Modern Network
Key insights
Modern networks are constantly evolving, connecting users, devices, applications, and data across multiple environments. With identities and workloads shifting between on-prem, cloud, SaaS, and OT, organizations face an ever-changing digital landscape that demands agility and awareness to stay secure and connected.
How modern networks changed the evolution of cyberattacks
The concept of a “modern network” emerged as organizations expanded beyond fixed, physical infrastructures. Where once the perimeter was well defined by corporate campuses, on-premises data centers, and internal directories, today’s networks extend across multiple environments.
This shift is not only about location. It reflects changes in scale, diversity, and constant movement. Cloud workloads, SaaS adoption, and hybrid work have created interconnected systems where identities, workloads, and devices exist in fluid states. Each connection adds complexity, and with it, more opportunities for attackers.
To better understand how this transformation shapes the way we think about defense, hear Mark Wojtasiak, VP of Product Marketing at Vectra AI, explain what defines the modern network and why it matters for security teams.
The rapid change in how networks operate has also driven a rapid evolution in how cyberattacks unfold. Threat actors now exploit speed and scale as core advantages, targeting the weakest link in any interconnected system.
The shift from traditional to modern networks
In the past, corporate networks were contained and easier to observe. Defenders could monitor traffic between predictable endpoints. That predictability is gone.
The pandemic accelerated a move that had already started - toward remote work, cloud-first deployments, and SaaS dependence. In weeks, remote work surged from 6% to 35%, and 81% of workers today remain in hybrid roles. Organizations condensed years of planned digital transformation into months, moving workloads to the cloud, expanding collaboration tools, and merging operational technology with IT networks.
This environment demands a different kind of defense. The shift from traditional to modern networks is not just a technological transition, but a structural one. The same transformation that improved collaboration and agility also broadened the attack surface attackers can exploit.
The modern network attack surface
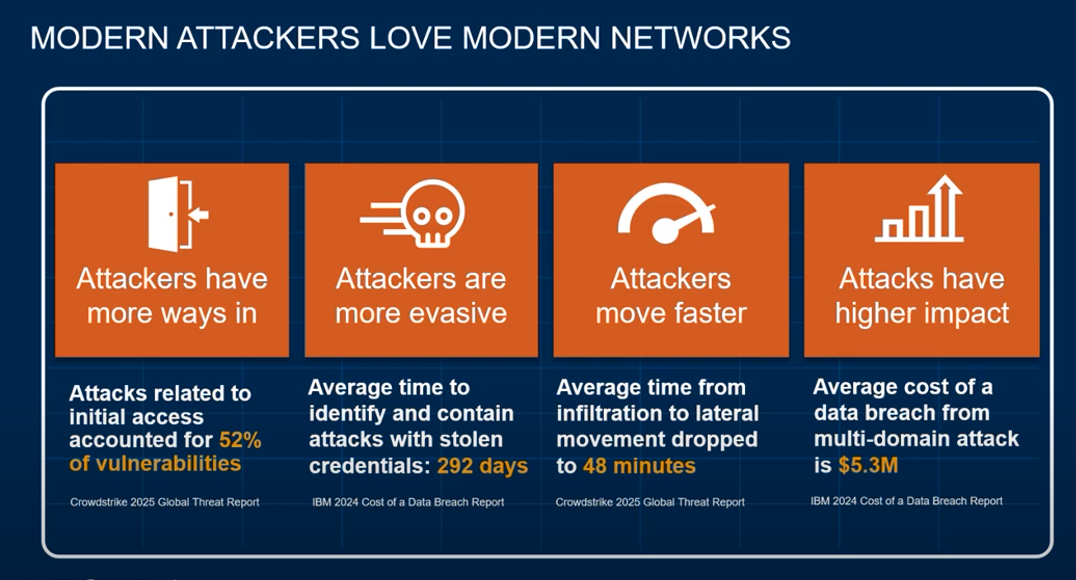
Modern networks no longer have a single entry point, they’re sprawling across on‑prem, cloud, SaaS, IoT/OT, identity services, and third‑party integrations.
Statistically, the expansion is real:
- 62% of enterprise security teams say their attack surface has grown over the past two years, driven by cloud and external integrations .
- 75% of organizations suffered a SaaS-related breach or incident in the last year, even though 89% feel confident in securing that environment.
- SaaS breaches surged by 300%, largely through identity compromise, with 85% starting via stolen credentials, and some attacks leading to data exfiltration in just 9 minutes.
- IoT breach attempts jumped 84% in 2025, exposing how unmanaged endpoints greatly increase risk .
- 93% of organizations experienced multiple identity-related breaches this year. Machine identities are proliferating quickly, with 50% of organizations expecting their identity footprint to triple soon .
