Attackers are getting better at blending in. Even highly resourced enterprises with layers of firewalls, SIEMs, and endpoint agents are still suffering major breaches. Groups like Scattered Spider, Volt Typhoon, Mango Sandstorm, and UNC3886 have proven that prevention and log-based monitoring alone are not enough. Each of these attackers slipped past defenses that were designed to keep them out. What gave them away was not a signature or an alert storm, but their behavior on the network.
This is where Network Detection and Response (NDR) proves essential. Every attacker leaves a trace in network traffic, whether through a hidden tunnel, an unusual login pattern, or a suspicious lateral move. NDR gives SOC teams the ground truth by monitoring live communications across managed, unmanaged, on-premises, and cloud systems.
I recently gave a talk at Black Hat USA 2025 on this exact topic. If you'd rather watch than read, the session recording is now available.
Let’s look at four real-world examples that show how NDR could have stopped advanced adversaries before they caused damage.
1. Scattered Spider: From SMS Phishing to Azure Cloud Pivot
Scattered Spider (UNC3944) is a financially motivated group known for using social engineering to bypass strong preventive controls. In recent campaigns, attackers used SMS phishing and SIM swapping to steal credentials, then used those credentials to log into Microsoft Entra ID (Azure AD). Once inside, they silently modified mailboxes in Exchange Online, established backdoor trust relationships, and pivoted into Azure cloud workloads.
Traditional tools struggled to catch them because the attackers used legitimate credentials. SIEM, CASB, and IAM platforms did not generate alerts once the credentials were valid, which meant the activity looked like normal user behavior. The SOC only saw signs of the breach after critical systems were already exposed.
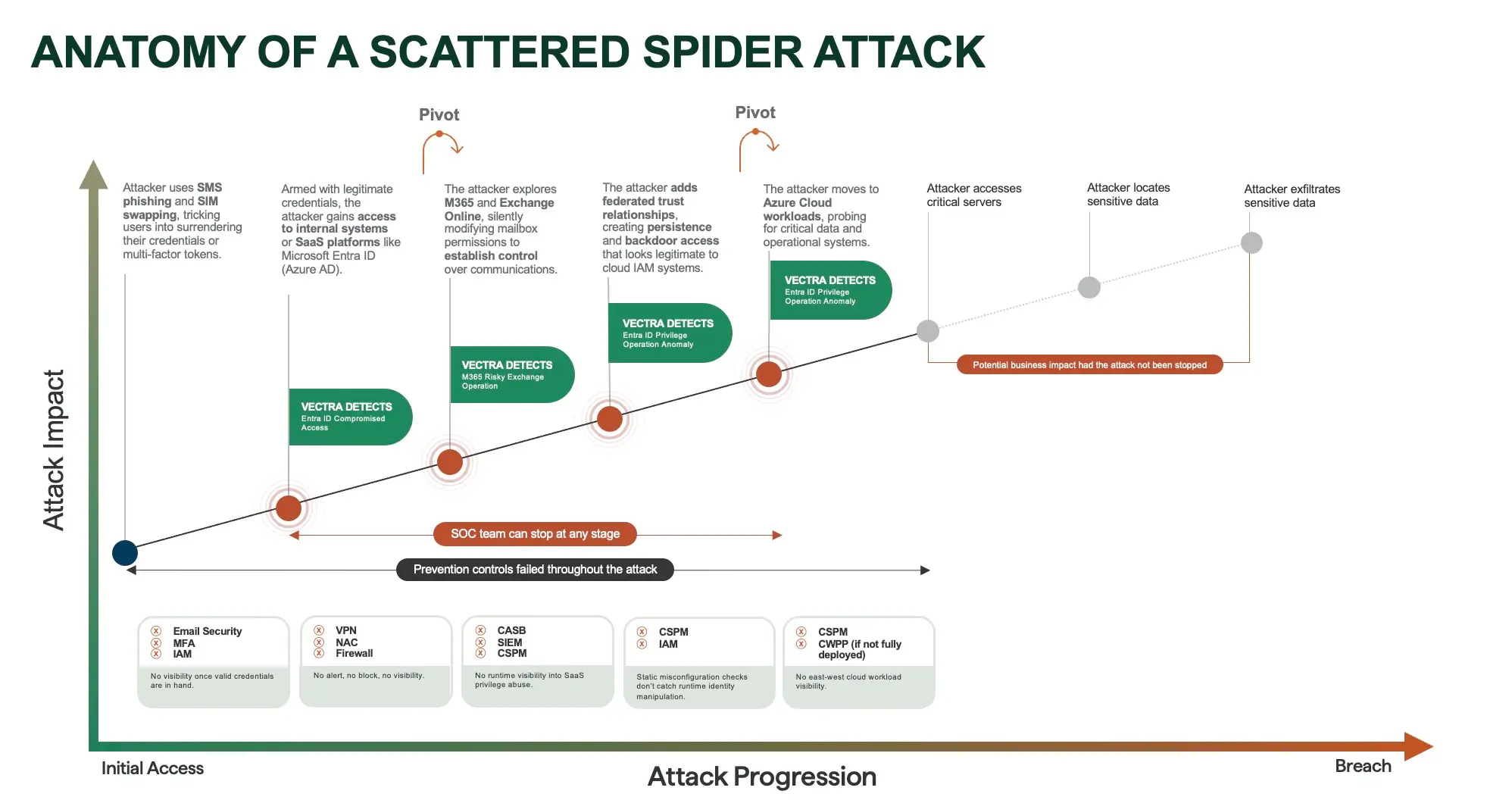
With NDR in place, these activities would not have blended in. NDR can detect risky sign-ins, mailbox manipulation, and identity privilege anomalies in real time. Instead of investigating weeks later, SOC teams could have spotted the attacker’s movement across Microsoft 365 and Azure at the moment it happened, stopping the pivot before sensitive data was accessed.
2. Volt Typhoon: Persistence Through DNS Tunnels
