Microsoft 365 & Hybrid Cloud Threat Detection
Microsoft 365 & Hybrid Cloud Threat Detection
Detect when your Microsoft 365 is under attack
See and stop unknown attackers hiding in your M365 SaaS environment with the industry’s only platform powered by advanced Attack Signal Intelligence™.

Find attackers in your Microsoft 365 environment
With 11 references in the MITRE D3FEND framework — more than any other vendor — only Vectra AI provides Cloud Detection and Response (CDR) solutions powerful enough to reveal the earliest signs of hybrid cloud compromise.
#1
Most-referenced in MITRE D3FEND
35
AI threat detection patents
>90%
MITRE ATT&CK coverage
Our customers
Integrate and operate Vectra CDR within a day
Before Vectra AI, developing a single detection at Blackstone took up to six months. Now, it's done in a day.
"Through one simple integration, completed in just a single day, we were able to add over 50 new threat detections against our Microsoft 365 environment."

Kevin Kennedy
Senior Vice President, Cybersecurity, Blackstone
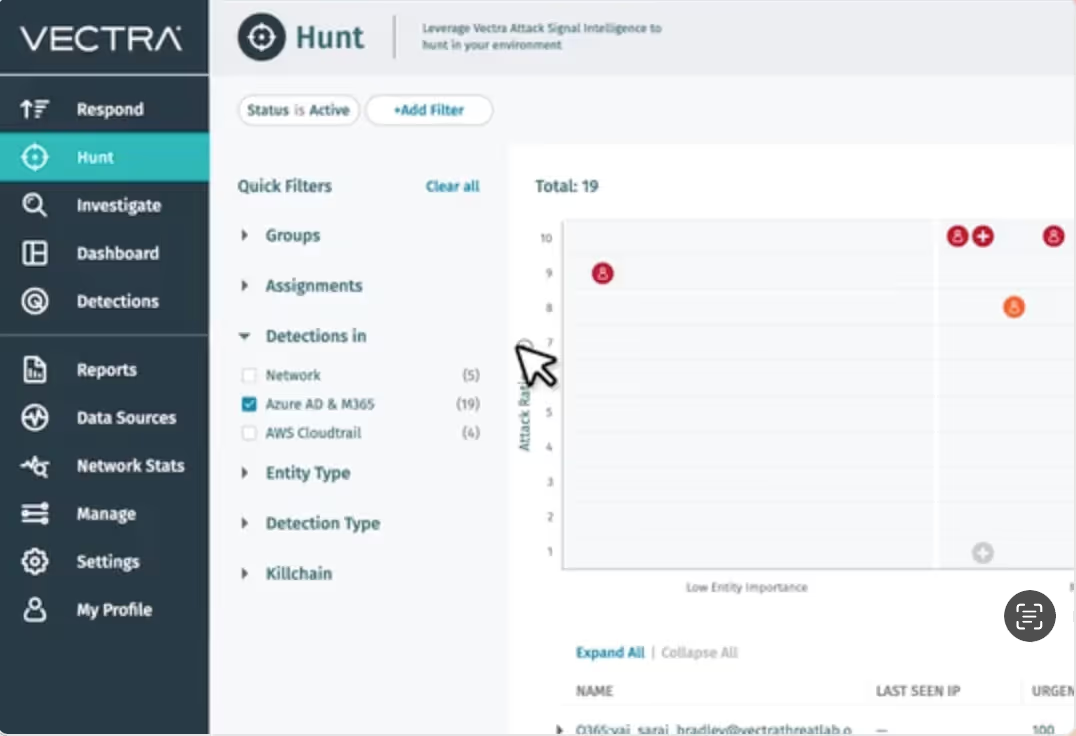
CDR Differentiators
Vectra CDR for M365 gives you:
See attackers manipulating M365 access, tools, services and applications including SharePoint, OneDrive, Teams, Exchange, Power Automate, eDiscovery and more.
Expose more than 90% of relevant MITRE ATT&CK techniques with Attack Signal Intelligence to zero in on post-compromise attacker behaviors.
Explore our AI
Use one central platform to query Azure AD, M365 and AWS Control Plane logs for faster threat hunting and response.

