The ransomware group calling itself GLOBAL has released a promotional video that feels more like a SaaS product launch than a criminal threat. With promises of 24/7 support, weekly updates, and mobile management, the video shows how ransomware-as-a-service (RaaS) has matured into a professionalized, franchise-style business model.
Behind the slick branding, GLOBAL’s feature set tells us a lot about how affiliates operate and why traditional defenses often fall short. Each capability is carefully designed to accelerate impact, reduce detection, and maximize ransom payments.
Enterprise Reach and Scale
Multi-Platform Build: Hitting the Enterprise Where It Hurts
Enterprises run more than Windows laptops. They depend on Linux servers for applications, VMware ESXi hypervisors for virtualization, and NAS/BSD appliances for storage. These platforms are central to resilience, but they’re also attractive ransomware targets.
GLOBAL’s builder lets affiliates create ransomware packages for all of them in minutes. This ensures that backups, storage, and virtual machines are just as vulnerable as desktops. Their goal is simple: remove every path to recovery. For SOC teams relying on endpoint tools alone, visibility into ESXi or NAS systems is almost nonexistent, leaving entire infrastructures exposed.
One-Click Propagation: Speed as a Weapon
A single infected endpoint doesn’t guarantee ransom leverage. To lock an enterprise into paying, attackers need scale and speed.
GLOBAL’s one-click propagation automates lateral movement, pushing ransomware across a network in minutes. Affiliates don’t need deep technical skills; the platform handles the spread using stolen credentials and shared drives. By the time defenders spot unusual activity on one host, dozens more may already be encrypted. Legacy defenses like EDR or firewalls rarely flag this kind of internal, credentialed traffic, allowing attackers to outrun response teams.
Mount Mode: Encrypting Beyond the Endpoint
Critical business data often lives on shared network drives mounted to user machines. These drives don’t typically run endpoint protection, making them prime ransomware targets.
GLOBAL’s mount mode exploits this by encrypting remote disks from the infected endpoint. No binary ever touches the NAS or file server. For the attacker, it means broad coverage without added risk. For defenders, it means EDRs never see malicious code on those storage systems, backups get encrypted alongside primary data, and SOCs are left with little visibility into the attack until it’s too late.
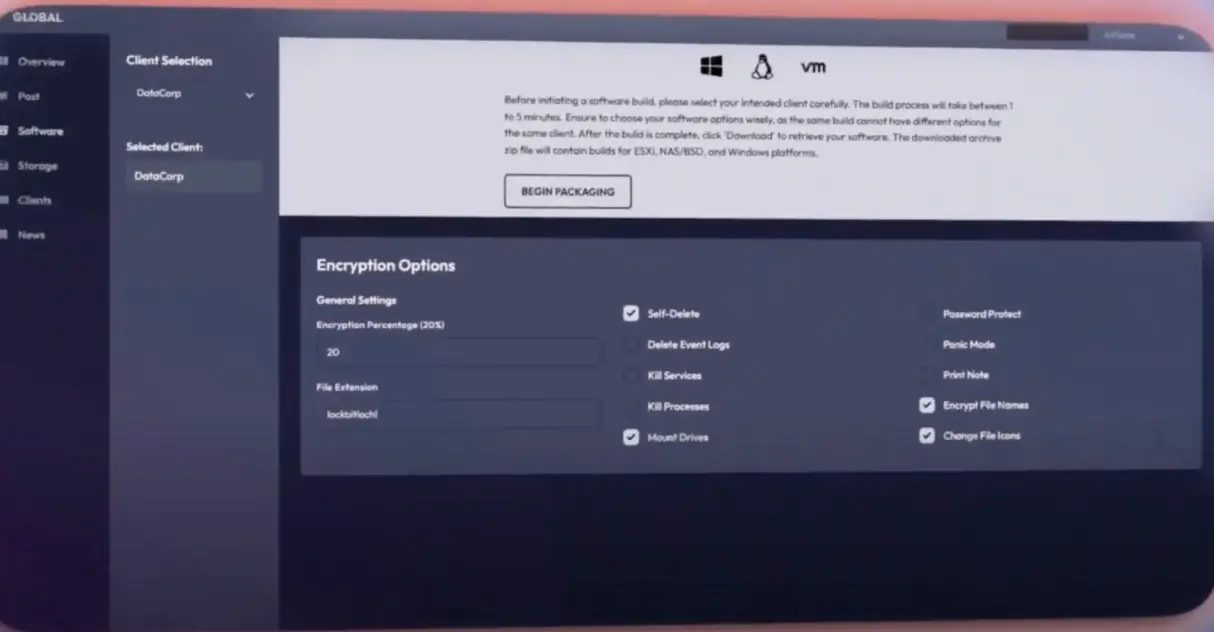
Destructive and Evasion Toolkit
Self-Delete Binaries: Erasing the Evidence
Once executed, GLOBAL can erase its own binary, leaving no file for defenders to analyze. This denies SOC teams critical forensic evidence and buys affiliates time to reuse the same payload elsewhere. Traditional antivirus, reliant on signatures, is blind once the sample is gone.
