Vectra AI and Gigamon: Automate threat detection and response with Gigamon Deep Observability Pipeline and the Vectra AI Platform




Learn all about our partnership.
Download Integration Brief
Gain full coverage, clarity, and control on attackers with Gigamon’s traffic optimization and Vectra AI’s threat intelligence.
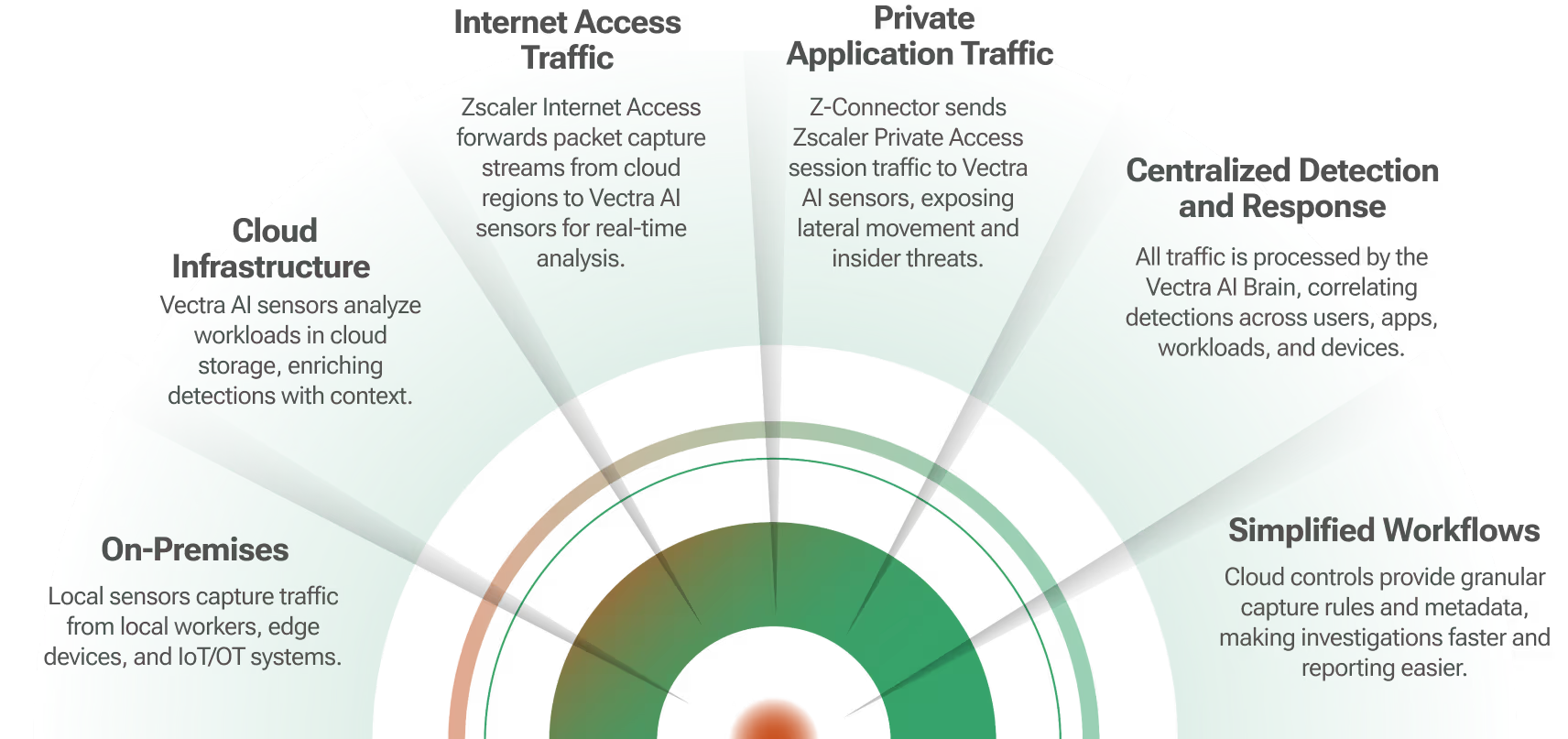
With the Gigamon Deep Observability Pipeline from Gigamon, Vectra NDR provides continuous monitoring of internal network traffic to pinpoint in-progress cyberattacks that evade perimeter defenses. Gigamon accesses traffic across physical and virtual networks, filters this traffic, and sends the intelligence to Vectra AI for real-time threat analysis. The Vectra AI Platform automatically detects cyber threats hidden in approved applications and encrypted traffic, correlates those threats to the hosts that are under attack, and delivers unique context about what attackers are doing, enabling security teams to quickly prevent or mitigate loss.