Team up with skilled analyst reinforcements committed to co-defending your M365 environment.
Explore our AI

Complete visibility and context
See attackers manipulating M365 access, tools, services and applications including SharePoint, OneDrive, Teams, Exchange, Power Automate, eDiscovery and more.

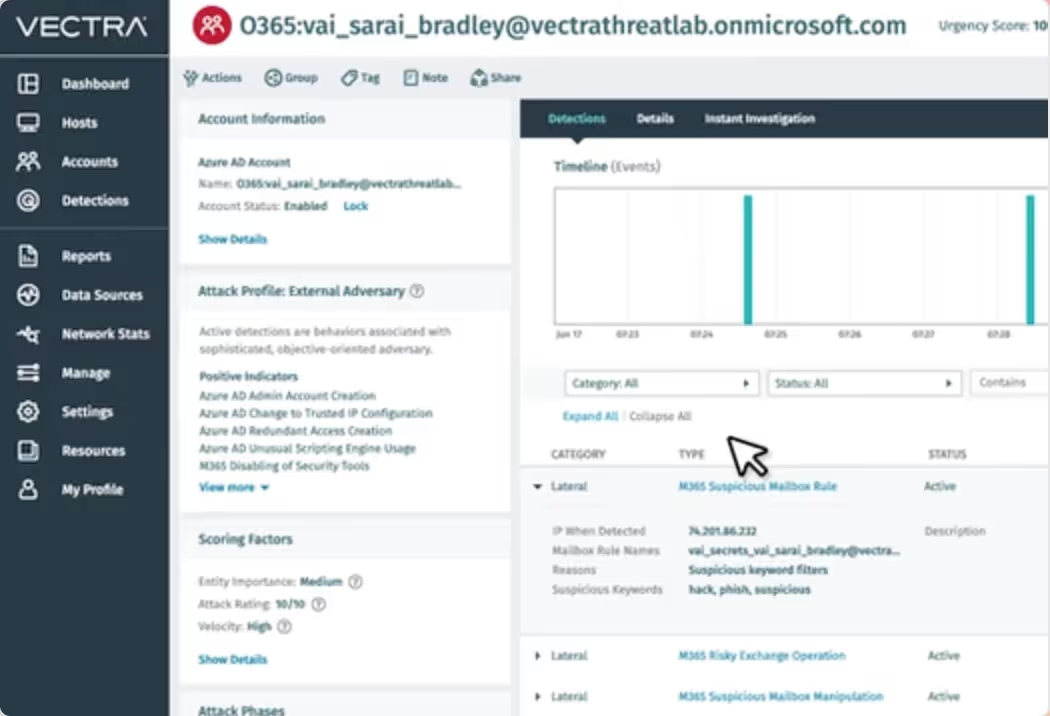
AI-driven detection and prioritization
Expose more than 90% of relevant MITRE ATT&CK techniques with Attack Signal Intelligence to zero in on post-compromise attacker behaviors.
Explore our AI

