Our customers rely on Vectra AI to detect, investigate, and respond to attacks at the speed and scale of hybrid attackers. However, even with advanced detection capabilities, our users often want to understand the alerts they receive and the context around detections. This additional information is used to contextualize findings and answer crucial questions such as the identity of the actors involved, whether the activity is malicious or legitimate and where else the activity is occurring, and if the actors persist elsewhere.
Understanding the Investigative Workflow: When and How Vectra AI Comes to the Rescue
As part of our ongoing UX research, we noticed that SOC teams typically investigate when they receive a detection that they don't fully understand — when information is missing or not correctly parsed. When analysts come across a detection, investigation becomes important as a way to gather further information to understand the indicators of compromise or what the actor was up to in the past hours, so they can spot and compare normal to malicious behaviour. This information is essential to demonstrate what happened, build evidence and have enough context to act.
“Our first step is to understand who the actor is and the legitimacy of the activity.”
– Use case research, multiple users answer
In the event of a malicious attack, the SOC analysts’ response becomes a critical race against time. Within a brief span, analysts must quickly evaluate circumstances, determine the legitimacy of the activity, identify the actors involved and isolate the compromised systems.
Through research and many in-depth conversations with customers, it’s clear that too often investigations can be time-consuming and complex — SOC analysts often need to switch between multiple tools to find crucial information and create a coherent understanding of the events — having to learn complex query languages to interrogate their data. Acting fast becomes crucial when there's a need to respond to potential malicious activities. Therefore, having easy access to relevant data is extremely important in such situations.
That's why Vectra AI started the journey to create tools to facilitate the SOC analysts’ investigation workflow, seamlessly gathering data from both cloud and network sources and consolidating it within a single, readily accessible platform — enabling effortless investigation at any given moment.
Streamlined Investigations: Introducing Instant Access with the Vectra AI Platform
To assist SOC teams with investigating patterns and potential malicious behaviours as fast as possible, the Vectra AI Platform encompasses a set of pre-defined queries directly into the entity page. This allows analysts to gain quick insights into an actor’s activities and have the most valuable data at their fingertips.
Instant Investigation offers users a curated collection of queries containing the most pertinent and aggregated data. These queries are readily accessible within the scope of an entity, facilitating effortless comparison between the detections triggered by the actor and its typical behaviour, eliminating the need to learn a new language, spend time building queries, or hunt for relevant information. This allows analysts to have the most crucial insights readily available.
