The Transition from On-prem to Hybrid Cloud
Managing your ever-changing network, especially when expanding to a cloud environment is no simple feat. There’s not a one-size-fits-all approach to securing your cloud environment. Our customers have identified three key themes that are driving them to the cloud:
- Scale & agility
- High availability
- Integrated services
While the benefits of the cloud are real and numerous, it also comes with additional security considerations often left unaddressed during upfront deployments. In this blog, we’ll examine known threats aimed at hybrid cloud environments and where you might be able to catch them before they become an issue.
Accelerating Threats in Hybrid Cloud
Accelerator 1: Quick & easy cloud deployment often results in security process slips
In most organizations, there are several teams involved with deploying new services, acting as unintentional safety nets before a service is deployed to the internet, but with the cloud, this isn’t necessarily true. While the threats against cloud workloads are not truly much different than those that affect their on-prem kin, the facts remain the same. It is much easier to deploy resources and modify configurations in the cloud. Although all attacks are possible on-prem, in the cloud it takes little more than an email address and credit card to deploy and expose your crown jewels. Add in automation, and this can happen in minutes.
Accelerator 2: Lateral movement between cloud and on-prem
For access and administrative purposes, often there are links between cloud workloads and on-prem systems. This means that a breach in the cloud can often result in a breach of on-prem resources using lateral movement. Most often, lateral movement is facilitated by site-to-site VPNs or other authorized connectivity. Attackers are seldom satisfied with whatever access they can procure through the initial compromise of data center resources. Instead, they will try to escalate a breach to target core systems where proprietary data lives and they can inflict the most pain on core infrastructure.
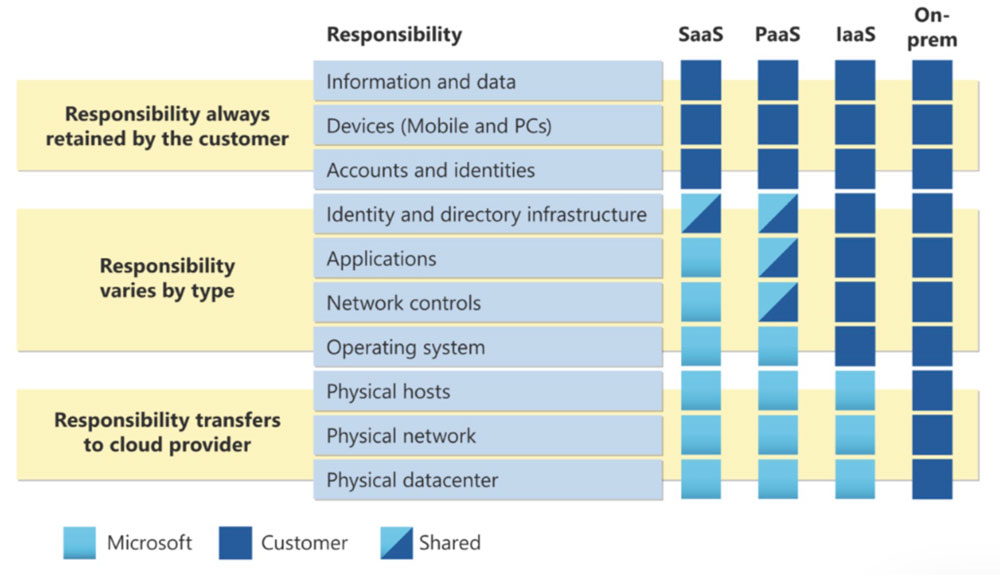
Accelerator 3: Hybrid cloud & the trials of shared responsibility
Another aspect of the cloud that is often overlooked or misunderstood is the ownership and responsibility model of the cloud provider vs. the customer. When using the cloud for workloads (IAAS), you are still responsible for the security and administration of your cloud workloads just like on-prem.
Even in the scenario where you are leveraging solutions like EC2 or AWS Open Search you still have some responsibility to secure your implementation (PaaS).