Volt Typhoon is a state-sponsored group that compromised organizations by starting with a home office foothold. They relied on Earthworm, a fast reverse proxy, and used DNS tunneling for command-and-control callbacks. From there, they leveraged brute force and PowerShell abuse to expand access and maintain persistence inside Windows environments.
These activities blended into the noise of normal traffic. DNS tunneling was hidden inside allowed protocols, valid credential use looked legitimate, and PowerShell scripts appeared similar to standard IT operations. Traditional EDR and IAM tools either missed the signals or failed to flag them as malicious.
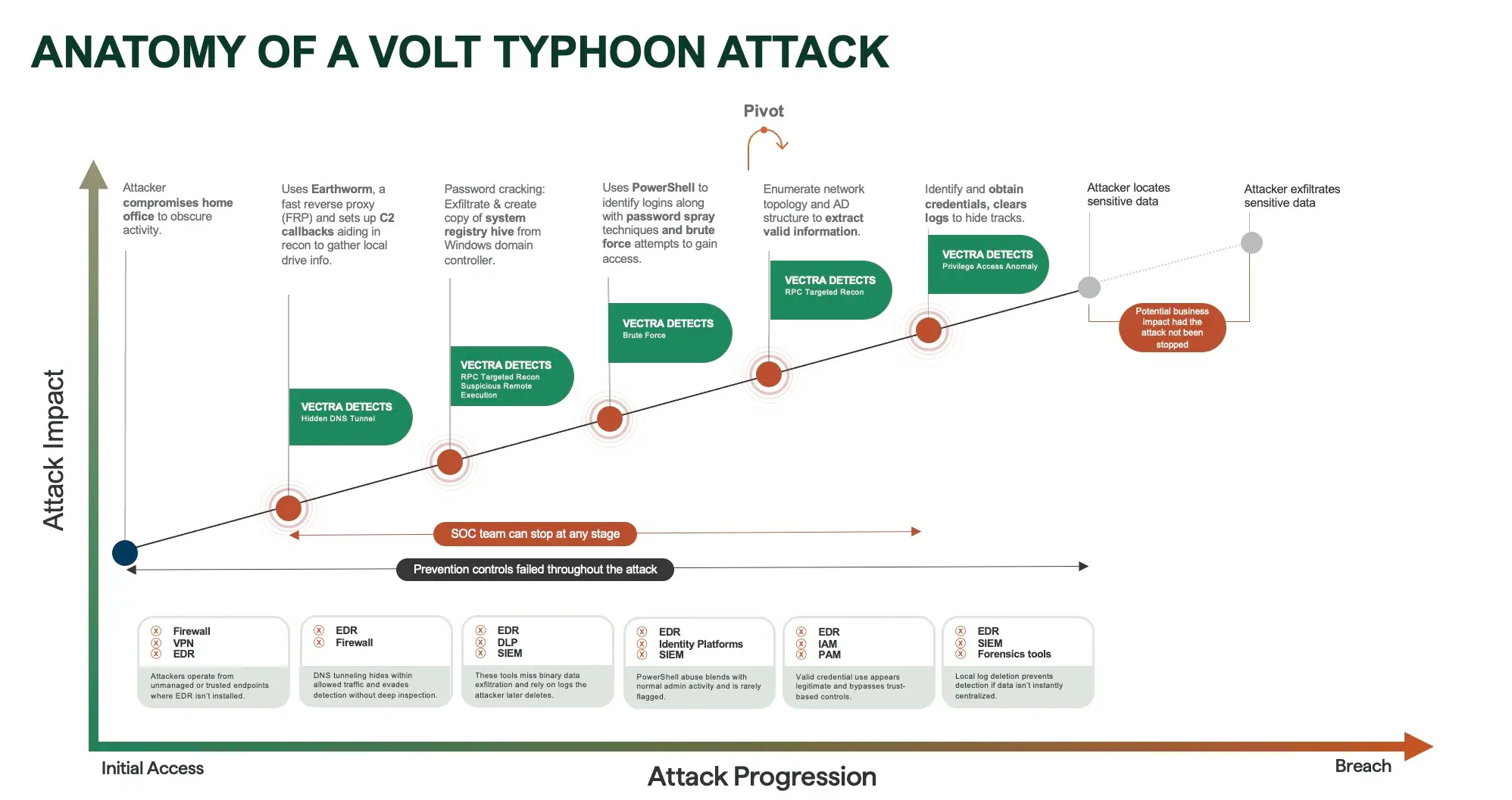
An NDR platform would have surfaced the attack in several ways. It can detect hidden DNS tunnels, identify brute force attempts, and highlight suspicious PowerShell activity that falls outside normal behavior. By correlating these signals across the network and identity layers, NDR gives SOC analysts the visibility they need to detect an attacker before critical systems are compromised.
3. Mango Sandstorm: From Server Exploit to Azure Destruction
Mango Sandstorm exploited an internet-facing server to gain initial access. After establishing control, they moved laterally via RDP and RPC using compromised accounts. The attackers then pivoted into Azure AD and targeted the Azure environment directly, ultimately leading to mass resource deletion of servers, disks, and databases.
