Cybersecurity authorities from the United States, New Zealand, and the United Kingdom have released a joint Cybersecurity Information Sheet (CIS) that recommends proper configuration and monitoring of PowerShell to address the recurrence of the scripting language's use in cyberattacks. The core message of the document is that while PowerShell remains a target of abuse by attackers, it provides too much of a benefit to organizations for defenders to disable it across enterprise environments. Instead of disabling the scripting language, the CIS recommends taking actions to reduce the chance of its abuse and to enable capabilities to detect when its abuse occurs.
Vectra Detect for Azure AD helps support teams follow the CIS's recommendations. Vectra monitors all users' Azure AD activity as they access cloud services, SaaS applications, and the Azure AD backend—and can see when that access is made using PowerShell. This monitoring feeds Vectra's Chaos dashboard and AI threat detections which together help teams reduce the chance of abuse of PowerShell and enable its detection.
Vectra's Azure AD Chaos Dashboard helps defenders proactively stop an attack by allowing them to review who and how PowerShell is used in their tenant. The Chaos dashboard highlights notable events related to potential security controls being bypassed, including PowerShell use. Each PowerShell access event is tracked with the specific users and PowerShell version reported for review. This information allows teams to place additional controls on users to minimize the risk of a user's PowerShell access being abused during an attack.
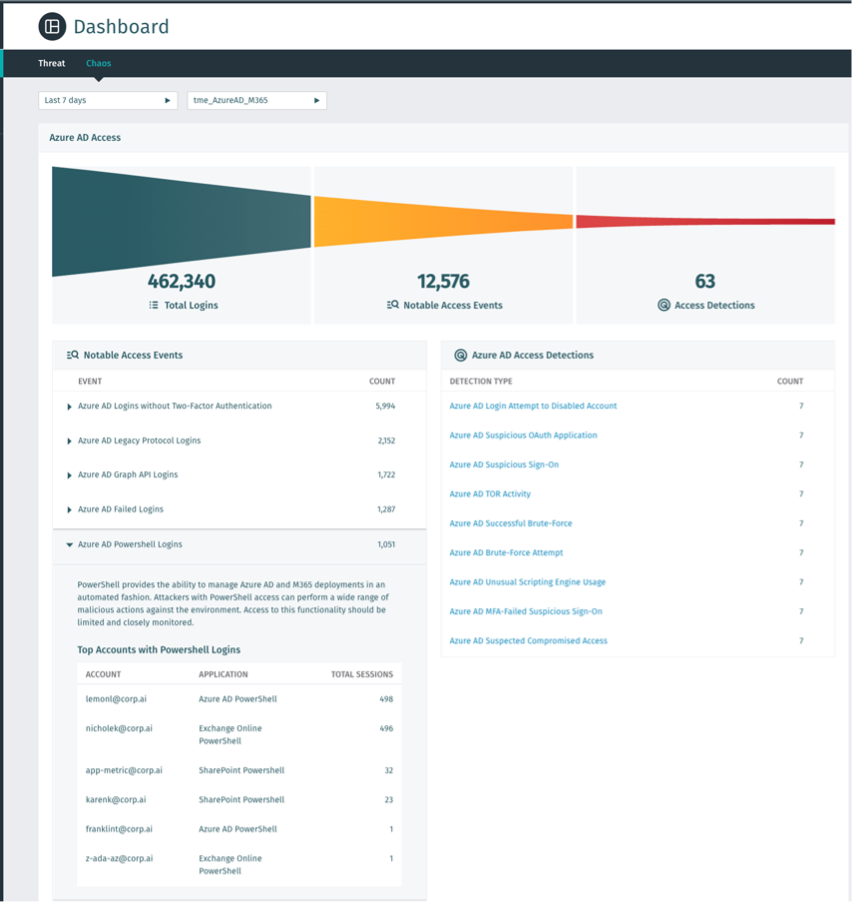
Vectra's Azure AD Unusual Scripting Engine Usage detection alerts on attackers abusing PowerShell or other scripting engines within Azure AD and SaaS environments. The alert first understands how scripting engines are commonly used by users. It then detects abnormal usage that would be aligned with an attack. This alerting enables Vectra to see a range of active threats early, ranging from initial breaches to the automation of attacks against the Azure cloud. Alongside Vectra's other Azure AD and Microsoft 365 alerts, a defender can quickly see and stop an attacker from progressing to their objective.