Don’t Worry, Now’s Not the Time to Jump Ship with Cloud
All these factors can give an organization pause when looking to take advantage of or extend cloud adoption. Yet cloud and hybrid deployments are a must in today’s working world. Instead of trying to prevent or stand in the way of your organization’s migration to the cloud, consider your more moderate options — for our purposes, we’ll feature Vectra AI examples below:
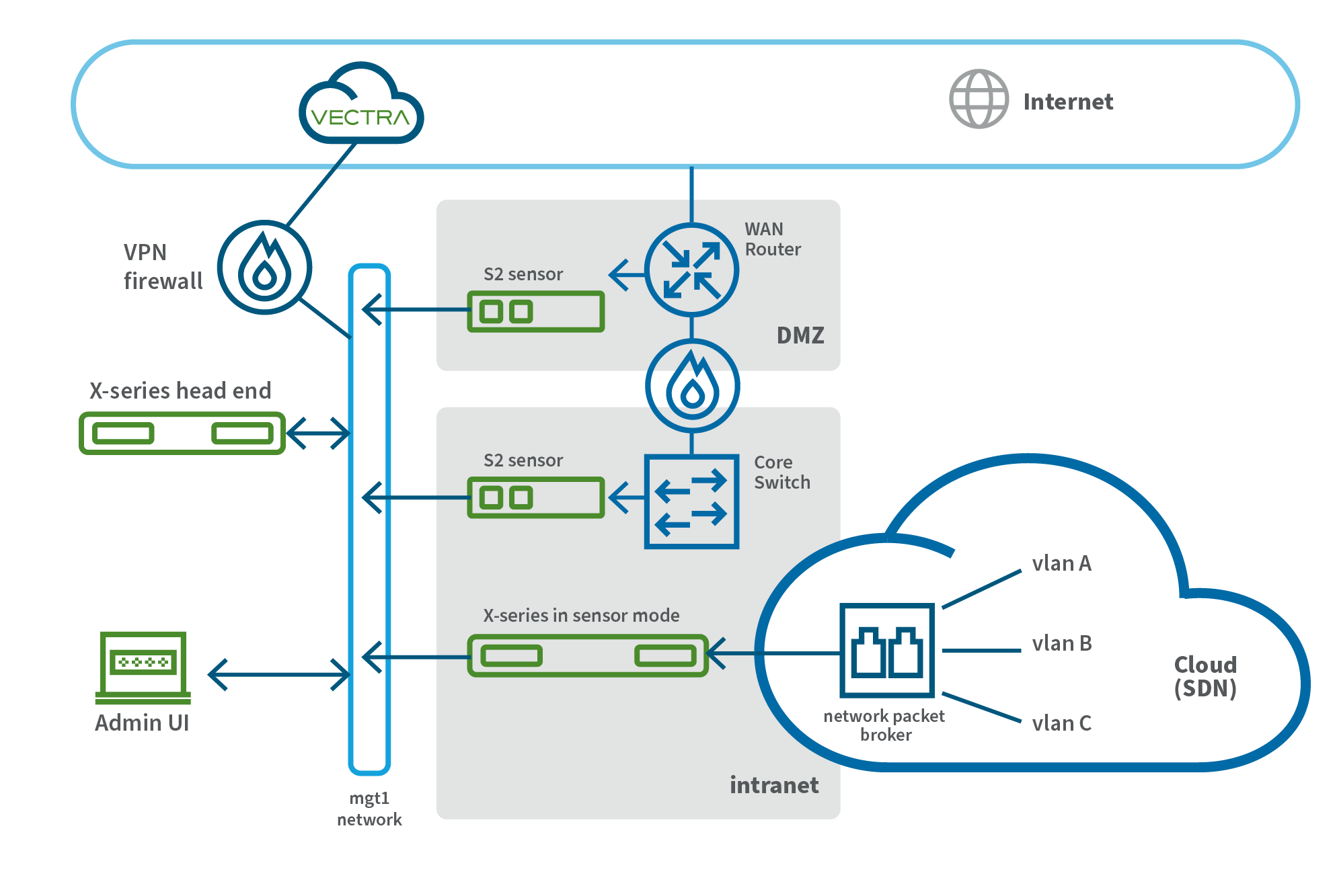
- Seamless Integration: Vectra cloud sensors can plug in seamlessly to protect your cloud workloads against network threats, lateral movement and escalation. This is accomplished the same way it is on-prem, by passively monitoring network traffic supplied by the cloud vendor to/from your workloads. Learn more about Vectra NDR, today.
- World Class AI Detections and Prioritization: Vectra harnesses Security AI-driven Attack Signal Intelligence™(ASI), to monitor threats against cloud, SaaS infrastructure, identity and on-prem. This is provided out of the box with no onus on the customer to build detections. ASI helps SOC and security teams to aggregate, contextualize and prioritize the most important host and accounts so you have actionable information at your fingertips to enable rapid response. See what ASI can do for you.
- Unified Threat Detection: Vectra provides a single user interface to tie all the different threat vectors together. This is important because attackers often try to pivot from cloud to on-prem, SaaS to on-prem, or cloud to cloud, so having this capability within a system that has knowledge of each aspect is critical. Explore more about Vectra’s TDR platform.
In our next blog, we will explore how Vectra can help protect multicloud environments which introduce new attack surfaces and challenges. Stay tuned!
Want to learn more? Schedule a demo today.

