I recently had the chance to sit down with René Kretzinger, a senior threat hunter at Infoguard, to talk about real-world threat hunting. He shared how he uses the Vectra AI Platform in his day-to-day work to uncover threats, investigate incidents, and close visibility gaps. Below are key insights and examples shared directly from his experience in the field.
What Is Threat Hunting? A Practitioner’s View
Threat hunting is a proactive, hypothesis-driven process designed to uncover threats that traditional alert-based systems might miss. It involves assuming compromise and actively seeking out signs of adversary behavior. Rather than waiting for an alert, threat hunters use contextual knowledge, intuition, and behavioral clues to identify abnormal or malicious activity.
Effective threat hunting hinges on visibility. If you can't see it, you can't hunt it. Having telemetry across the network, endpoints, identity systems, and cloud environments is the foundation. It's also a mindset—you must think like an adversary while defending your environment.
Building Blocks of Effective Threat Hunting
- Visibility: Collect data across your full attack surface: DNS logs, SMB logs, proxy traffic, endpoint process logs, authentication records, USB activity, identity activities and cloud usage.
- Data Centralization: Aggregate telemetry in one place. Fragmented logs slow detection and reduce accuracy.
- Baselining: Establish "normal" behaviors to detect deviations more effectively.
- Adversary TTP Knowledge: Study real-world attack playbooks and tools to hunt for adversary behavior.
Types of Threat Hunting and Real-World Examples
1. Baseline-Based Hunting
Baseline hunting begins with understanding what is typical across systems, users, and applications. This might involve cataloging how many remote management tools are expected in the environment and on which systems. When HR workstations, which usually don’t run any RMMs, show ten or more installed, that’s a strong deviation from the norm and a potential signal for insider misuse or misconfiguration.
