Understanding Spoofing Attacks: A Comprehensive Security Guide
Key insights
- Spoofing attacks exploit trust across eight major vectors from email to GPS, with phishing-related breaches averaging $4.8 million and GPS interference affecting 1,100+ flights daily
- AI has transformed the threat landscape—attacks surged 1,265% since ChatGPT's launch, but ML-powered detection now achieves 80% accuracy in identifying sophisticated spoofing attempts
- Proven defenses deliver results: organizations with strict DMARC policies reduced phishing success rates from 68.8% to 14.2% in 2025, demonstrating the effectiveness of proper authentication protocols
- Critical infrastructure faces escalating risks (GPS spoofing up 220% from 2021-2024), requiring multi-layered defense strategies that combine technical controls, behavioral analytics, and incident response capabilities
What is a spoofing attack?
A spoofing attack is a type of cybercriminal activity where attackers disguise themselves as trusted sources by falsifying data to gain unauthorized access, steal information, or disrupt services. According to Cisco's security definition, spoofing involves forging sender information and pretending to be a legitimate source, exploiting the trust relationships that exist between users and systems.
Spoofing attacks matter more than ever in 2025, with phishing attacks leveraging spoofed identities increasing by an unprecedented 1,265% since the introduction of ChatGPT. This explosion in attack volume directly correlates with devastating financial impacts—phishing attacks involving spoofing now average $4.8 million in breach costs, even as the global average data breach cost decreased to $4.44 million according to IBM's 2025 report.
The core characteristics that define spoofing attacks include identity falsification, trust exploitation, and deception through familiarity. Attackers manipulate technical identifiers like email headers, IP addresses, or phone numbers to impersonate trusted entities. Unlike simple fraud attempts, spoofing specifically targets the authentication and verification mechanisms that systems and people rely on to establish trust. This makes spoofing particularly insidious, as victims often have no reason to suspect the communication isn't legitimate.
Social engineering attacks frequently incorporate spoofing as a primary technique, combining technical deception with psychological manipulation. The sophistication of modern spoofing extends beyond basic impersonation—attackers now leverage artificial intelligence to create convincing deepfakes, automate personalized attacks at scale, and evade traditional security controls. As CrowdStrike's spoofing guide notes, these attacks can range from simple email header modifications to complex server compromises affecting entire organizations.
What type of attack relies on spoofing?
Spoofing is not a standalone attack but a foundational technique used by many common cyberattacks to bypass trust controls. Any attack that depends on impersonation, misattribution, or falsified identity relies on spoofing at some stage.
The most common attack types that rely on spoofing include phishing and business email compromise (BEC), man-in-the-middle attacks, distributed denial-of-service (DDoS) attacks using IP spoofing, credential theft campaigns, and ransomware attacks that use spoofed communications for initial access. In each case, spoofing allows attackers to appear legitimate long enough to trigger user action or evade automated defenses.
Modern attackers increasingly chain spoofing with post-compromise activity. A spoofed email or DNS response may only be the entry point, while the real damage occurs later through lateral movement, privilege escalation, or data exfiltration. This is why spoofing should be treated as a signal of broader attack progression, not just an isolated deception attempt.
What is the purpose of spoofing attacks?
The purpose of a spoofing attack is to exploit trust, either human trust, system trust, or protocol-level trust, to gain access that would otherwise be blocked.
Attackers use spoofing to:
- Trick users into revealing credentials or approving malicious actions.
- Bypass authentication or verification mechanisms.
- Redirect traffic to malicious infrastructure.
- Conceal the true origin of malicious activity.
- Create plausible legitimacy during reconnaissance or persistence.
In modern environments, spoofing is especially effective because many systems still assume that identity signals such as email headers, IP addresses, caller IDs, or DNS responses are trustworthy by default. Once attackers successfully spoof an identity, they can operate inside the environment using valid-looking traffic, often avoiding signature-based detection.
How spoofing attacks work
Spoofing attacks exploit fundamental weaknesses in communication protocols and human trust through a combination of technical manipulation and social engineering. The attacks operate through various mechanisms, from simple header modifications that take seconds to execute, to sophisticated multi-stage campaigns that compromise entire networks.
At the technical level, spoofing exploits the fact that many internet protocols were designed for functionality rather than security. Email protocols like SMTP allow senders to specify any "From" address without verification, while DNS operates on UDP without built-in authentication mechanisms. Network protocols like ARP function on local trust assumptions that attackers can manipulate. According to security researchers, approximately 30,000 ARP spoofing attacks occur daily across monitored networks, demonstrating the persistent exploitation of these protocol vulnerabilities.
The typical spoofing attack flow progresses through distinct stages: reconnaissance, where attackers gather information about targets and systems; preparation, involving the creation of spoofed identities or technical infrastructure; execution, when the falsified communication or connection is initiated; and exploitation, where attackers achieve their objectives whether data theft, financial fraud, or system compromise. Network security teams observe these patterns repeatedly, with attackers often maintaining persistence through multiple attack vectors simultaneously.
Protocol vulnerabilities represent the foundation of most spoofing attacks. DNS cache poisoning exploits the lack of authentication in DNS responses, allowing attackers to redirect traffic to malicious servers. As explained in Cloudflare's DNS poisoning documentation, attackers impersonate DNS nameservers, make requests to resolvers, then forge replies when the resolver queries legitimate nameservers. IP spoofing takes advantage of the stateless nature of IP packets, enabling attackers to falsify source addresses and evade detection.
