What is hybrid cloud security?
Key insights
- Hybrid cloud risk emerges in the seams between identity, network, and cloud control planes.
- Most cloud security failures stem from misconfiguration and poor identity governance.
- Fragmented visibility increases detection latency and amplifies lateral movement.
Hybrid cloud security protects workloads, data, identities, and network traffic across environments that span on-premises infrastructure, private cloud, public cloud, and SaaS platforms. It requires unified visibility, consistent policy enforcement, and coordinated detection across distributed systems. Because hybrid environments dissolve the traditional perimeter, attackers exploit identity gaps, misconfigurations, and cross-domain blind spots. Effective hybrid cloud security reduces exposure by correlating identity, network, and cloud behavior as one unified attack surface.
Hybrid cloud security is the practice of protecting workloads, data, identities, and network traffic across environments that span on-premises infrastructure, private cloud, public cloud, and SaaS platforms.
Unlike traditional perimeter-based security, hybrid cloud security must account for dynamic workloads, federated identities, API-driven communication, and encrypted east–west traffic across multiple control planes.
Hybrid cloud security depends on integrating identity governance, workload protection, network observability, configuration management, and threat detection into a single, coordinated operating model.
Without that integration, blind spots form in the seams between environments, and those seams are where modern attackers operate.
Why hybrid cloud security matters
Hybrid cloud security matters because modern enterprises no longer operate within a single perimeter or control domain. Applications span data centers and multiple cloud providers. Identities authenticate across SaaS and infrastructure platforms. APIs replace traditional network flows. Risk is no longer centralized.
When visibility fragments across tools and environments, attackers exploit the gaps. A misconfigured storage bucket in one cloud can expose sensitive data. A stale identity synchronized across directories can enable lateral movement. A compromised SaaS account can provide persistence beyond endpoint controls.
Hybrid cloud security ensures organizations can see and govern activity across these interconnected systems as one unified attack surface. Without that unified view, detection slows, policy enforcement drifts, and containment becomes reactive instead of proactive.
What are hybrid cloud security threats?
Hybrid cloud security threats emerge when enterprises span on‑premises, private, and public cloud environments. This model brings flexibility and scalability, but also new, high‑stakes risks. Attackers often target the seams where environments meet, exploiting misconfigured workloads (APIs, storage, secrets), weak or inconsistent identity and access controls (over‑privileged or stale accounts, poor MFA/conditional access), and gaps in unified monitoring and threat detection.
Unlike legacy infrastructure, hybrid environments are highly dynamic: workloads spin up and down, IP addresses recycle, data flows cross environments, and APIs become critical gateways. For security teams, this means the attack surface constantly expands, and the traditional perimeter dissolves.
Hybrid cloud security isn’t just about protecting isolated systems, it’s about achieving continuous visibility, consistent enforcement of policies (governance and least privilege), strong identity hygiene, and rapid detection and response across distributed, shifting infrastructure. Especially in regulated sectors, this also involves ensuring compliance, audit‑readiness, and managing cost by reducing tool sprawl.
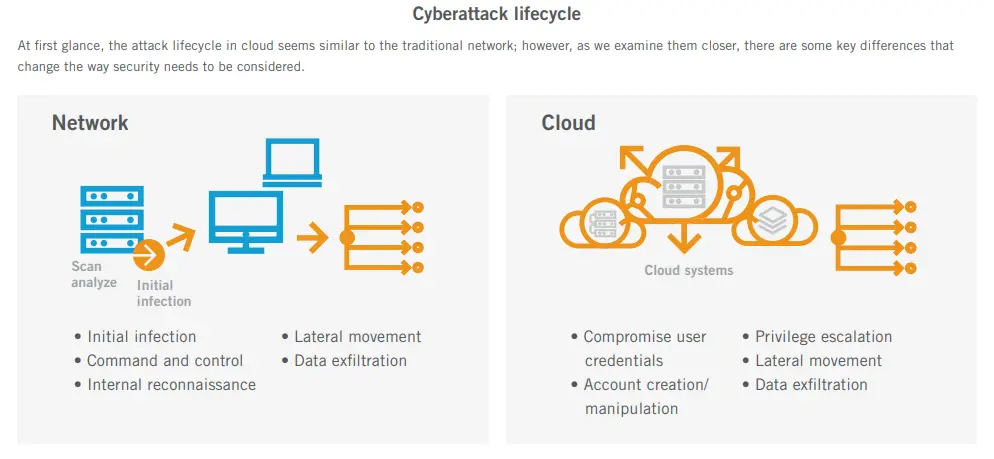
What are the top hybrid security threats?
Hybrid cloud security threats concentrate in the seams between identity, cloud infrastructure, SaaS platforms, and on-prem systems. Because these distributed systems operate as a single, interconnected modern network, trust relationships and synchronized identities create dependencies that attackers exploit through inconsistencies in configuration, authentication, and monitoring. The table below outlines the most significant hybrid cloud threats, how they typically manifest, and why they are uniquely dangerous in hybrid architectures.
