Vectra AI + Superna
Safeguard your data with an integrated and automated approach to security




Learn all about our partnership.
Download Integration Brief
Bridge the gap between detection and response with automation playbooks and critical AI technologies.
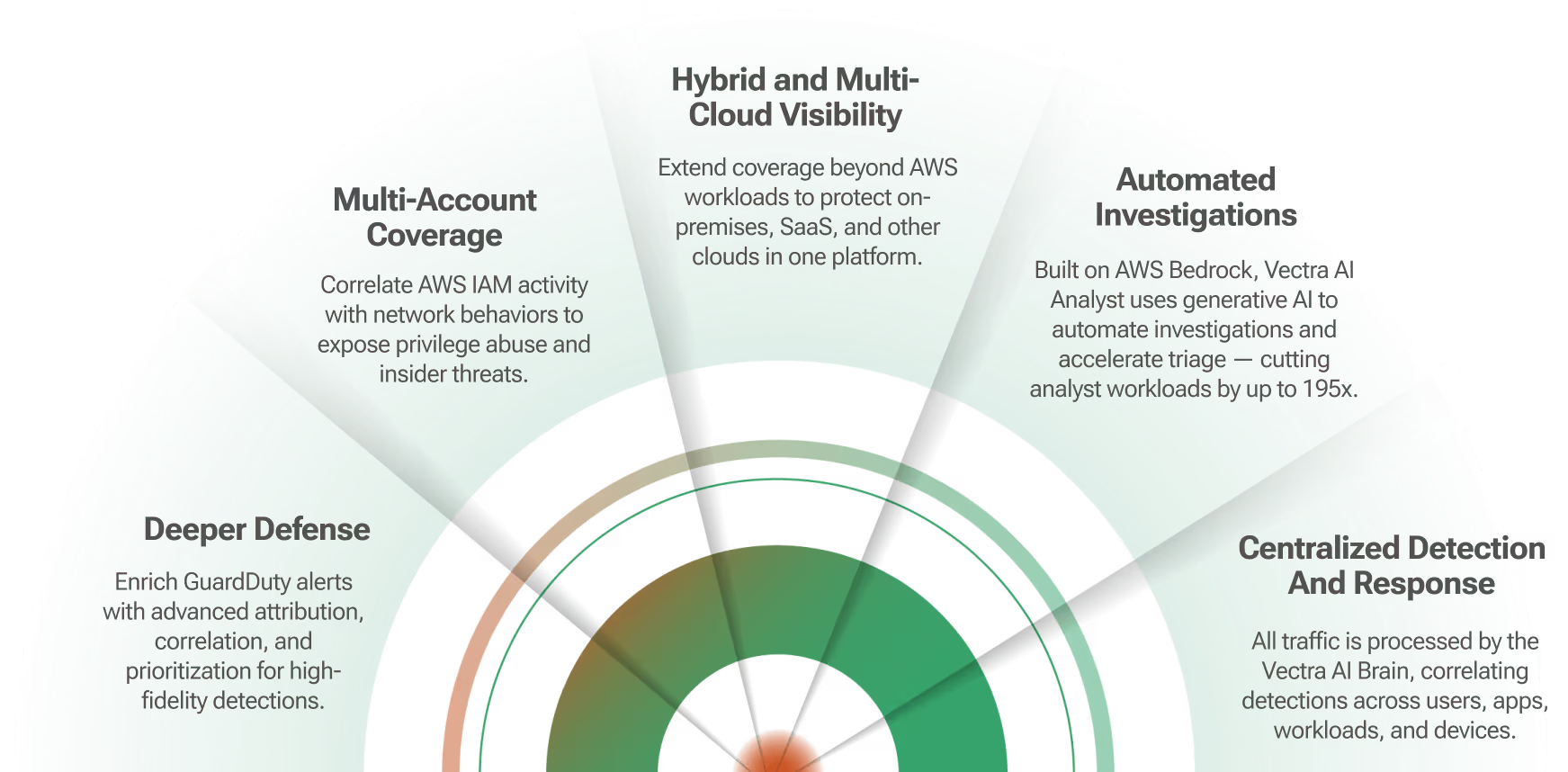
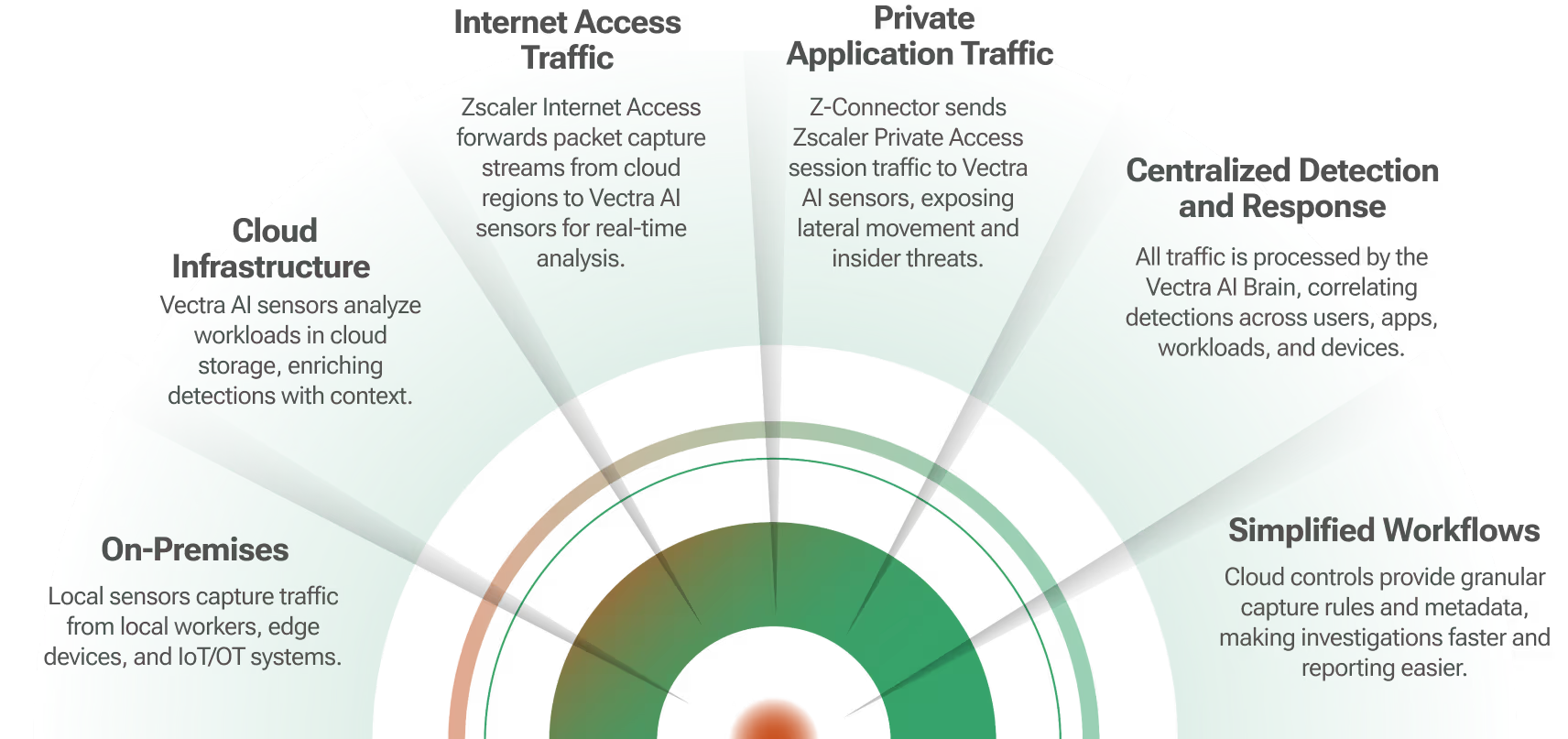
With the adoption of more and more hybrid environments, maintaining a cohesive security program continues to be a challenge that many organizations face, especially when it comes to detecting threats and responding to them with confidence and speed. Vectra AI and Superna’s technical integration combines Network security and Cyber Storage security with automation allows customers to execute automated playbooks that provide SOC teams with the tools they need to protect corporate data.