The exploitation of trust relationships remains central to spoofing success. Email spoofing leverages organizational hierarchies and established communication patterns, with attackers impersonating executives or trusted partners. Voice spoofing exploits the inherent trust people place in familiar voices, now enhanced through AI-generated voice clones. GPS spoofing manipulates the trust navigation systems place in satellite signals, causing receivers to report false locations with potentially catastrophic consequences for aviation and maritime operations.
Complex spoofing techniques have emerged that combine multiple attack vectors for maximum impact. Modern campaigns might begin with reconnaissance through social media, proceed to email spoofing for initial access, incorporate DNS manipulation for credential harvesting, and conclude with voice spoofing to bypass additional verification. These coordinated attacks demonstrate why single-point defenses prove insufficient against determined adversaries who understand how to chain vulnerabilities together.
Spoofing vs phishing: what’s the difference?
Spoofing and phishing are closely related but not interchangeable.
- Spoofing is the technical act of impersonation. It forges identity signals such as email headers, IP addresses, or phone numbers.
- Phishing is a social engineering attack that often uses spoofing to convince victims to take action.
In simple terms, spoofing makes an attacker look legitimate, while phishing uses that legitimacy to deceive a target. Not all spoofing leads to phishing, but most phishing attacks rely on some form of spoofing to succeed.
Types of spoofing attacks
Organizations face eight major categories of spoofing attacks, each targeting different protocols and trust mechanisms across the technology stack. Understanding these distinct attack types and their specific characteristics enables more effective detection and prevention strategies tailored to each threat vector.
Email spoofing attacks
Email spoofing remains the most prevalent form, with Microsoft alone accounting for 38% of all attempted brand phishing attempts in Q1 2024. Attackers manipulate email headers, particularly the "From" field, to impersonate trusted senders and bypass security awareness. These attacks exploit SMTP's lack of built-in authentication, allowing anyone to claim any sender identity without verification. The sophistication ranges from simple display name spoofing to complex lookalike domain registration and compromised mail server abuse. Organizations without proper email authentication see dramatically higher success rates, with only 33.4% of the top one million domains implementing valid DMARC records as of 2025.
Network-layer spoofing
IP spoofing underpins many devastating DDoS attacks, including the record-breaking 22.2 Tb/s attack blocked by Cloudflare in September 2025. Attackers falsify source IP addresses in packet headers to hide their location, bypass access controls, or amplify attacks through reflection. This technique saw a 358% year-over-year increase in Layer 7 DDoS attacks in Q1 2025, demonstrating its continued effectiveness.
DNS spoofing, also known as cache poisoning, corrupts DNS resolver caches to redirect users to malicious sites. As detailed in Cloudflare's technical analysis, attackers exploit DNS's reliance on UDP and lack of authentication to inject false records. Q1 2024 alone saw 1.5 million DNS DDoS attacks, with 38% involving malware distribution through poisoned responses.
ARP spoofing targets local networks by associating attacker MAC addresses with legitimate IP addresses. According to CAIDA monitoring, nearly 30,000 ARP spoofing attacks occur daily, with average recovery costs reaching $50,000 per incident in 2025. Small businesses prove particularly vulnerable, with 60% reporting ARP attacks in 2024. These attacks enable man-in-the-middle scenarios, allowing attackers to intercept and modify network traffic between hosts, often facilitating lateral movement across compromised networks.
Voice and location spoofing
Caller ID spoofing has evolved dramatically with AI integration, experiencing a 194% surge in deepfake-related incidents during 2024. Attackers now combine voice cloning with number spoofing to create virtually undetectable vishing attacks. The Group-IB deepfake report reveals that over 10% of financial institutions suffered deepfake vishing attacks exceeding $1 million, with average losses around $600,000 per incident. The accessibility of voice cloning technology, costing as little as $50 per campaign, has democratized these sophisticated attacks.
GPS spoofing presents critical infrastructure risks, with aviation incidents increasing from dozens in February 2024 to over 1,100 affected flights daily by August. According to GPS World's aviation analysis, GPS signal loss events surged 220% from 2021 to 2024. The Baltic Sea region alone experienced 46,000 GPS interference incidents between August 2023 and April 2024. Maritime sectors report a 500% rise in GPS spoofing and jamming, with 400 incidents recorded and 25% affecting actual vessel operations.
Website leverages homograph attacks and visual similarity to trick users into revealing credentials on fake sites. Attackers register domains using similar-looking characters from different alphabets or common misspellings of legitimate sites. SMS spoofing, or smishing, falsifies sender information in text messages to impersonate banks, delivery services, or government agencies. These attacks particularly target mobile users, who are 25-40% more likely to fall for spoofing attempts than desktop users due to smaller screens and limited security indicators.
The convergence of these attack types creates compound threats that challenge traditional security boundaries. Sophisticated campaigns now combine email spoofing for initial contact, DNS manipulation for credential harvesting, and voice spoofing for verification bypass. As ransomware attacks increasingly leverage spoofing for initial access, organizations must address all attack vectors comprehensively rather than focusing on individual threats in isolation.
