GLOBAL GROUP
GLOBAL GROUP is a newly emerged Ransomware-as-a-Service (RaaS) operation launched in June 2025 by a known Russian-speaking threat actor, offering AI-driven negotiation, mobile control panels, and aggressive affiliate incentives to rapidly expand its reach across global industries.

The Origin of GLOBAL
GLOBAL GROUP is an emerging Ransomware-as-a-Service (RaaS) platform first observed on June 2, 2025, introduced by a threat actor using the alias "$$$" on the Ramp4u cybercrime forum. The actor has a history with previous ransomware strains including Mamona RIP and Black Lock (formerly El Dorado). Analysts assess with medium to high confidence that GLOBAL GROUP represents a rebranding of Black Lock, aimed at rebuilding credibility and expanding its affiliate base. The group's infrastructure is hosted via Russian VPS providers (notably IpServer), which was also used by its predecessor Mamona RIP.
GLOBAL GROUP promotes a revenue model that offers up to 85% profit share to affiliates, provides a mobile-friendly affiliate panel, and integrates AI-powered negotiation bots for non-English-speaking affiliates. Its malware is cross-platform capable (Windows, ESXi, Linux, BSD), and it boasts EDR evasion features.
Source: EclecticIQ
Countries Affected by GLOBAL
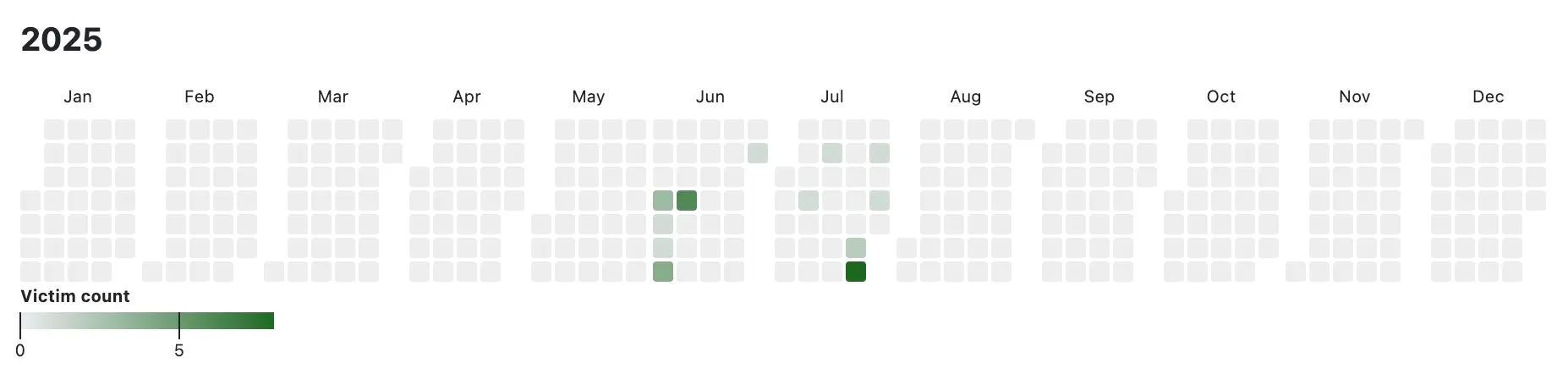
Confirmed victims span across multiple countries, with notable activity in the United States, United Kingdom, Australia, and Brazil. This global focus highlights the group's intent to maximize ransom potential by focusing on high-income, infrastructure-rich targets.
Industries Targeted by GLOBAL
GLOBAL GROUP targets a wide range of industries, with a strong emphasis on healthcare, oil and gas, industrial engineering, automotive services, and business process outsourcing. The group tailors its ransomware builds for both general-purpose environments and virtualized infrastructure like VMware ESXi.
GLOBAL's Known Victims
- Healthcare providers in the United States and Australia
- Oil & gas equipment manufacturers in Texas, USA
- Precision engineering firms and automotive services in the UK
- Facilities management and BPO companies in Brazil
The group claimed 30 victims so far, including nine victims within five days of its debut, indicating rapid deployment and scalability.
Global's Attack Method