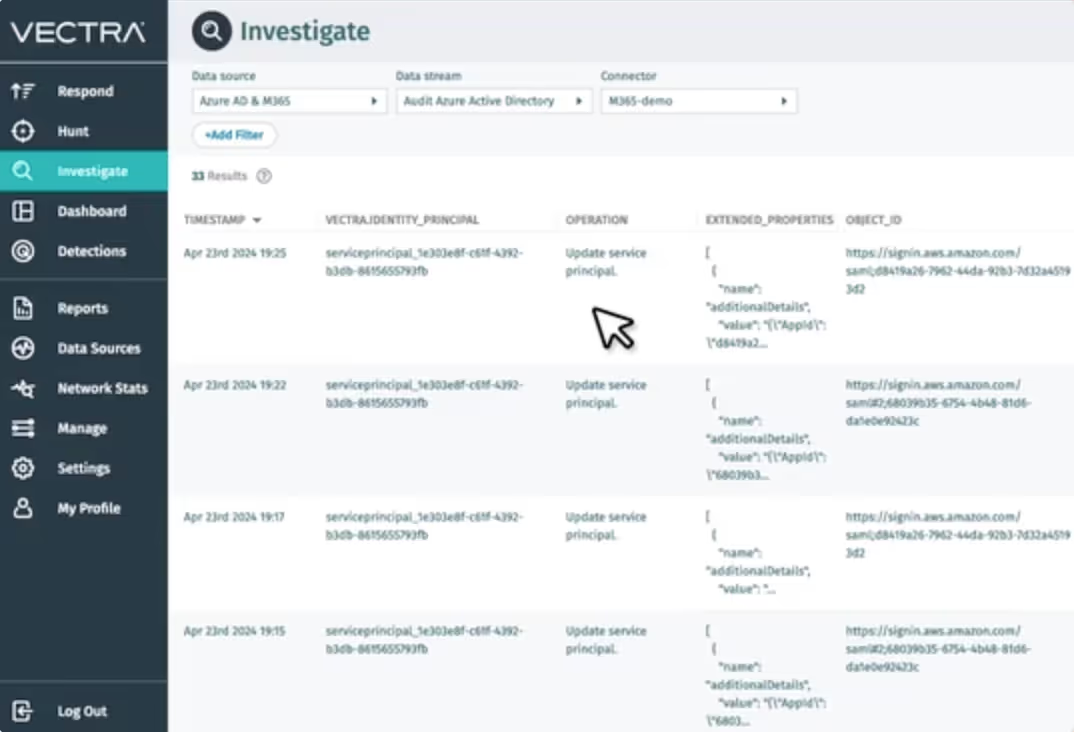
Integrated investigations
Use one central platform to query Azure AD, M365 and AWS Control Plane logs for faster threat hunting and response.

Shared responsibility for 24x7x365 coverage
Team up with skilled analyst reinforcements committed to co-defending your M365 environment.
Explore Vectra MDR
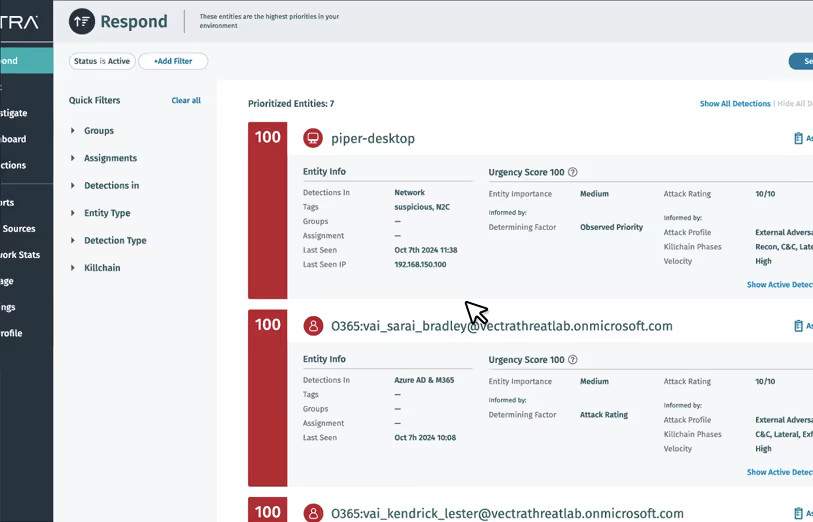
CDR Capabilities
With Vectra CDR for M365, detect and disarm attacks in minutes — no matter where they occur
AI-driven Detection
Expose the complete narrative of an attack and cover over 90% MITRE ATT&CK techniques.
AI-driven Triage
Reduce alert noise by 80% or more with ML that understands your environment.
AI-driven Prioritization
Harness security AI to automate prioritization to escalate the threats that matter most to the business.
Advanced Investigations
Streamline research of Azure AD, M365 and AWS Control Plane logs to understand the attacks facing you in minutes.
Ecosystem Integrations
Integrate existing tech for correlation and context and to automate analyst workflows and response controls.
Copilot for M365 Detection and Response
Stop attackers from abusing Copilot for Microsoft 365
Secure your GenAI attack surface and stop attackers from gaining access to sensitive applications and data.
Learn more

Integrations
Protect your M365 environment with Vectra CDR
Enterprises worldwide trust Vectra AI's Cloud Detection and Response solution to protect their Microsoft environment.
- Stop attackers in Microsoft 365 and Azure AD
- Use native integrations for Microsoft Sentinel and Defender for Endpoint
- Stay compliant by ingesting need-to-know logs only
Self-Guided Tours
Experience the power of the Vectra AI Platform
Click through at your own pace to see what analysts can achieve in a platform powered by the world's most accurate attack signal.