Real-world spoofing attacks and incidents
The devastating impact of spoofing attacks becomes clear through examining major incidents from 2024-2025, which demonstrate both the scale of financial losses and the sophisticated techniques employed by modern attackers. These cases reveal how spoofing serves as the foundation for some of the most damaging cyberattacks affecting organizations globally.
The EchoSpoofing campaign of 2024 exploited a critical security gap in Proofpoint's email protection service to dispatch millions of spoofed emails impersonating major brands including Disney, Nike, IBM, and Coca-Cola. This massive campaign demonstrated how even leading security vendors can harbor vulnerabilities that enable widespread spoofing attacks, undermining trust in established brands while evading detection systems specifically designed to prevent such attacks.
Pepco Group's €15.5 million loss in February 2024 exemplifies the devastating effectiveness of business email compromise attacks using spoofed identities. Fraudsters successfully impersonated legitimate employees within the organization's communication channels, convincing finance staff to authorize substantial fund transfers. The sophistication of the social engineering, combined with accurate spoofing of internal email patterns, bypassed both technical controls and human judgment.
The Change Healthcare breach of February 2024 stands as one of the most impactful healthcare data breaches in history, affecting over 100 million Americans—approximately one-third of the U.S. population. The ALPHV/BlackCat ransomware group initiated the attack through phishing emails with spoofed sender information, ultimately exposing vast amounts of medical data and causing widespread disruption to healthcare payment systems nationwide.
Aviation safety faced unprecedented challenges when a United Airlines flight from New Delhi to New York experienced continuous GPS spoofing throughout its entire journey in August 2024. The attack, originating from the Black Sea region, demonstrated the global reach of GPS interference and its potential to affect commercial aviation operations. This incident contributed to the alarming statistic of 1,100+ flights affected daily by GPS spoofing, representing a 220% increase in such events from 2021 to 2024.
Law enforcement achieved a notable victory in November 2024 when Kolade Akinwale Ojelade received a 26-year prison sentence for conducting email spoofing attacks that defrauded homeowners across the United States. This conviction highlighted both the human cost of spoofing attacks on individual victims and the increasing priority law enforcement agencies place on prosecuting these crimes.
The September 2025 takedown of the RaccoonO365 phishing network marked a significant collaborative effort between Microsoft and Cloudflare, resulting in the seizure of 338 domains used for Office 365 spoofing campaigns. Before the takedown, this network had stolen over 5,000 credentials using advanced evasion techniques including Direct Send abuse, demonstrating the industrial scale at which modern spoofing operations function.
These incidents collectively illustrate several critical trends: the industrialization of spoofing attacks with dedicated infrastructure, the targeting of trusted brands and services for maximum impact, the integration of spoofing with ransomware and broader attack campaigns, and the massive financial losses that can result from a single successful attack. The €15.5 million lost by Pepco and the $4.8 million average phishing-related breach cost reported by IBM's 2025 Cost of a Data Breach Report underscore that spoofing attacks represent existential financial threats to organizations regardless of size or industry.
Detecting and preventing spoofing attacks
Comprehensive detection and prevention of spoofing attacks requires layered defenses combining authentication protocols, network monitoring, artificial intelligence, and organizational controls. Modern approaches have achieved remarkable success rates, with U.S. organizations implementing strict email authentication seeing phishing success rates plummet from 68.8% to 14.2% in 2025.
Email spoofing detection and prevention
Email authentication forms the cornerstone of anti-spoofing defenses through three complementary protocols. SPF (Sender Policy Framework) verifies that sending servers are authorized to send on behalf of a domain. DKIM (DomainKeys Identified Mail) provides cryptographic signatures ensuring message integrity. DMARC (Domain-based Message Authentication, Reporting and Conformance) ties these together with policy enforcement, telling receiving servers how to handle unauthenticated messages.
The effectiveness of proper DMARC implementation cannot be overstated. According to 2024 DMARC adoption statistics, U.S. organizations with DMARC enforcement at p=reject achieved an 80% reduction in successful phishing attacks. However, only 47.7% of top domains have adopted DMARC, with 508,269 domains remaining vulnerable due to p=none policies that don't enforce authentication failures.
Email security solutions must also incorporate header analysis for inconsistencies, domain reputation scoring to identify suspicious senders, and machine learning-based content analysis that detects spoofing indicators beyond simple authentication checks. Multi-factor authentication provides an additional barrier, ensuring that even successful spoofing attempts cannot easily compromise accounts.
Network spoofing detection
ARP spoofing detection requires both manual and automated approaches. Security teams can manually check for duplicate MAC addresses using "arp -a" commands, though this proves impractical at scale. Modern solutions employ Deep Neural Network models achieving 100% accuracy in identifying ARP anomalies, combined with dynamic ARP inspection on network switches and software certification of data before transmission.
DNS spoofing detection relies heavily on DNSSEC (DNS Security Extensions) implementation, which provides cryptographic authentication of DNS responses. Organizations should deploy DNS over HTTPS (DoH) for encrypted queries, utilize fast, DoS-resistant DNS resolvers, and implement regular monitoring for cache poisoning indicators. DNSSEC adoption reduces cache poisoning success by 95%, though deployment remains inconsistent across the internet.
