Automate response and speed remediation with Vectra and Swimlane




Learn all about our partnership.
Download Integration Brief
Organizations need greater visibility into threats and the devices and accounts used in attacks against them. Security teams are overburdened with alerts, increasing the risk of alert fatigue and allowing attackers to be active inside the enterprise network.
As the scale and sophistication of network threats continues to increase, businesses need greater visibility into threats and the devices and accounts used in attacks against them. A modern security approach must be built on automated and actionable intelligence to reduce the security operations center (SOC) workload and decrease the time an attacker is allowed to be active in an organization’s network.
Why integrate Vectra AI with Swimlane?
Automate response workflows
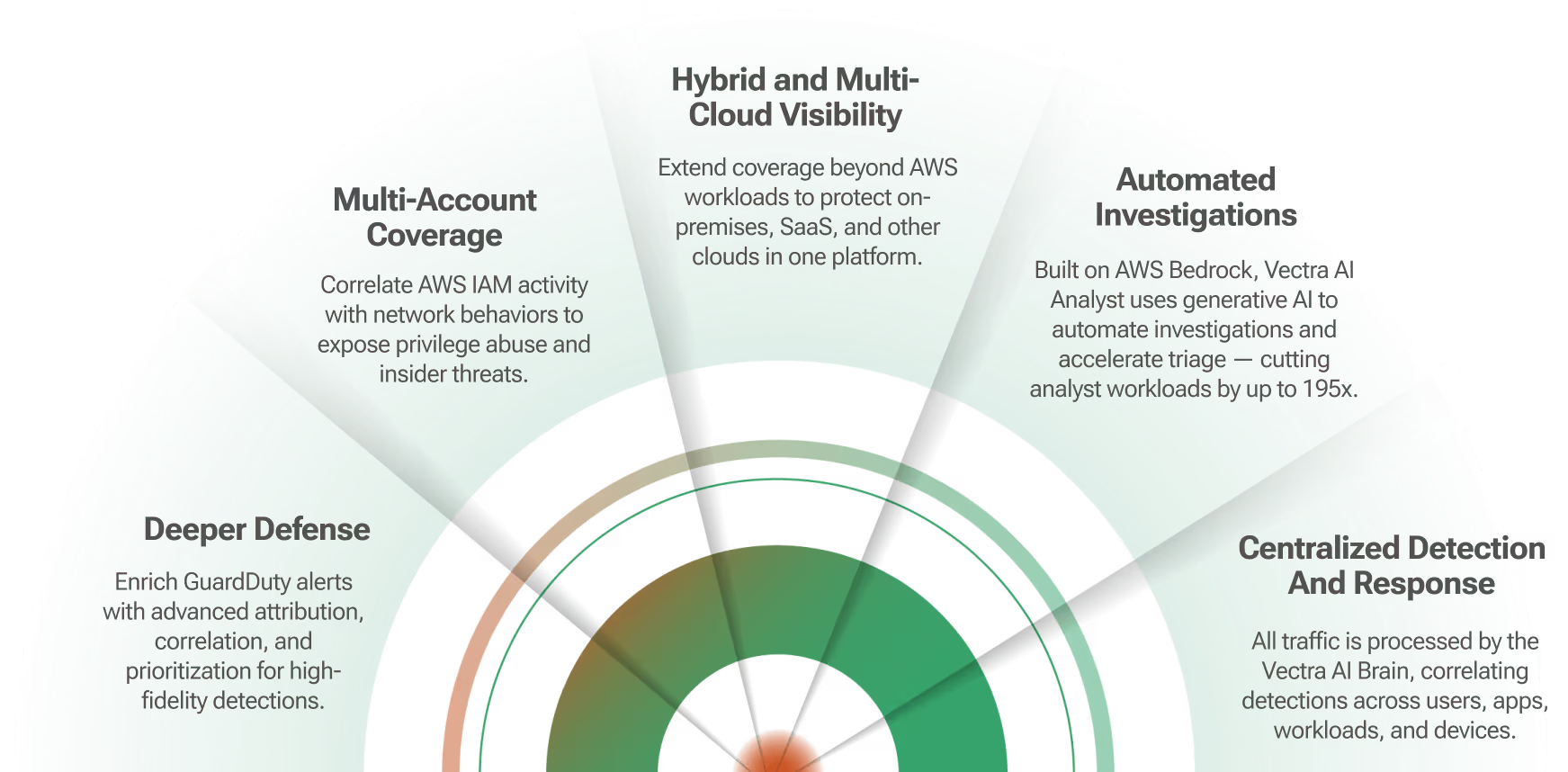
Vectra AI correlates threats, prioritizes hosts based on risk and provides rich context to empower response. Vectra automatically associates all malicious behaviors to the physical network host, even if the IP address changes, and scores the host in terms of its overall risk.
Once the Vectra platform identifies an infected device, its IP address and threat certainty are ingested into Swimlane over an API-first architecture, which centralizes information from the Vectra platform and other systems.
Swimlane then triggers automated response workflows to other security tools to notify users, dynamically segment or quarantine the infected device, stop communication with a C&C server or prevent data exfiltration across all device types and network tiers. Integration between Vectra and Swimlane ultimately reduces the workload of security analysts and the risk of alert fatigue.
Machine-speed decision making
With this joint solution, Vectra and Swimlane have created a new class of defense, replacing manual incident response processes with machine-speed detection and decision making.