Delete Event Logs: Blinding the Defenders
By wiping Windows event logs, GLOBAL eliminates the audit trail of lateral movement, privilege escalation, or process execution. Investigators are left with encrypted files and no trace of how the attack unfolded. SIEM platforms that depend on logs become ineffective when those logs vanish at the source.
Kill Services and Processes: Clearing the Path for Encryption
GLOBAL can terminate databases, backups, and endpoint security agents before encryption. This guarantees smoother encryption, denies recovery options, and silences defenses. While EDRs can flag mass process kills, attackers disguise them as routine IT tasks, blending into normal administrative noise.
Encrypt File Names and Icons: Branding the Attack
GLOBAL lets affiliates customize encrypted files with extensions like .GLOBAL and ransom-branded icons. It’s not just technical: it’s psychological. Employees opening folders see nothing but renamed, branded files, reinforcing panic and pressure. Antivirus ignores cosmetic changes, and many SOC tools aren’t tuned to catch bulk metadata alterations.
Panic Mode: A Kill Switch for Control
GLOBAL includes a “panic mode” to halt execution instantly. This protects affiliates if they hit a sandbox, encounter hardened defenses, or misfire on a target. The ransomware disappears mid-operation, leaving partial traces at best. AV and EDR rarely catch an attack that stops before telemetry builds up.
Extortion and Pressure Tactics
AI-Powered Negotiation: Automating the Ransom Conversation
Negotiating ransom payments is labor-intensive. GLOBAL solves this with AI support that guides conversations, adapts demands, and maximizes payouts. Affiliates can run multiple campaigns without juggling chats. Victims aren’t talking to a human—they’re bargaining with automation optimized for leverage. No legacy tool can disrupt this dynamic.
Blog and Mobile App: Extortion at Their Fingertips
GLOBAL affiliates control their own extortion blog and can manage leaks via a mobile app. They can upload stolen data, start countdowns, and escalate pressure campaigns instantly. Double extortion becomes portable, always-on, and independent of central operators. Traditional defenses offer no prevention here—only threat intel monitoring after leaks go public.
Conclusion: Defenders Need to Match the Industrialization of Ransomware
GLOBAL illustrates a larger truth: ransomware has evolved into an industrialized service model. Affiliates are empowered with automation, destructive tools, and professional support, while traditional defenses struggle to keep pace.
For defenders, relying on EDR, SIEM, or backups alone is no longer enough. These tools are important, but GLOBAL’s features are explicitly designed to bypass them. To stop ransomware before encryption and extortion begin, SOC teams need visibility that spans identity, network, cloud, and endpoint, tied together with intelligence that can detect attacker behaviors in real time.
That’s where the Vectra AI Platform comes in. By detecting behaviors like lateral movement, credential misuse, and abnormal encryption activity, Vectra AI helps SOC teams see attacks like GLOBAL before the ransom note appears. It’s the missing layer that closes the detection and response gaps left by traditional tools.
- Read how Vectra AI can help your team stop ransomware in its tracks.
- Watch the self-guided demo of the Vectra AI Platform.

