This is the second installment in our command and control (C2) Evasion Technique series, where I talk about malleable C2 profiles. Check out my first blog where I examine a method known as JA3 signature randomization.
Malleable C2 profiles have been widely adopted and used by Cobalt Strike, a popular framework used by pen-testers and Advanced Persistent Threat (APT) groups. It is worth noting that while Malleable profiles are familiar to Cobalt Strike users, the adoption of their use has started to spread to other C2 Frameworks as well. As of this writing malleable profiles are also used in Empire C2 as of version 3.4. What makes this development even more interesting is that Empire team has recently announced a partnership with Kali Linux, a popular pen-testing distribution, which will increase the prevalence of malleable profile use.
Malleable Profiles for Evasion
Malleable profiles for C2 allow the actor to not only evade detection on the wire from network-based detection tools but also endpoint security products. The level of “malleability” allows Cobalt Strike operators to not only fully customize the shape and timing of C2 beacons but furthermore gave the ability to customize on-target functions like process injection and in-memory obfuscation methods. Operational security is always a concern when running agents inside of a target environment. As such network security monitoring is always a consideration when maintaining stealth with command and control. Let us suppose that when attackers install agents on compromised machines inside your network the traffic generated by these agents when connecting to the C2 server used the same or similar user-agents, URI’s or other artifacts that are easy to flag. The risk of those activities being detected would be exceptionally high if they were known in advance due to repeated use. As such there is a need to transform or shape traffic in such a way that it can either blend in with “normal” expected traffic or just use new values on each run. Either approach would be useful in evading detection. Another motivation for employing malleable profiles is a desire to test against know threats. If I can setup an agent and C2 server to appear exactly the way some malware looks over the wire or on a target endpoint I can then see if my network detection stack or endpoint security monitoring is able to flag the activity.
This is where malleability comes into play. It is worth going over some of the options provided to the operator to customize C2. Additionally, in summary we will talk about how these make detection difficult especially with signature-based detection strategies. I will separate the summary of functionality between network and endpoint. The options presented are in no way to be considered an exhaustive list.
Evasion through Customization
Regardless of the network protocol e.g., HyperText Transfer Protocol (HTTP) or HTTPS, agents will communicate with servers in a specified way. If using HTTP there are many parts of an HTTP conversation that can be inspected by network layer defenses. For example, strings within a HTTP header that are unique enough can be used by defenders to detect connections on the wire. Things like unique user-agents, custom accept strings, and unique path values are all open for inspection Settings can also be used to modify header elements from the server end as well.
With malleable profiles one can simply mirror a legitimate programs values such as those in the HTTP header to make the connection appear identical to benign connections like Microsoft Windows update agent for example. The screenshot below shows a Wireshark reconstruction of a HTTP session using a Cobalt Strike Windows update malleable profile.

It is worth pointing out that data transforms are available to encode data prior to transmission. It may not be obvious but the Uniform Resource Identifier (URI) following the HTTP GET request in the screenshot above is base 64 encoded prior to transmission and then decoded on the server end. The following list below are data transforms available in Cobalt Strike.
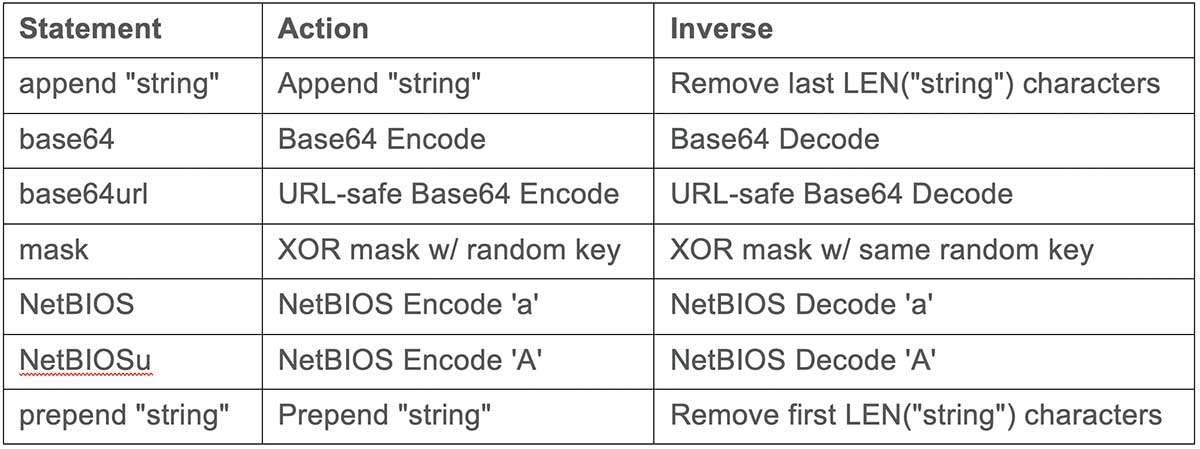
Moreover, multiple transforms can be in tandem as well. So base64 and mask for example can be layered together for added OPSEC.