The attack was missed because traditional tools could not correlate activity across environments. EDR agents focused on endpoints, while log tools were siloed and lacked visibility into the lateral moves between on-premises systems and the cloud.
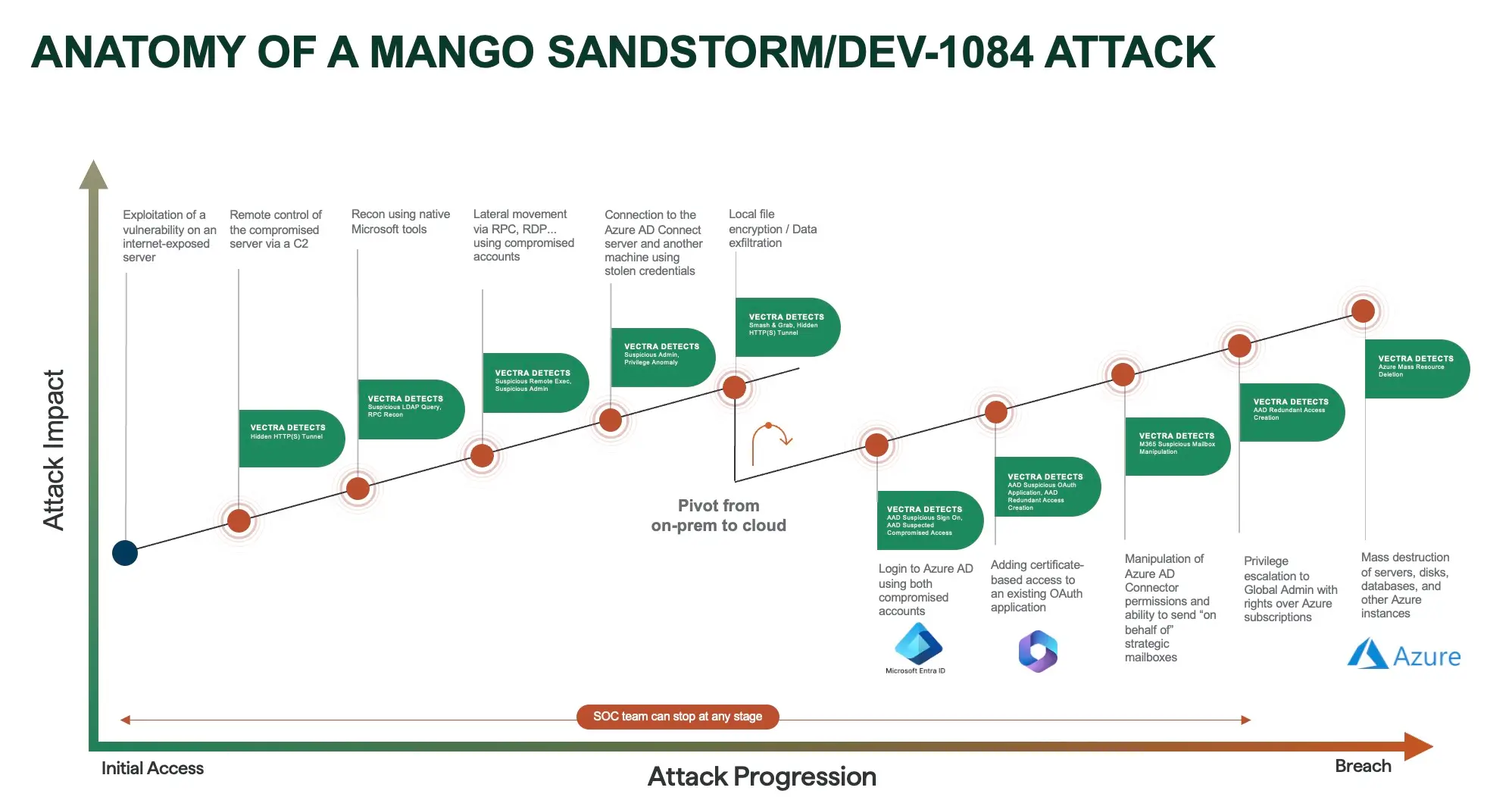
With NDR, the sequence would have looked very different. Behavioral detections for RPC reconnaissance, suspicious privilege escalation, and anomalous Azure activity would have triggered early in the chain. Instead of a large-scale breach and resource destruction, SOC teams would have been able to contain the threat during the lateral movement stage.
4. UNC3886: Zero-Day Exploits in Trusted Zones
UNC3886 is a sophisticated threat group that exploited zero-day vulnerabilities in Fortinet and VMware vCenter to gain access. They installed custom malware on ESXi hypervisors and then used DNS tunneling and other stealth techniques to exfiltrate data.
These environments were difficult to monitor with traditional tools. EDR agents could not be deployed on ESXi, SIEM had no visibility into east-west traffic, and prevention controls had no known indicators to match against. As a result, the attacker persisted undetected for extended periods.