FAQS
Vectra CDR for M365: Frequently Asked Questions
What’s the difference between hype and real value in cloud threat detection?
Real value looks like behavior-based detections across cloud, identity, and network. It enriches data, ties signals to known attacker techniques, and limits alert noise. It maps activity to entities and attack stages, not just events. It shows lateral movement, privilege misuse, and risky API calls with clear next steps. It must cover AWS, Azure, and M365 consistently. Effective platforms also explain “why it matters” in plain language and support quick investigation. See how Vectra unifies coverage, clarity, and control across domains.
How do I avoid alert fatigue while maintaining strong coverage?
Reduce noise at the source. Use detections that understand normal behavior, then elevate only high-relevance signals. Correlate events across identities, networks, and clouds to build attack profiles, not stacks of alerts. Prioritize entities using context like privilege, spread, and speed. Keep everything visible server-side so teams can act fast. This approach lowers false positives and shortens investigations without closing detection gaps. Vectra’s AI Agents triage, stitch, and prioritize in real time to remove 99% of alert noise and save analyst time.
What environments and threats should “cloud threat detection” cover, including hybrid and API misuse?
Cover control planes, data planes, and both machine and human identities across hybrid footprints. Watch for risky role changes, abnormal API calls, and token misuse. Detect lateral movement between on-prem and cloud, SaaS credential theft, and staging for exfiltration. Include container orchestration and serverless where applicable. Tie every signal back to entities and techniques so teams know impact and urgency. Multi-cloud breadth matters, but consistency across AWS, Azure, and M365 matters more. Vectra provides cloud, identity, and network detections with entity-centric context across those stacks.
How is cloud threat detection different from SIEM, EDR, or NDR?
SIEMs aggregate logs, and EDR tools monitor endpoints, but modern NDR now incorporates cloud threat detection. That means analyzing control plane activity, API misuse, and identity behaviors across cloud environments as part of a unified detection approach. Rather than treating cloud as a separate silo, effective solutions correlate signals across network, cloud, and identity layers to expose real attacks with clear context on impacted entities, supporting faster, more accurate responses.
What makes automated cloud threat detection more scalable and efficient?
Scalable cloud threat detection automatically ingests relevant data, enriches it with context, and applies behavior-based models to identify real threats. It must correlate activity across cloud, identity, and network domains, factoring in privilege level, access patterns, and attack progression. Efficient systems minimize noise, adapt to dynamic environments like short-lived workloads or shifting roles, and clearly surface what matters, without constant tuning. Analysts need reliable, explainable results that accelerate investigations and response workflows.
How can cloud threat detection help with compliance needs like HIPAA, FedRAMP, or SOX?
Continuous monitoring of identities, control plane activity, and data access supports audit evidence and exception handling. Mapping detections to recognized frameworks improves control effectiveness. Clear narratives help explain incidents and remediation. Breadth matters: hybrid coverage ensures gaps are visible during attacks. Teams also need quick reporting and stable integrations. Vectra AI aligns detections to frameworks and provides cross-domain visibility with simple paths to investigate, document, and respond across identity, cloud, and network.
Can cloud threat detection work for small teams with limited bandwidth?
Yes. Look for platforms that reduce investigations, not just create alerts. They should auto-triage noise, correlate signals, and rank urgency by entity and host. Interfaces must guide analysts with one-click pivots to deeper context. Deployment should be agentless where possible and cover hybrid environments without custom effort. These traits lower operational load and help security operations teams focus on real attacks. Vectra’s AI Agents and unified detections give lean teams coverage, clarity, and control in one place.
Resources