These queries reflect the combined expertise of our professionals regarding the primary data to analyse in the face of various detections, while guiding users to delve into activities that should be prioritized for comprehensive investigation to response to potential security threats.
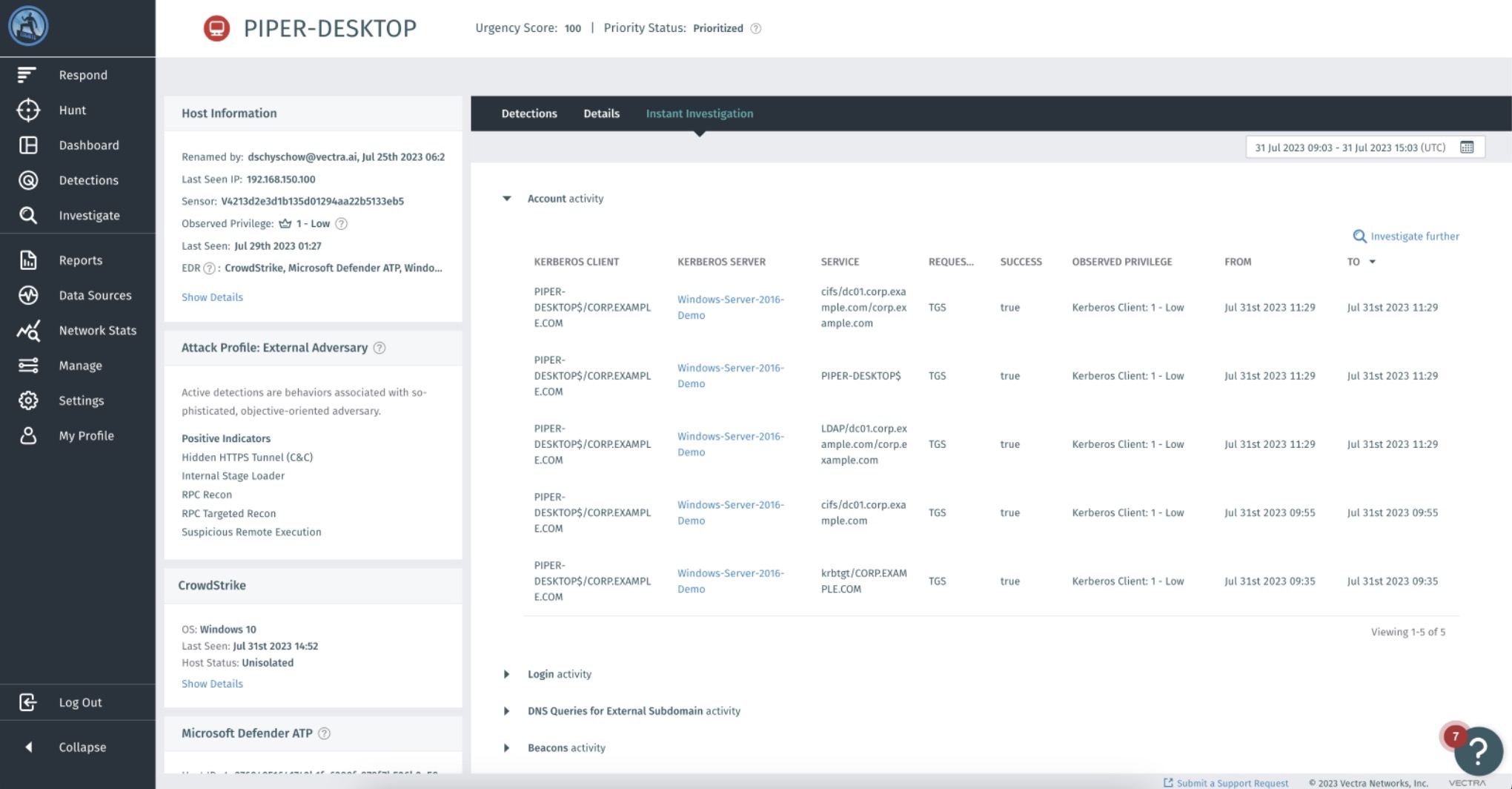
Elevate Your Analysis: Vectra AI's Advanced Investigation Tools Unveiled
Advanced Investigation for Comprehensive Insights
If the data presented in Instant Investigation is insufficient, or if there are indications of potential malicious activities, users can seamlessly dive into a more advanced investigation and immediately start analysing data thanks to a curated collection of default columns crafted by our experts that include the most relevant information.
Enhancing Understanding with Enterprise Search
Vectra AI's enterprise search function, built on top of Vectra AI-driven Attack Signal IntelligenceTM, enriches the users' understanding of the alerts they receive, adding a new level of detail and context. Our customers can now effectively investigate incidents directly within the Vectra UI, eliminating the need to exit the platform to find the answers they seek.
Flexible Data Interaction
This advanced feature presents a complete, non-aggregated view of the data in a comprehensive format. Users can interact with the data easily by manipulating the tabular view, adding columns, creating custom filters and extending the time range. Such capabilities equip them to proactively hunt for more pertinent information and delve into a more intensive investigation as necessary.
User-Friendly Query Building
During usability testing of our new investigation tools, we observed that learning a new query language for data exploration is both challenging and time-consuming, and it may not align with the preferences or needs of all customers. In the race against time that characterizes investigations into potentially malicious events, the ability to save time by efficiently crafting queries becomes crucial.
Powerful and User-Friendly Query Solution
Advanced Investigation provides a powerful, custom-built enterprise search solution that offers the flexibility and guidance that analysts need to conduct thorough investigations without having to learn another query language.
Through the implementation of this new investigation workflow and the introduction of a user-friendly query builder, the Vetra AI Platform empowers analysts of all levels, from junior to senior — to conduct investigations with enhanced efficiency and effectiveness.
Simplified Data Exploration for All Skill Levels
When testing the feature, we noticed that it proved exceptionally beneficial for junior analysts who may lack proficiency in advanced query languages. We observed that these individuals found this query-creation method to be both user-friendly and highly effective.
Now, anyone, regardless of skill level, can delve into the data and craft a query simply by adding a few filters. This streamlined process empowers all analysts to better safeguard their organizations from cyber threats.