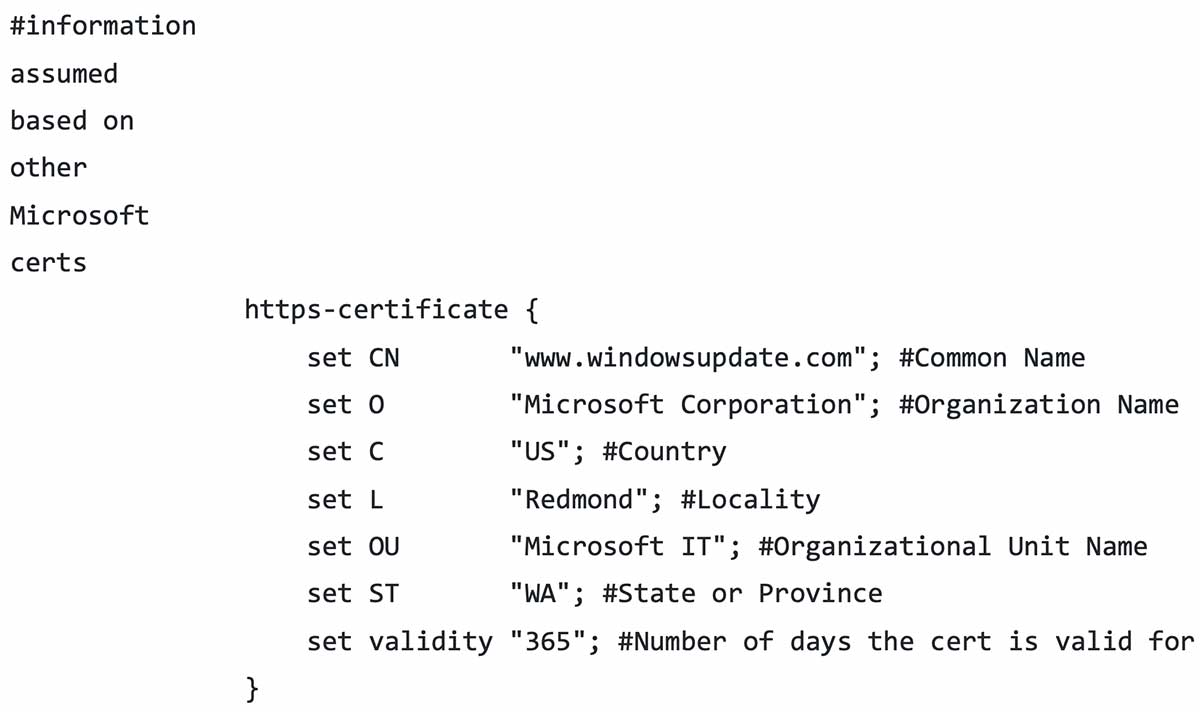
Even in cases where HTTPS is used, values can still be manipulated such as SSL (Secure Sockets Layer) certificates. The following SSL certificate below is used by the Windows update profiles previously mentioned:
In addition to fine control over the way connections appear over the wire, timing values which control when the client connects to the C2 server can also be manipulated via malleable profiles. Values like jitter and delay allow attackers to change the timing interval between C2 connections.
Endpoint malleable
Malleable is not just used when the agent sends data over the network but is also employed when controlling the in-memory characteristics, how it injects into processes and post-exploitation tasks as well. This is useful in evading endpoint detection and response (EDR) and antivirus detection. An example below shows some options related to how the agent behaves on the target endpoint that can be set in malleable profiles.