These threats succeed because hybrid cloud environments prioritize connectivity and operational speed. In many cases, attackers begin with reconnaissance, mapping identity relationships, exposed APIs, and network paths before credential abuse or privilege escalation occurs.
Understanding the individual threats is important. Seeing how they connect across identity, SaaS, infrastructure, and network layers is what reveals the true blast radius.
Real-world hybrid cloud security incidents
Recent incidents illustrate how attackers exploit hybrid complexity to amplify impact.
In one case, adversaries gained initial access through a vulnerable endpoint, harvested credentials, pivoted into Azure AD and Exchange, established persistence in directory services, and deleted cloud resources. The compromise crossed endpoint, identity, and infrastructure domains before containment.
Operation Cloud Hopper demonstrated a similar cross-domain pattern. Attackers compromised managed service providers and moved laterally across tenant environments using phishing, PowerShell, and remote access malware.
These incidents show that hybrid attacks are not isolated events. They unfold across identity, SaaS, and infrastructure layers. Detection must therefore correlate behavior across those domains rather than treating them as separate silos.
Hybrid cloud security challenges in practice
Hybrid cloud environments introduce structural complexity that traditional security models were never designed to manage.
First, the shared responsibility model divides accountability between cloud providers and customers. Providers secure infrastructure, but organizations remain responsible for identities, data, workload configuration, and access control. Misunderstanding this boundary creates persistent blind spots.
Second, visibility gaps widen as workloads become short-lived, traffic becomes encrypted, and identity systems federate across domains. Traditional perimeter and signature-driven tools often miss activity that moves across APIs, identity tokens, and east–west cloud traffic.
Third, multi-cloud sprawl introduces inconsistent default policies, logging formats, and control frameworks. As access policies drift across platforms, enforcement becomes fragmented and attackers gain space to maneuver.
Finally, compliance obligations such as HIPAA, PCI DSS, and FedRAMP require continuous governance across distributed assets. Achieving consistent audit readiness across SaaS, IaaS, and on-prem systems requires unified telemetry and coordinated control.
These challenges are not operational mistakes. They are architectural realities of hybrid cloud.
Hybrid cloud security architecture
Hybrid cloud security architecture defines how controls operate across identity, workload, network, and data layers in distributed environments.
A resilient architecture includes:
- Identity layer: Centralized identity governance, least privilege enforcement, MFA integrity, and detection of credential misuse.
- Workload layer: Configuration management, runtime protection, and continuous validation of cloud-native services.
- Network layer: Visibility into north–south and east–west traffic across data center and cloud, including encrypted flows.
- Data layer: Encryption, access monitoring, and detection of abnormal data movement.
- Control plane layer: Unified logging, correlation, and automated response across providers.
Architecture matters because attackers move across these layers. If monitoring remains siloed within one layer, lateral movement and privilege escalation can remain undetected.
Hybrid cloud security best practices
6 best practices for securing hybrid cloud environments
Effective hybrid cloud security requires consistent governance and detection across control planes.
- Enforce least privilege and Zero Trust principles. Continuously validate identities and restrict lateral movement.
- Harden configurations continuously. Monitor infrastructure-as-code and cloud services for drift and misconfigurations.
- Unify telemetry across identity, SaaS, and infrastructure. Correlate activity across domains rather than relying on siloed alerts.
- Monitor east–west traffic and API activity. Attack progression often occurs within encrypted or internal flows.
- Automate detection and response. AI-driven analytics reduce latency in identifying credential abuse and privilege escalation.
- Maintain audit visibility. Align monitoring and reporting with regulatory frameworks to ensure continuous compliance.
Best practices succeed only when applied consistently across environments, not piecemeal within individual platforms.
Hybrid cloud security solutions
Hybrid cloud security solutions combine multiple technologies to address distributed risk.
Common solution categories include:
- Cloud security posture management (CSPM) and CNAPP platforms
- Identity governance and access management (IAM)
- Network detection and response (NDR)
- Endpoint detection and response (EDR)
- Security information and event management (SIEM) and SOAR
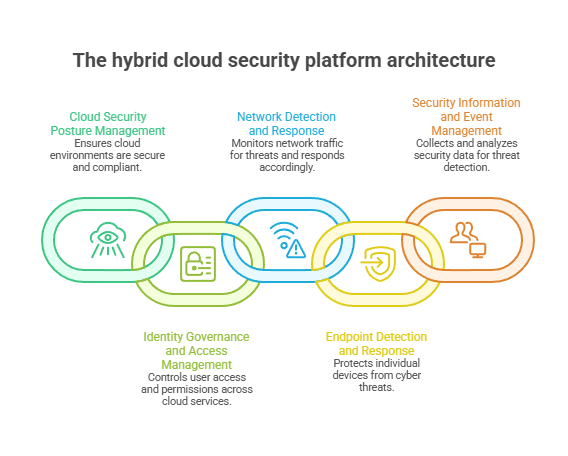
The key is integration. Tools must share telemetry and context across identity, network, workload, and SaaS layers. Solutions that operate in isolation recreate the same blind spots hybrid architectures introduce.