Scheduled tasks also offer clues. For example, a task found on a non-administrative workstation launching PowerShell scripts during off-hours can prompt an investigation into unauthorized automation or attacker persistence.
Another example involves browser extensions. A legitimate-looking extension might be installed across multiple endpoints but initiates connections to Mega or Telegram APIs, which are uncommon destinations for enterprise traffic, highlighting data exposure concerns.
2. Threat Actor TTP Hunting
This approach involves hunting based on known attacker tactics, techniques, and procedures (TTPs). For example, when ransomware groups or other threat actors leak their tools or techniques, those indicators can be used to search for similar activity within an environment. Tools such as Rclone or Mimikatz are often renamed by attackers, but their command-line behavior remains unchanged. Hunting by command-line arguments helps detect these tools even when obfuscated.
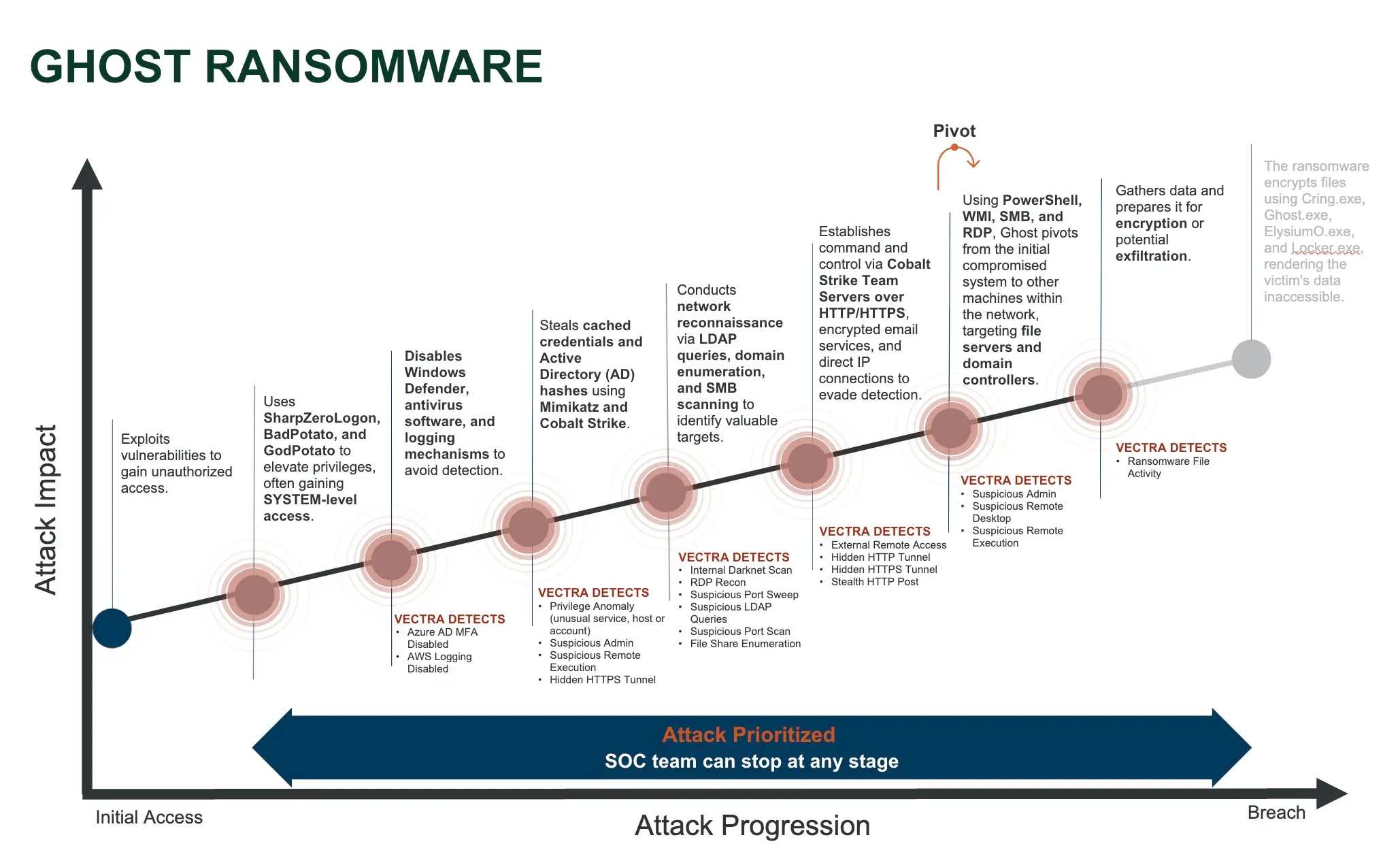
3. Exfiltration Hunting
Exfiltration-focused hunts look for signs that data is being staged and transferred out of the environment. In one case, a ChatGPT-named process located in a Firefox folder was observed exfiltrating Firefox password and cookie data to the Telegram API. In another, ZIP files were created before a user connected to a cloud storage service, indicating possible staging and smuggling of sensitive data.
These activities are often subtle. Attackers may spread out uploads over time to mimic regular user behavior and avoid detection. Connections to known exfiltration channels like cloud storage platforms, messaging APIs, or even command-line email transfers via SMTP are signals of interest.
