Juniper and Vectra create a new class of Advanced Persistent Threat defense




Learn all about our partnership.
Download Integration Brief
As the scale and sophistication of network threats continues to increase, businesses need greater insight into attackers, threats, and the devices used in attacks. Nextgeneration security has to be built on automated and actionable intelligence that can be quickly shared to meet the demands of modern and evolving networks.
Features and benefits of integrating Juniper with Vectra
- Delivers real-time detection and deep analysis of active cyber attacks
- Uses continuous malware threat monitoring to instantly identify any phase of an attack
- Learns new malware threat behaviors and adapts to an ever changing network and threat landscape
With this joint solution, Vectra and Juniper have created a newclass of APT defense. By combining data science and machine learning, it provides inside-the-network threat detection as a next layer of defense in today’s security infrastructure.
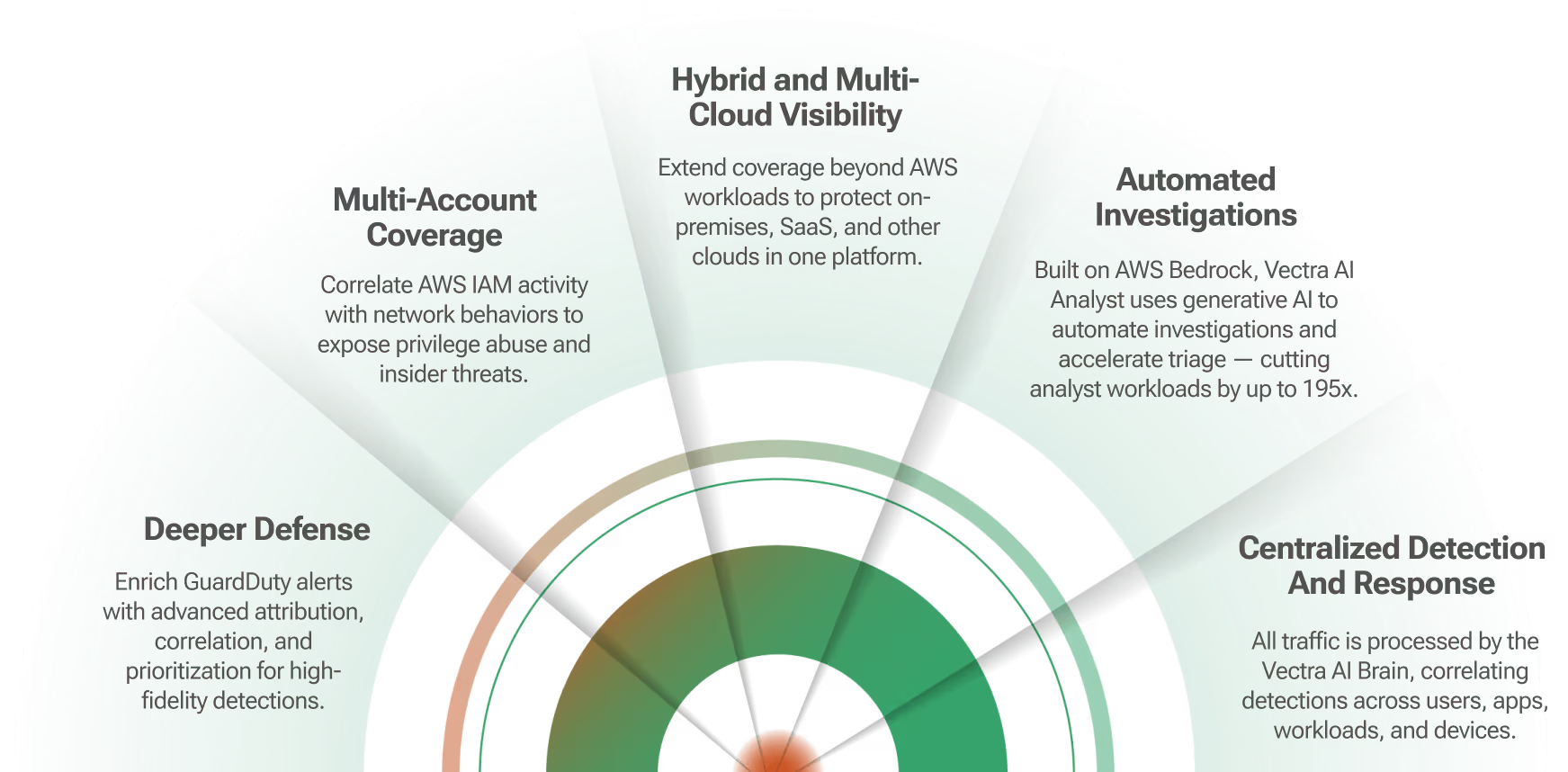
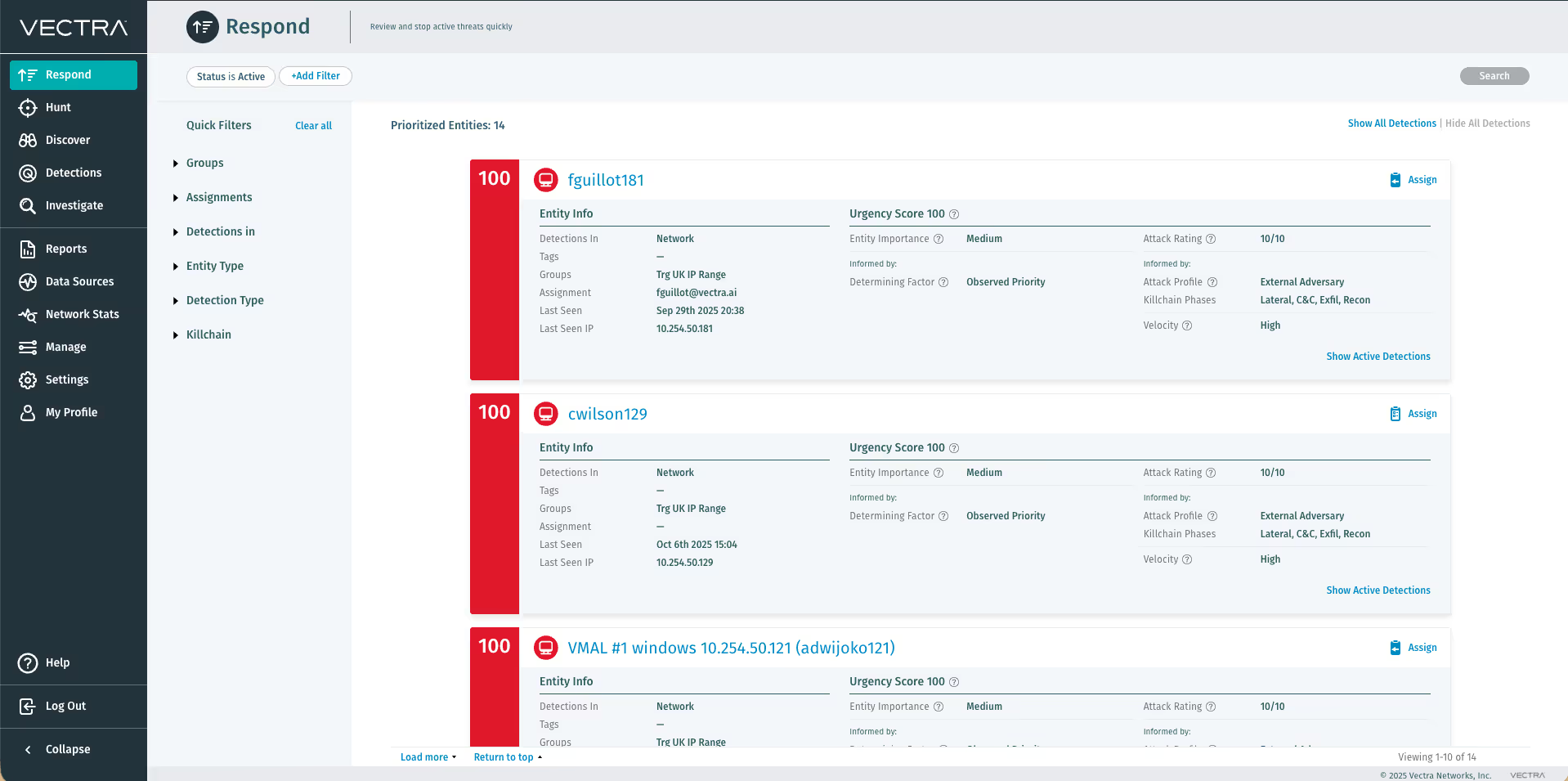
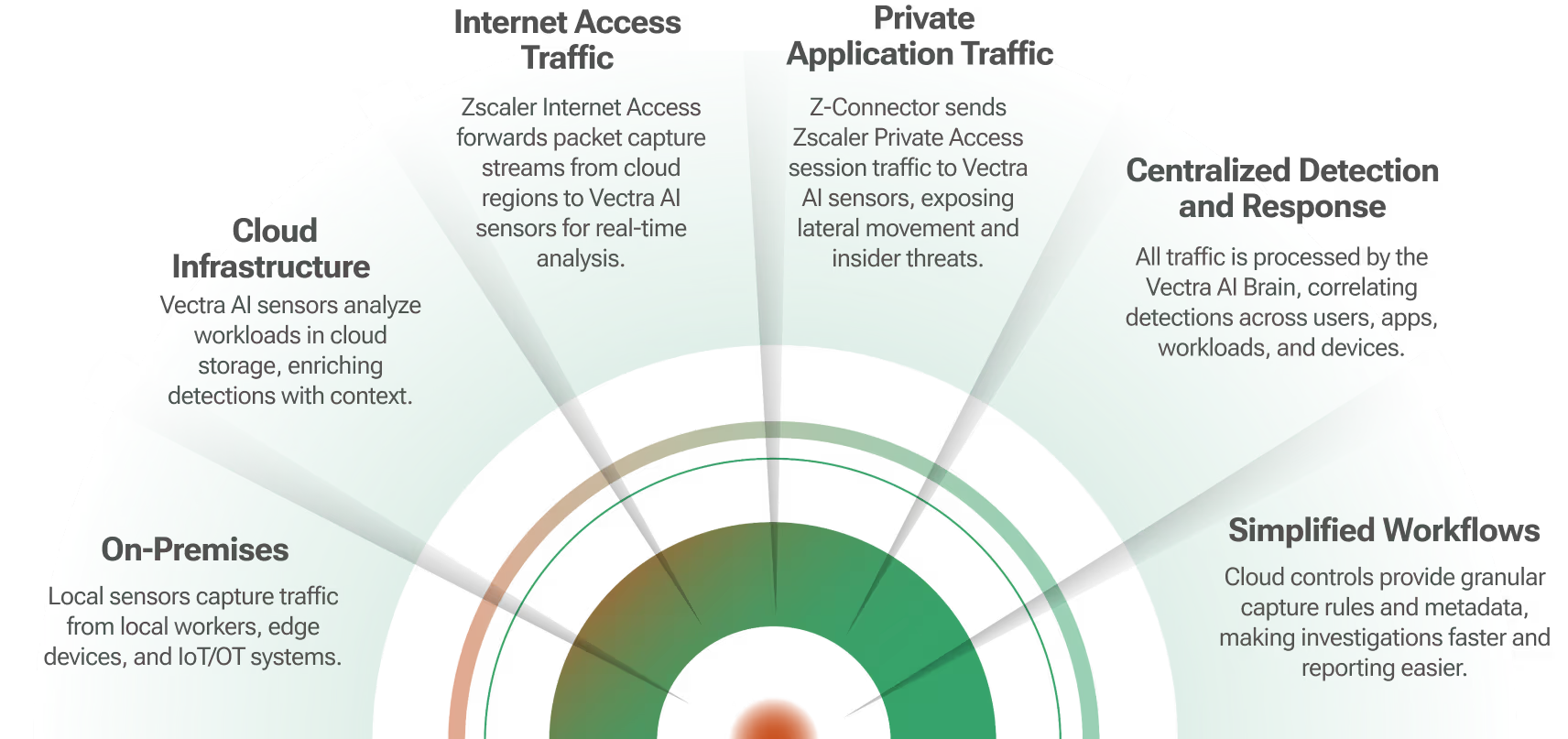
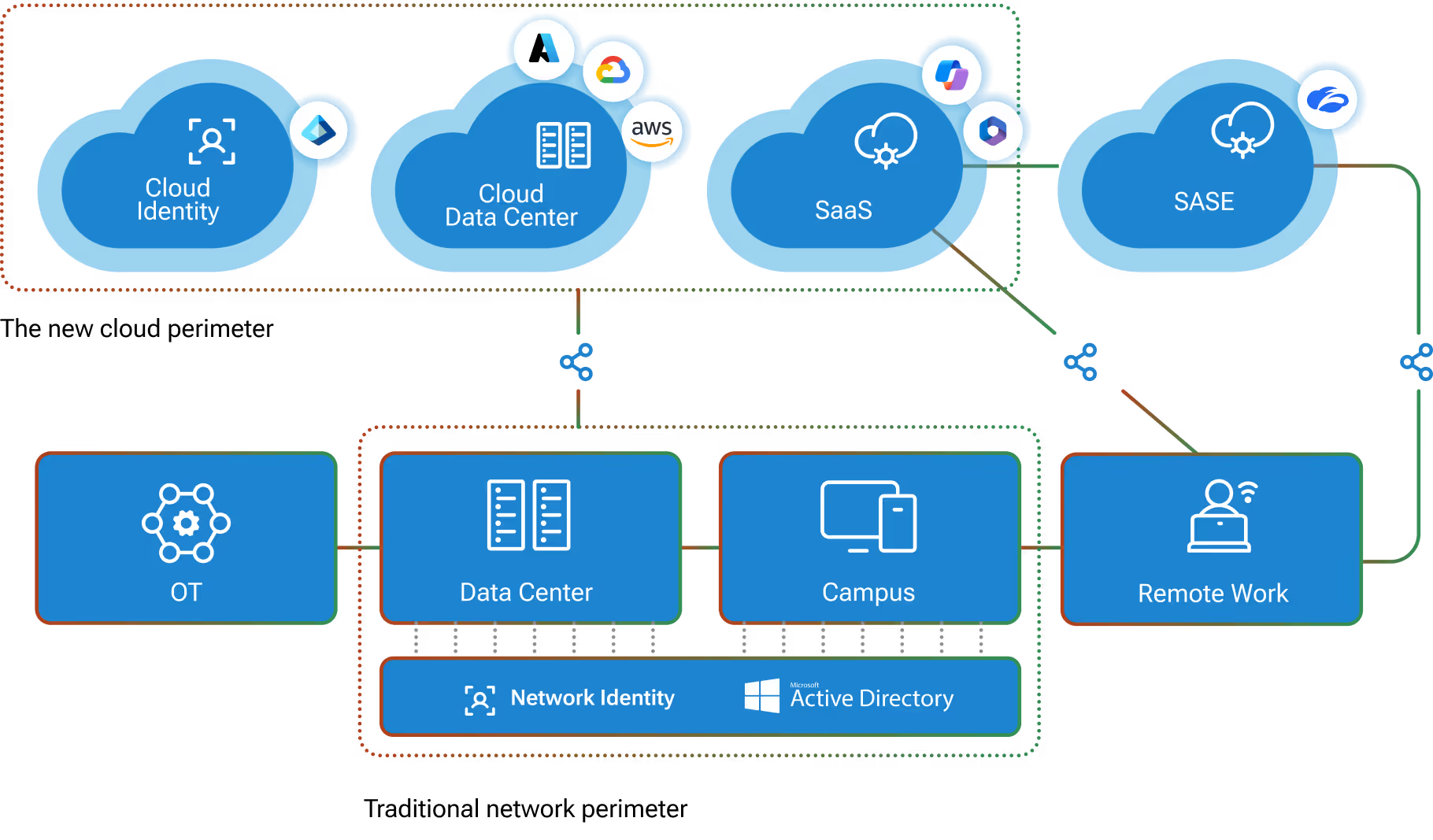
Using the Spotlight Secure Connector API, Vectra analyzes internal network traffic to reveal all phases of an active cyber attack, including hidden C&C communications, internal reconnaissance, lateral movement, botnet fraud, and data exfiltration.
The combination of Vectra and Juniper technology picks up where perimeter security leaves off by providing deep, continuous analysis of both internal and Internet network traffic to automatically detect all phases of an attack as hackers attempt to spy, spread, and steal within your network.
Why integrate Vectra AI with Juniper?
Vectra has teamed with Juniper Networks to provide inside-the-network threat detection as a next layer of defense in today’s security infrastructure. The Vectra automated threat detection and response platform