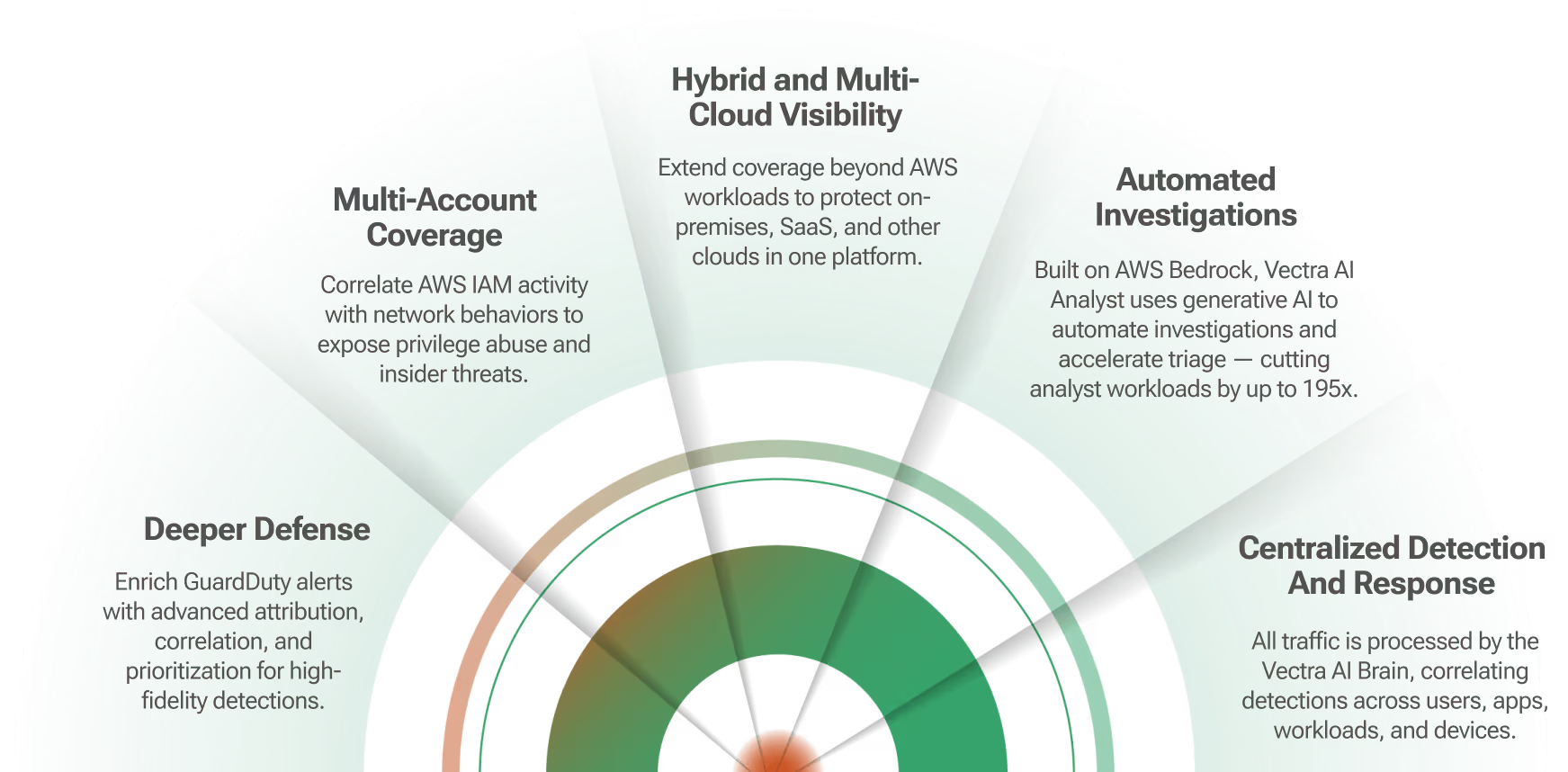
Key benefits of the Gigamon and Vectra AI integration:
- Vectra NDR detects in-progress cyber-attacks that evade prevention security defenses and spread inside networks – automatically and in real-time.
- Offering visibility into physical, virtual traffic across the network, Vectra NDR combines data science, machine learning, and behavioral analysis to detect all phases of a cyberattack.
- Gigamon taps traffic across physical, private cloud, public cloud, and container environments and delivers the intelligence to Vectra NDR on the physical network – ensuring all traffic is monitored and analyzed to avoid blind spots. Gigamon ensures that only relevant traffic and sessions are sent to Vectra AI, prioritizing security efforts on traffic that poses the most risk.
- Together, Vectra and Gigamon offer a turnkey solution to secure traffic in virtualized environments. Customers do not need an intermediary to feed cloud traffic into Vectra AI – significantly simplifying the process of implementation.
