ITDR solution for Microsoft Entra ID (Azure AD)
ITDR solution for Microsoft Entra ID (Azure AD)
Detect Microsoft cloud identity attacks others can’t
Low budget? Limited resources? Overextended staff? Find and stop Microsoft Entra ID (Formerly Azure AD) cloud identity attacks before they can cause damage — no matter what your security team looks like.

Find Microsoft Entra ID identity attacks within minutes
That’s 99% faster than the average time of 328 days it takes to detect and contain a data breach caused by compromised credentials.*
*Source: IBM Data Breach Report
>90%
MITRE ATT&CK coverage
50%
less analyst workloads
50%
Vectra AI found an attack in 50% of deployments in the past 6 months
Why Vectra AI
Why choose Vectra ITDR to defend against Microsoft Entra ID attacks?
Find identity attacks others can't
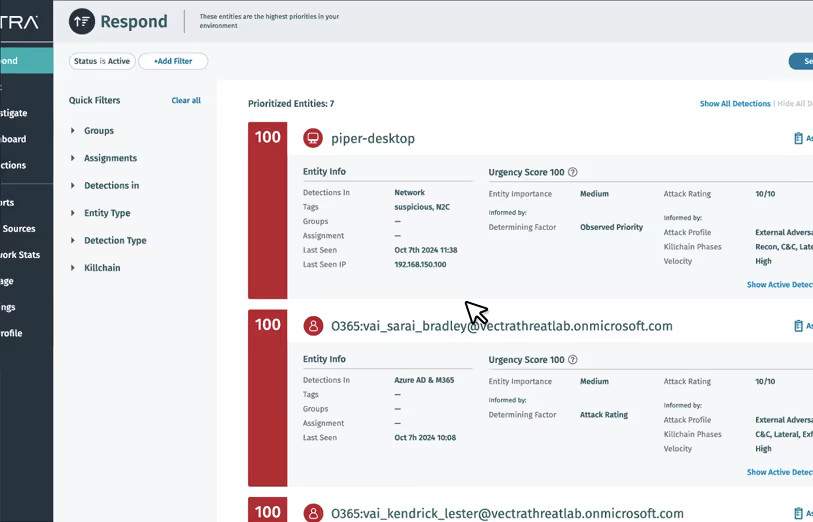
Find attacks early with zero-day coverage for never-before seen attack techniques. You’ll see everything that happens after an attacker gains access — Vectra AI correlates identity activity to broader network and cloud activity for integrated detection coverage.


Reduce workloads
AI prioritization and attack ratings correlate cloud and network activity to create clear attacker narratives — so you can focus on urgent threats, not benign events. Deploy it out-of-the-box within 10 minutes, minimal tuning needed.


Reduce workloads
AI prioritization and attack ratings correlate cloud and network activity to create clear attacker narratives — so you can focus on urgent threats, not benign events. Deploy it out-of-the-box within 10 minutes, minimal tuning needed.
Maximize talent
See and stop attacks in one place — no more switching between tools. Our enhanced logs make investigations easy and fast, and flexible response options let you halt attacks without impacting operations.


Attack Anatomy
See how Vectra ITDR defends against real-world Microsoft Entra ID attacks
When prevention controls fail to stop a Microsoft Entra ID cloud identity attack, Vectra AI finds it — fast and early.

Self-Guided Tours
Experience the power of the Vectra AI Platform
Click through at your own pace to see what analysts can achieve in a platform powered by the world's most accurate attack signal.

MITRE Mapping
Comprehensive MITRE ATT&CK coverage for Microsoft Entra ID (Formerly Azure AD)
With more references in the MITRE D3FEND framework than any other vendor, only Vectra AI gives you an unfair advantage over attackers targeting Microsoft Entra ID.
TA0001: Initial Access
T1078: Valid Accounts
TA0002: Execution
T1059: Command and Scripting Interpreter
T1651: Cloud Administration Command
TA0003: Persistence
T1098: Account Manipulation
T1136: Create Account
T1556: Modify Authentication Process
T1078: Valid Accounts
TA0004: Privilege Escalation
T1484: Domain Policy Modification
T1078: Valid Accounts
TA0005: Defense Evasion
T1484: Domain Policy Modification
T1562: Impair Defenses
T1556: Modify Authentication Process
T1078: Valid Accouts
T1564: Hide Artifacts
T1070: Indicator Removal
T1550: Use Alternate Authentication Material
TA0006: Credential Access
T1110: Brute Force
T1606: Forge Web Credentials
T1556: Modify Authentication Process
T1621: Multi-Factor Authentication Request Generation
T1528: Steal Application Access Token
T1649: Steal of Forge Authentication Certification
T1552: Unsecured Credentials
T1539: Steal Web Session Cookie
TA0007: Discovery
T1087: Account Discovery
TA0008: Lateral Movement
T1534: Internal Spearphishing
T1080: Taint Shared Content
T1550: Use Alternate Authentication Material
TA0009: Collection
T1119: Automated Collection
T1530: Data from Cloud Storage
T1213: Data from Information Repositories
T1114: Email Collection
TA0010: Exfiltration
T1048: Exfiltration Over Alternative Protocol
TA0040: Impact
T1531: Account Access Removal
T1499: Endpoint Denial of Service
T1498: Network Denial of Service
Copilot for M365 Detection and Response
Stop attackers from abusing Copilot for Microsoft 365
Secure your GenAI attack surface and stop attackers from gaining access to sensitive applications and data.
Learn more

Featured Datasheet
Vectra Identity Threat Detection and Response
Learn more about how Vectra ITDR helps you defend against identity attacks.


Microsoft Entra ID FAQs
What types of risks are there in Microsoft Entra ID?
As Microsoft’s enterprise cloud-based identity and access management (IAM) solution, Entra ID is your frontline defense for secure access to apps and data. But it has vulnerabilities. Attackers use flaws and misconfigurations to take over accounts that rely on pre-established trust.
How can you make Microsoft Entra ID (Azure AD) more secure?
Prevention can fail. To fully defend against identity attacks, you need to expose the cloud identity attacks already hiding in your environment. AI-driven detection and response is the only proven way to stop attackers before they can inflict damage.
How does Vectra AI help?
Vectra Identity Threat Detection and Response (ITDR) uses machine learning and identity-focused behavior analytics to identify active identity attackers. It reveals credential misuse, privilege escalation, entitlement abuse, replication streams and other identity-based threat tactics in meaningful detail — without long delays and guesswork. As a result, our customers are able to identify and stop Microsoft Entra ID attacks the day they occur.
How is Vectra AI different from your prevention solutions?
The Vectra AI Platform detects the earliest signs of an attack so you can stop an attacker before any damage is done. It detects identity attacks when attackers bypass prevention.For example, unlike privilege access management (PAM), which focuses on preventing unauthorized access, Vectra AI uses privileged access analytics (PAA) to closely follow accounts most useful to attackers. PAM focuses on prevention; Vectra AI finds attackers already hiding in your environment so you can shut them down in minutes.