By combining data science and machine learning, Vectra provides inside-the-network threat detection as a next layer of defense in today’s security infrastructure.
With sophisticated automation and response tools seamlessly integrated across the security ecosystem, Swimlane enables an instant automated response to quarantine an infected device and stop communication with a C&C server, providing a foundation that secures against the broadest spectrum of threats.
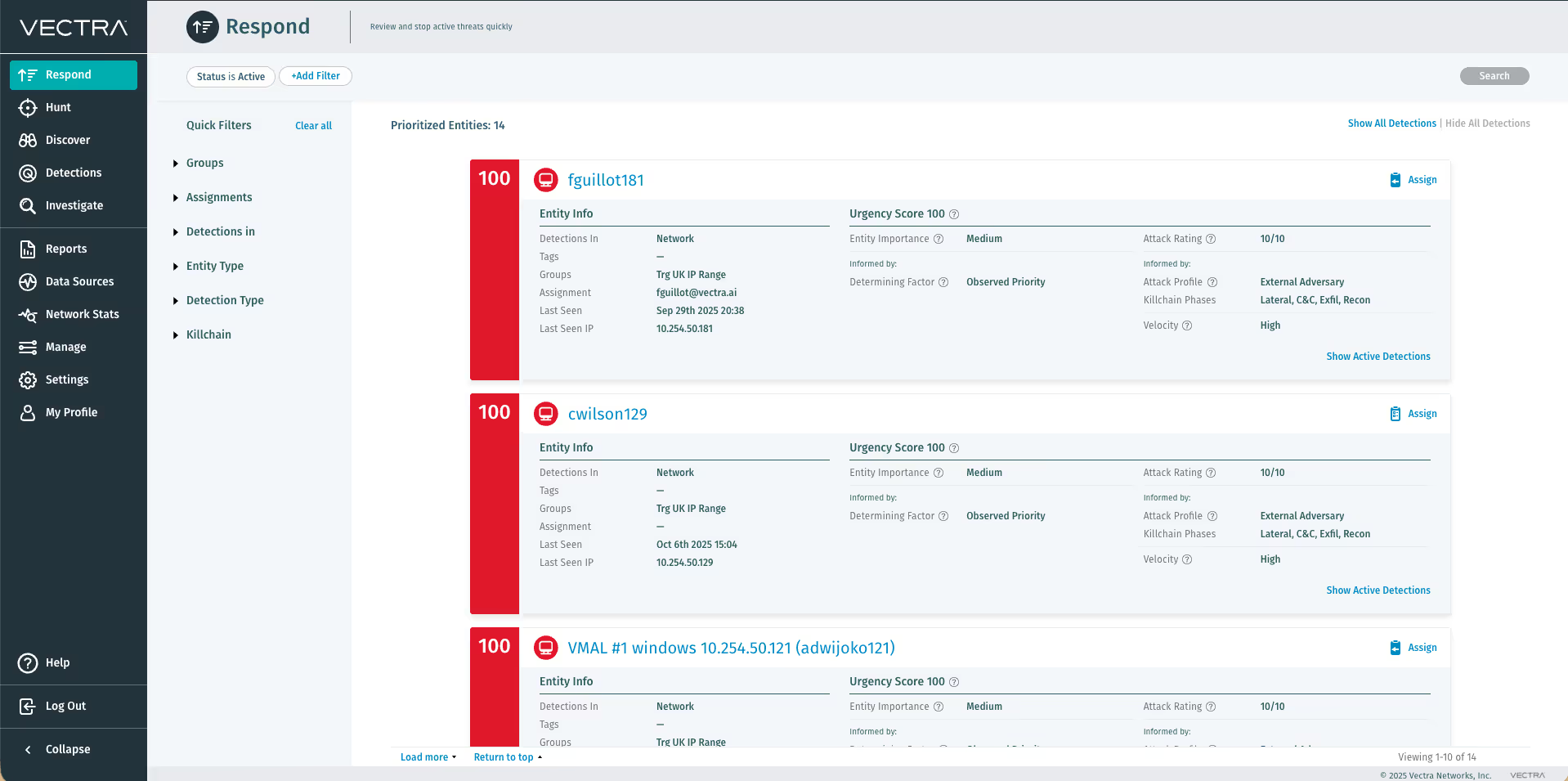
The Vectra platform is the fastest, most efficient way to detect and respond to cyberattacks, reducing security operations workload by 34X. Security analysts use the Vectra platform to perform real-time attack hunting by analyzing rich metadata from network traffic, relevant logs and cloud events to detect attacker behaviors within all cloud and data center workloads, and user and IoT devices.
Vectra correlates threats, prioritizes hosts based on risk and provides rich context to empower response. Vectra integrates with endpoint detection and response, network access control (NAC) and firewalls to automate containment, and provides a clear starting point for searches within SIEM and forensic tools.
Swimlane is at the forefront of the growing market of security automation, orchestration and response (SOAR) solutions. It delivers scalable and flexible security solutions to organizations struggling with alert fatigue, vendor proliferation and chronic staffing shortages.
Swimlane’s solution helps organizations address all security operations needs, including prioritizing alerts, orchestrating tools and automating the remediation of threats, protecting against cyberattacks and reducing business risk. Together, Vectra and Swimlane deliver automated and actionable intelligence that reduces the SOC workload and the time attackers are active inside the network
The Platform
The Platform
Vectra AI Platform
The integrated signal for extended detection and response (XDR)
Vectra AI Platform
MXDR Services
Technology Integrations