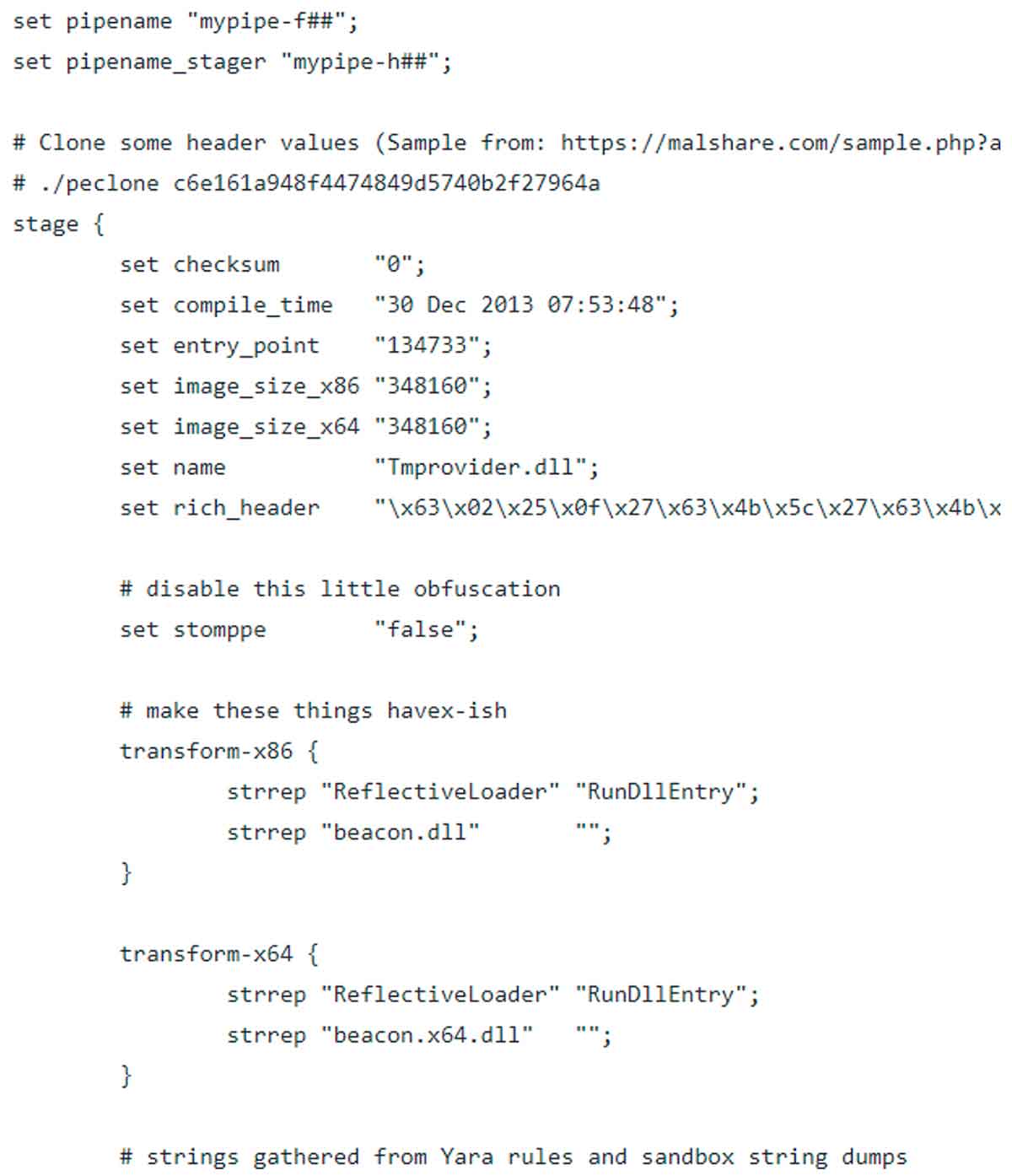
Under the stage block you can control how the agent loads into memory. Things like name, compile time, memory permissions, obfuscation as well as loader type can be specified. Often analysts looking for malicious code loaded into a process will check first the memory segments and key in on segments loaded with RWX permission in suspect memory segments.
Under the process injection options you can shape the injected content. You can pad data using transform options and set the allocation method as well as control permissions. Finally, you can also control post exploitation tasks by choosing different pipe names to use, use smart injection and specify spawn locations. This is great for evading and testing EDR solutions. For a more exhaustive overview you can visit Cobalt Strikes online guide.
Challenges for Defenders
Allowing such granularity with which to control C2 communications and the staging behavior make defending and detecting with signatures a challenging task. Another point of emphasis should be made that while Cobalt Strike has allowed malleability for some time other popular C2 Frameworks like Empire C2 are also adopting malleable profiles. This coupled with the fact that their use is increasing in recent intrusions by APT and ransomware actors makes for an increasingly complex task for defenders.
Network and endpoint defense technologies will have to either have rapidly updated signatures or use other investigative ways to detect command and control which do not rely on repeated patterns in the data or even timing sequences that correspond to beaconing activity.

