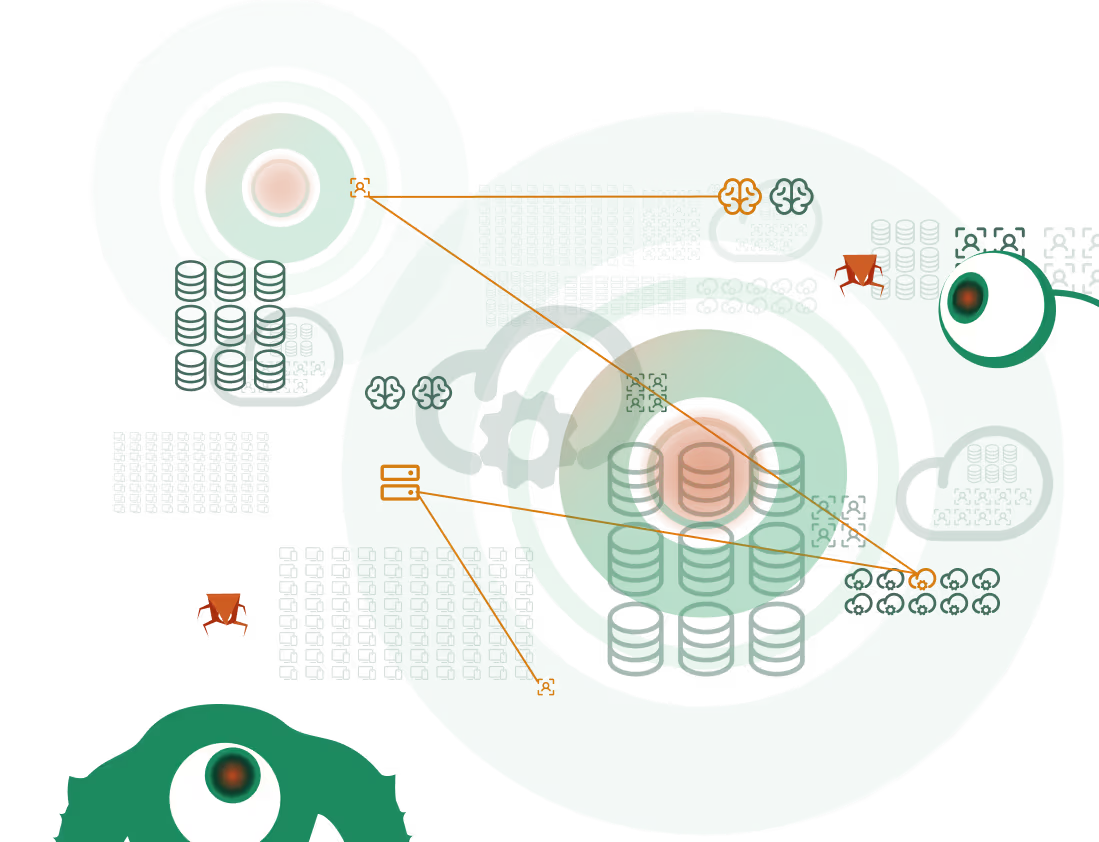
The network has changed
We went remote
And into the cloud
The cloud grew
And has become more complex
Expanding to identities
Now IT and OT are converging
Into one giant attack surface
Scroll to discover the modern network
Attackers have more options than ever to get in — and even more places to hide.



Scroll to discover the modern network
The network has changed
We went remote
And into the cloud
The cloud grew
And become more complex
Expanding to identities
Now IT and OT are converging
Into one giant attack surface
Attackers have more options than ever to get in — and even more places to hide.

Scroll to discover the modern network
Introducing
The platform that protects modern networks
from modern attacks
Vectra AI sees attackers’ every move. Our advanced AI/ML connects the dots as attackers move across network, identity, and cloud — so you can stop them.
Vectra AI Platform
MXDR Services
Technology Integrations
See how the Vectra AI Platform protects your entire network.
Explore the Platform
Why Vectra AI
The world leader in AI security
We give your security teams the advantage…
#1
Most-referenced in MITRE D3FEND
35
AI threat detection patents
>90%
MITRE ATT&CK coverage


To stop real attacks in real time
90%
fewer blind spots
80%+
alert fidelity
38x
lighter analyst workload
What does the Vectra AI Platform detect?
Our AI-driven detections reveal modern attacks early in their progression, so you can stop them before damage is done.
Explore Detections
See why 1,600+ security teams trust Vectra AI to find and stop attacks
Industry Recognition
What are global experts and analysts saying about Vectra AI?

Vectra AI named a Leader in NDR 2025
2025 Gartner® Magic Quadrant™ for Network Detection and Response

Gartner
Vectra AI is the only vendor to be named Customer’s Choice in the Voice of the Customer for Network Detection and Response.

IDC names Vectra AI 2024 global leader for Network Detection and response

2024 SPARK Matrix Leader
QKS Group positions Vectra AI as a Leader in the 2024 Spark Matrix for Network Detection and Response (NDR).

2025 GigaOm Market Leader
Vectra AI recognized as a Leader and Outperformer in the GigaOm Radar Report for Identity Threat Dectection & Response

2025 GigaOm Market Leader
Vectra AI was named a Leader in the 2025 GigaOm Radar Report for Network Detection and Response.
Stop attacks 99% faster with Vectra AI
On average, it takes 10 months to identify and contain a breach. With Vectra AI, it’s closer to 10 minutes.
*Vectra AI stops identity attacks — the most common and dangerous attack type — within 24 hours. That’s 99% faster than the average 292 days it takes to find and contain breaches involving stolen credentials. (Source: IBM Data Breach Report)
































.webp)