In essence each new SaaS app, IoT device, unmanaged endpoint, or cloud identity drives the attack surface outward introducing blind spots that attackers are eager to exploit.
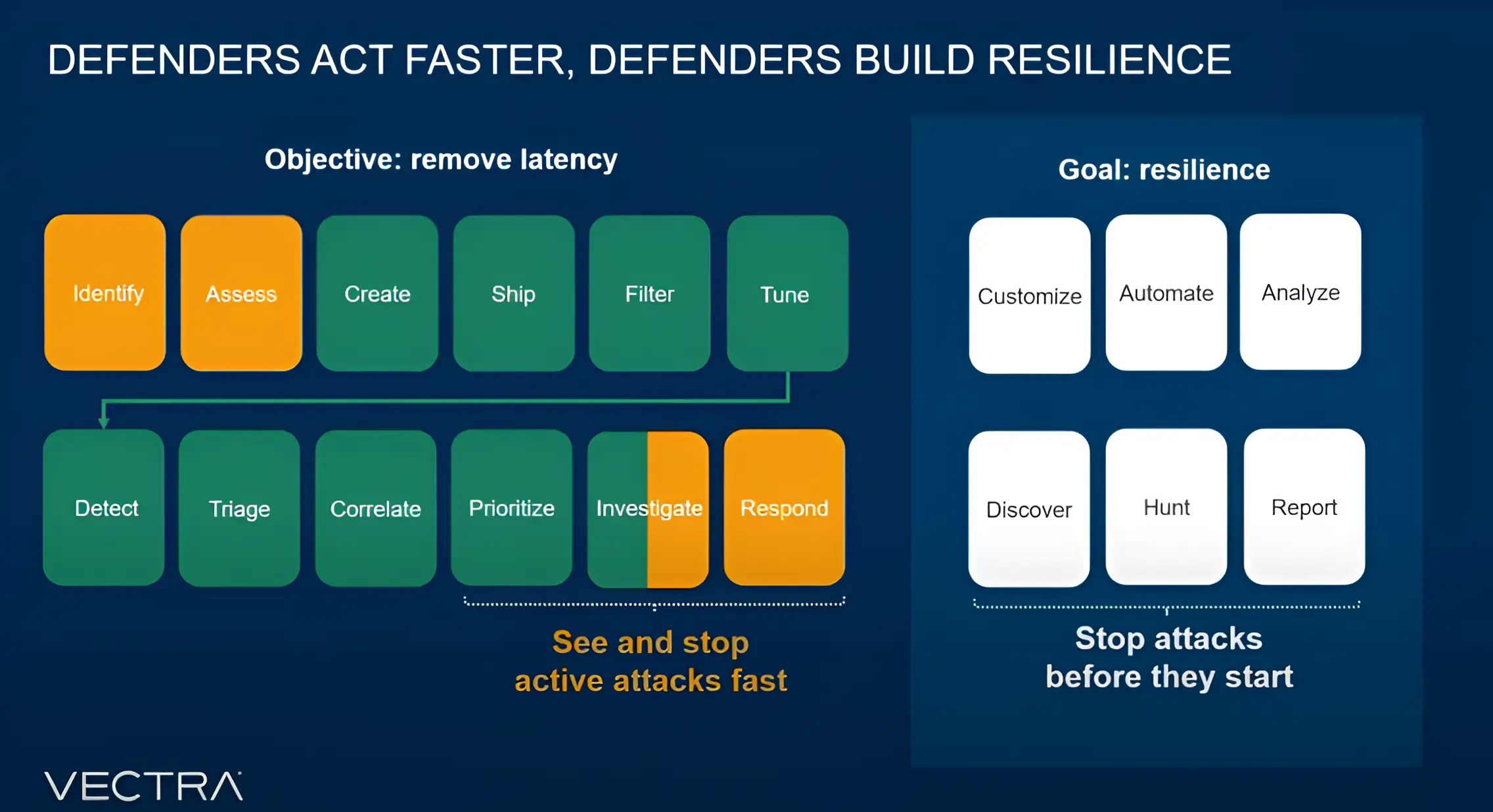
Protect today’s modern network with Vectra’s modern NDR
Detection needs for modern networks
Attackers thrive in complexity. They use the gaps between tools, the latency in detection workflows, and the lack of unified visibility to their advantage.
They are moving faster, adapting quicker, and using every possible route into a network. Traditional detection often fails because it treats each attack surface separately. In contrast, attackers see the entire interconnected network as one attack surface.
This speed is measurable:
- Average time from infiltration to lateral movement: 48 minutes (CrowdStrike).
If defenders cannot see across the entire environment at once, they will always be slower than the threat they are trying to contain.
