Vectra Active Enforcement for the Demisto security automation and orchestration platform




Learn all about our partnership.
Download Integration Brief
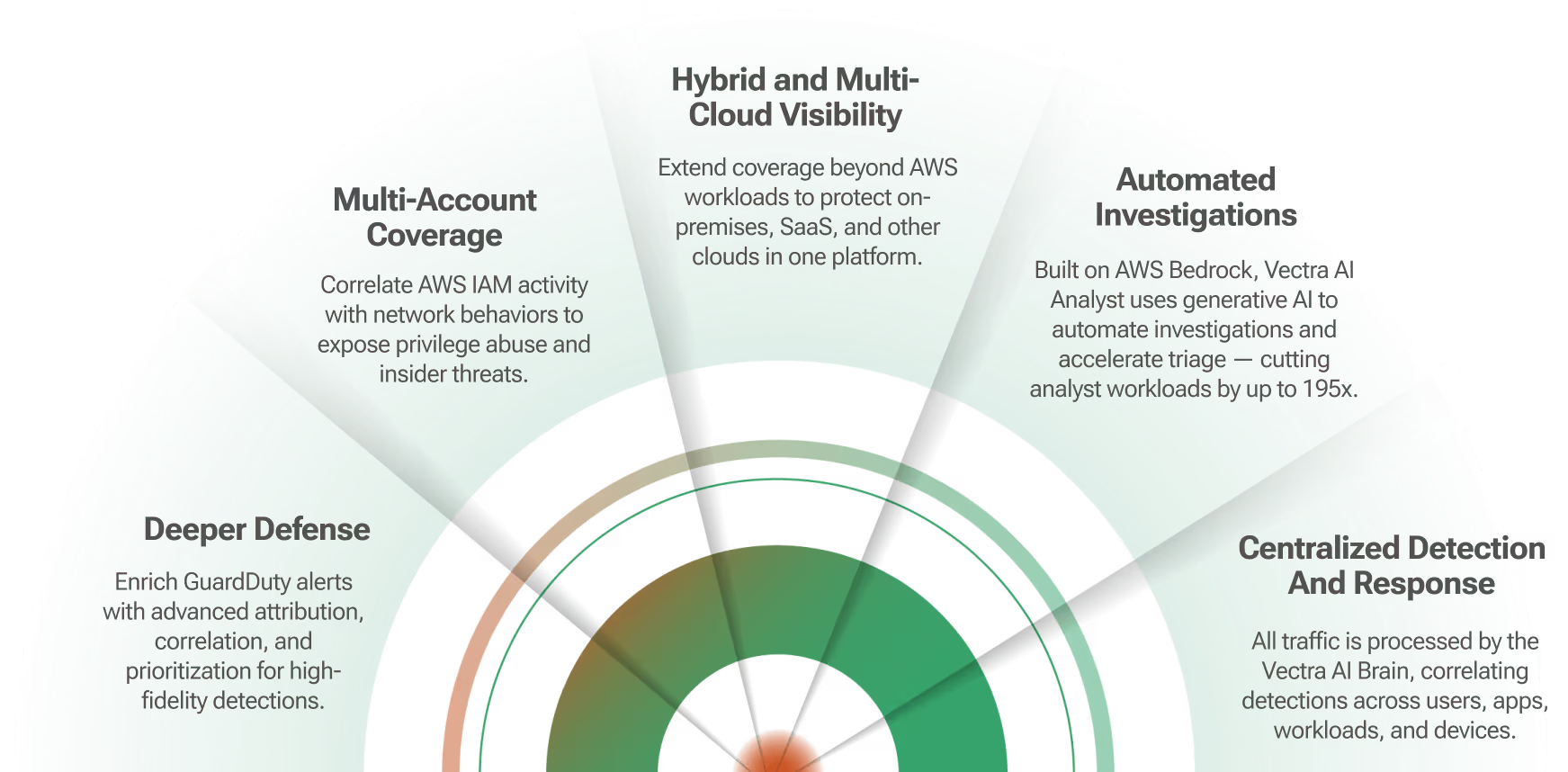
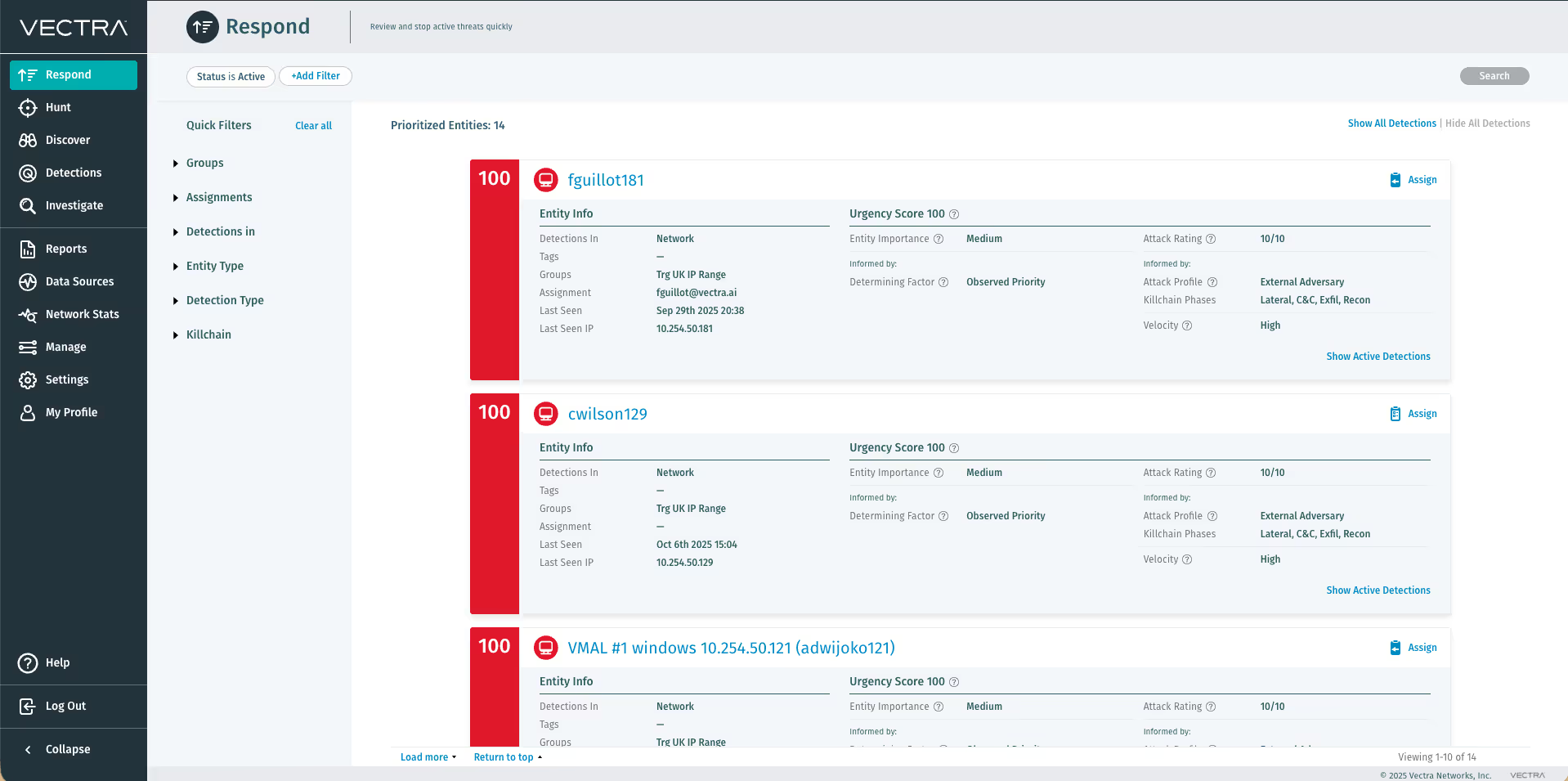
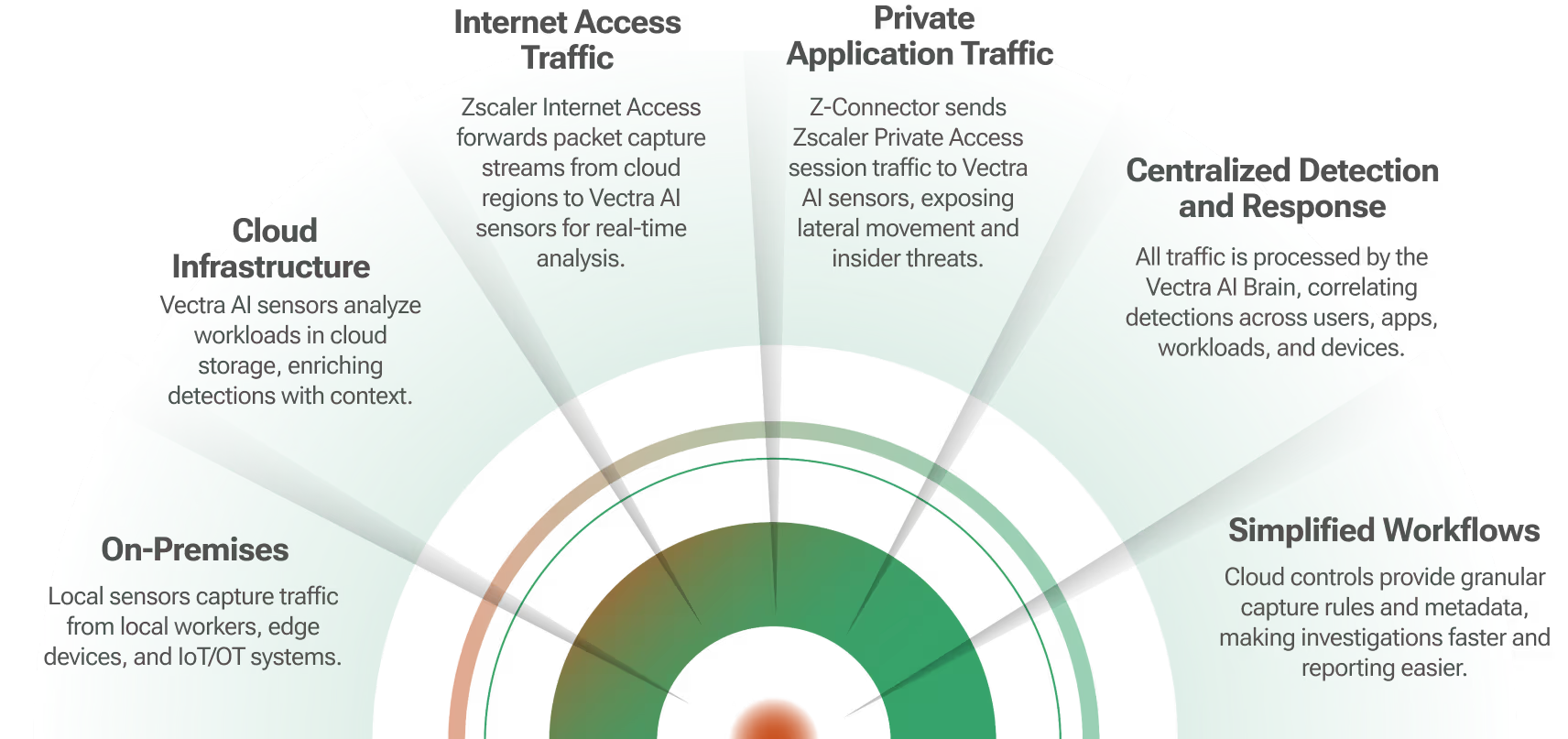
There is a need to close the cybersecurity skills gap facing enterprise security operations teams. The Vectra Active Enforcement application for Demisto enables security teams to quickly expose a variety of hidden cyber attack behaviors, pinpoint host devices at the center of an attack, and block threats before data is compromised or stolen.
The Platform
The Platform
Vectra AI Platform
The integrated signal for extended detection and response (XDR)
Vectra AI Platform
MXDR Services
Technology Integrations