UNC3886
UNC3886, called CAULDRON PANDA by CrowdStrike, is a highly‑skilled China‑nexus intrusion set assessed to operate in direct support of Chinese state intelligence objectives.

UNC3886's origin
Active since at least late 2021 and publicly reported from February 2023 onward, the group is noted for:
- Expertise in zero‑day exploitation: they weaponised four distinct vulnerabilities across Fortinet and VMware products (CVE‑2022‑41328, ‑42475; CVE‑2023‑20867, ‑34048) before vendor patches were available.
- Operations‑security discipline: use of dead‑drop resolvers (DDR) on GitHub, bespoke rootkits, and log scrubbers to reduce forensic artefacts.
- Hybrid malware stack: proprietary implants (WhizShell, SideWalk variant, VMCI backdoors), customised open‑source tooling (FastReverseProxy, TinyShell, REPTILE, MEDUSA) and abuse of trusted SaaS channels (GitHub Pages, Google Drive) for covert C2.
The tradecraft strongly aligns with the intelligence‑collection priorities of the Chinese Communist Party (CCP) toward technology supply chains, aerospace research, and global telecom infrastructure.
Countries targeted by UNC3886
Campaign telemetry clusters around the United States and Singapore, with additional victims in broader Southeast Asia, Oceania, and, to a lesser extent, Europe and Africa. Geographic dispersion mirrors global points where US‑allied and Taiwanese aerospace supply chains interconnect and where regional telecom traffic transits.
Industries targeted by UNC3886
UNC3886 focusses on organisations whose networks deliver or carry strategic communications and sensitive technical IP. Confirmed sectors include telecommunications carriers, satellite & commercial aerospace primes, network‑equipment vendors, cloud‑service providers, and (in a smaller sample set) government technology laboratories.
UNC3886's victims
Public reporting cites at least:
- A large US telecommunications provider (compromised Feb 2023).
- A US‑based aerospace manufacturer (intrusion uncovered June 2024).
- A Singapore telecom operator (parallel June 2024 activity).
- Multiple unnamed operators whose ESXi hypervisors and FortiGate devices were co‑opted during “Campaign 23‑022.”
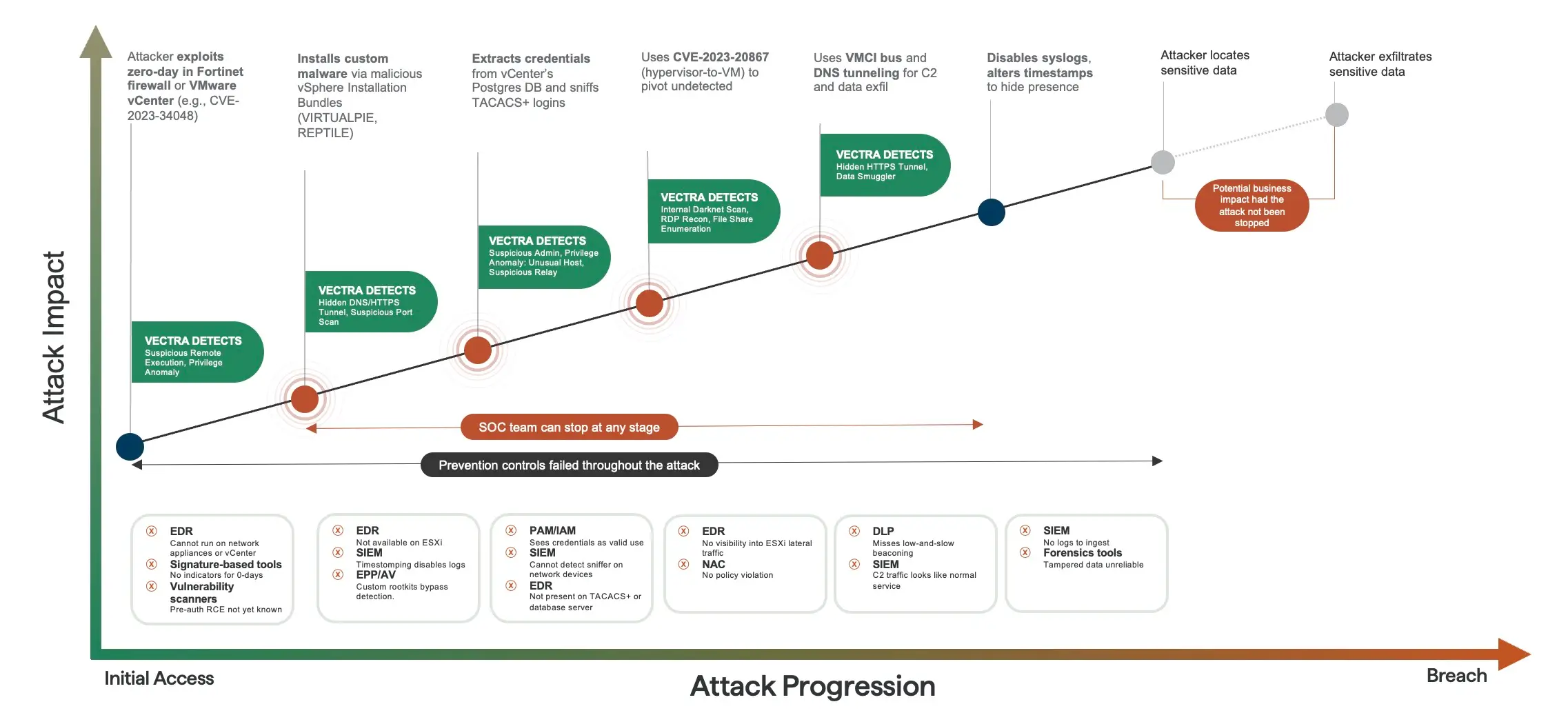
UNC3886's attack stages

Exploits zero‑day CVEs in FortiOS SSL‑VPN and VMware vCenter/Tools; alternative foothold via compromised TACACS+ or SSH credentials harvested earlier.