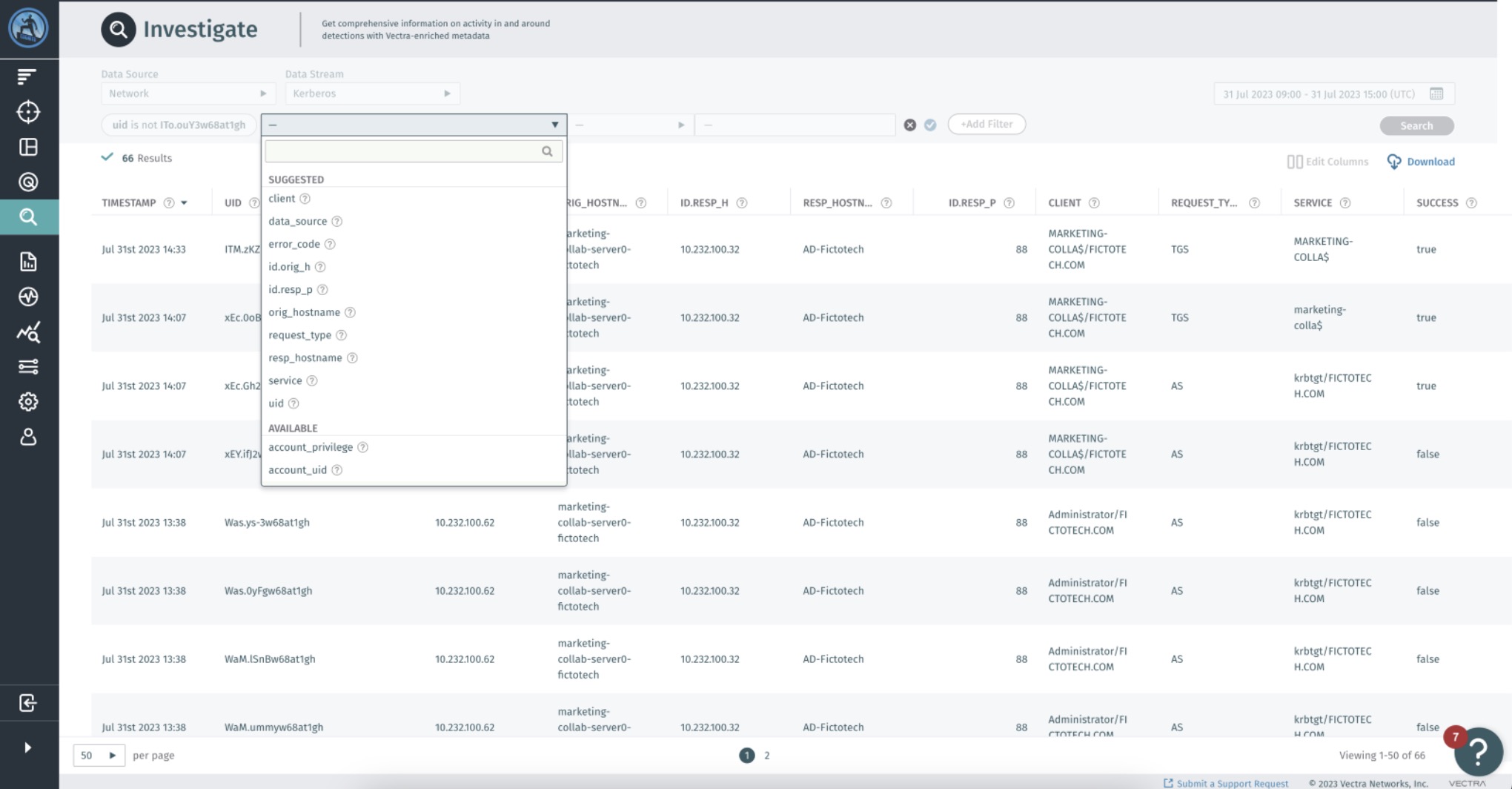
Focusing on Relevant Data
Through our customer feedback, SOC analysts face a challenge of dealing with a vast amount of raw data. Vectra AI ensures that SOC teams only interact with the most relevant fields, allowing them to quickly navigate the information essential for their investigation workflow.
Connecting the Dots Across Attack Surfaces
Moreover, to help customers to recognize patterns in actors’ behaviour across their hybrid cloud environment, the Vectra AI Platform enhances the data by connecting the actor’s activities across different attack surfaces. This approach allows for a comprehensive understanding of potentially threatening movements as they interact with diverse data sets.
"Advanced Investigation, is easy to read so you can quickly determine what is going on and drill down, for more queries. That's very useful." – MSSP customer
Learn how to arm your SOC with Instant Investigations by reading the tech overview or try our self guided platform tour.