IP spoofing detection focuses on packet filtering techniques that analyze packets for conflicting source information. Deep Packet Inspection examines both headers and content for spoofing indicators, while egress filtering prevents internal systems from sending packets with external source addresses. Network detection and response platforms now incorporate these capabilities alongside behavioral analytics that identify anomalous traffic patterns indicative of spoofing attacks.
Advanced detection technologies
Artificial intelligence has revolutionized spoofing detection, with machine learning models achieving 80% accuracy for 5G network spoofing using Bidirectional LSTM networks. These systems process billions of events monthly, identifying subtle patterns humans cannot detect. Hybrid approaches combining deep learning with traditional techniques like Naive Bayes classifiers provide robust detection for IoT environments where spoofing attacks increasingly target connected devices.
Behavioral analytics examine user and entity behavior to identify anomalies suggesting account compromise through spoofing. These systems establish baselines for normal communication patterns, flagging deviations that might indicate spoofed messages or connections. Real-time analysis enables rapid response before attackers can achieve their objectives, while continuous learning improves detection accuracy over time.
Modern security platforms integrate multiple detection methods into unified solutions. Attack pattern recognition systems identify known spoofing techniques across different vectors, while anomaly detection algorithms flag novel attacks. User behavior analytics combined with network traffic analysis provide comprehensive visibility into potential spoofing attempts. These AI-powered platforms dramatically reduce the time between initial spoofing attempt and detection, often identifying attacks within seconds rather than the hours or days required by traditional methods.
Prevention strategies extend beyond technical controls to encompass organizational measures. Regular security awareness training helps employees recognize spoofing indicators, while phishing simulations test and reinforce learning. Incident response procedures must include specific protocols for suspected spoofing attacks, with clear escalation paths and communication guidelines. Organizations implementing comprehensive anti-spoofing programs combining technology, training, and process improvements report 60-80% reductions in successful attacks compared to those relying on single-point solutions.
Spoofing attacks and compliance
Regulatory frameworks and security standards increasingly recognize spoofing attacks as critical threats requiring specific controls and detection capabilities. Organizations must navigate complex compliance requirements while implementing practical defenses aligned with industry frameworks and regulatory mandates.
The MITRE ATT&CK framework provides detailed mapping of spoofing techniques used by adversaries. Email spoofing falls under technique T1672 within the Initial Access tactic, documenting how adversaries modify email headers to fake sender identity. The framework recommends implementing SPF, DKIM, and DMARC as primary mitigations. Parent PID spoofing (T1134.004) represents a more sophisticated technique within Defense Evasion and Privilege Escalation tactics, where attackers spoof parent process identifiers to evade detection. Security teams use these mappings to ensure comprehensive coverage of spoofing attack vectors in their detection and response capabilities.
NIST's cybersecurity framework addresses spoofing through control SC-16(2), requiring organizations to implement anti-spoofing mechanisms that prevent falsification of security attributes and detect alteration of security process indicators. Related controls including SI-3 (Malicious Code Protection), SI-4 (System Monitoring), and SI-7 (Software, Firmware, and Information Integrity) provide additional layers of defense against spoofing-based attacks.
Regulatory compliance requirements vary by jurisdiction but increasingly mandate anti-spoofing measures. The U.S. FCC's STIR/SHAKEN framework requires telecommunications providers to implement caller ID authentication to combat voice spoofing. The FAA issued specific Safety Alerts in February 2024 addressing GPS spoofing threats to aviation. GDPR and similar data protection regulations require organizations to implement appropriate technical measures against spoofing attacks that could lead to data breaches, with strict notification requirements when incidents occur.
Framework alignment strategies must balance comprehensive coverage with practical implementation. Organizations should start by mapping their environment to relevant frameworks, identifying which spoofing techniques pose the greatest risk. Priority should go to controls addressing email spoofing given its prevalence, followed by network-layer protections based on infrastructure criticality. Regular assessments verify control effectiveness, while framework updates ensure continued alignment as spoofing techniques evolve.
The convergence of multiple frameworks creates both challenges and opportunities. While different frameworks may use varying terminology for similar controls, this overlap enables organizations to achieve multiple compliance objectives through unified implementations. A robust DMARC deployment, for instance, satisfies requirements across MITRE ATT&CK technique mitigations, NIST email security controls, and various regulatory mandates for email authentication.
Modern approaches to spoofing defense
The rapid evolution of spoofing attacks demands equally sophisticated defense strategies that leverage artificial intelligence, zero trust principles, and emerging technologies. Organizations at the forefront of cybersecurity are adopting integrated approaches that adapt to the changing threat landscape while preparing for future challenges.
AI-driven security has transformed spoofing detection from reactive to proactive, with machine learning models now processing billions of events to identify subtle attack patterns. Modern platforms analyze network traffic, user behavior, and communication patterns simultaneously, achieving detection rates previously impossible with rule-based systems. The 80% accuracy rate for 5G spoofing detection represents just the beginning, as models continue improving through exposure to new attack variations.