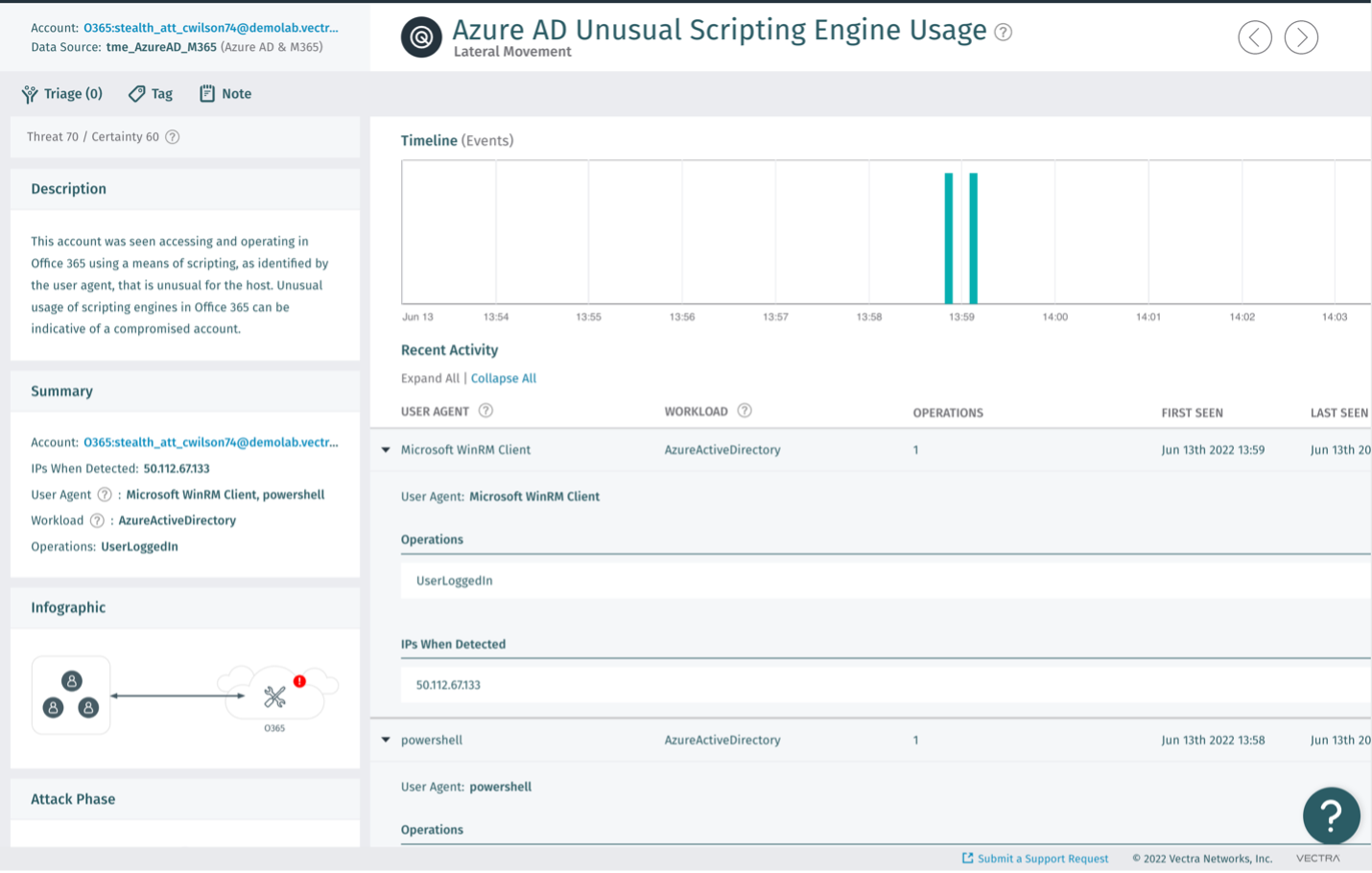
So, while it might be instinctive in some cases to disable PowerShell as a precaution to stop potential cyberattacks, such drastic measures aren't necessary with the right tools and controls in place. The CIS states that PowerShell is essential to secure Windows and that "removing or improperly restricting PowerShell would prevent administrators and defenders from utilizing PowerShell to assist with system maintenance, forensics, automation, and security." Instead, concerned security teams should have a plan in place to detect and stop a compromise if, and when one occurs.
For additional information about detecting attacks that leverage PowerShell or Azure AD, head over to the Vectra page on securing Azure AD.