Key benefits of the Superna and Vectra AI integration:
- Rapid, confident, and automatic response to threats
- AI-driven threat prioritization with Vectra AI’s Attack Signal Intelligence
- Mitigation before attack fully occurs, avoiding a costly recovery
- Real-time auditing and historical forensics for effective remediation with Superna
How it works
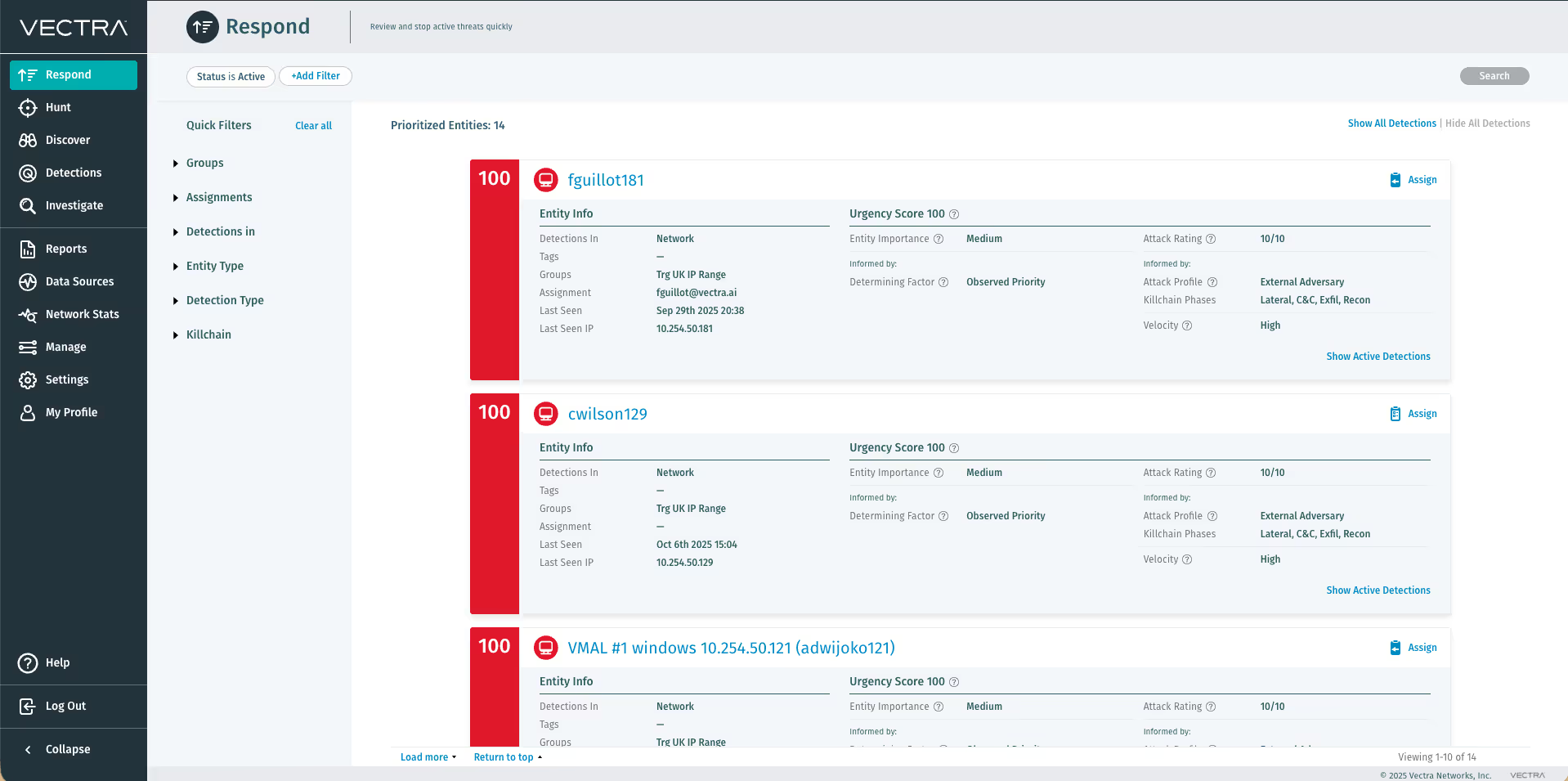
Vectra AI uses advanced artificial intelligence to identify and prioritize suspicious activity early in the attack progression — before any damage is inflicted. When individual threats or attack profiles target data, Vectra AI notifies Superna through automation playbooks, so that critical data can be immediately placed into a protective, immutable state and lockout the compromised user account without impacting production data access for other users. Thus, securing the data and isolating the user's data access and preventing the need for costly recovery.
Additionally, Superna delivers its real-time analytics and historical forensics at the data layer, understanding when a nefarious activity timeline is critical to root cause and remediation. This advanced, real-time auditing and historical view of data activity helps secure and provide forensics to assist in root cause and impact radius of a compromised IT environment.
The Platform
The Platform
Vectra AI Platform
The integrated signal for extended detection and response (XDR)
Vectra AI Platform
MXDR Services
Technology Integrations