Zero trust architecture fundamentally changes how organizations approach spoofing defense by eliminating implicit trust. Every communication, regardless of source, undergoes verification through multiple factors including identity, device health, and behavioral analysis. This approach proves particularly effective against spoofing because it assumes attackers have already breached the perimeter, requiring continuous verification rather than one-time authentication. Organizations implementing zero trust report 90% reductions in successful spoofing attacks, particularly when combined with microsegmentation that limits lateral movement even after initial compromise.
Emerging technologies promise further improvements in spoofing defense. Blockchain-based identity verification systems create immutable records of legitimate communications, making spoofing exponentially more difficult. Quantum-resistant cryptography prepares organizations for future threats when quantum computers might break current encryption methods used in authentication protocols. Behavioral biometrics add another layer by analyzing typing patterns, mouse movements, and other unique behaviors that spoofing attacks cannot replicate.
Looking toward 2025-2026, several trends will shape spoofing defense strategies. The integration of generative AI into security platforms will enable real-time creation of detection rules adapted to emerging attack patterns. Federated learning will allow organizations to benefit from collective threat intelligence without sharing sensitive data. Extended detection and response (XDR) platforms will provide unified visibility across email, network, endpoint, and cloud environments, correlating spoofing indicators that individual tools might miss.
How Vectra AI thinks about spoofing detection
Vectra AI's approach to spoofing detection centers on Attack Signal Intelligence™, which identifies attacker behaviors rather than relying solely on known signatures or patterns. This methodology proves particularly effective against spoofing because it focuses on the actions attackers take after initial deception succeeds, catching attacks that bypass traditional authentication checks.
The platform continuously analyzes network traffic, cloud communications, and identity behaviors across hybrid environments, correlating seemingly unrelated events that together indicate spoofing-based attacks. By understanding normal communication patterns and user behaviors, the system identifies anomalies suggesting spoofed identities or connections, even when technical indicators appear legitimate. This behavioral approach complements technical controls like DMARC and DNSSEC, providing defense-in-depth against sophisticated spoofing campaigns that might evade single-layer defenses.
Future trends and emerging considerations
Over the next 12–24 months, spoofing attacks will continue to escalate as attackers exploit artificial intelligence, trusted digital relationships, and identity-dependent systems. These trends are already shaping how impersonation-based attacks succeed and how defenses must evolve.
Artificial intelligence has significantly lowered the effort required to launch effective spoofing attacks. Large language models now generate highly personalized impersonation and phishing messages at scale, with an estimated 32% of phishing emails showing clear LLM characteristics. At the same time, deepfake voice technology has advanced vishing attacks, making them more convincing and harder to detect as attackers adapt in near real time.
Regulatory pressure is increasing as spoofing affects critical infrastructure and financial systems. Caller ID authentication frameworks such as STIR/SHAKEN target voice spoofing, while aviation authorities have issued alerts following widespread GPS spoofing incidents. Financial services organizations face growing scrutiny around identity verification for remote and voice-based transactions.
Defensive priorities are shifting in response. Organizations should focus on:
- Behavioral detection that identifies attacker activity after spoofing succeeds.
- Verification controls across email, voice, SaaS platforms, and cloud identities.
- Incident response playbooks are designed specifically for impersonation and fraud.
Spoofing attacks are also becoming more targeted and persistent. Rather than broad campaigns, attackers increasingly build credibility through legitimate-seeming interactions before acting, reinforcing the need for continuous monitoring and behavior-based detection instead of reliance on identity signals alone.
Conclusion
Spoofing attacks have evolved from simple deceptions into sophisticated, AI-powered threats that cost organizations billions annually and threaten critical infrastructure worldwide. The data underscores the scale of the problem: a 1,265% surge in phishing attacks since the introduction of ChatGPT, $4.8 million in average phishing-related breach costs (even as the global average declined to $4.44 million in 2025), and GPS spoofing affecting more than 1,100 flights daily.
These attacks exploit fundamental trust mechanisms across email, network, voice, and location systems, leaving no communication channel immune to impersonation.