How it works

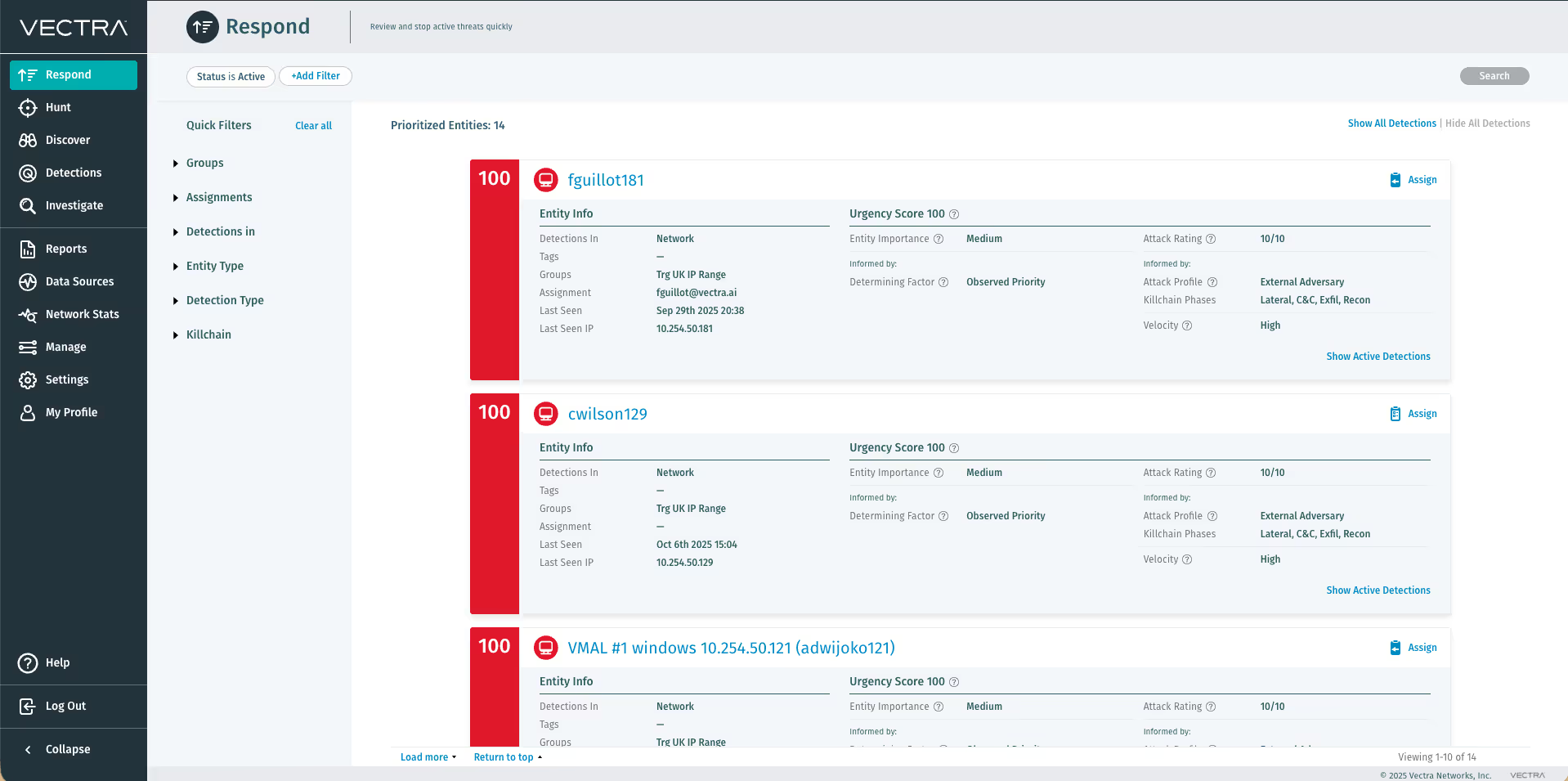
The Gigamon Deep Observability Pipeline communicates with taps sitting across an infrastructure to access East-West traffic. Once East-West traffic is accessed by taps, it is then sent to either GigaVUE® HC series appliances in physical datacenters or mirrored to GigaVUE® Visibility Nodes in virtual environments for aggregation, deep packet inspection, and filtering of traffic. The HC series and Visibility Nodes then present a filtered intelligence stream that contains only important traffic to the Vectra AI Platform. Once the Vectra AI Platform receives the network traffic from Gigamon, it is automatically correlated with detected threats and prioritized on the user interface.
How we partner with Gigamon
Learn more about how Vectra AI and Gigamon partner together
The Platform
The Platform
Vectra AI Platform
The integrated signal for extended detection and response (XDR)
Vectra AI Platform
MXDR Services
Technology Integrations