LAPSUS$
LAPSUS$ (Slippy Spider) is a high-profile cyber extortion group best known for its public, chaotic, and non-traditional attack style, often involving credential theft, DNS hijacking, and data leaks via Telegram.

The origin of LAPSUS$
The LAPSUS$ Group - alternatively named SLIPPY SPIDER, Strawberry Tempest, DEV-0537, Slippy Spider or Team Imm0rtal - was first seen in June 2021.
Unlike traditional ransomware groups, LAPSUS$ does not rely on encryption-based extortion, instead opting for public shaming, defacement, and doxxing to pressure victims into payment or attention. Intelligence indicates that the group may purchase credentials from access brokers, recruit insiders, and exploit poor MFA hygiene. The group leverages off-the-shelf tools like Mimikatz, RedLine Stealer, and Metasploit, and often repurposes existing infrastructure for their attacks.
In August 2025, LAPSUS$ reentered the spotlight through a strategic partnership with Scattered Spider and ShinyHunters, forming the volatile new threat collective known as Scattered LAPSUS$ Hunters. This alliance grants LAPSUS$ access to advanced intrusion techniques via Scattered Spider’s cloud exploitation capabilities, as well as vast credential and data dumps from ShinyHunters’ breach networks. In turn, LAPSUS$ contributes its signature chaotic extortion model, viral messaging tactics, and public-facing Telegram theatrics - amplifying the trio’s visibility and psychological impact. The coalition enhances LAPSUS$’s operational reach and spectacle while maintaining their disruptive, anti-establishment image.
Countries targeted by LAPSUS$
Primary regions affected include:
- Brazil
- Portugal
- United Kingdom
- United States
- South Korea
- France
- Argentina
Industries targeted by LAPSUS$
LAPSUS$ exhibits little discernable pattern in victim selection. However, observed sectors include:
- Government (UK MoJ, DHS)
- Telecommunications & Technology (NVIDIA, Microsoft, Samsung)
- Education, Healthcare, and Media
- Manufacturing and Energy
- Financial Services
LAPSUS$ known victims
Notable victims include:
- Okta: Breach involving identity access management systems
- Microsoft: Source code exfiltrated
- NVIDIA: Credential theft followed by leaked employee data
- Samsung: Source code and internal data leaks
- Uber: Breach tied to social engineering and MFA abuse
LAPSUS$ Attack Method

Typically gained via purchased credentials, SIM-swapping, social engineering (e.g., impersonating users via help desks), or recruiting insiders.

Exploits unpatched vulnerabilities in applications like JIRA, GitLab, or Confluence to escalate privileges.

Employs valid credentials, DNS manipulation, and token replay to remain undetected.

Uses Mimikatz, RedLine Stealer, ntdsutil, and DCSync to dump credentials and access session tokens.

Uses AD Explorer, searches platforms (Confluence, GitHub, Slack) for additional credentials or sensitive data.

Moves within compromised environments using VPN/RDP/VDI access and compromised cloud accounts.

Harvests credentials, email traffic, source code, internal communications, and collaboration data.

Executes malicious payloads via remote access, script execution, or insider-assisted actions.

Uploads sensitive files, screenshots, and internal documents to actor-controlled platforms or leak sites.

Disrupts operations through data deletion, service shutdowns, DNS hijacking, and high-visibility leaks.

Typically gained via purchased credentials, SIM-swapping, social engineering (e.g., impersonating users via help desks), or recruiting insiders.

Exploits unpatched vulnerabilities in applications like JIRA, GitLab, or Confluence to escalate privileges.

Employs valid credentials, DNS manipulation, and token replay to remain undetected.

Uses Mimikatz, RedLine Stealer, ntdsutil, and DCSync to dump credentials and access session tokens.

Uses AD Explorer, searches platforms (Confluence, GitHub, Slack) for additional credentials or sensitive data.

Moves within compromised environments using VPN/RDP/VDI access and compromised cloud accounts.

Harvests credentials, email traffic, source code, internal communications, and collaboration data.

Executes malicious payloads via remote access, script execution, or insider-assisted actions.

Uploads sensitive files, screenshots, and internal documents to actor-controlled platforms or leak sites.