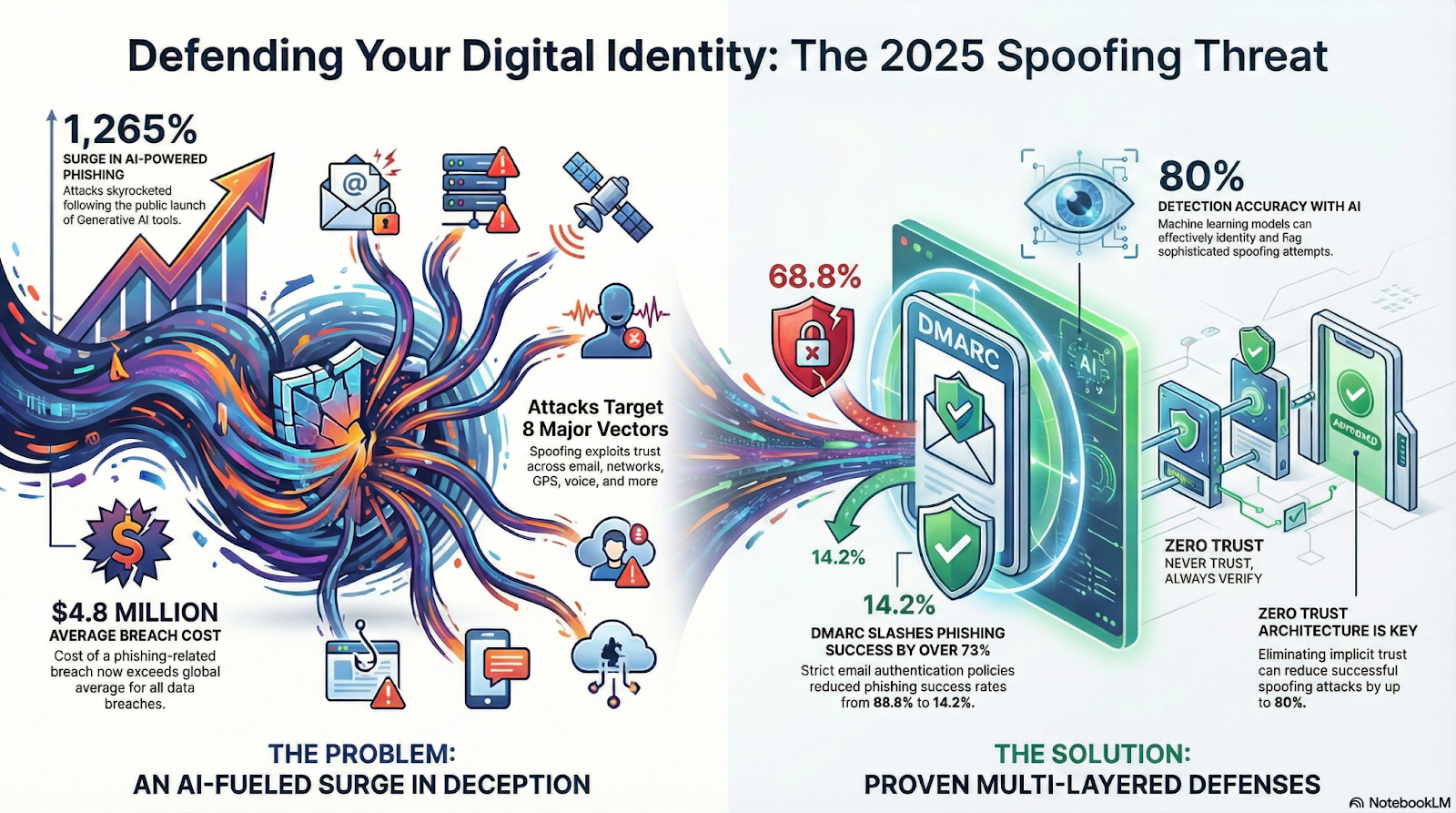
Despite this escalation, organizations are not defenseless. Comprehensive email authentication has proven highly effective, with strict DMARC enforcement reducing phishing success rates from 68.8% to 14.2%. Modern AI-powered detection, achieving up to 80% accuracy, combined with zero-trust principles and behavioral analytics, provides strong defense against increasingly evasive spoofing techniques. The most resilient strategies rely on layered controls that address multiple attack vectors rather than a single point solution.
As spoofing techniques continue to evolve, organizations must balance immediate improvements with long-term readiness. Priorities include enforcing authentication protocols, strengthening network-layer protections, and maintaining incident response procedures designed specifically for spoofing scenarios. Equally important is continuous monitoring that detects attacker behavior after impersonation succeeds.
For organizations seeking to strengthen their spoofing defenses with advanced behavioral detection and comprehensive visibility across hybrid environments, explore how Vectra AI's Attack Signal Intelligence can identify sophisticated spoofing campaigns that evade traditional security controls.
More cybersecurity fundamentals
FAQs
What's the difference between spoofing and phishing?
Spoofing is the technical act of falsifying identity or source information to appear as a trusted entity, while phishing represents a complete attack strategy that often uses spoofing as its primary technique. Spoofing focuses on the deception method itself—whether manipulating email headers, falsifying IP addresses, or faking caller ID information. Phishing, conversely, describes the broader goal of stealing sensitive information, typically through deceptive communications that leverage spoofed identities.
The relationship between these concepts is hierarchical: spoofing serves as the technical foundation that makes phishing attacks believable. When attackers send emails appearing to come from your bank, they're spoofing the sender information to execute a phishing attack aimed at stealing credentials. Not all spoofing constitutes phishing—GPS spoofing affects navigation systems without seeking information theft. Similarly, some phishing attempts don't require spoofing, such as attacks using compromised legitimate accounts. Understanding this distinction helps organizations implement appropriate defenses, as anti-spoofing measures like DMARC prevent the impersonation, while anti-phishing training helps users recognize deceptive content regardless of its apparent source.
Can spoofing attacks be completely prevented?
Complete prevention of all spoofing attacks remains practically impossible due to fundamental protocol limitations and human factors, but organizations can achieve dramatic risk reduction through comprehensive defense strategies. Based on 2025 data, implementing strict DMARC policies with p=reject reduces email spoofing success by up to 80%, while network segmentation and AI-powered detection can identify and block most network-layer spoofing attempts with similar effectiveness.
The challenge lies in the variety of spoofing vectors and the continuous evolution of attack techniques. While technical controls like DNSSEC can virtually eliminate DNS cache poisoning, and STIR/SHAKEN frameworks reduce caller ID spoofing, new attack methods emerge constantly. GPS spoofing increased 220% from 2021 to 2024 despite awareness and countermeasures. Human factors also play a critical role—even perfect technical controls cannot prevent an employee from responding to a convincing deepfake voice call.