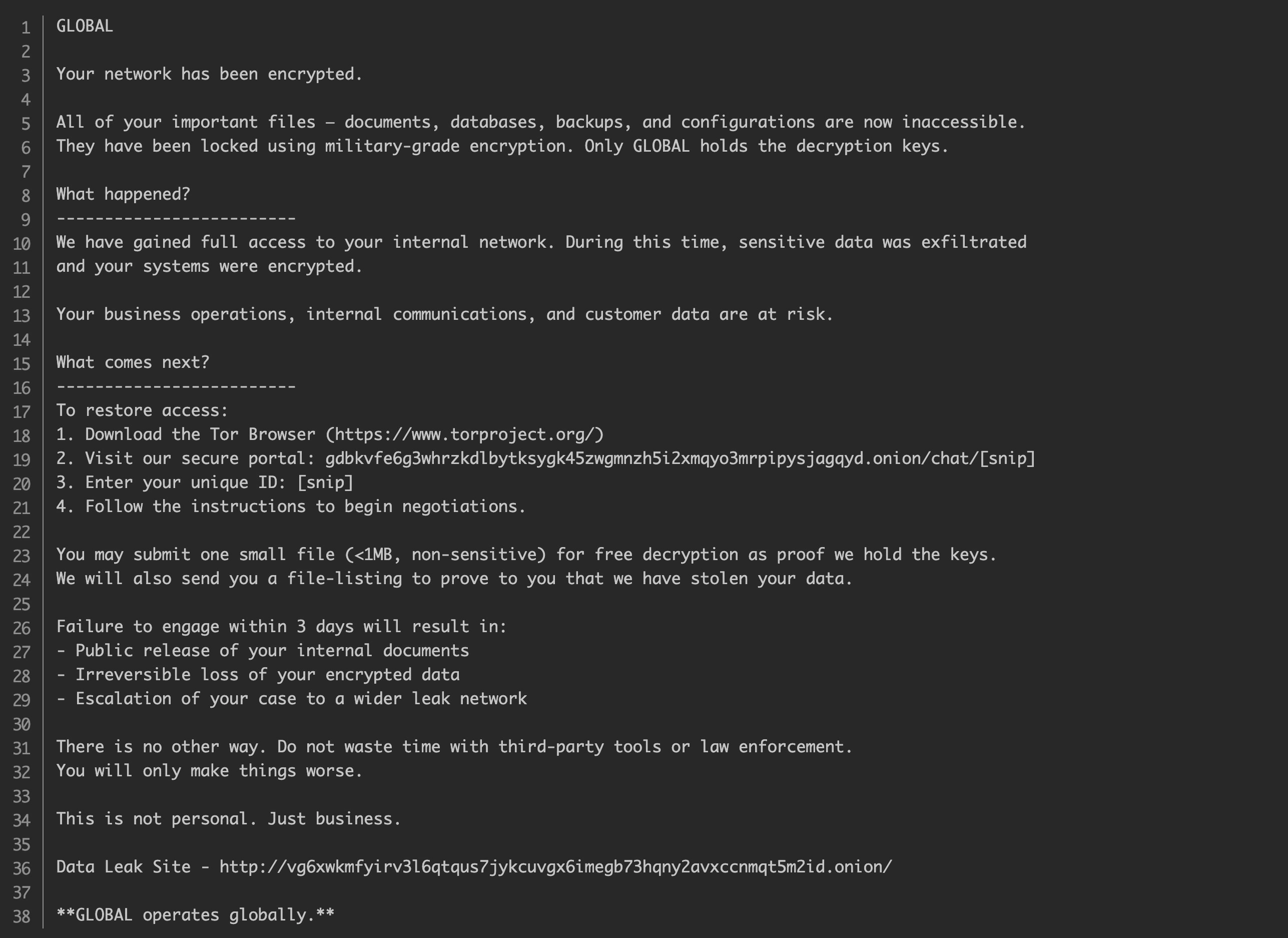
Purchased access from Initial Access Brokers (IABs), brute-forced VPNs, RDWeb, and Outlook portals. Exploits Fortinet, Palo Alto, and Cisco devices.

Leverages webshells and valid credentials to gain domain user or local admin access.

Bypasses traditional EDR, uses legitimate credentials, and deploys malware compiled in Golang for stealth.

Harvests cached credentials, conducts password spraying, and uses custom tools provided by IAB partners.

Maps domain environments, identifies ESXi hosts, and performs network enumeration using built-in tools.

Moves laterally using SMB, malicious service creation, and remote shell sessions across the environment.

Exfiltrates sensitive files including legal, financial, and healthcare data before ransomware deployment.

Executes ransomware across endpoints and hypervisors, encrypting VMs in parallel using Go-based binaries.

Uses Tor-based infrastructure and misconfigured APIs to store and manage stolen data.

Delivers ransom notes, threatens public leaks on Tor DLS, and demands seven-figure payouts, often $1M or more.

Purchased access from Initial Access Brokers (IABs), brute-forced VPNs, RDWeb, and Outlook portals. Exploits Fortinet, Palo Alto, and Cisco devices.

Leverages webshells and valid credentials to gain domain user or local admin access.

Bypasses traditional EDR, uses legitimate credentials, and deploys malware compiled in Golang for stealth.

Harvests cached credentials, conducts password spraying, and uses custom tools provided by IAB partners.

Maps domain environments, identifies ESXi hosts, and performs network enumeration using built-in tools.

Moves laterally using SMB, malicious service creation, and remote shell sessions across the environment.

Exfiltrates sensitive files including legal, financial, and healthcare data before ransomware deployment.

Executes ransomware across endpoints and hypervisors, encrypting VMs in parallel using Go-based binaries.

Uses Tor-based infrastructure and misconfigured APIs to store and manage stolen data.

Delivers ransom notes, threatens public leaks on Tor DLS, and demands seven-figure payouts, often $1M or more.
TTPs used by GLOBAL
How to Detect GLOBAL with Vectra AI
List of the Detections available in the Vectra AI Platform that would indicate a ransomware attack.