Disrupts operations through data deletion, service shutdowns, DNS hijacking, and high-visibility leaks.
TTPs used by LAPSUS$
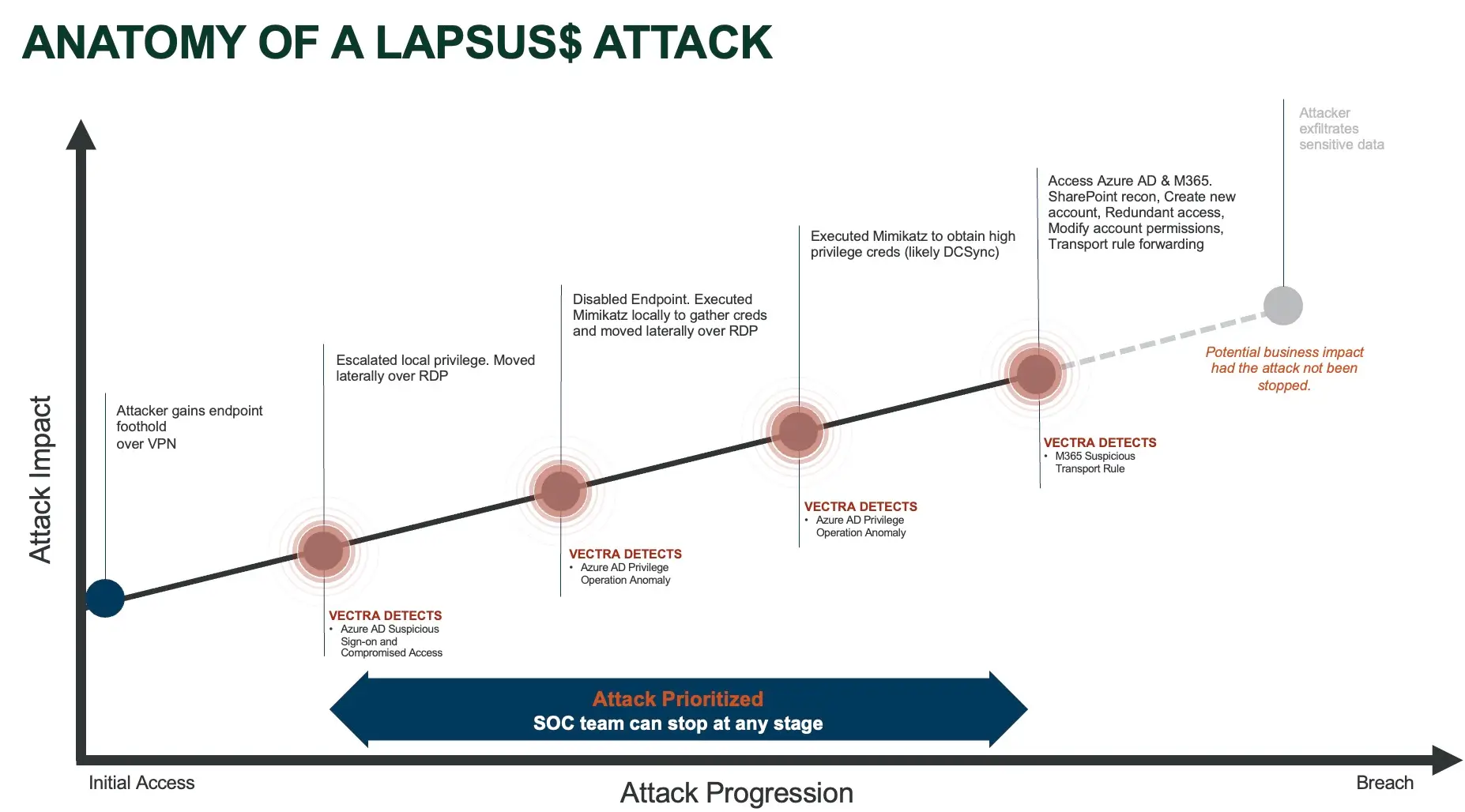
How to Detect LAPSUS$ with Vectra AI
FAQs
Does LAPSUS$ use ransomware encryption?
No. LAPSUS$ does not typically encrypt systems. Instead, they use data theft, public leaks, and social pressure as their extortion method.
How does LAPSUS$ gain initial access?
They often buy credentials from access brokers, use SIM-swapping, or recruit insiders to gain access.
What makes LAPSUS$ different from traditional cybercriminal groups?
Their emphasis on chaos, notoriety, and public spectacle, rather than stealth or monetary gain, sets them apart.
How do they maintain persistence in a network?
They often create cloud admin accounts or manipulate DNS records to retain control.
Is MFA effective against LAPSUS$?
Basic MFA is often bypassed via MFA fatigue attacks. Organizations should implement number matching, FIDO2, or hardware tokens.
What tools are used by LAPSUS$?
They use common tools like Mimikatz, RedLine Stealer, AD Explorer, and Metasploit, alongside custom scripts.
Are they financially motivated?
Partially. However, their extortion demands are often unrealistic, suggesting ego, influence, and disruption are key motives.
Where are LAPSUS$ members located?
Some evidence points to Portugal and Brazil, but deliberate obfuscation makes attribution unreliable.
How should organizations detect LAPSUS$-style intrusions?
Detecting LAPSUS$ activity requires visibility into behaviors that go beyond signatures or static rules. Vectra AI provides AI-driven detection of real-time attack behaviors—such as privilege escalation, credential misuse, lateral movement, and abuse of cloud identities—that align with LAPSUS$ TTPs. Its deep coverage across hybrid environments (including Microsoft 365, Azure AD, AWS, and on-prem infrastructure) makes it well-suited to detect the stealthy use of valid credentials, rogue admin account creation, and suspicious MFA-related activity associated with these attacks.
What is the best response to a LAPSUS$ attack?
The best response includes early detection, rapid containment, and automated investigation. Vectra AI supports this by prioritizing high-risk detections based on observed attacker behavior, not just alerts, and enables security teams to investigate and respond faster using contextual insights and attack timelines. With integrations into SOAR, EDR, and SIEM tools, Vectra helps orchestrate swift containment—such as disabling compromised accounts or isolating affected workloads- minimizing damage from extortion-driven attacks like those carried out by LAPSUS$.