Ransomware operations don’t disappear. They evolve.
The ransomware names may change, but the operators, infrastructure, and behaviors often persist under new branding. The latest example is DevMan, a group operating on modified DragonForce code and positioned as the newest entrant in a long lineage of ransomware families built on top of Conti and Black Basta foundations.
While multiple security vendors and analysts have noted technical and operational similarities across these groups, attribution in ransomware remains complex. The rise of DevMan is better understood as a continuation of code reuse, affiliate migration, and shared tooling rather than a definitive link to any specific operator.
The Conti Legacy: The Code That Never Died
Conti’s leaked source code remains one of the most reused ransomware frameworks in existence. It directly fueled the development of Black Basta, and later the DragonForce ransomware family. The leaked Black Basta chat logs further confirmed that its leader, Tramp, had long-standing ties with LockBitSupp, the administrator of the LockBit RaaS empire.
By September 2025, DragonForce announced a coalition with Qilin and LockBit, creating a cross-affiliate ransomware network. The same names reappear across leak sites, affiliate programs, and shared infrastructure, reinforcing that ransomware today operates as an ecosystem, not isolated crews.

The DragonForce Model and the Birth of DevMan
DragonForce introduced a “Dragons-as-a-Service” model, offering affiliates prebuilt ransomware, Tor infrastructure, and leak site publishing rights under its brand. This RaaS program allowed emerging operators to launch attacks quickly, using proven tools.
DevMan first surfaced in mid-April 2025, initially acting as an affiliate for Qilin (Agenda) and DragonForce, while also linked to APOS operations (APOS has also been linked to PEAR since…). Early attacks mirrored DragonForce playbooks: VPN exploitation for entry, SMB probing for lateral movement, and double extortion tactics.
By July 2025, everything changed. DevMan split from DragonForce, launching his own infrastructure including the first leak site called “DevMan’s Place.” Forensic analysis published by ANY.RUN on July 1 confirmed that his payload reused DragonForce code, itself based on Conti, and included several technical flaws:
- The ransom note self-encrypts, a builder misconfiguration.
- The wallpaper feature fails on Windows 11 but works on Windows 10.
- Three encryption modes are included: full, header-only, and custom.
- The malware operates entirely offline, with only SMB-based network activity.
The .DEVMAN file extension and new internal strings distinguish the variant, but its DNA remains unmistakably DragonForce.
Attribution in Ransomware Ecosystems is Complex
Attribution in ransomware ecosystems is inherently complicated. As Jon DiMaggio notes in The Art of Attribution (Analyst1, 2024), accurately linking one operation to another requires alignment across technical, behavioral, and human evidence rather than relying on code similarities or timelines alone.