Loads modified REPTILE kernel modules or MEDUSA LD_PRELOAD rootkits to obtain root; abuses vpxuser privileges on ESXi for host‑level control.

Hides files/processes via REPTILE commands, installs yum‑versionlock to freeze backdoored OpenSSH packages, and executes Hidemyass log cleaner.

Backdoors ssh/sshd, sniffs TACACS+ traffic with LOOKOVER, dumps encrypted vCenter DB passwords, and captures in‑memory creds with MEDUSA key‑logging.

Runs bespoke static Nmap binary (sc) for port sweeps; enumerates VMware guest lists and network interface data from FortiGate and ESXi hosts.

Leverages stolen SSH keys/passwords, FortiGate administrative sessions, and CVE‑2023‑20867 Guest Operations to pivot between VMs and network appliances.

Uses WhizShell and SideWalk to stage documents and command output; VMCI backdoors (VIRTUALSHINE/‑PIE/‑SPHERE) stream interactive shells for targeted collection.

Deploys TinyShell & FastReverseProxy to run arbitrary commands; triggers payloads through systemd scripts or RC scripts created by rootkits.

RIFLESPINE uploads encrypted archives via Google Drive; MOPSLED retrieves C2 instructions from GitHub then tunnels data over custom TCP with ChaCha20.

Primary goal is espionage, but secondary impact includes network‑device persistence and potential supply‑chain manipulation; no destructive payloads observed to date.

Exploits zero‑day CVEs in FortiOS SSL‑VPN and VMware vCenter/Tools; alternative foothold via compromised TACACS+ or SSH credentials harvested earlier.

Loads modified REPTILE kernel modules or MEDUSA LD_PRELOAD rootkits to obtain root; abuses vpxuser privileges on ESXi for host‑level control.

Hides files/processes via REPTILE commands, installs yum‑versionlock to freeze backdoored OpenSSH packages, and executes Hidemyass log cleaner.

Backdoors ssh/sshd, sniffs TACACS+ traffic with LOOKOVER, dumps encrypted vCenter DB passwords, and captures in‑memory creds with MEDUSA key‑logging.

Runs bespoke static Nmap binary (sc) for port sweeps; enumerates VMware guest lists and network interface data from FortiGate and ESXi hosts.

Leverages stolen SSH keys/passwords, FortiGate administrative sessions, and CVE‑2023‑20867 Guest Operations to pivot between VMs and network appliances.

Uses WhizShell and SideWalk to stage documents and command output; VMCI backdoors (VIRTUALSHINE/‑PIE/‑SPHERE) stream interactive shells for targeted collection.

Deploys TinyShell & FastReverseProxy to run arbitrary commands; triggers payloads through systemd scripts or RC scripts created by rootkits.

RIFLESPINE uploads encrypted archives via Google Drive; MOPSLED retrieves C2 instructions from GitHub then tunnels data over custom TCP with ChaCha20.

Primary goal is espionage, but secondary impact includes network‑device persistence and potential supply‑chain manipulation; no destructive payloads observed to date.
TTPs used by UNC3886
How to detect UNC3886 with Vectra AI
FAQs
How does UNC3886 usually get in first?
By exploiting unpatched FortiGate or VMware vCenter/Tools vulnerabilities; patch management lag is the single biggest risk reducer.
What early indicators should we hunt for?
Outbound GitHub raw.githubusercontent.com requests from ESXi or vCenter, unexpected VMCI socket creations, and unusual files in /var/lib/fwupdd/.
Which EDR telemetry best exposes REPTILE?
Kernel‑mode module load events (insmod, modprobe) from non‑standard paths, hidden process anomalies, and sudden disappearance of /proc/<pid> entries.
Can network‑based controls stop RIFLESPINE?
Yes—TLS inspection or egress filtering that blocks Google Drive API hosts for server‑class assets will break the C2 loop.
What log sources help detect TACACS+ credential theft?
Packet captures on TCP/49, hash mismatches on tac_plus binary, and high‐frequency writes to /var/log/tac* or /var/log/ldapd*.gz.
Is standard SSH hardening enough?
Partly; also deploy file‑integrity monitoring (FIM) on /usr/bin/ssh, /usr/sbin/sshd, and enable AllowTcpForwarding no plus strict version pinning so malicious replacements are flagged.
How can we spot VMCI abuse inside ESXi?
Enable ESXi shell auditing, monitor /var/log/vmkernel.log for VMCISock connection events, and restrict vmci0 in the VMX configuration when not needed.
What immediate response if WhizShell is found?
Isolate the hypervisor, collect volatile memory, export VM disk snapshots, and rotate all vCenter and ESXi service credentials; persistence likely exists on FortiGate or TACACS+ appliances as well.
Does Multi‑Factor Authentication (MFA) help?
MFA on VPN and privileged Linux/ESXi SSH accounts disrupts lateral moves once credentials are harvested, but does not mitigate zero‑day exploitation paths.
Recommended long‑term mitigations?
① Aggressive patching/virtual‑appliance lifecycle management; ② exploit‑prevention (IPS/NGFW) signatures for the cited CVEs; ③ host integrity baselines for network devices; ④ least‑privilege account design plus TACACS+ audit forwarding; and ⑤ continuous threat‑hunt playbooks aligned to the TTP list above.