from Vectra brings an added layer of security, analyzing internal network traffic to reveal all phases of an active cyber attack, including hidden command and control (C&C) communications, internal reconnaissance, lateral movement, botnet fraud, and data exfiltration.

Once Vectra identifies an infected node, its IP address and threat certainty are pushed to Juniper’s Security Intelligence (SecIntel) framework, enabling SRX Series Services Gateways to quarantine the infected device, stop communication with a C&C server, and prevent data exfiltration.
There are two methods to bring feeds into the internal database of Juniper’s SecIntel framework where the SRX Series Services Gateways can retrieve and apply the feed information to firewall policies.
- The first is a list of IP addresses or ranges of addresses, without an associated threat score. These are typically used in blacklist or whitelist applications, where a threat level is inferred from the application. Blacklist entries are assumed to be “bad,” while whitelist entries are assumed to be “good.”
- The second data format, used by Vectra, is an IP address with an associated threat level. These mimic the format used by Juniper’s own threat feeds. The entries are typically used with SecIntel policies on the firewall, and the threat levels allow a more granular application of the rules. Vectra seamlessly integrates with the Spotlight Secure Connector, giving the SRX Series gateways the necessary intelligence to prevent infected nodes from gaining Internet access, moving laterally, and exfiltrating valuable company data.

Spotlight Secure provides an API that allows Vectra to push datadirectly into Spotlight Secure Connector. This enables the SRXSeries to quarantine the infected device and stop communication with a C&C server.
The Platform
The Platform
Vectra AI Platform
The integrated signal for extended detection and response (XDR)
Vectra AI Platform
MXDR Services
Technology Integrations