Explore all the modern attack techniques
How are security operations teams evolving?
Security operations teams have shifted from reactive, incident-by-incident response to a proactive, intelligence-driven approach. This shift is necessary because modern attacks move too fast to allow for long investigative cycles.
Defenders are asking for two things above all: better quality signals and faster response times. Without accurate, context-rich alerts, security operations teams spend valuable time sorting through noise. Without speed, even the best signals arrive too late to stop an attack.
By removing latency in detection, automating triage, and prioritizing the highest-risk threats, AI allows security operations teams to focus on stopping real attacks in progress.
The role & impact of modern NDR
Network Detection and Response gives defenders the ability to see attacker activity that traditional endpoint or perimeter tools may miss. In the modern network, spanning on-prem data centers, cloud, SaaS, IoT/OT systems, and distributed identities, it observes traffic and behaviors as attackers move laterally, escalate privileges, or pivot between environments.
Modern NDR is most effective when it correlates signals across these domains into a single, coherent view. By doing so, it cuts investigation noise, elevates the behaviors that matter most, and enables defenders to act before intrusions spread further.
Attackers already think of the modern network as one giant attack surface. That perspective allows them to scale their campaigns faster than defenders can react. Seeing the network through the same lens is what makes modern NDR indispensable.
“Attackers just think one giant network attack surface, and that way of thinking enables them to scale their programs and campaigns much faster than we can.”
– Mark Wojtasiak, VP of Product Marketing, Vectra AI
Architecture patterns of modern networks
Modern networks share structural patterns that enable global collaboration and fast innovation, but they also expand the attacker’s advantage if left unchecked. Each pattern changes where latency appears in detection and response, and latency is exactly what modern attackers exploit.
- Hybrid and multi-cloud adoption: Workloads shift between environments, often crossing multiple providers. This increases complexity in monitoring and controlling access.
- Identity as the new perimeter: User and machine identities replace fixed network edges. Compromised credentials can provide a direct path to critical systems.
- Convergence of IT and OT: Operational technology systems are now connected to IT networks. This creates new opportunities for attackers to move laterally.
- Growth of unmanaged devices and machine identities: IoT devices, BYOD equipment, and service accounts often operate outside traditional security controls.
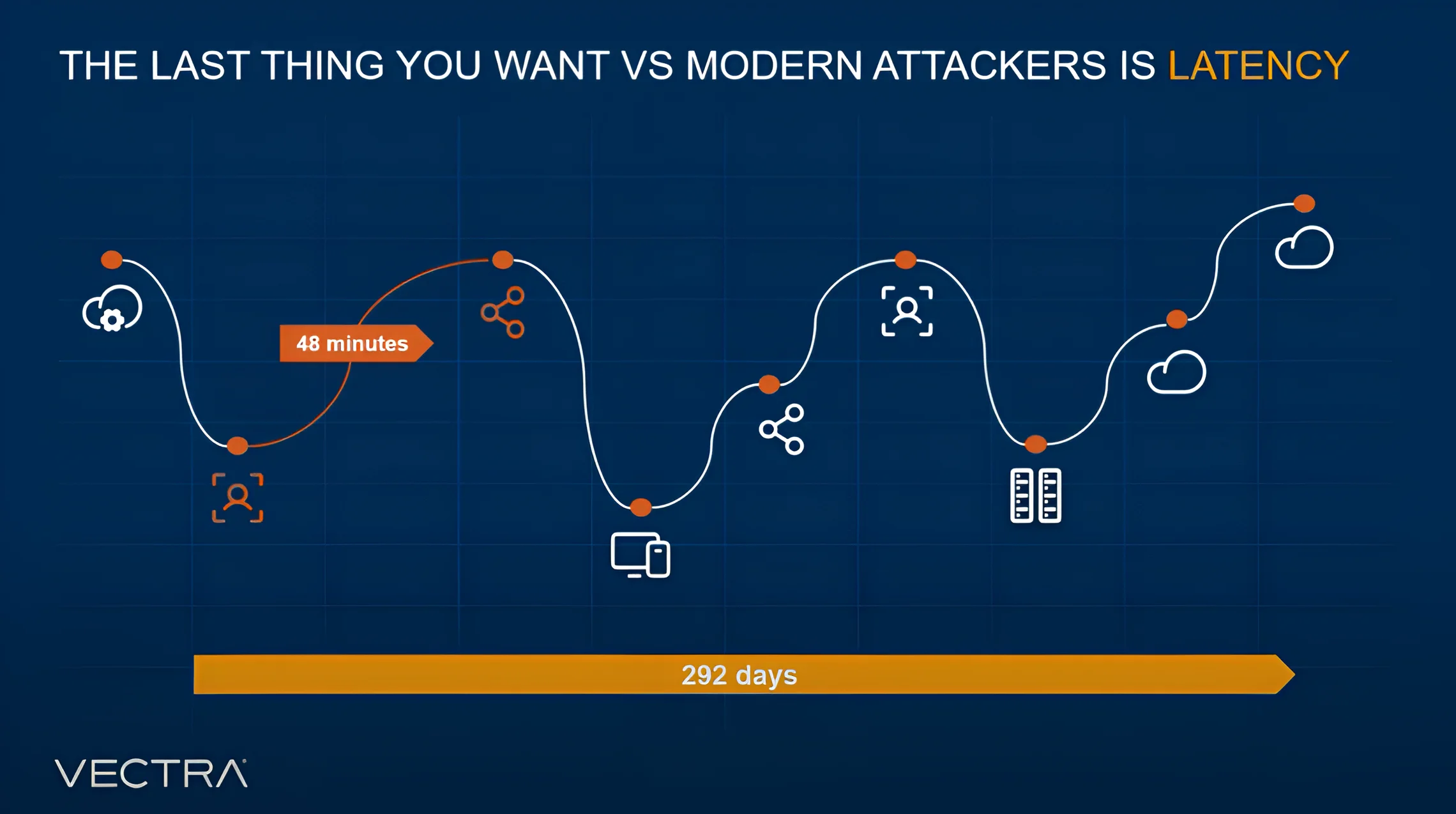
When these patterns intersect, attackers gain multiple ways to enter and escalate quickly if defenders are slowed by investigation delays. The diagram below illustrates this reality: the average time from infiltration to lateral movement is just 48 minutes, while defenders may spend an average of 292 days dealing with the aftermath of an undetected breach. This imbalance shows why removing latency is central to defending modern architectures.
Vectra AI’s approach