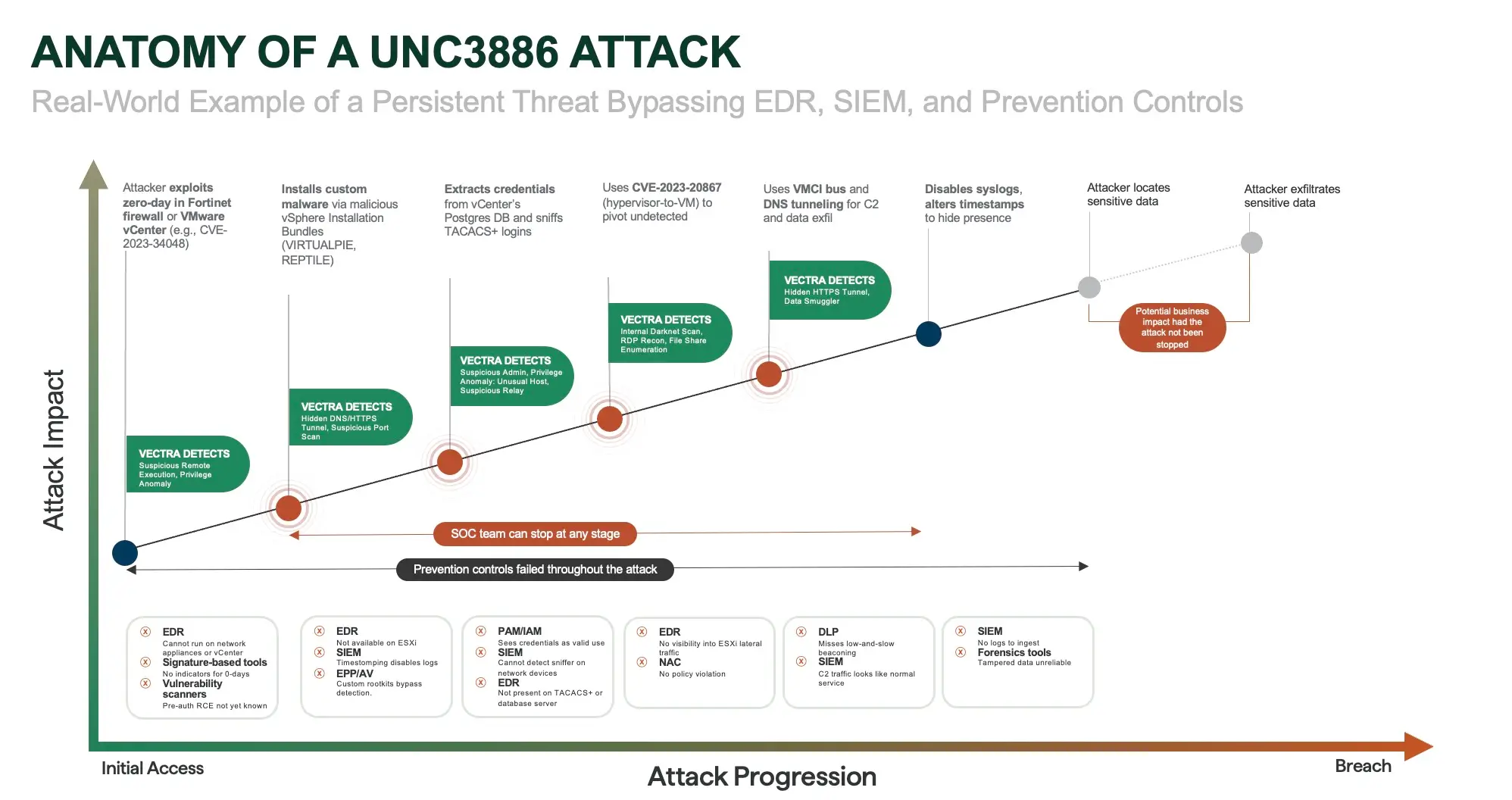
NDR provides the missing visibility in this type of scenario. By analyzing packet flows and metadata directly, NDR detects hidden HTTPS tunnels, suspicious administrative anomalies, and lateral reconnaissance inside high-trust zones. This allows SOC teams to uncover and stop attacks that bypass both prevention and endpoint-based defenses.
Key Takeaways
Across all four examples, the common thread is clear:
- Advanced adversaries did not need malware or obvious exploits to succeed.
- They relied on stolen credentials, hidden tunnels, and legitimate tools to operate under the radar.
- Traditional controls missed them because those behaviors looked normal at first glance.
NDR changes the outcome. By focusing on behaviors in network traffic, it detects what other tools cannot see. Whether it is a DNS tunnel, a suspicious mailbox change, or a lateral move to the cloud, NDR exposes attackers before they reach their objectives.
For SOC teams, this means the difference between investigating a breach weeks later and stopping an intrusion in real time.
Not convinced yet?
- Watch the full Black Hat session to see how these attacks unfold and why NDR is the only layer that exposes them in real time.
- Or, check out how Vectra AI leads in the 2025 Gartner® Magic Quadrant™ for Network Detection and Response.