When evaluating solutions, organizations should prioritize cross-domain visibility, detection latency, automated response capability, and consistent policy enforcement across providers.
How to monitor and detect hybrid cloud attacks
Monitoring hybrid cloud requires correlating identity activity, API calls, workload behavior, and network traffic as a unified dataset.
Effective detection models include:
- Behavioral analysis of identity and token use
- Detection of abnormal east–west traffic across cloud and data center
- Monitoring of privilege escalation and administrative actions
- Visibility into SaaS authentication and API abuse
- Detection of suspicious data movement across storage services
Because attackers move laterally across domains, detection must follow behavior rather than static indicators. Organizations that unify telemetry across identity, infrastructure, and network layers detect compromise earlier and reduce blast radius.
The future of hybrid cloud security
Hybrid cloud security is shifting from perimeter defense to behavior-driven, adaptive protection.
Attackers are automating credential harvesting, token abuse, and lateral movement. In response, defenders are increasing reliance on AI-driven detection, automated investigation, and cross-domain correlation.
Emerging risks such as adversarial AI, deepfake-enabled phishing, and automated SaaS abuse further reinforce the need for unified observability.
Future resilience depends on reducing detection latency, eliminating telemetry silos, and enabling automated containment across identity, cloud, and network layers.
Take the Next Step
See how Vectra AI secures hybrid cloud environments with Attack Signal Intelligence.
Related cybersecurity fundamentals
FAQs
Why is hybrid cloud more vulnerable to misconfigurations?
Hybrid cloud environments are more vulnerable to misconfigurations because automation and infrastructure-as-code can replicate errors at scale. A single overly permissive IAM role or exposed storage bucket can propagate across multiple environments. Without continuous configuration monitoring and governance, these errors expand exposure faster than manual controls can correct them.
How do attackers exploit identity in hybrid cloud?
Attackers exploit identity in hybrid cloud by stealing credentials, abusing federated trust relationships, and escalating privileges through token misuse or weak MFA enforcement. Because identities synchronize across cloud and SaaS systems, a compromised account can provide cross-domain access. This allows adversaries to move laterally while appearing as legitimate users.
What role does lateral movement play in hybrid cloud attacks?
Lateral movement enables attackers to pivot across identity, cloud workloads, and on-prem systems after initial access. In hybrid environments, this movement often occurs through valid credentials and internal APIs rather than malware signatures. Fragmented monitoring across domains makes it difficult to correlate these behaviors early.
What did Operation Cloud Hopper reveal about hybrid cloud threats?
Operation Cloud Hopper demonstrated that compromising a managed service provider can grant attackers access across multiple tenant environments. The campaign showed how phishing, PowerShell, and remote access malware can enable stealthy lateral movement across hybrid infrastructures. It reinforced the importance of cross-domain monitoring and trust boundary enforcement.
What is the shared responsibility model in hybrid cloud security?
The shared responsibility model divides security obligations between cloud providers and customers. Providers secure the underlying infrastructure, while customers remain responsible for identities, data protection, access control, and workload configuration. Misunderstanding this division creates blind spots that attackers exploit.
How does ransomware operate in hybrid environments?
Ransomware in hybrid environments often combines endpoint compromise with cloud identity persistence. Attackers disable defenses, escalate privileges, and encrypt or exfiltrate data across IaaS, SaaS, and on-prem systems. The hybrid architecture amplifies blast radius if detection is delayed.
Why is visibility a challenge in hybrid cloud security?
Visibility is challenging because workloads are short-lived, traffic is encrypted, and identity events occur across multiple providers. Traditional perimeter tools cannot easily correlate activity across APIs, SaaS platforms, and east–west cloud traffic. Without unified telemetry, attack progression remains hidden.
How can organizations mitigate hybrid cloud threats?
Organizations mitigate hybrid cloud threats by enforcing least privilege, continuously monitoring configurations, and unifying telemetry across identity, network, and cloud domains. Automated detection and response reduce latency in identifying credential abuse and privilege escalation. Consistent policy enforcement across providers prevents security drift.
What is the future of hybrid cloud security?
The future of hybrid cloud security is behavior-driven and adaptive rather than perimeter-based. As attackers automate credential theft and lateral movement, defenders increasingly rely on AI-driven detection and automated response. Reducing telemetry silos and correlating activity across domains will define resilience.