expertise of cybersecurity professionals, stay updated on the latest threats, and ensure a proactive approach to defending against evolving cyber risks. This approach is particularly valuable for organizations that may lack the in-house resources or expertise to effectively manage their network security.
> Learn more about Vectra's Managed NDR services
Iintegrating Network Detection and Response (NDR) into your cybersecurity strategy is not just an option—it's a necessity. Vectra AI empowers organizations to proactively detect, investigate, and respond to threats with cutting-edge NDR solutions. Contact us to explore how our NDR capabilities can fortify your network defenses and ensure the resilience of your digital assets.
Related cybersecurity fundamentals
FAQs
What is Network Detection and Response (NDR)?
Network Detection and Response (NDR) is a security solution that monitors network traffic to identify and respond to suspicious activities and potential threats in real time. NDR tools employ advanced analytics, machine learning, and artificial intelligence to detect anomalies, offering insights into malicious behaviors and facilitating swift incident response.
How does NDR differ from traditional network security measures?
Unlike traditional network security measures that primarily focus on prevention through perimeter defenses (e.g., firewalls, antivirus), NDR emphasizes the detection of and response to threats already inside the network. It provides deeper visibility into network activities, enabling the identification of sophisticated attacks that bypass initial security barriers.
What are the core functionalities of NDR?
Core functionalities of NDR include: Traffic analysis: Continuous monitoring of network traffic to identify anomalies. Threat detection: Utilizing advanced algorithms and threat intelligence to recognize signs of malicious activities. Alert triage: Prioritizing alerts based on severity and context to focus on the most critical issues. Incident response: Facilitating automated or manual responses to neutralize or mitigate threats. Forensic analysis: Providing tools for in-depth investigation of security incidents to understand attack vectors and impacts.
What benefits does NDR provide to organizations?
NDR provides several benefits, including: Enhanced visibility into encrypted and unencrypted network traffic. Early detection of advanced threats, including zero-days and insider threats. Reduced incident response times through automation and actionable intelligence. Improved security posture and compliance with regulatory requirements. Insightful data for refining security strategies and policies.
What challenges do organizations face in implementing NDR?
Challenges in implementing NDR may include: The complexity of integrating NDR solutions with existing security infrastructure. The need for skilled personnel to manage and interpret NDR outputs. Balancing the sensitivity of detection algorithms to minimize false positives without overlooking genuine threats. Ensuring the privacy and compliance aspects of monitoring network traffic.
Are there any viable NDR alternatives?
Several tools help with network detection, but do not match NDR’s ability to identify real-time attacker behaviors across the hybrid attack surface:
- IDS/IPS: Detects known threats but misses stealthy in-network activity
- SIEM: Centralizes logs but depends on upstream detections
- SOAR: Automates response but needs reliable detections from network visibility tools
- EDR/XDR: Strong on endpoints but blind to unmanaged devices, IoT/OT, and lateral movement
- Firewalls/NGFW: Block known bad traffi,c but not built for behavioral detection
- Cloud security tools: Protect assets but lack deep visibility into on-prem or East-West traffic
The Vectra AI Platform monitors hybrid networks, detects attacker tactics in real time, and improves SOC efficiency, serving as a trusted source of network-based attack intelligence alongside SIEM, SOAR, and EDR.
Can NDR solutions scale to accommodate organizational growth?
Yes, modern NDR solutions are designed with scalability in mind, capable of adjusting to the growing volume of network traffic and expanding network perimeters, especially with the adoption of cloud services and remote workforces. Selecting scalable NDR solutions is critical for ensuring long-term cybersecurity resilience.
What role does artificial intelligence play in NDR?
Artificial intelligence (AI) plays a crucial role in NDR by enhancing the accuracy and speed of threat detection. AI algorithms can analyze vast amounts of network data in real-time, identify complex patterns indicative of cyber threats, and automate response actions, significantly reducing the workload on security teams.
How does NDR contribute to an organization's overall cybersecurity strategy?
NDR contributes to an organization's cybersecurity strategy by adding a dynamic layer of defense that actively monitors for and responds to threats, complementing preventive measures and endpoint security. It ensures continuous vigilance and adaptability to emerging threats, forming an integral part of a comprehensive, multi-layered cybersecurity framework.
What’s the difference between modern vs traditional NDR solutions?
Traditional Network Detection and Response (NDR) solutions often rely on static rules, signatures, or basic anomaly thresholds. These methods:
- Generate large volumes of low-context alerts, creating analyst fatigue.
- Struggle with encrypted traffic analysis and hybrid cloud visibility.
- Operate in silos, without correlating identity, network, and cloud activity.
A modern NDR platform, like the Vectra AI Platform, uses advanced AI-driven behavioral analytics to model how real attackers operate across hybrid environments.