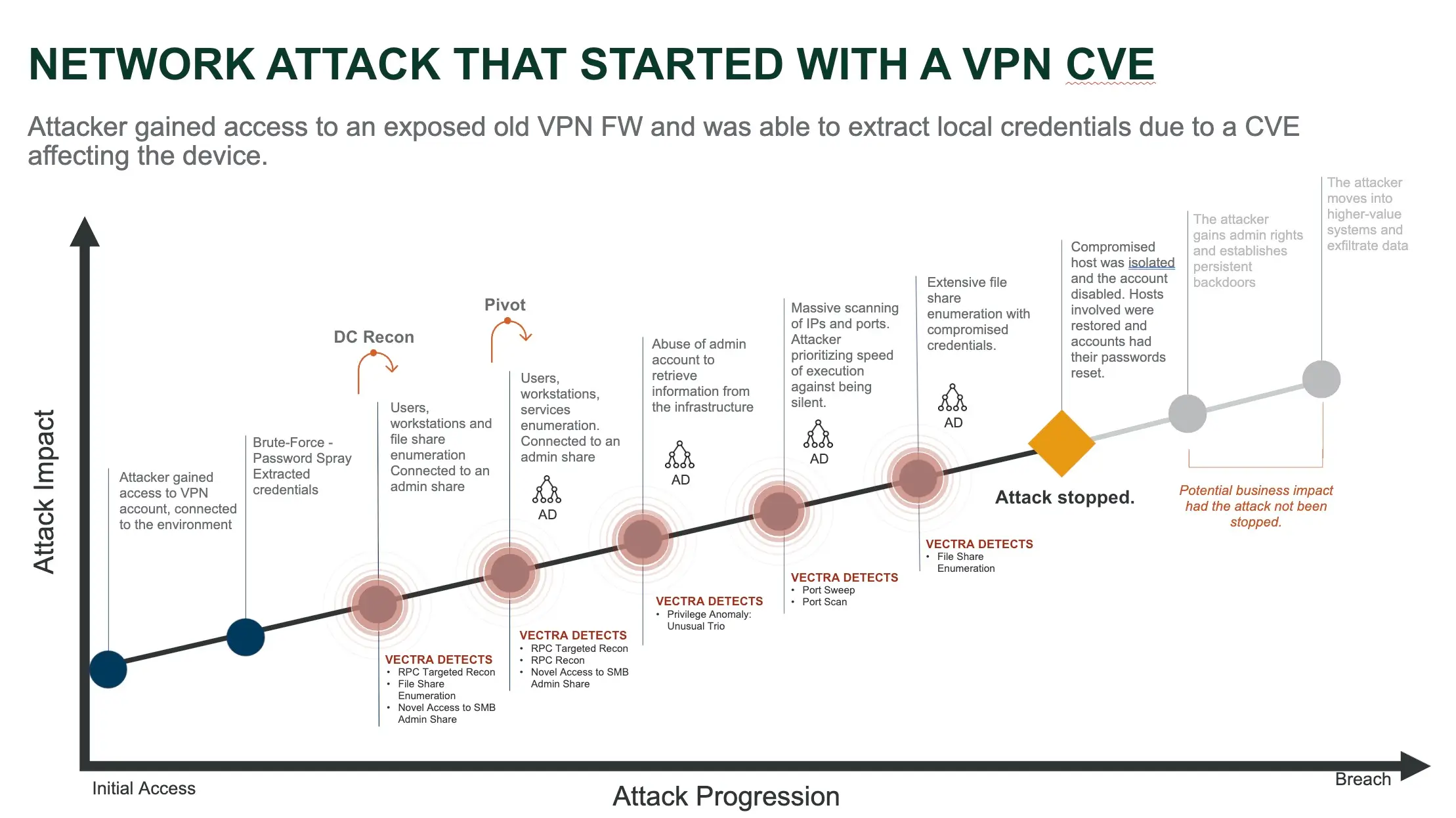
4. Exploit/CVE-Based Hunting
Hunting based on recent CVEs involves checking whether attackers are actively exploiting newly disclosed vulnerabilities. For example, after a CVE affecting SAP systems was disclosed, threat hunters looked for signs of exploitation—such as web shells being deployed or lateral movement initiated after RDP exposure.
This type of hunting includes reviewing logs for known attack sequences or command execution chains following exploitation attempts.
5. Compliance-Based Hunting
Compliance-based hunting ensures security controls are aligned with standards like HIPAA, PCI-DSS, or ISO. Threat hunters check for violations such as:
- Open SMB shares containing sensitive information.
- Storage of plaintext credentials in Excel or text files.
- Unauthorized use of USB drives for data transfer. Additionally, tools placed in unmonitored folders (e.g., C:\temp, C:\pictures) and excluded from security scans may be leveraged by threat actors for persistence or evasion. The presence of such tools often correlates with non-compliance and elevated risk.