DevMan, like many emerging operators, sits at the intersection of reused codebases, repurposed infrastructure, and shared affiliate networks. The overlap with DragonForce and indirect ties to Conti and Black Basta reflect the broader realities of the ransomware ecosystem. Groups borrow, buy, copy, or modify code. Affiliates frequently migrate across operations. Tooling is resold, leaked, or bundled into new RaaS services.
This creates continuity at a technical level without necessarily implying continuity of leadership. For this reason, DevMan is best understood as a product of ecosystem reuse rather than a confirmed extension of any prior operator.
DevMan 2.0: From Operator to RaaS Provider
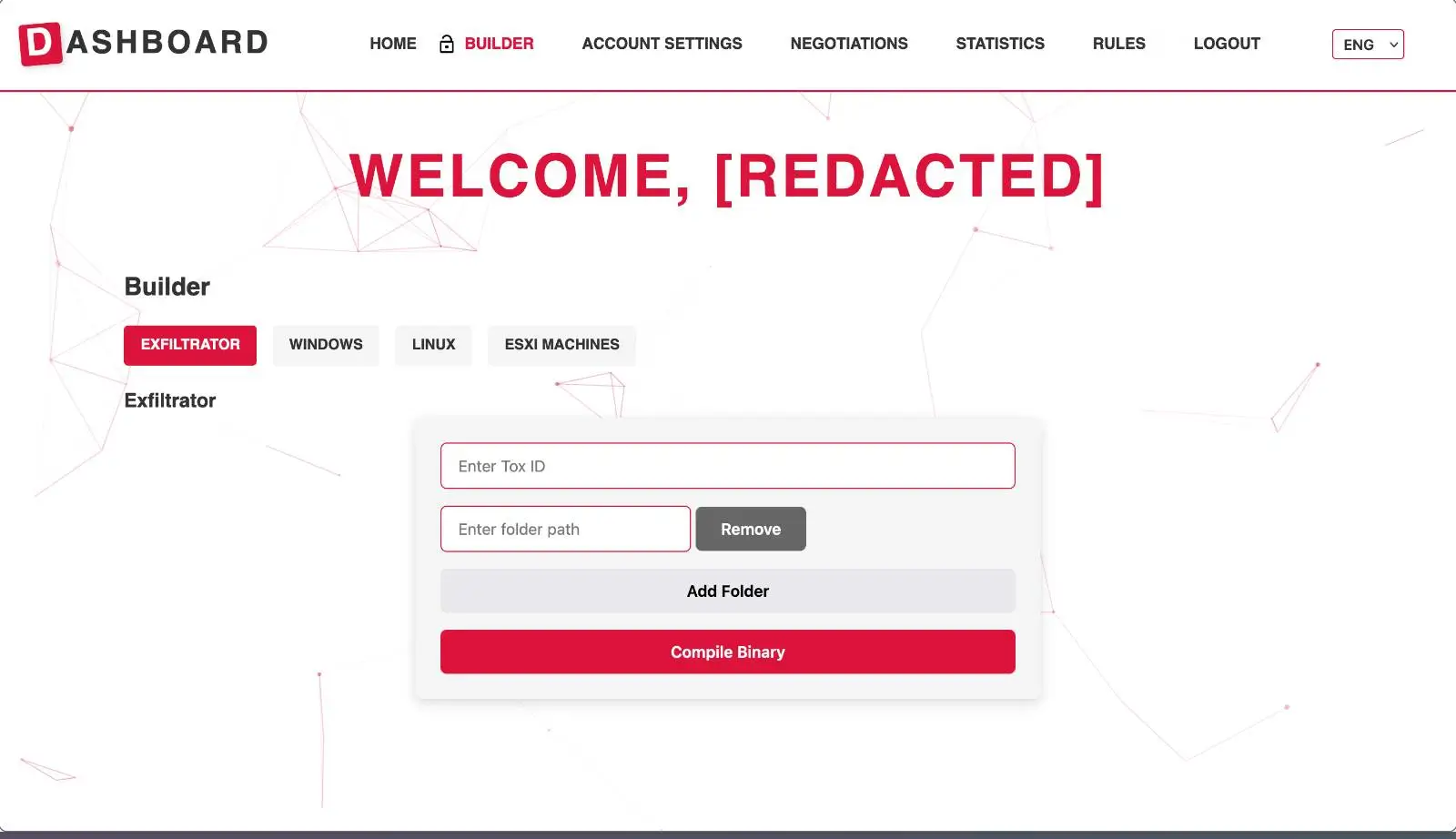
By late 2025, DevMan had evolved from operator to provider. On September 30, 2025, he launched DevMan 2.0, a redesigned Ransomware-as-a-Service platform with affiliate recruitment, a builder dashboard, and new variants written in Rust.
Screenshots from the platform reveal:
- A web-based affiliate dashboard for building encryptors targeting Windows, Linux, and ESXi.
- A structured profit-sharing model, offering 22% revenue share for affiliates generating under $20 million.
- Automated data exfiltration utilities and ransom note customization.
- Rules of conduct prohibiting attacks against CIS states and healthcare entities related to children.
In practice, DevMan 2.0 functions much like DragonForce, but with branding, infrastructure, and affiliate control entirely under one operator.
Why It Matters for Defenders
DevMan illustrates how ransomware operations can rebrand, restructure, and redistribute code without altering the underlying behaviors used during intrusions. SOC teams face adversaries who change names frequently, but their techniques remain consistent.
Across Conti, Black Basta, DragonForce, and DevMan, several behaviors continue to surface:
- Offline encryption and lateral movement via SMB and RDP.
- Use of legitimate tools for persistence.
- Rapid affiliate onboarding using shared builder frameworks.
Signature-based defenses fail against this model. What remains constant is attacker behavior, visible in network traffic, identity misuse, and privilege escalation attempts. These are exactly the patterns the Vectra AI Platform detects in real time.
How Vectra AI Detects What Rebrands Can’t Hide
Whether or not attribution can be confirmed, the behaviors are what matter for defenders. The Vectra AI Platform focuses on detecting attacker tactics and behaviors, not brand names.
By analyzing identity, network, and cloud behaviors, the Vectra AI Platform detects the signs of ransomware execution and lateral movement before encryption begins, whether it’s DevMan, Play, Qilin, Scattered Spider or any other APT group.
Attackers can change their names, but not their behaviors.
With Vectra AI, you can see what they can’t hide.
Watch a self-guided demo of the Vectra AI Platform to see how behavioral AI detects ransomware activity, even across rebrands.