Vectra AI focuses on removing latency and delivering accurate, prioritized attack signals across network, identity, and cloud. By covering over 90% of MITRE ATT&CK techniques, our AI detection platform ensures visibility into the most relevant adversary behaviors.
Signals are correlated in real time and integrated directly into SOC workflows and SIEMs. This approach allows defenders to act within minutes, not hours, and ensures that their effort is spent on the threats that matter most.
Tour the Vectra AI Platform to see protection for modern network NDR.
Related cybersecurity fundamentals
FAQs
What is a modern network?
A modern network is no longer confined to a single location or a fixed perimeter. It is an interconnected environment that blends on-premises systems, cloud workloads, SaaS applications, IoT and OT devices, and both human and machine identities. These components constantly shift and interact, making it important to understand the elements that form this landscape, such as:
- On-prem, cloud, SaaS, IoT, and OT components
- Hybrid human and machine identities
- Continuous changes in devices, workloads, and user locations
Why do modern networks need advanced detection?
Modern networks present attackers with many possible points of entry. Threat actors often operate across multiple domains within the same campaign, moving from infiltration to lateral movement in less than an hour. Detecting and correlating this activity before it spreads requires visibility into key risk drivers, including:
- Targeting of multiple surfaces in a single campaign
- Lateral movement within 48 minutes on average (CrowdStrike)
- The need for unified visibility that spans on-prem, cloud, SaaS, identity, and IoT/OT
- Gaps in endpoint coverage, where some devices aren’t enrolled in EDR, or attackers bypass EDR entirely
How can SecOps teams stay ahead of modern threats?
Security operations centers are shifting from reactive responses to proactive defense models. By integrating signals from across the attack surface, applying AI to reduce latency, and focusing analysts on higher-value investigations, modern SOCs can better match attacker speed. This approach relies on several foundational practices, for example:
- Correlating alerts from network, identity, and cloud sources
- Using AI to prioritize the most critical threats and reduce noise
- Allocating more time to proactive threat hunting and investigations
How does a modern network NDR improve SOC efficiency?
A modern network NDR brings together telemetry from network, identity, and cloud to form a unified picture of attacker activity. This real-time correlation increases accuracy, reduces false positives, and shortens investigation cycles. SOC efficiency improves when teams can act based on the following advantages:
- Integrated, multi-domain visibility in one view
- Up to 99% reduction in alert noise
- Investigation time cut by as much as 50%
Which architectures define a modern network today?
Modern network architectures are designed for flexibility and distributed operations, but they also introduce new security challenges that must be addressed. These challenges are linked to the core architectural patterns shaping most enterprise environments today, such as:
- Hybrid-cloud and multi-cloud adoption
- SaaS-integrated operations
- Identity-centric security perimeters
- IT and OT convergence
Together, these architectures create a highly dynamic, interconnected ecosystem, expanding the attack surface and increasing the need for unified visibility and detection across every domain.