6. Credential & Identity-Based Hunting
Credential hunting often begins with leaked credentials found in breach data or on dark web platforms. Threat hunters trace those credentials back to systems and user activity within the organization. In some cases, credential-stealing browser extensions or adware bundled with freeware have been linked to password exfiltration.
Behavior such as unexpected logins from foreign IPs, or MFA events involving bypass techniques like EvilGinx, also raise suspicion. For instance, a user based in Switzerland was observed logging in from the U.S. without valid travel context, indicating session hijacking.
How Vectra AI Makes a Difference in Threat Hunting
1. Unified Visibility Across Network, Identity, and Cloud
Vectra AI brings together telemetry from network traffic, user identity, and cloud activity in a single platform. As modern networks now span on-premises infrastructure, campuses, remote offices, cloud data centers, cloud identities, SaaS, IoT, and OT systems, this holistic approach eliminates the need to pivot across siloed tools. It empowers threat hunters to monitor the entire attack surface in one place—an essential capability for today’s hybrid environments.
2. Unique Network Visibility Exposes the Full Scope of Attacks
In one customer case, slow and stealthy exfiltration occurred over six months via a host that lacked an EDR agent. Because no endpoint telemetry was available, the exfiltration went undetected until Vectra AI was deployed. With its unique network metadata analysis, Vectra AI revealed the consistent outbound traffic pattern to a cloud storage service, uncovering both the tactic and its duration. This demonstrated how Vectra AI fills visibility gaps that other tools may miss.
3. Accelerated Investigation by Clarifying Assets and Users
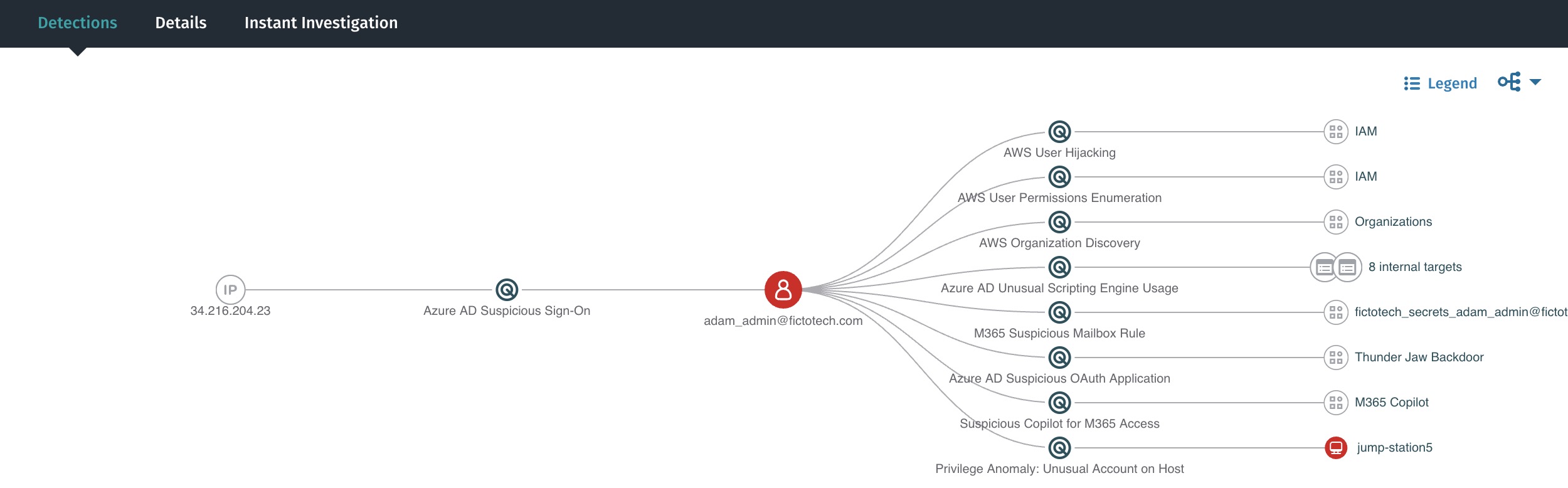
Vectra AI enriches raw telemetry with context—mapping device IPs and session IDs to named users and assets. In cases involving credential theft or identity anomalies (e.g., MFA bypass or suspicious logins), this helped quickly determine which user was involved and what systems were accessed. René highlighted how this clarity reduced time-to-investigation and helped isolate the affected systems without delay.