The realistic goal is risk minimization rather than elimination. Organizations should implement defense-in-depth strategies combining multiple layers: authentication protocols (SPF, DKIM, DMARC), network controls (packet filtering, ARP inspection), behavioral analytics, employee training, and incident response capabilities. This multi-layered approach ensures that even when one defense fails, others can detect and stop the attack. Regular testing, updates, and adaptation to emerging threats maintain effectiveness over time. Success metrics should focus on reducing successful attacks, minimizing impact when breaches occur, and improving detection and response times rather than achieving impossible perfection.
What should I do if I suspect a spoofing attack?
Immediate response to suspected spoofing attacks requires swift, coordinated action to minimize damage and preserve evidence for investigation. First, disconnect affected systems from the network to prevent lateral movement or additional compromise, but avoid completely powering down systems which might destroy volatile memory containing valuable forensic data. Document everything observed, including suspicious email headers, unusual network behavior, or unexpected system activities, taking screenshots when possible.
Notify your security team or IT department immediately, providing all documented evidence and timeline information. If your organization lacks dedicated security staff, contact your managed security service provider or consider engaging an incident response firm. For email spoofing, forward suspicious messages with complete headers to your security team and report them to your email provider's abuse system. Check authentication logs for unusual login attempts or successful authentications from unexpected locations or devices.
External reporting strengthens collective defense against spoofing attacks. File a complaint with the FBI's IC3 (Internet Crime Complaint Center) if financial losses occurred, providing transaction details and communication records. Report phone spoofing to the FCC, email spoofing affecting your domain to relevant ISPs and anti-abuse organizations, and GPS spoofing incidents to appropriate aviation or maritime authorities. Many industries have Information Sharing and Analysis Centers (ISACs) that aggregate threat intelligence.
Post-incident actions should focus on strengthening defenses and improving incident response procedures. Review how the attack bypassed existing controls, implement additional authentication measures where needed, and update security awareness training to include specific examples from the incident. Consider implementing stricter DMARC policies, deploying additional monitoring tools, or engaging third-party security assessments to identify other potential vulnerabilities.
How effective is DMARC against email spoofing?
DMARC proves extremely effective against email spoofing when properly implemented, with U.S. organizations using strict DMARC policies witnessing phishing success rates plummet from 68.8% to 14.2% in 2025 according to comprehensive industry research. This dramatic 80% reduction in successful attacks demonstrates DMARC's power to prevent domain impersonation, the foundation of most email-based spoofing attacks. However, effectiveness depends entirely on implementation quality and policy enforcement levels.
The three DMARC policy levels provide different protection levels: p=none offers monitoring without blocking, p=quarantine sends suspicious messages to spam folders, and p=reject completely blocks unauthenticated messages. Unfortunately, only 47.7% of top domains have implemented DMARC at any level, with 508,269 domains remaining vulnerable due to p=none policies that don't actually prevent spoofing. Organizations must progress from monitoring to enforcement to achieve real protection.
DMARC's effectiveness stems from combining SPF and DKIM authentication with clear handling instructions for receiving servers. SPF verifies sending servers, DKIM ensures message integrity through cryptographic signatures, and DMARC ties these together with alignment checks and reporting mechanisms. This multi-factor approach makes spoofing extremely difficult for attackers who cannot compromise legitimate infrastructure. Regular DMARC reports provide visibility into both legitimate email sources and spoofing attempts, enabling organizations to refine policies and identify previously unknown sending sources.
Limitations exist despite high effectiveness rates. DMARC only protects against direct domain spoofing, not lookalike domains or display name spoofing. It requires proper SPF and DKIM implementation, which many organizations struggle to maintain across complex email ecosystems. Third-party senders like marketing platforms must be properly configured to maintain authentication. Nevertheless, DMARC remains the single most effective technical control against email spoofing, particularly when combined with user training and additional security layers.
What industries are most targeted by spoofing attacks?
Financial services bear the brunt of spoofing attacks, experiencing 38% of all business email compromise attempts in 2024-2025, with sophisticated campaigns targeting everything from wire transfer processes to customer communications. Banks face particular pressure from AI-enhanced vishing attacks, with median losses of $1,400 per incident and the largest single incident reaching $25 million. The sector's high-value transactions, complex vendor relationships, and customer trust requirements create ideal conditions for spoofing success.
Healthcare organizations represent the second most targeted sector, driven by valuable patient data and often outdated security infrastructure. The Change Healthcare breach affecting 100 million Americans exemplifies the sector's vulnerability, with medical providers increasingly facing AI voice fraud attempts impersonating colleagues or vendors. Vanderbilt University Medical Center's public warning about deepfake fraud attempts highlights growing awareness of these evolving threats. The combination of life-critical systems, HIPAA compliance complexities, and widespread legacy technology makes healthcare particularly susceptible to spoofing campaigns.
Supply chain and logistics companies face escalating threats as attackers recognize the cascading impact of compromising these interconnected networks. The Pepco Group's €15.5 million loss demonstrates how spoofing attacks exploit supply chain communications and payment processes. Manufacturing, retail, and distribution companies report increasing incidents of vendor email compromise and invoice fraud through spoofed communications. The sector's reliance on just-in-time operations and complex partner ecosystems provides numerous opportunities for attackers to insert themselves into legitimate business processes.