4. Revealing Compliance Violations
During compliance-based hunts, Vectra AI flagged activities such as unauthorized RDP connections, the use of unsanctioned USB storage, and open SMB shares containing sensitive data. These findings provided concrete evidence of policy violations and helped inform compliance readiness for frameworks like PCI DSS and HIPAA.
5. Simple, Intuitive Investigation Experience
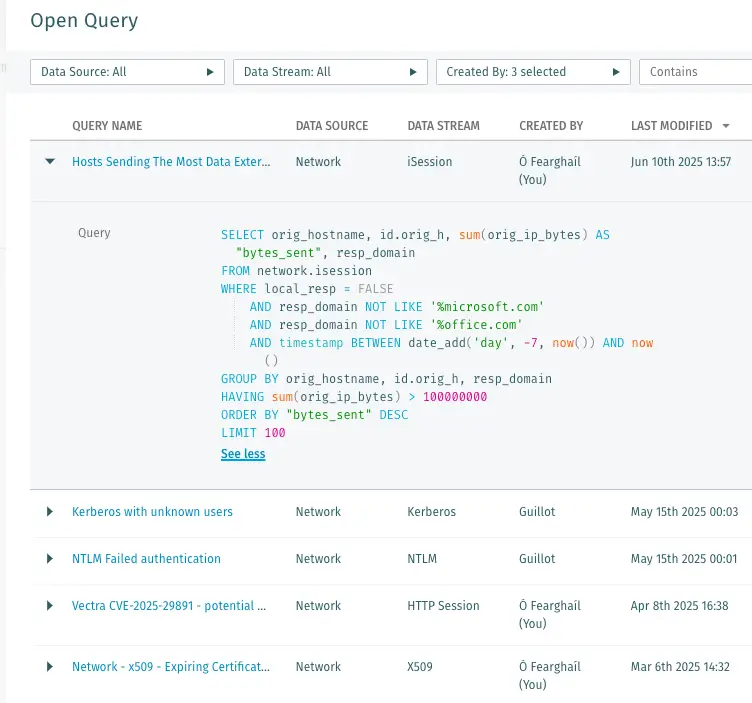
Vectra AI provides threat hunters with direct access to saved searches and curated queries developed by security experts. René emphasized how easy it was to pivot between detections, drill into alerts, visualise multi-domain attacks and reconstruct timelines using the Vectra AI Platform. This simplified access to insights empowered efficient and targeted hunting across environments.

Getting Started: Best Practices for Threat Hunting
- Start with visibility: Ensure you have data from your network, endpoints, cloud, and identity sources all in one place.
- Baseline normal behavior: Understand how your users and systems typically operate.
- Regular themed hunts: Structure hunts around specific use cases or threat scenarios on a monthly or quarterly basis. You can also leverage Vectra AI’s saved searches and expert-curated suggested searches to kickstart your threat hunting.
- Automate where possible: Build detection rules for recurring patterns, such as new RMM tool installations.
- Use reports and CTI platforms: Leverage threat intel feeds and reports to build fresh hunt hypotheses.
Final Thoughts
Threat hunting is about knowing your environment well enough to recognize what doesn’t belong. Vectra AI transforms this process by giving you visibility across all attack surfaces, enriching the data with behavioral context, and tying it all together.
Start small. Choose a use case. Correlate what you find. With Vectra AI, your first hunt can be your first win.
Ready to see Vectra AI Platform in action?
Watch the demo and see how we make a difference in your investigation and threat hunting.