Technology companies, despite superior security awareness, remain attractive targets due to their central role in digital infrastructure. The compromise of 20 npm packages affecting 2 billion weekly downloads shows how spoofing attacks against individual maintainers can impact entire ecosystems. Software companies, cloud providers, and technology vendors face persistent attempts to compromise their communication channels, potentially affecting thousands of downstream customers.
Is GPS spoofing illegal?
GPS spoofing is unequivocally illegal in most jurisdictions worldwide, with severe penalties for violations due to the critical safety implications for aviation, maritime, and ground transportation systems. In the United States, the Federal Communications Commission explicitly prohibits the manufacture, import, sale, or use of GPS jamming and spoofing equipment under the Communications Act, with violations carrying fines up to $112,500 per incident and potential criminal prosecution resulting in imprisonment.
International aviation and maritime regulations treat GPS spoofing as a serious safety violation. The International Civil Aviation Organization (ICAO) classifies intentional GPS interference as a threat to aviation safety, while the International Maritime Organization considers it a violation of the Safety of Life at Sea (SOLAS) convention. The FAA issued specific Safety Alerts about GPS spoofing threats in February 2024, emphasizing the criminal nature of intentional interference. Countries regularly coordinate through these international bodies to track and prosecute GPS spoofing incidents that affect commercial transportation.
Despite clear illegality, GPS spoofing incidents increased 220% from 2021 to 2024, affecting over 1,100 flights daily by August 2024. The Baltic Sea region alone experienced 46,000 GPS interference incidents between August 2023 and April 2024, many attributed to state actors operating from contested regions. While individual prosecution proves challenging when attacks originate from foreign territories, affected nations increasingly implement detection systems and diplomatic pressure to address the threat.
Legitimate GPS testing and research requires specific authorization from relevant authorities, with strict controls on signal strength, geographic scope, and notification requirements. Emergency responders and military forces may use GPS denial in specific circumstances, but civilian GPS spoofing remains illegal regardless of intent. Organizations experiencing GPS spoofing should immediately report incidents to aviation authorities (FAA in the US), maritime authorities for vessel impacts, and law enforcement for investigation and potential prosecution.
How can AI help detect spoofing attacks?
Artificial intelligence achieves remarkable 80% accuracy in detecting sophisticated 5G network spoofing attacks through advanced machine learning models, fundamentally transforming how organizations identify and respond to these threats. AI systems process billions of events monthly, identifying subtle behavioral patterns and anomalies that human analysts would never detect in real-time. Bidirectional LSTM (Long Short-Term Memory) networks excel at recognizing temporal patterns in network traffic that indicate spoofing attempts, while hybrid approaches combining deep learning with traditional Naive Bayes classifiers provide robust detection across diverse attack vectors.
The power of AI in spoofing detection stems from its ability to establish behavioral baselines and identify deviations suggesting falsified identities. Machine learning models analyze countless factors simultaneously: email sending patterns, network traffic flows, user behavior sequences, and communication metadata. When an executive's email account suddenly sends messages with different linguistic patterns, or network traffic shows subtle timing anomalies consistent with ARP spoofing, AI systems flag these indicators faster than any human team could respond. Natural language processing capabilities detect sophisticated phishing attempts that use spoofed sender information, identifying linguistic inconsistencies even in AI-generated messages.
Modern AI-powered platforms continuously learn and adapt to new spoofing techniques without requiring manual rule updates. As attackers evolve their methods, machine learning models automatically adjust detection parameters based on observed patterns across global threat intelligence networks. This adaptive capability proves critical against polymorphic attacks where spoofing techniques change with each iteration. Federated learning approaches allow organizations to benefit from collective intelligence without sharing sensitive data, improving detection rates for everyone.
Beyond detection, AI enables predictive capabilities that anticipate spoofing attacks before they fully execute. By analyzing reconnaissance activities, failed authentication attempts, and correlation with global threat indicators, AI systems provide early warning of impending spoofing campaigns. This proactive approach allows security teams to strengthen defenses, warn potential targets, and prepare incident response procedures before attacks cause damage. As spoofing techniques become more sophisticated with AI-generated content, AI-powered defense represents the only scalable approach to maintaining security parity with attackers.
What is involved in an IP address spoofing attack?
An IP address spoofing attack involves falsifying the source IP address in network packets to make traffic appear as if it originates from a trusted system. Attackers use IP spoofing to hide their true location, bypass access controls, or amplify distributed denial-of-service (DDoS) attacks through reflection. Because the IP protocol does not authenticate packet origins, spoofed traffic can traverse networks undetected unless additional inspection and behavioral analysis are applied.
What are the different types of spoofing attacks?
Spoofing attacks include email spoofing, IP spoofing, DNS spoofing, ARP spoofing, caller ID and voice spoofing, website spoofing, SMS spoofing, and GPS spoofing. Each type targets a different trust mechanism, from communication protocols to human verification processes. While modern attack techniques vary, all spoofing attacks rely on impersonation to bypass defenses and enable further malicious activity such as credential theft, fraud, or system compromise.